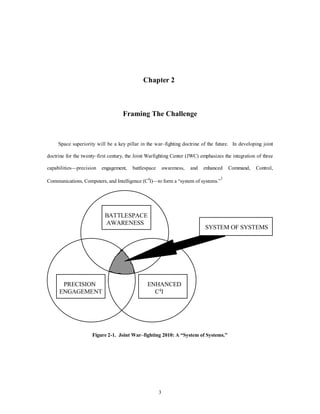
This document proposes concepts and technologies for counterspace operations in 2025, including space detection, anti-satellite weapons, space interdiction nets, miniaturized satellites, satellite cloaking, kinetic and directed energy weapons. It outlines offensive and defensive counterspace architectures and recommends further analysis of miniaturization, stealth, detection and targeting concepts as well as kinetic and directed energy weapons. The goal is to maintain US space superiority as space becomes increasingly vital to national security and more countries and commercial entities access space.





















































![Contribution to Air and Space Superiority - Probability that a particular system will spur a military
technical revolution in 2025 (a silver bullet system). (5= revolutionary contribution to air and space
53
superiority; 1= minimal contribution).
Cost - An order of magnitude estimate of system cost. (5= system cost measured in millions; 3= system
cost measured in billions; 1= system cost measured in trillions).
Lethality - Probability of kill (for offensive systems) or probability to prevent hard kill (for defensive
systems). (5=very high probability of kill/save; 1=very low probability of kill/save).
Selectivity - Represents the range of options a system offers in terms of offensive or defensive
capabilities. For offensive systems, selectivity measures the ability to inflict hard kill, soft kill, or both. For
defensive systems, selectivity represents the ability to protect against hard kill, soft kill, or both. (5= offers
all options [hard kill, soft kill, both]; 1= offers no options).
Technology Challenge - The probability that technology will advance enough in key areas to provide
the capability described in the concept. (5=forecast by 2025; 4=plausible by 2025; 3= possible by 2025; 2=
beyond 2025; 1= well beyond 2025).
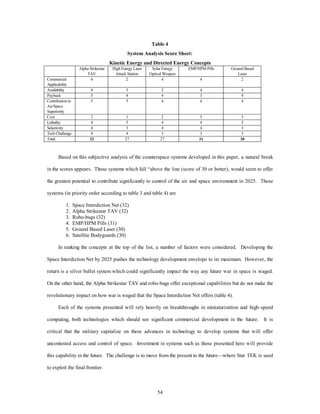
Table 3
System Analysis Score Sheet:
Miniaturization, Stealth, and Detection/Targeting Concepts
Satellite
Bodyguards
Robo-bugs Satellite
Cloaking
SMAKS Gravity
Gradiometer
Anti-ASAT Space Interdiction Net
Commercial
Applicability
2 2 4 2 2 1 4
Availability 4 4 2 4 3 3 3
Payback 4 5 3 3 3 2 5
Contribution to
4 5 3 3 2 3 5
Air/Space
Superiority
Cost 3 4 2 3 3 3 2
Lethality 5 4 4 3 3 3 5
Selectivity 4 5 3 2 3 3 5
Tech Challenge 4 3 2 5 2 4 3
Total 30 32 23 25 21 22 32](https://image.slidesharecdn.com/vol3ch09-140914105110-phpapp01/85/Vol3ch09-60-320.jpg)