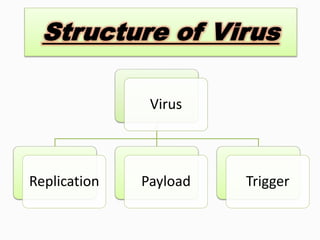
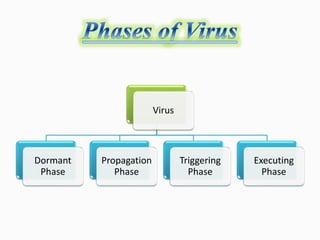
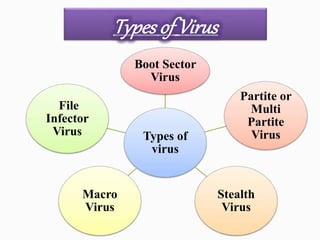
Viruses are computer programs that can replicate themselves and infect computers without permission. They enter systems through email attachments or downloads. Viruses have four components: replication, payload, trigger, and infection mechanism. The payload can damage systems, while the trigger activates the payload under certain conditions. There are different types of viruses like boot sector viruses that infect hard drives, macro viruses that use application code, and file infector viruses that attach to executable files. System updates, firewalls, antivirus software, and caution with email attachments can help combat viruses.