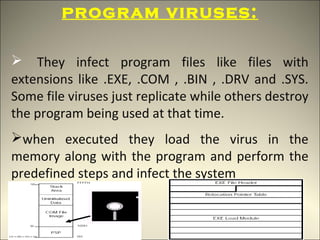
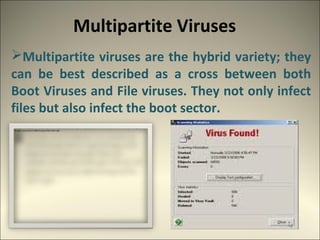
This document discusses computer viruses and malware. It defines different types of viruses like boot viruses, program viruses, polymorphic viruses, stealth viruses, and macro viruses. It also discusses worms, trojan horses, spam, and other types of malware. The document advocates for the potential use of "good viruses" that could help update antivirus software on networks rather than cause harm. It acknowledges the ongoing arms race between viruses and antivirus technology.














![1. The Little Black book of Computer Viruses (electronic
edition) By Mark A. Ludwig
2. An Undetectable Computer Virus by David Chess and Steve
White, presented at the Virus Bulletin Conference,
September 2000 [PDF version]
3. Fred Cohen, Computer Viruses - Theory and Experiments,
Computer Security: A Global Challenge, Elsevier Science
Publishers B. V. (North-Holland), 1984, pp. 143-158.
4. Fred Cohen, Models of Practical Defenses against Computer
Viruses, Computers Security, 8 (1989), 2, pp. 149-160.
5. Nachenberg, C. “Computer Virus-Antivirus Coevolution.”
Communications of the ACM.
6. Computational Aspects of Computer Viruses by Fred Cohen
7. Trends in Computer Virus Research by Fred Cohen
8. Methodology of Computer Anti-Virus Research by Vesselin
Bontchev](https://image.slidesharecdn.com/computerviruses-130205000327-phpapp01/85/Computer-viruses-18-320.jpg)

