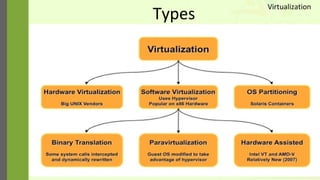
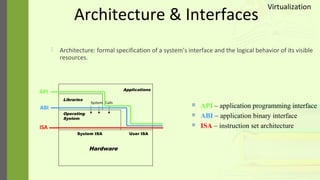
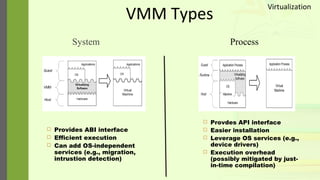
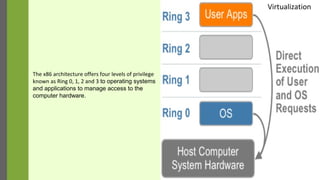
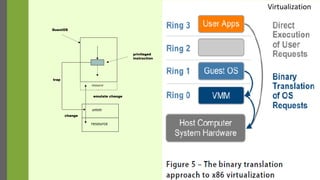
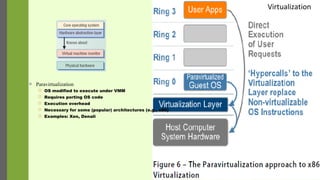
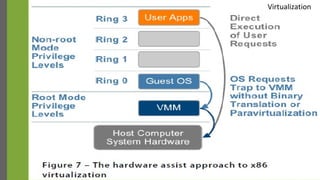
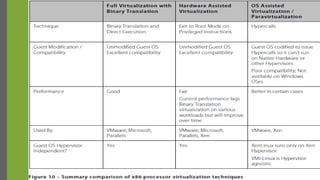
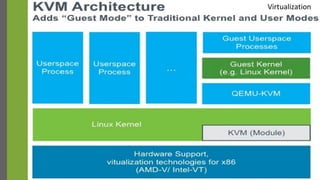
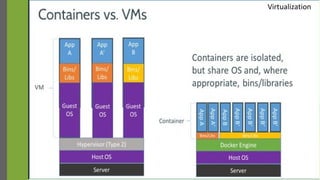
The document discusses virtualization as a method to abstract, replicate, and isolate resources by mapping interfaces and resources between layers. It explains the roles of virtual machine monitors (VMMs), types of virtualization (full and paravirtualization), and the associated instruction types and architecture specifications. Additionally, it covers the x86 architecture's privilege levels and their management for operating systems and applications.