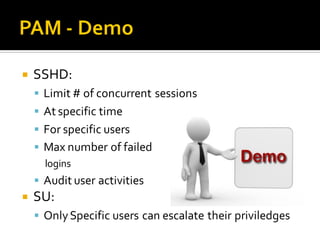
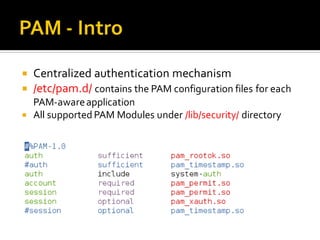
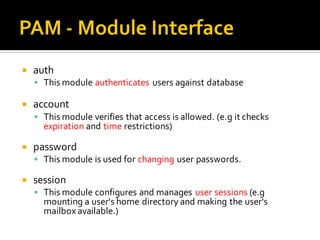
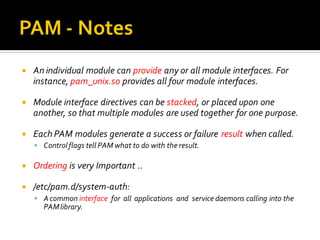
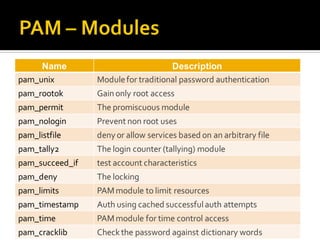
This document discusses Pluggable Authentication Modules (PAM) and how they provide a flexible framework for authentication in Linux systems. PAM allows authentication methods to be configured per application using configuration files in /etc/pam.d. Common PAM modules like pam_unix, pam_rootok, and pam_tally2 are described along with their uses for authentication, authorization, password management, and session control. The document provides examples of configuring PAM for applications like SSHD to implement features like limited login attempts, time-based access restrictions, and auditing of user activities.





![ Test account characteristics ..
Synopsis: pam_succeed_if.so [flag...] [condition...]
Flags:
Conditions:
auth required pam_succeed_if.so use_uiduser ingroup wheel
use_uid
Evaluate conditions using the account of the user whose UID the
application is running under instead of the user being authenticated.
quiet Don´t log failure or success to the system log.
Field Test Value
user ingroup Wheel
uid >= 500](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-11-320.jpg)
![ Authenticate using cached successful authentication
attempts.
Synopsis: pam_timestamp.so[timestamp_timeout=number]
The auth and session module types are provided.
auth sufficient pam_timestamp.so
auth required pam_unix.so
session required pam_unix.so
session optional pam_timestamp.so
/etc/pam.d/wireshark](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-12-320.jpg)

![ Deny or allow using services based on an arbitraryfile
Synopsis:
pam_listfile.soitem=[user|rhost|group|shell]sense=[allow|deny]
file=/path/filename onerr=[succeed|fail]
auth required pam_listfile.soitem=user onerr=fail
file=/etc/ssh.allowsense=allow
item What is listed in the file and should be checked for.
sense Action to take if found in file
onerr What to do if something weird happens like being unable to open the file
/etc/pam.d/sshd](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-14-320.jpg)
![ Enable or disable TTY auditing for specified users.
Synopsis: pam_tty_audit.so[disable=patterns][enable=patterns]
To view the data that was logged by the kernel to audit use
the command #aureport --tty.
session required pam_tty_audit.sodisable=*enable=root
/etc/pam.d/sshd](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-15-320.jpg)
![ The login counter.
Synopsis:
pam_tally2.so[onerr=[fail|succeed]][even_deny_root] [deny=n]
[unlock_time=n][root_unlock_time=n] [audit]
To view the status for locked users run this command
#pam_tally -u username
auth required pam_tally2.so deny=4
even_deny_root unlock_time=1200
/etc/pam.d/sshd](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-16-320.jpg)
![ PAM module to limit resources
Synopsis: pam_limits.so[change_uid][conf=/path/to/limits.conf]
By default limits are taken from the /etc/security/limits.conf
session required pam_limits.so
/etc/pam.d/sshd
<domain> <type> <item> <value>
student - maxlogins 1
/etc/security/limits.conf
CPU
Maxlogin
Priority
Memlock
Hard
Soft
-
Username
@Group
uid:uid
*](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-17-320.jpg)
![ PAM module for time control access
Synopsis: pam_time.so [noaudit]
The time access rules are taken from /etc/security/time.conf
account required pam_time.so
/etc/pam.d/sshd
services; ttys; users; times
sshd; * ; !root ; Wk0800-1700
/etc/security/time.conf
Users
Groups
tty
ttyp*
*
sshd
login](https://image.slidesharecdn.com/pluggableauthenticationmodules-130617103837-phpapp02/85/Pluggable-authentication-modules-18-320.jpg)