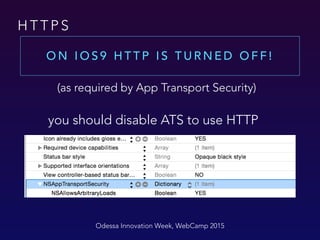
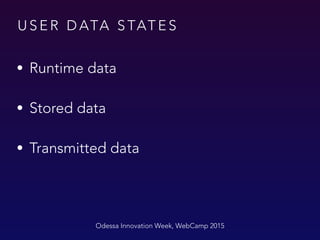
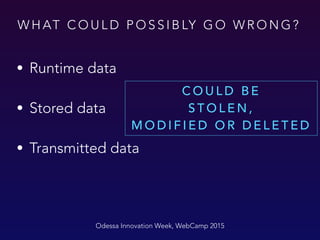
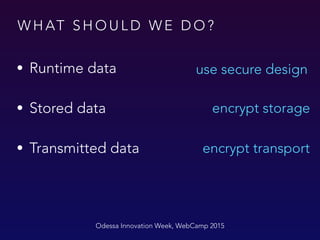
The document outlines best practices for user data security in iOS applications, emphasizing the protection of sensitive data during runtime, storage, and transmission. It recommends encrypting data, using secure design principles, and implementing additional security measures such as password protection and biometric authentication. The importance of not storing sensitive information in plaintext, and the advantages of using keychain and encryption libraries, are also highlighted.




![U I PA S T E B O A R D
• general Pasteboard is open for everyone
Odessa Innovation Week, WebCamp 2015
[[UIPasteboard generalPasteboard] setValue:@"1234 5689 3455 6604"
forPasteboardType:@"card"];
• custom Pasteboards are open for current app and
apps with same team ID
UIPasteboard * pasteboard = [UIPasteboard pasteboardWithName:@"my.app"
create:YES];
pasteboard.persistent = YES;
[pasteboard setValue:@"1234 5689 3455 6604”forPasteboardType:@"card"];](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-8-320.jpg)
![U I PA S T E B O A R D
• prevent copying sensitive data
Odessa Innovation Week, WebCamp 2015
@implementation UITextView (DisableCopyPaste)
- (BOOL)canPerformAction:(SEL)action withSender:(id)sender {
[UIMenuController sharedMenuController].menuVisible = NO;
return NO;
}
@end](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-9-320.jpg)
![S N A P S H O T T I N G & S C R E E N S H O T T I N G
Odessa Innovation Week, WebCamp 2015
- (void)applicationWillResignActive:(UIApplication *)application {
UIImageView * imageView = [[UIImageView alloc]initWithFrame:
[self.window frame]];
[imageView setImage:[UIImage imageNamed:@"mySplash"]];
[self.window addSubview:imageView];
}
• hide any sensitive data before snapshotting
• or set your picture as snapshot
- (void)applicationWillResignActive:(UIApplication *)application {
self.window.rootViewController.view.cardLabel.hidden = YES;
}](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-10-320.jpg)


![T O U C H I D
#import <LocalAuthentication/LocalAuthentication.h>
LAContext * myContext = [LAContext new];
NSError * authError = nil;
NSString * myLocalizedReasonString = @"Authenticate using your
finger";
if ([myContext canEvaluatePolicy:LAPolicyDevice
OwnerAuthenticationWithBiometrics error:&authError]) {
...
} else {
NSLog(@"Authentication error %@", authError);
}
Odessa Innovation Week, WebCamp 2015](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-13-320.jpg)
![T O U C H I D
[myContext evaluatePolicy:
LAPolicyDeviceOwnerAuthenticationWithBiometrics
localizedReason:myLocalizedReasonString
reply:^(BOOL success, NSError * error) {
if (success) {
NSLog(@"User is authenticated successfully”);
} else {
NSLog(@"Authentication failed with error %@", error);
}
}];
Odessa Innovation Week, WebCamp 2015](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-14-320.jpg)
![T O U C H I D
switch (error.code) {
case LAErrorAuthenticationFailed:
NSLog(@"Authentication Failed");
break;
case LAErrorUserCancel:
NSLog(@"User pressed Cancel button");
break;
case LAErrorUserFallback:
NSLog(@"User pressed "Enter Password"");
[self showPassword];
break;
default:
NSLog(@"Touch ID is not configured");
[self showPassword];
break;
}
Odessa Innovation Week, WebCamp 2015](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-15-320.jpg)


![P L A I N T E X T K E Y S A R E B A D
Odessa Innovation Week, WebCamp 2015
[Parse setApplicationId:@"GpvoqI7Ut29H...2JL1dyceOv0hV1"
clientKey:@“sv8wcfIf0neo...y2m9YIwu0OxQr”];
static NSString *kMyAPIKey = @"mySecretApiKey";](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-18-320.jpg)

![P L A I N T E X T K E Y S A R E B A D
Odessa Innovation Week, WebCamp 2015
GpvoqI7Ut29...2JL1dyceOv0hV1
sv8wcfIf0neo...y2m9YIwu0OxQr
application did finish launching
window
T@"UIWindow",&,N
T@"UIWindow",&,N,V_window
[Parse setApplicationId:@"GpvoqI7Ut29H...2JL1dyceOv0hV1"
clientKey:@“sv8wcfIf0neo...y2m9YIwu0OxQr”];
static NSString *kMyAPIKey = @"mySecretApiKey";](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-20-320.jpg)
![AV O I D P L A I N T E X T K E Y S
• store like hex strings
Odessa Innovation Week, WebCamp 2015
unsigned char myApiKey[] = { 0xAB, 0xAA, 0xBE, 0xDE, 0xEF };
• obfuscate
NSString * key = [NSString stringWithFormat:@"%@%@%@%@", @"my",
@"secret", @"Api", @“Key"];
NSString * key = [NSString stringWithFormat:@"%3$@%2$@%1$@%4$@",
@"Api", @"secret", @"my", @"Key"];
NSString * format = [[[@"x3$yx2$z%1$yx4$@"
stringByReplacingOccurrencesOfString:@"x" withString:@"%"]
stringByReplacingOccurrencesOfString:@"y" withString:@"@"]
stringByReplacingOccurrencesOfString:@"z" withString:@"@"];
NSString * key = [NSString stringWithFormat:format, @"Api",
@"secret", @"my", @"Key"];
"mySecretApiKey"](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-21-320.jpg)
![U S E E N C RY P T E D K E Y S
1. take key in plain text
Odessa Innovation Week, WebCamp 2015
static NSString *kMyAPIKey = @"mySecretApiKey";
NSData * encryptedData = [RNEncryptor encryptData:kMyAPIKey
withSettings:kRNCryptorAES256Settings
password:[self calculatePassword]
error:&error];
NSString * resultString = [[NSString alloc] initWithData:encryptedData
encoding:NSUTF8StringEncoding];
2. encrypt it](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-22-320.jpg)
![U S E E N C RY P T E D K E Y S
3. hardcode encrypted key
Odessa Innovation Week, WebCamp 2015
static NSString *kMyAPIKeyEncrypted =
@“789fae43c3e66113e48cebfafeef6806542c0c9062b78b686f515acb0
9b2c0a6";
NSData *decryptedData = [RNDecryptor decryptData:encryptedData
withPassword:[self calculatePassword]
error:&error];
NSString * resultString = [[NSString alloc] initWithData:encryptedData
encoding:NSUTF8StringEncoding];
4. decrypt it before using](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-23-320.jpg)
![U S E E N C RY P T E D K E Y S
5. use generated password, not static string
Odessa Innovation Week, WebCamp 2015
- (NSString * )calculatePassword {
CGFloat result = (CGFloat) (1.0/23.0);
return [NSString stringWithFormat:@"%.10f", result];
}
@“0.0434782609” this password is calculated each time;
is not stored as string](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-24-320.jpg)



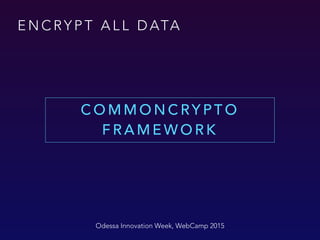
![E N C RY P T A L L D ATA
#import <CommonCrypto/CommonCryptor.h>
- (NSData *)AES256EncryptWithKey:(NSString*)key {
char keyPtr[kCCKeySizeAES256 + 1]; // room for terminator (unused)
bzero(keyPtr, sizeof(keyPtr)); // fill with zeroes (for padding)
[key getCString:keyPtr maxLength:sizeof(keyPtr) encoding:NSUTF8StringEncoding];
NSUInteger dataLength = [self length];
size_t bufferSize = dataLength + kCCBlockSizeAES128;
void* buffer = malloc(bufferSize);
size_t numBytesEncrypted = 0;
CCCryptorStatus cryptStatus = CCCrypt(kCCEncrypt, kCCAlgorithmAES128,
kCCOptionPKCS7Padding,
keyPtr, kCCKeySizeAES256,
NULL
[self bytes], dataLength, /* input */
buffer, bufferSize, /* output */
&numBytesEncrypted);
if (cryptStatus == kCCSuccess) {
//the returned NSData takes ownership of the buffer and will free it on deallocation
return [NSData dataWithBytesNoCopy:buffer length:numBytesEncrypted];
}
free(buffer);
return nil;
}
Odessa Innovation Week, WebCamp 2015
C O M M O N C RY P T O](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-29-320.jpg)
![E N C RY P T A L L D ATA
#import <CommonCrypto/CommonCryptor.h>
- (NSData *)AES256EncryptWithKey:(NSString*)key {
char keyPtr[kCCKeySizeAES256 + 1]; // room for terminator (unused)
bzero(keyPtr, sizeof(keyPtr)); // fill with zeroes (for padding)
[key getCString:keyPtr maxLength:sizeof(keyPtr) encoding:NSUTF8StringEncoding];
NSUInteger dataLength = [self length];
size_t bufferSize = dataLength + kCCBlockSizeAES128;
void* buffer = malloc(bufferSize);
size_t numBytesEncrypted = 0;
CCCryptorStatus cryptStatus = CCCrypt(kCCEncrypt, kCCAlgorithmAES128,
kCCOptionPKCS7Padding,
keyPtr, kCCKeySizeAES256,
NULL
[self bytes], dataLength, /* input */
buffer, bufferSize, /* output */
&numBytesEncrypted);
if (cryptStatus == kCCSuccess) {
//the returned NSData takes ownership of the buffer and will free it on deallocation
return [NSData dataWithBytesNoCopy:buffer length:numBytesEncrypted];
}
free(buffer);
return nil;
}
Odessa Innovation Week, WebCamp 2015
C O M M O N C RY P T O](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-30-320.jpg)
![E N C RY P T A L L D ATA
#import <RNCryptor/RNCryptor.h>
NSData *data = [@"Data" dataUsingEncoding:NSUTF8StringEncoding];
NSError *error;
NSData *encryptedData = [RNEncryptor encryptData:data
withSettings:kRNCryptorAES256Settings
password:aPassword
error:&error];
NSData *decryptedData = [RNDecryptor decryptData:encryptedData
withPassword:aPassword
error:&error];
Odessa Innovation Week, WebCamp 2015
https://github.com/RNCryptor/RNCryptor
U S E W R A P P E R S](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-31-320.jpg)
![E N C RY P T A L L D ATA
#import "scell_seal.h"
NSData *data = [@"Data" dataUsingEncoding:NSUTF8StringEncoding];
TSCellSeal * cellSeal = [[TSCellSeal alloc] initWithKey:masterKeyData];
NSData * encryptedMessage = [cellSeal wrapData:data
context:nil
error:&error];
NSData * decryptedMessage = [cellSeal unwrapData:encryptedMessage
context:nil
error:&error];
Odessa Innovation Week, WebCamp 2015
https://github.com/cossacklabs/themis
U S E C O O L
L I B R A R I E S](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-32-320.jpg)

![Odessa Innovation Week, WebCamp 2015
NSFileManager * fileManager = [NSFileManager defaultManager];
NSDictionary * attributes = @{ NSFileProtectionKey :
NSFileProtectionComplete };
[fileManager createFileAtPath:path
contents:data
attributes:attributes];
[fileManager setAttributes:attributes
ofItemAtPath:path
error:&errorFolderProtect];
F I L E S P R O T E C T I O N](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-36-320.jpg)
![Odessa Innovation Week, WebCamp 2015
[SSKeychain setPassword:password
forService:@"com.my.app"
account:@"MyAppUserPasswordKey"];
S E C U R E K E Y C H A I N
https://github.com/soffes/sskeychain
S E C U R I T Y F R A M E W O R K O R U S E W R A P P E R S](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-37-320.jpg)
![D I S A B L E D E B U G G I N G Y O U R A P P S
Odessa Innovation Week, WebCamp 2015
typedef int (*ptrace_ptr_t)(int _request, pid_t _pid, caddr_t _addr, int _data);
#if !defined(PT_DENY_ATTACH)
#define PT_DENY_ATTACH 31
#endif
void disable_gdb() {
void* handle = dlopen(0, RTLD_GLOBAL | RTLD_NOW);
ptrace_ptr_t ptrace_ptr = dlsym(handle, "ptrace");
ptrace_ptr(PT_DENY_ATTACH, 0, 0, 0);
dlclose(handle);
}
int main(int argc, char * argv[]) {
#if !(DEBUG) // Don't interfere with Xcode debugging sessions.
disable_gdb();
#endif
@autoreleasepool {
return UIApplicationMain(argc, argv, nil, NSStringFromClass([AppDelegate
class]));
}
} https://www.theiphonewiki.com/wiki/Bugging_Debuggers](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-38-320.jpg)





![U S I N G H T T P S : B A D P R A C T I C E S
• allowing self-signed certificates
Odessa Innovation Week, WebCamp 2015
- (void)connection:(NSURLConnection *)connection
didReceiveAuthenticationChallenge:(NSURLAuthenticationChallenge *)challenge {
[challenge.sender continueWithoutCredentialForAuthenticationChallenge:challenge];
}
[AFSecurityPolicy setAllowInvalidCertificates:YES];
[AFSecurityPolicy setValidatesDomainName:NO];
• allowing invalid certificates](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-44-320.jpg)
![U S I N G H T T P S : B A D P R A C T I C E S
• allowing self-signed certificates
Odessa Innovation Week, WebCamp 2015
- (void)connection:(NSURLConnection *)connection
didReceiveAuthenticationChallenge:(NSURLAuthenticationChallenge *)challenge {
[challenge.sender continueWithoutCredentialForAuthenticationChallenge:challenge];
}
[AFSecurityPolicy setAllowInvalidCertificates:YES];
[AFSecurityPolicy setValidatesDomainName:NO];
• allowing invalid certificates
A F N E T W O R K I N G B U G S 2 . 5 . 1 - 2 . 5 . 2](https://image.slidesharecdn.com/usersdatasecurity-150715110701-lva1-app6892/85/Users-Data-Security-in-iOS-Applications-45-320.jpg)