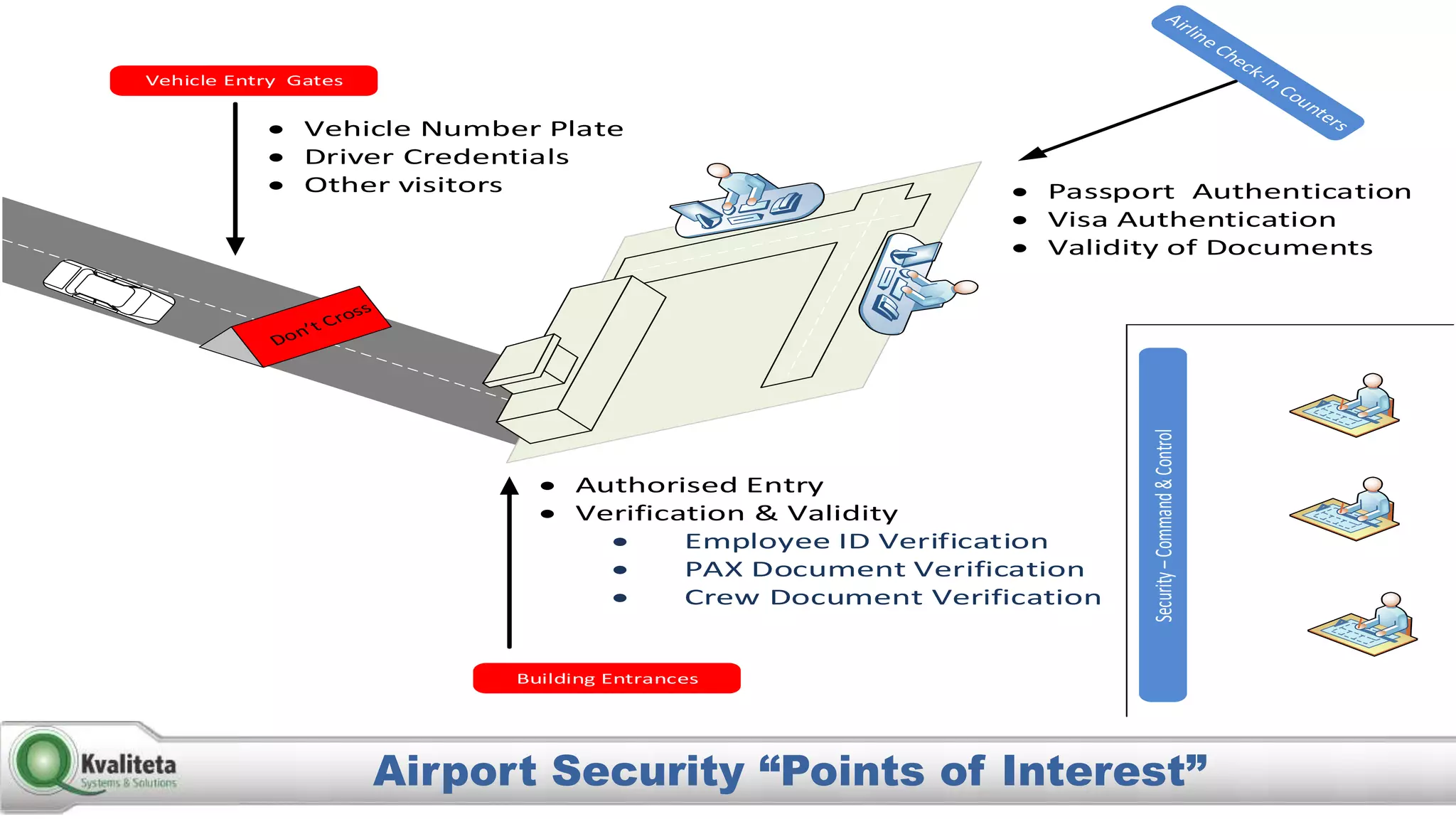
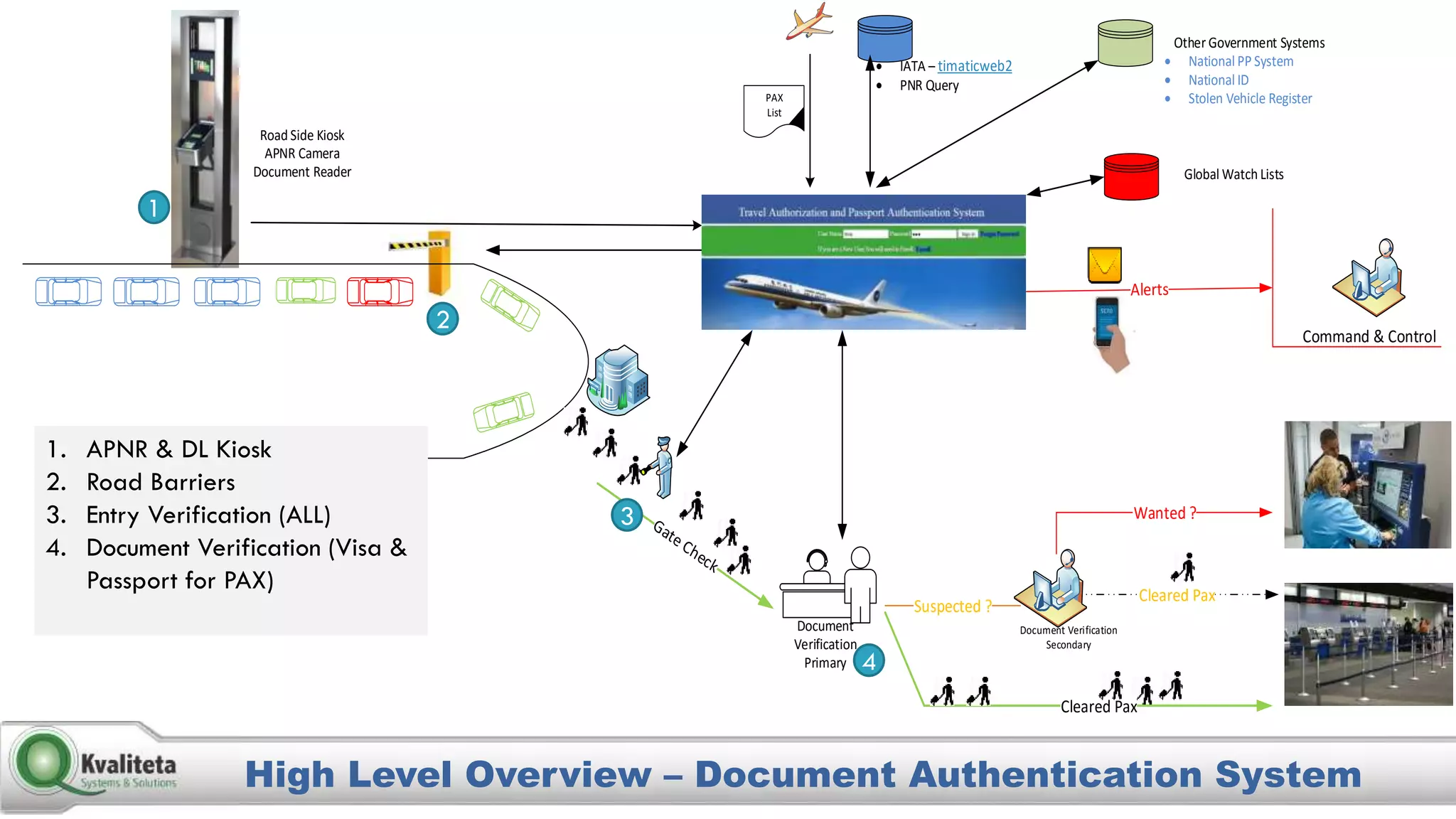
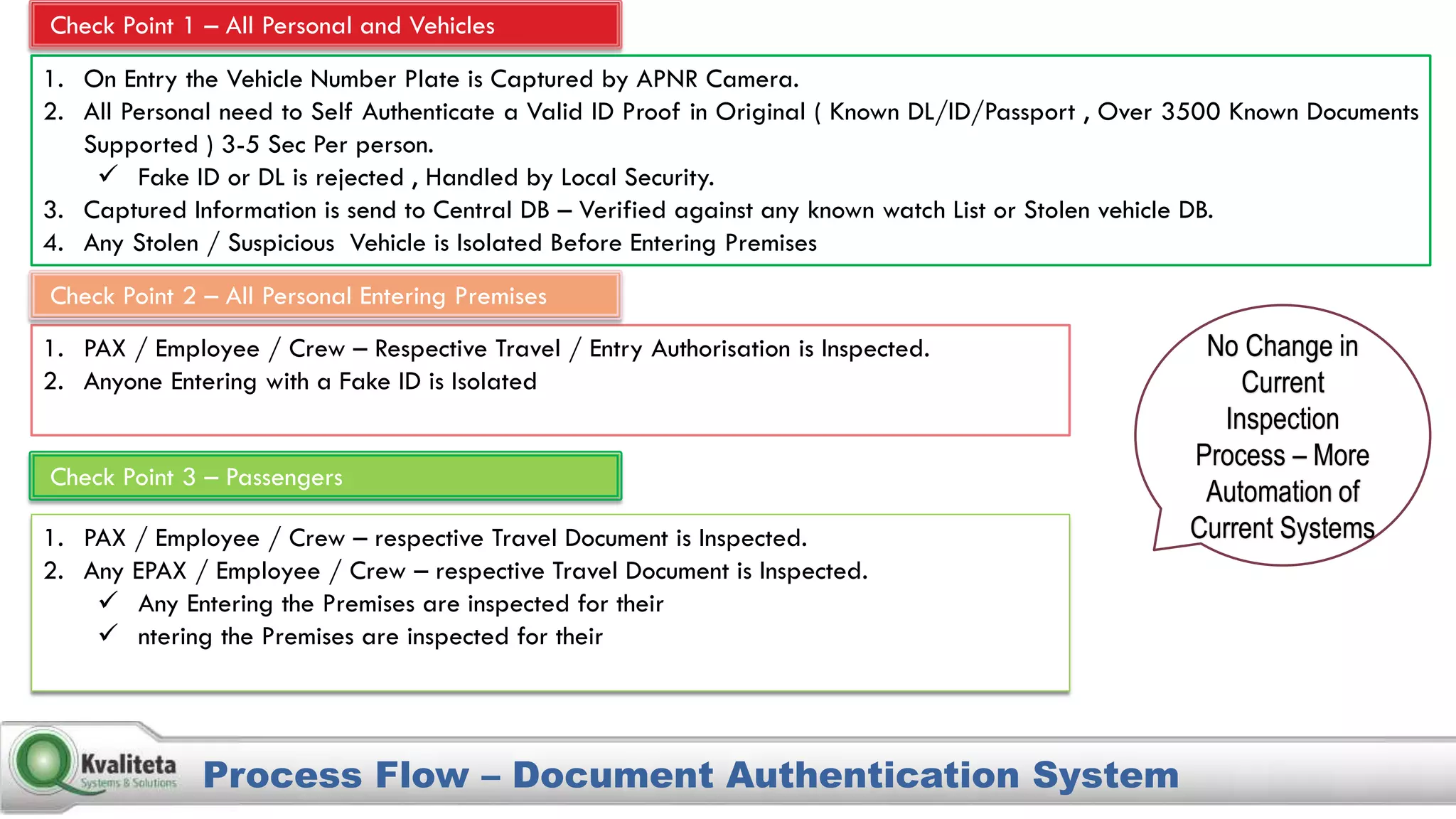
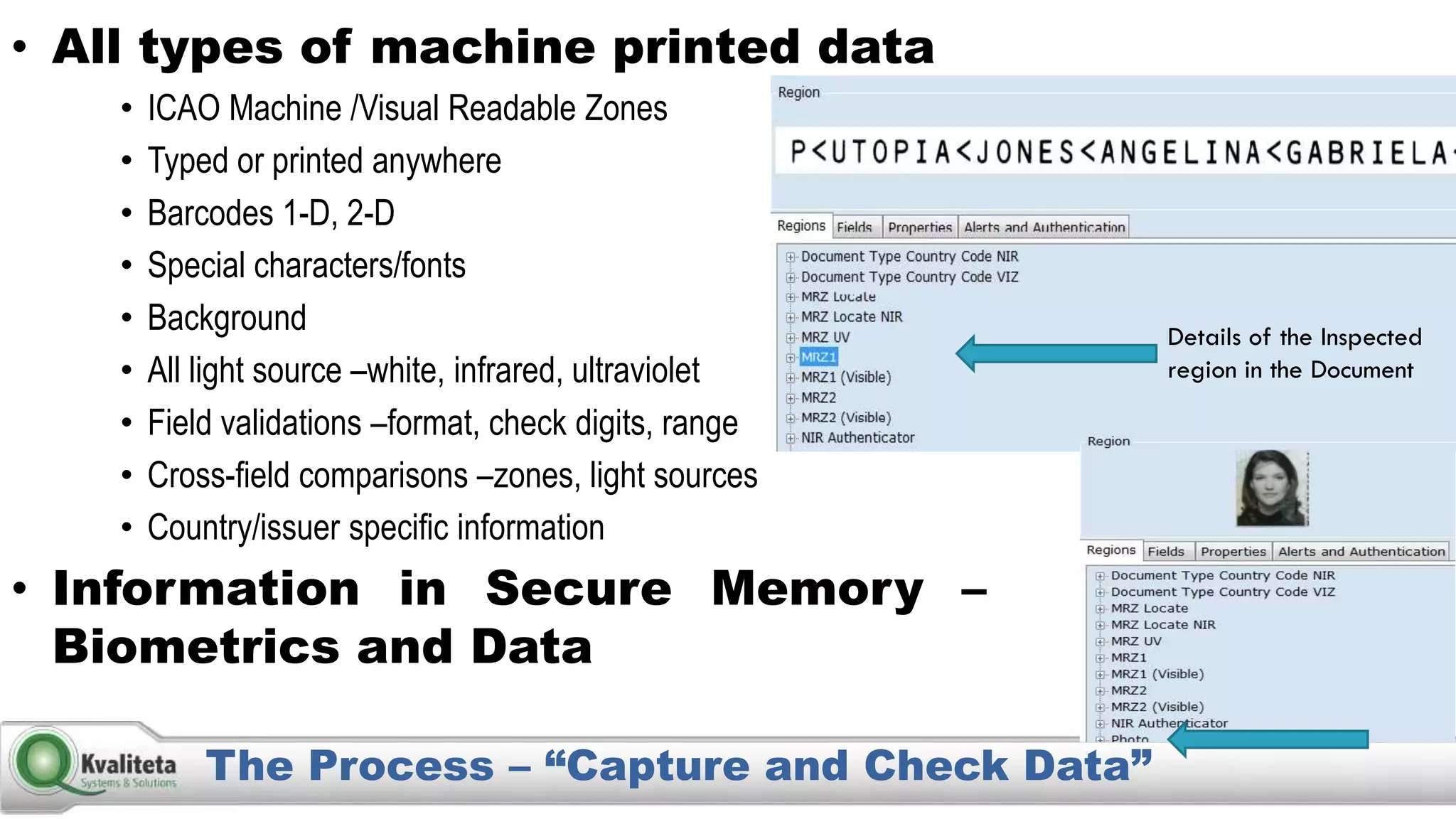
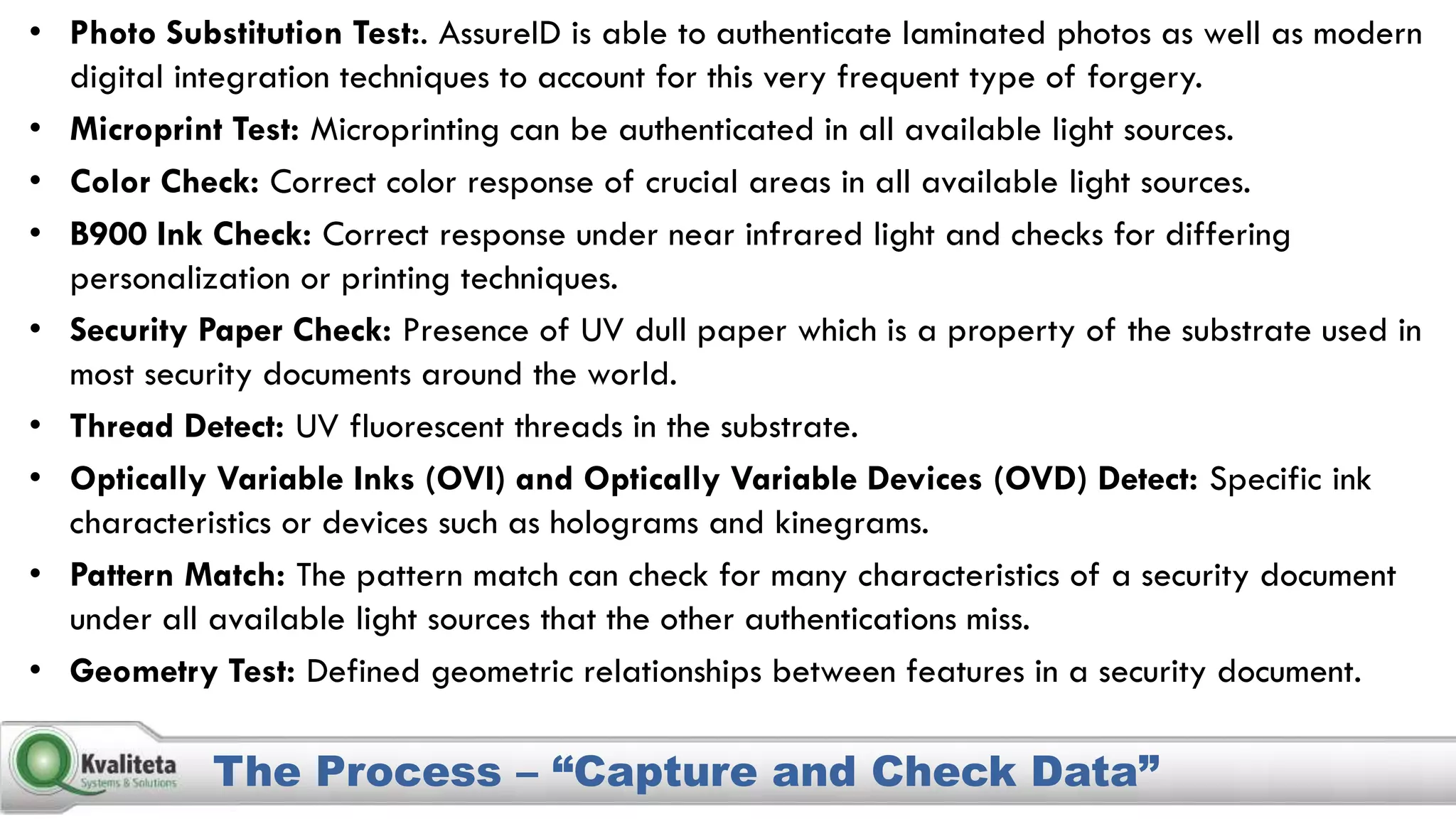
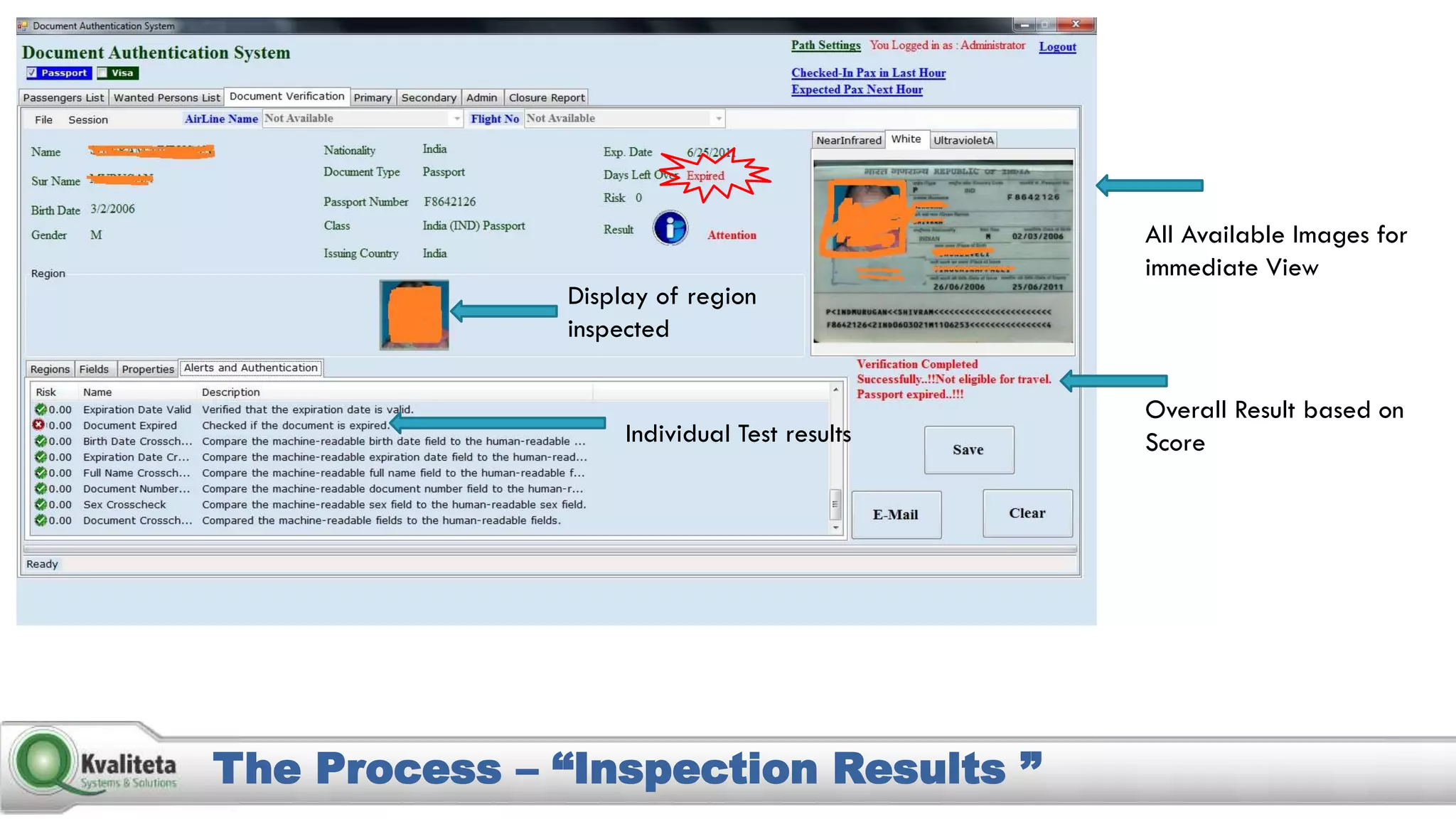
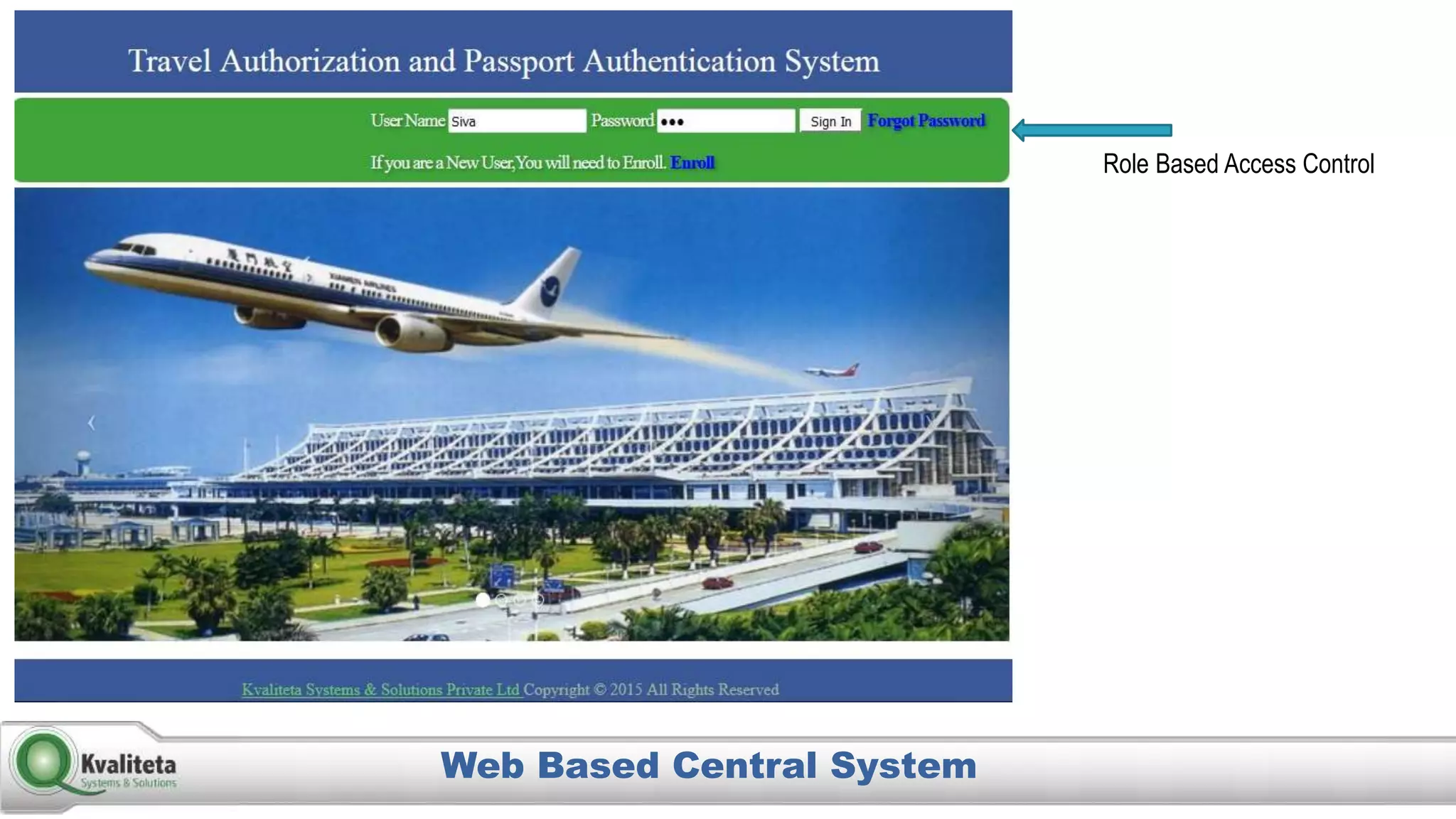
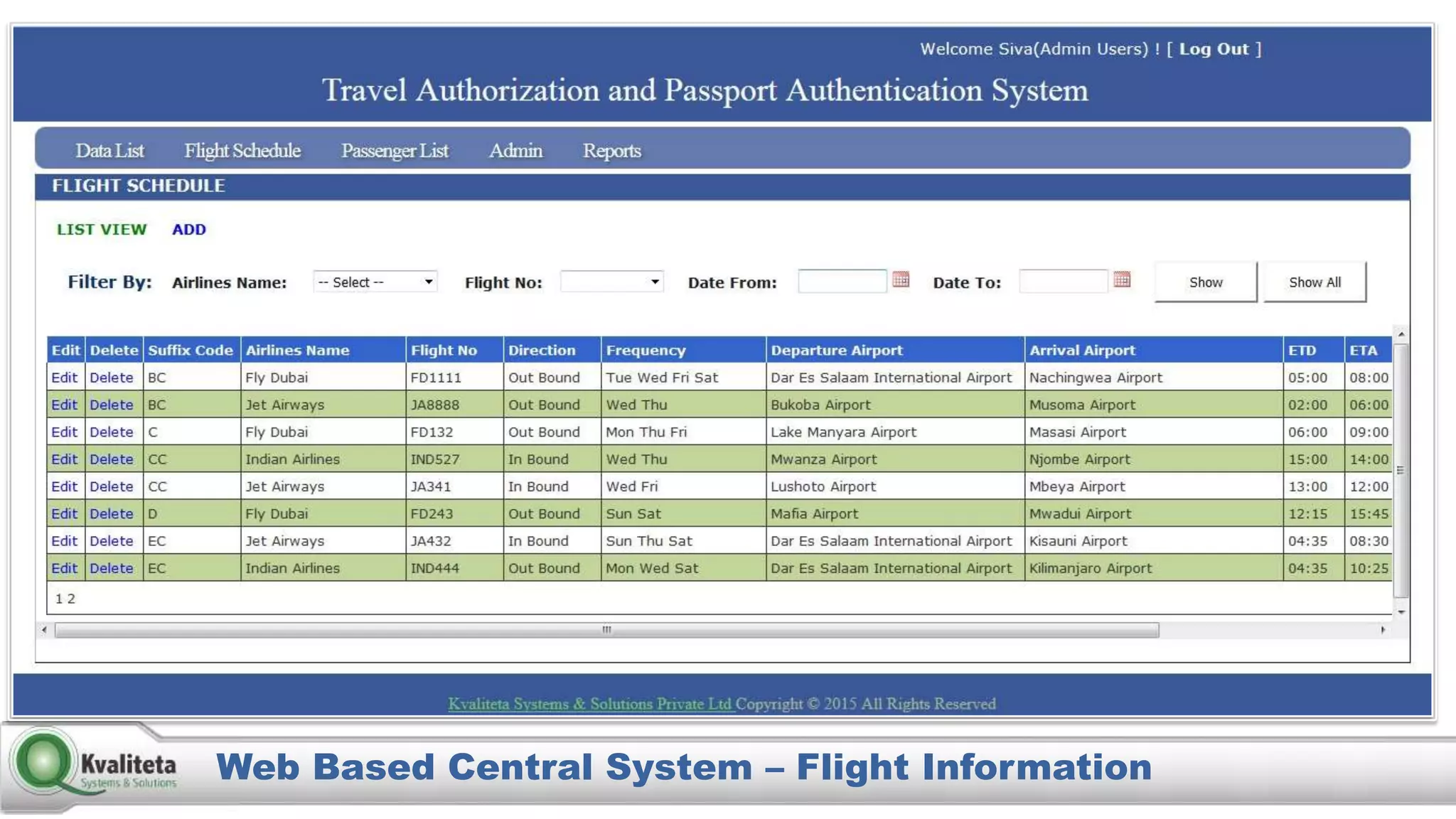
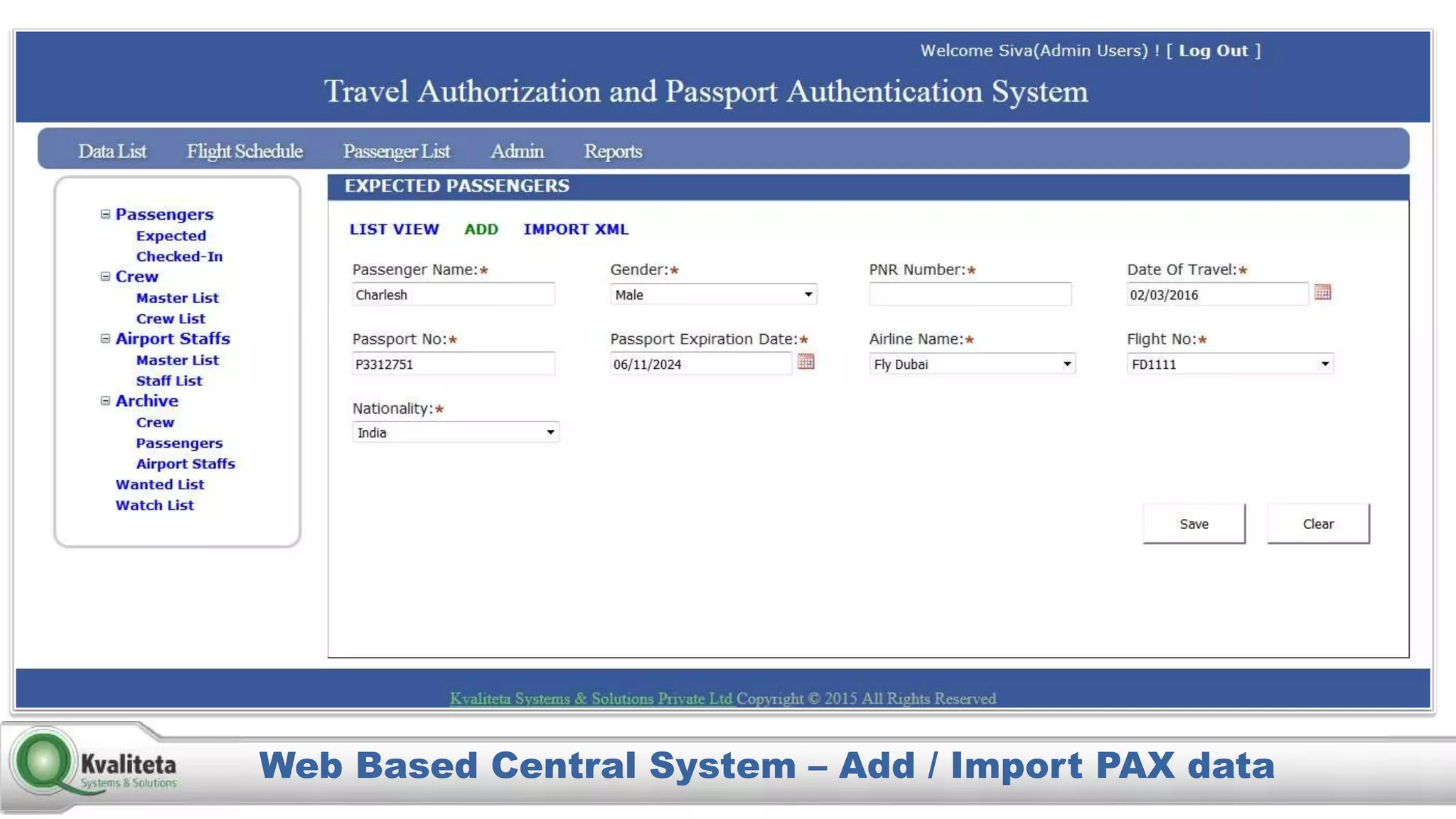
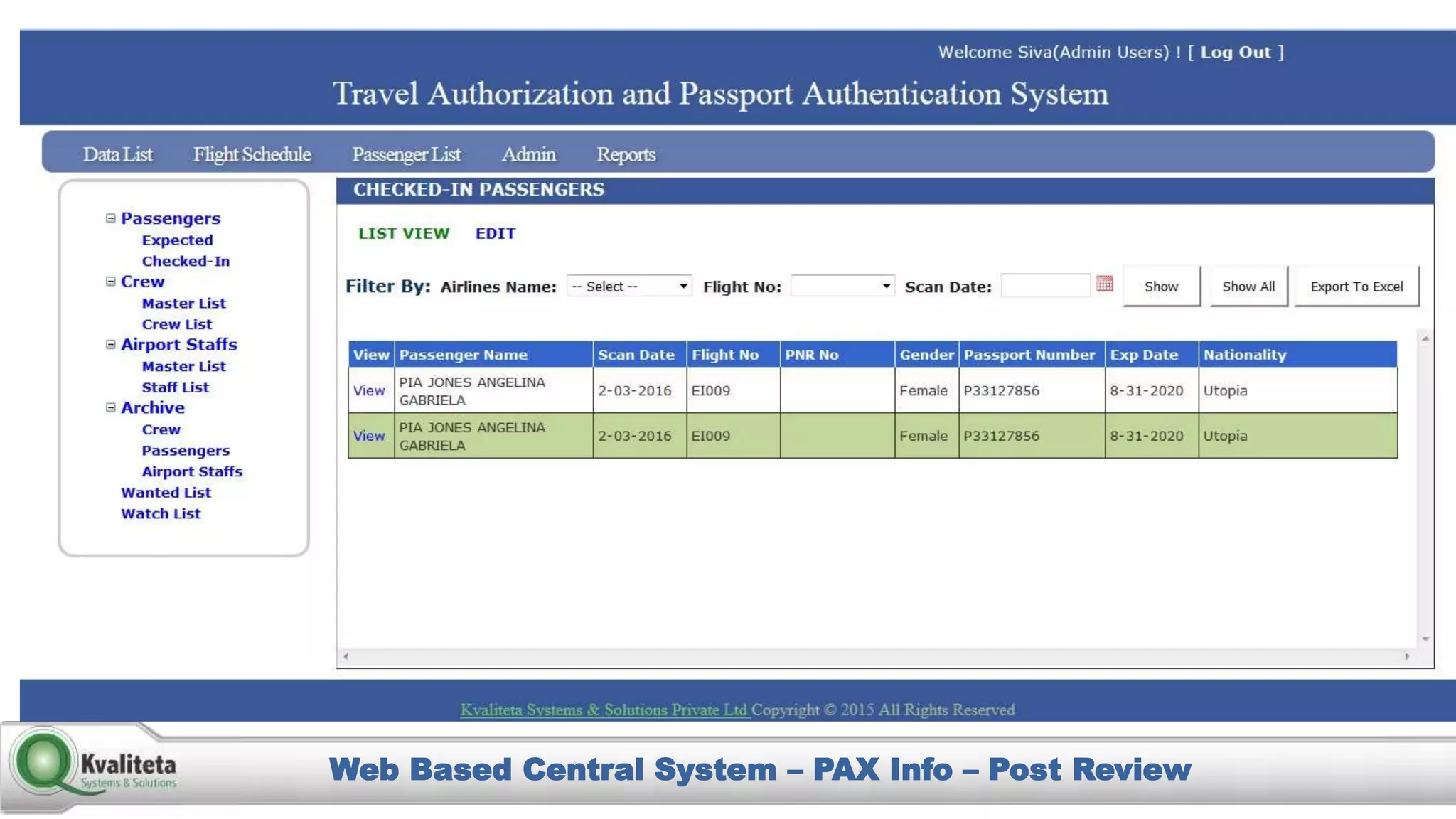
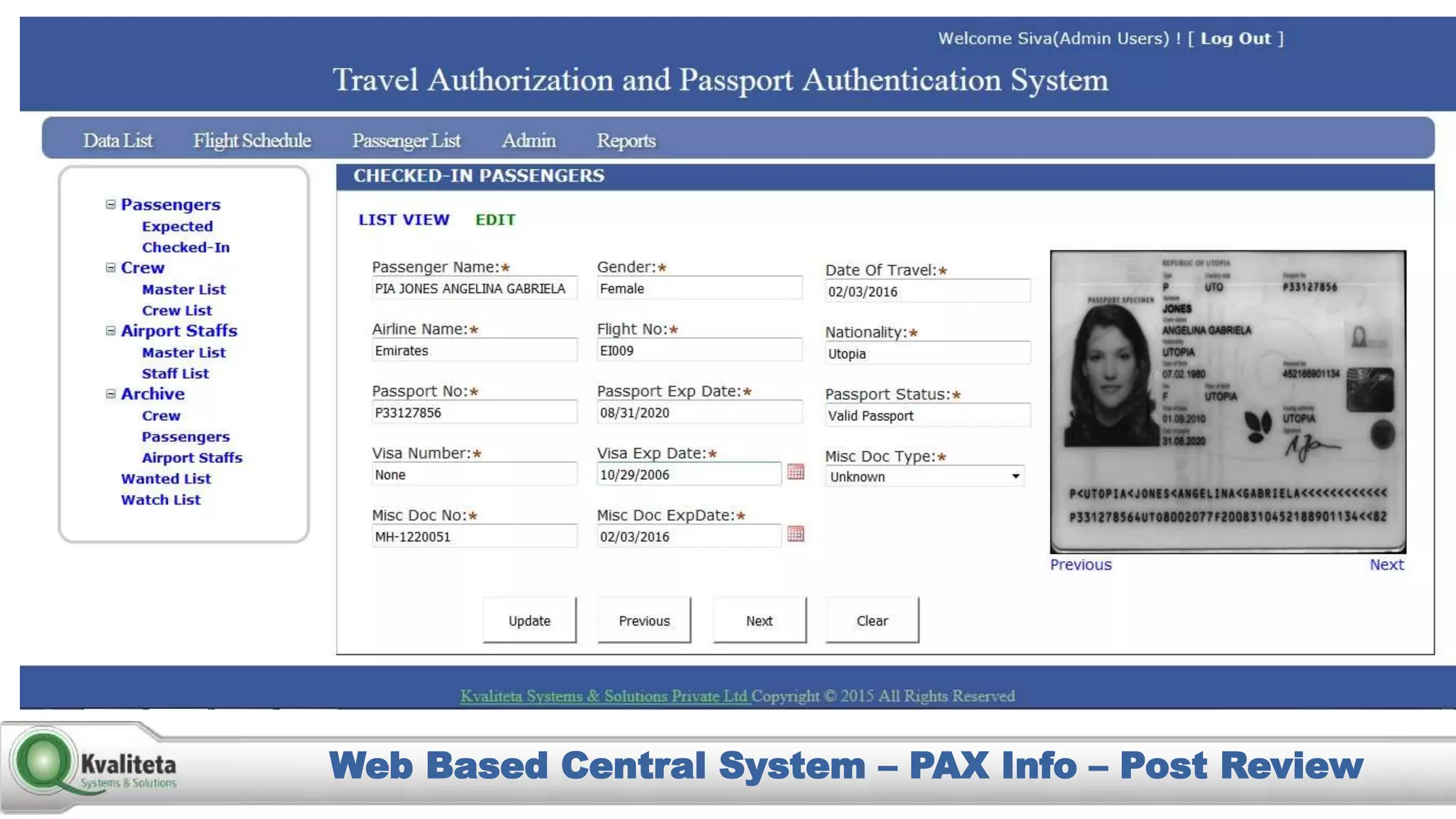
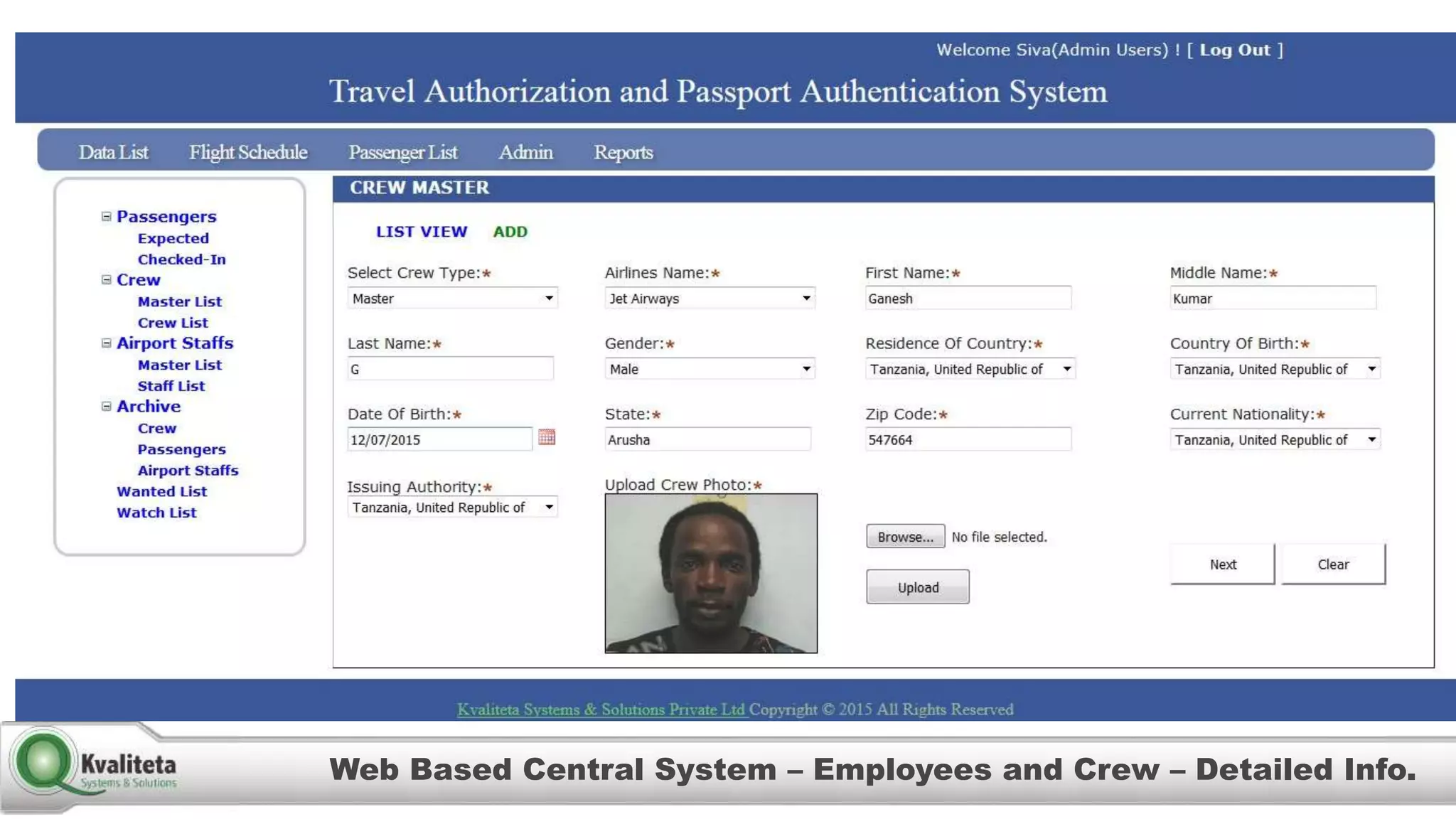
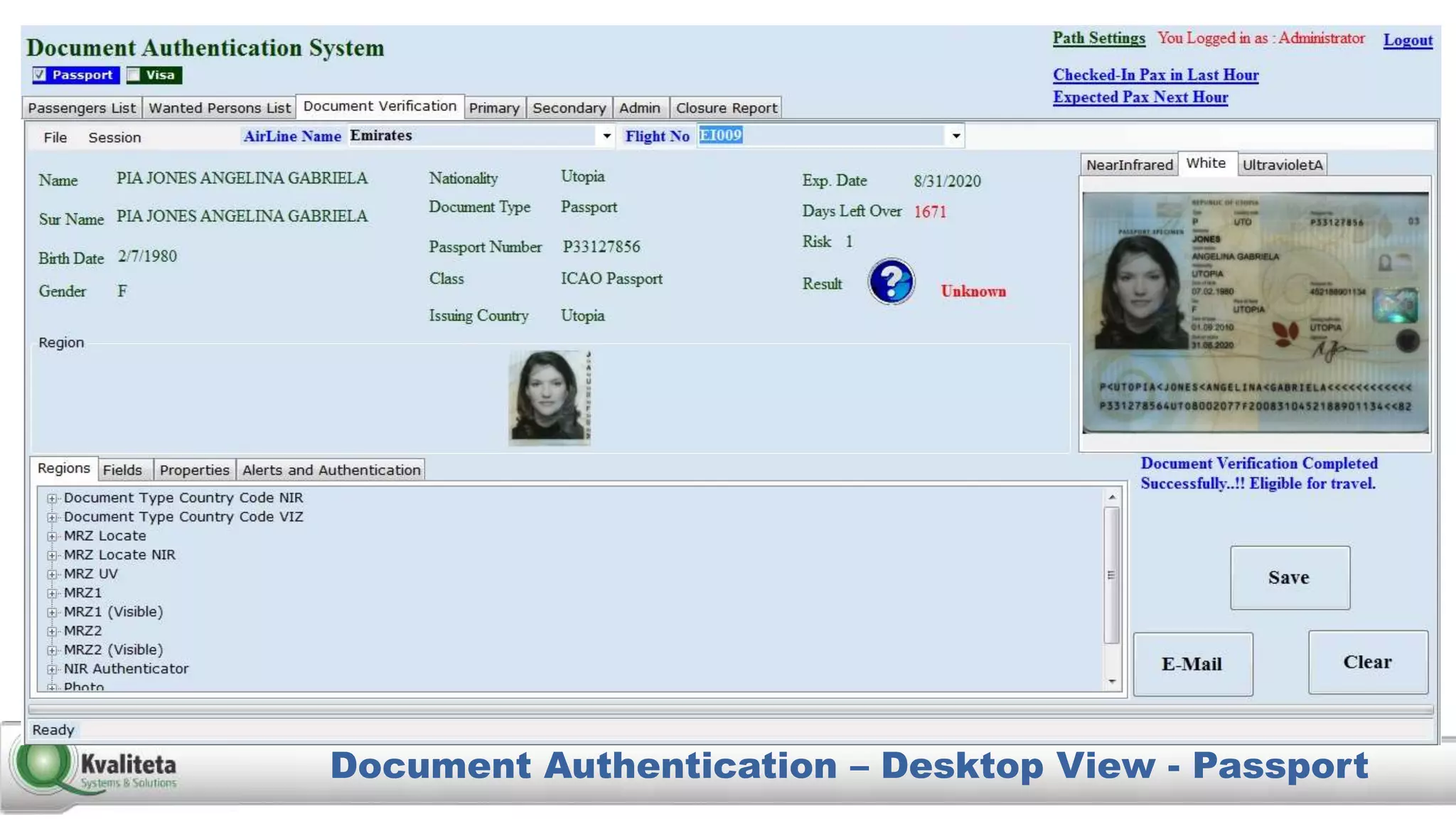
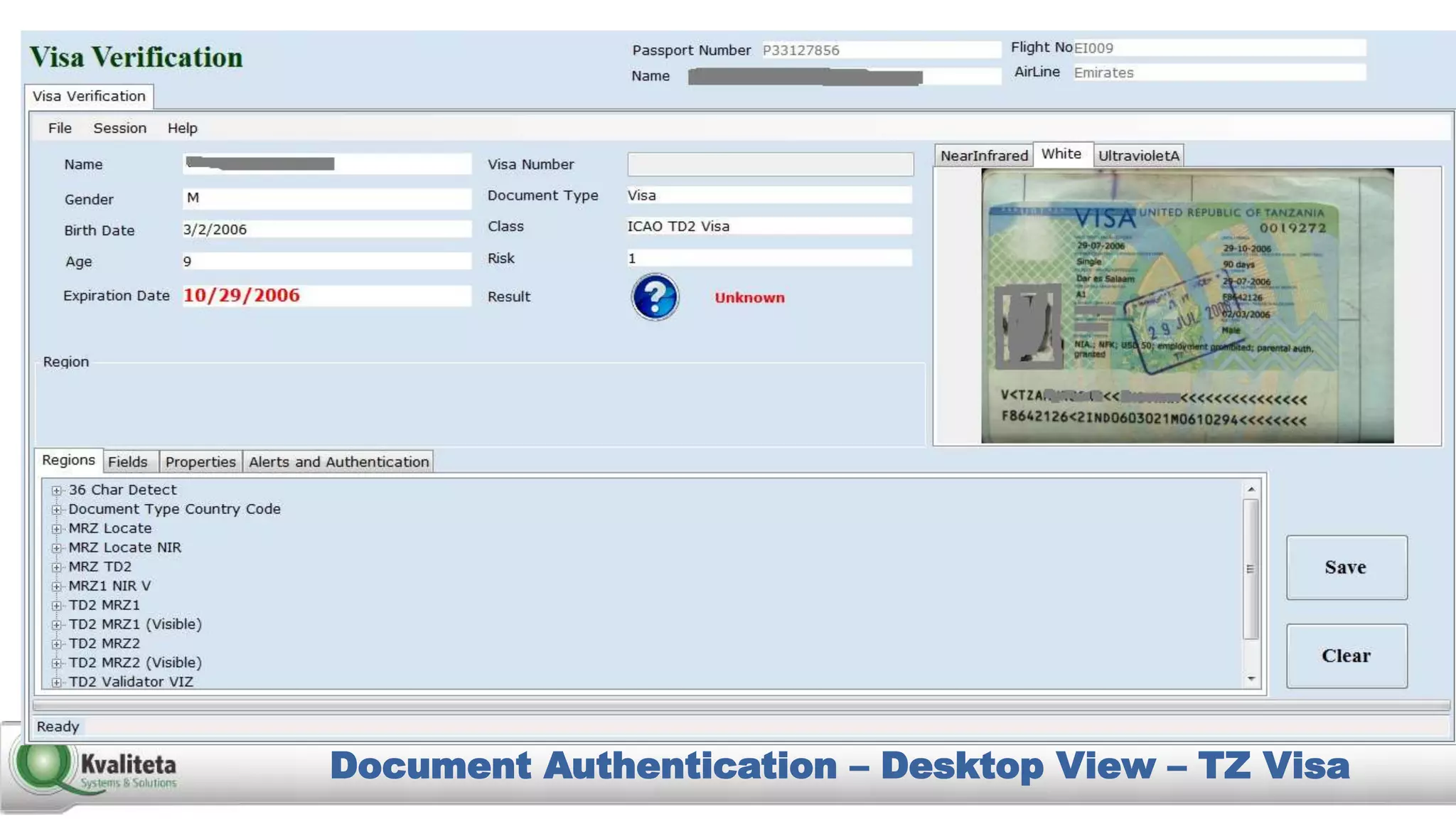
Kvaliteta Systems and Solutions provides a comprehensive document authentication system to enhance security and efficiency in travel-related processes across multiple global locations. The system employs advanced technology to detect fraudulent or altered identification and improve collaboration among airport security, immigration, and airlines. Objectives include increased security, reduced processing time, and automation of document inspections for travelers and personnel.