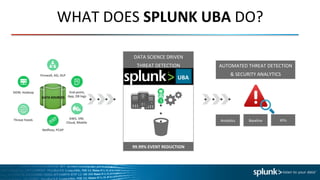
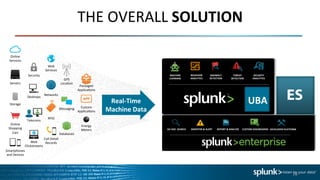
The document discusses Splunk User Behavior Analytics (UBA) and its capabilities for detecting advanced cyber attacks and insider threats through behavioral threat detection using machine learning. It notes that traditional threat detection focuses only on known threats, while UBA aims to detect unknown threats through automated security analytics and anomaly detection based on establishing user and entity baselines and identifying deviations from normal behavior. The document provides examples of UBA use cases and the types of data sources it can integrate to perform threat detection and security analytics.