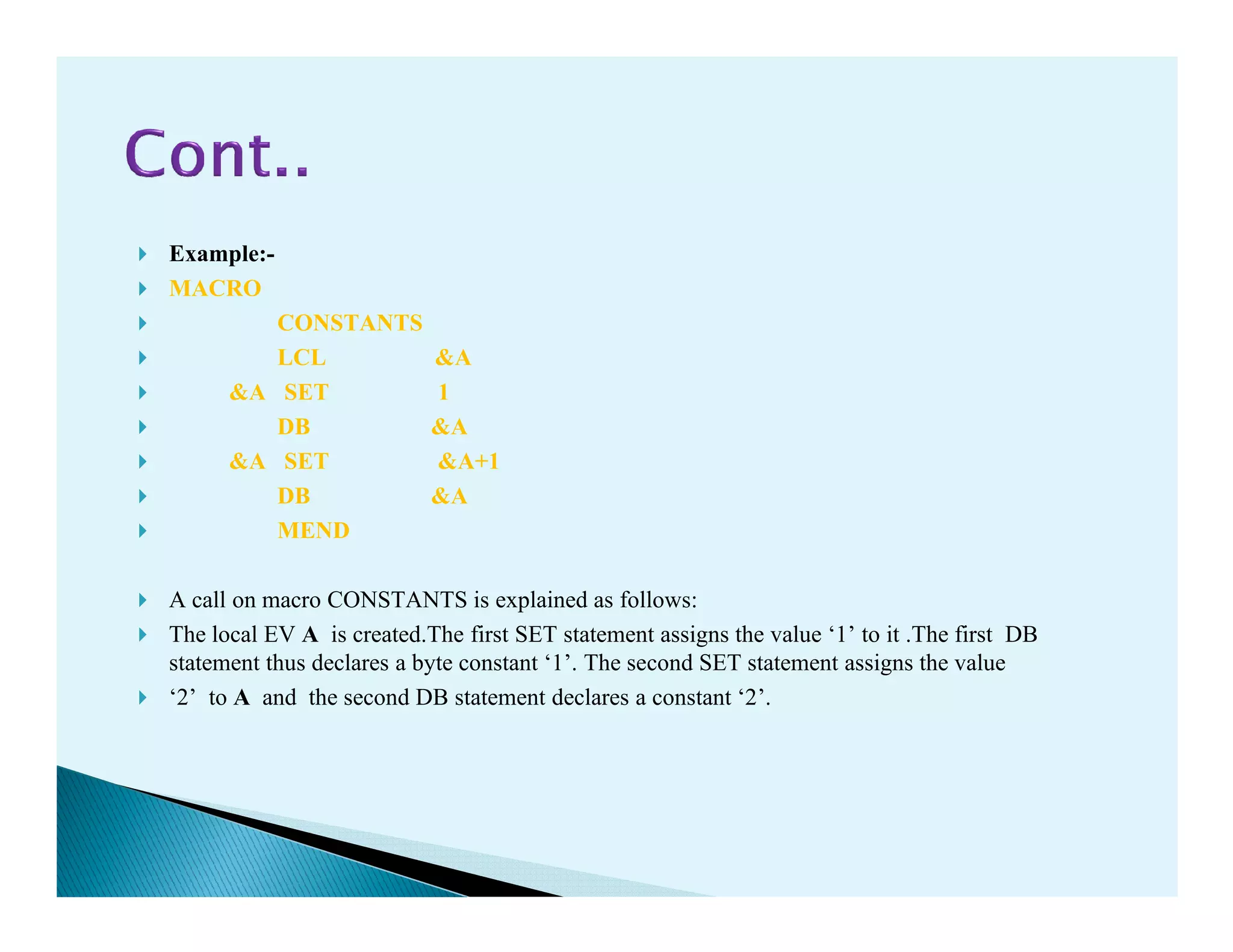
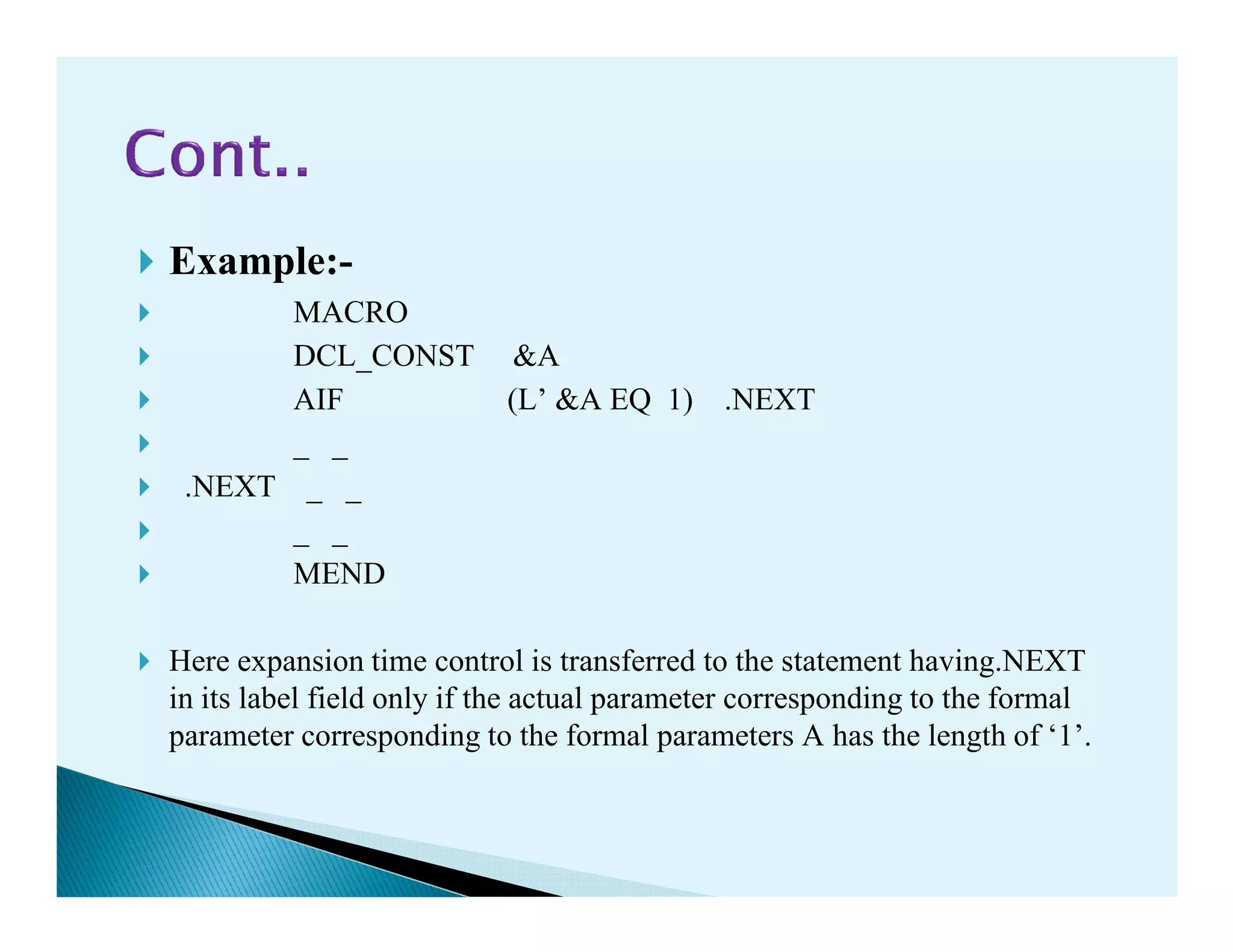
The document discusses macro processors, compilers, and interpreters. It provides details on:
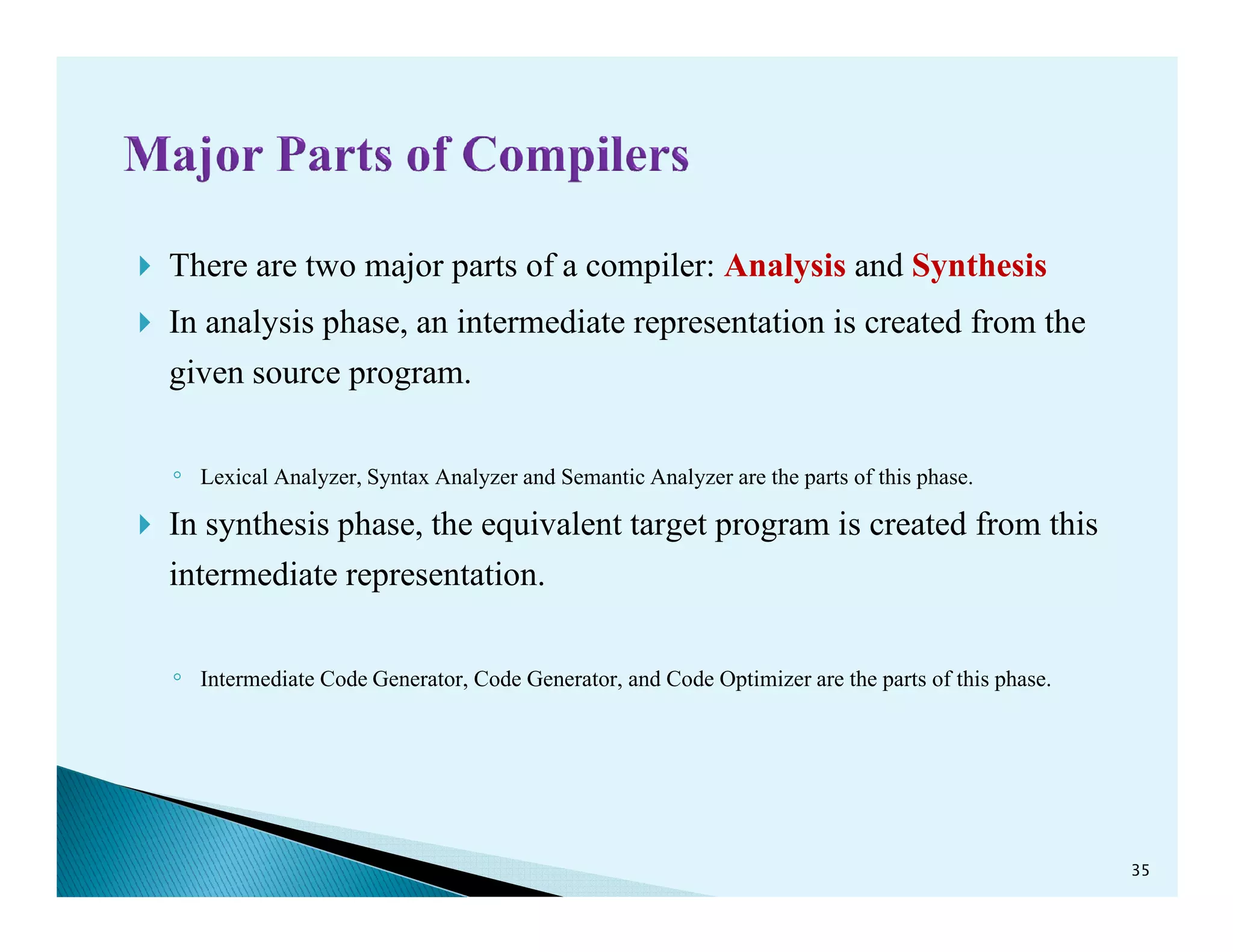
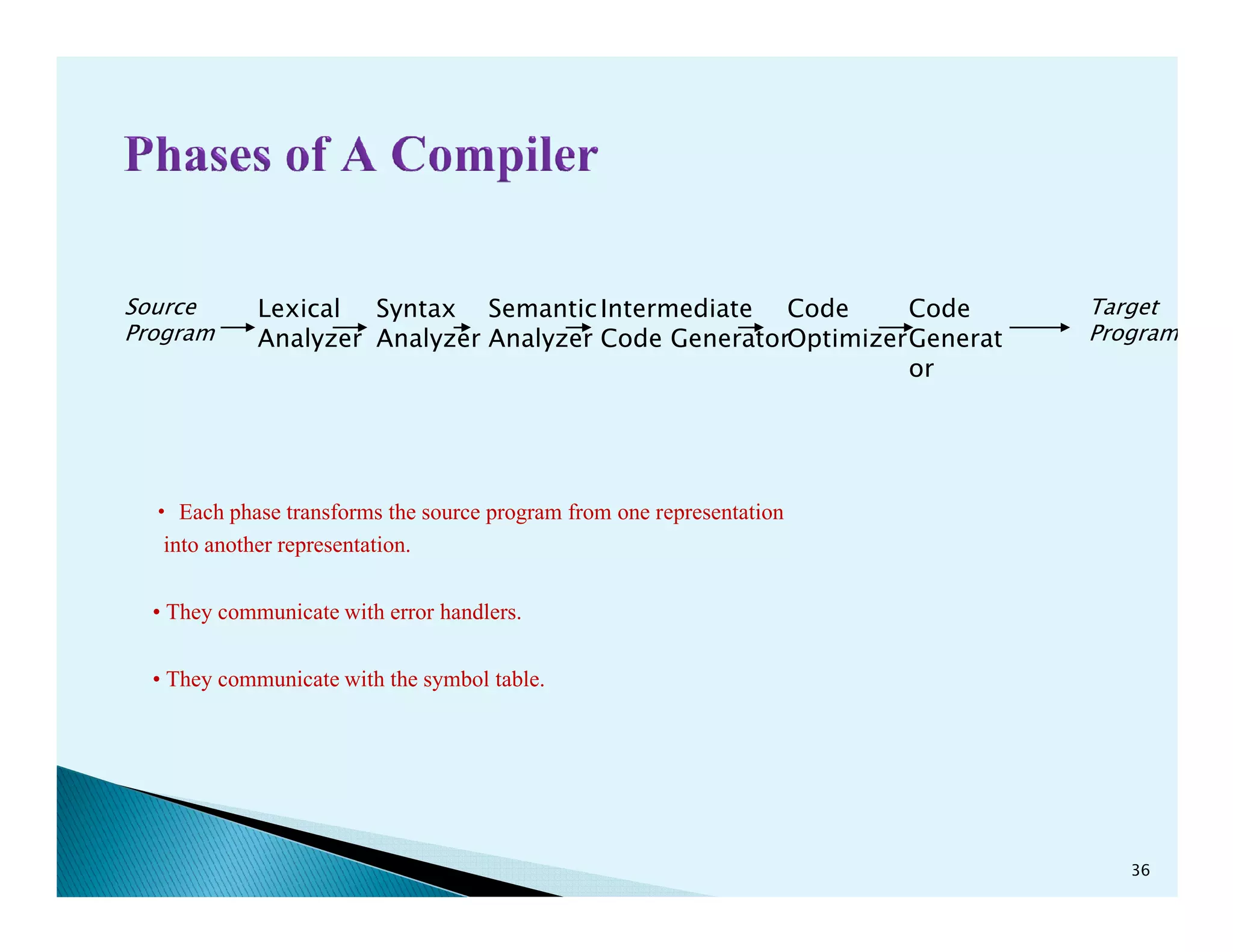
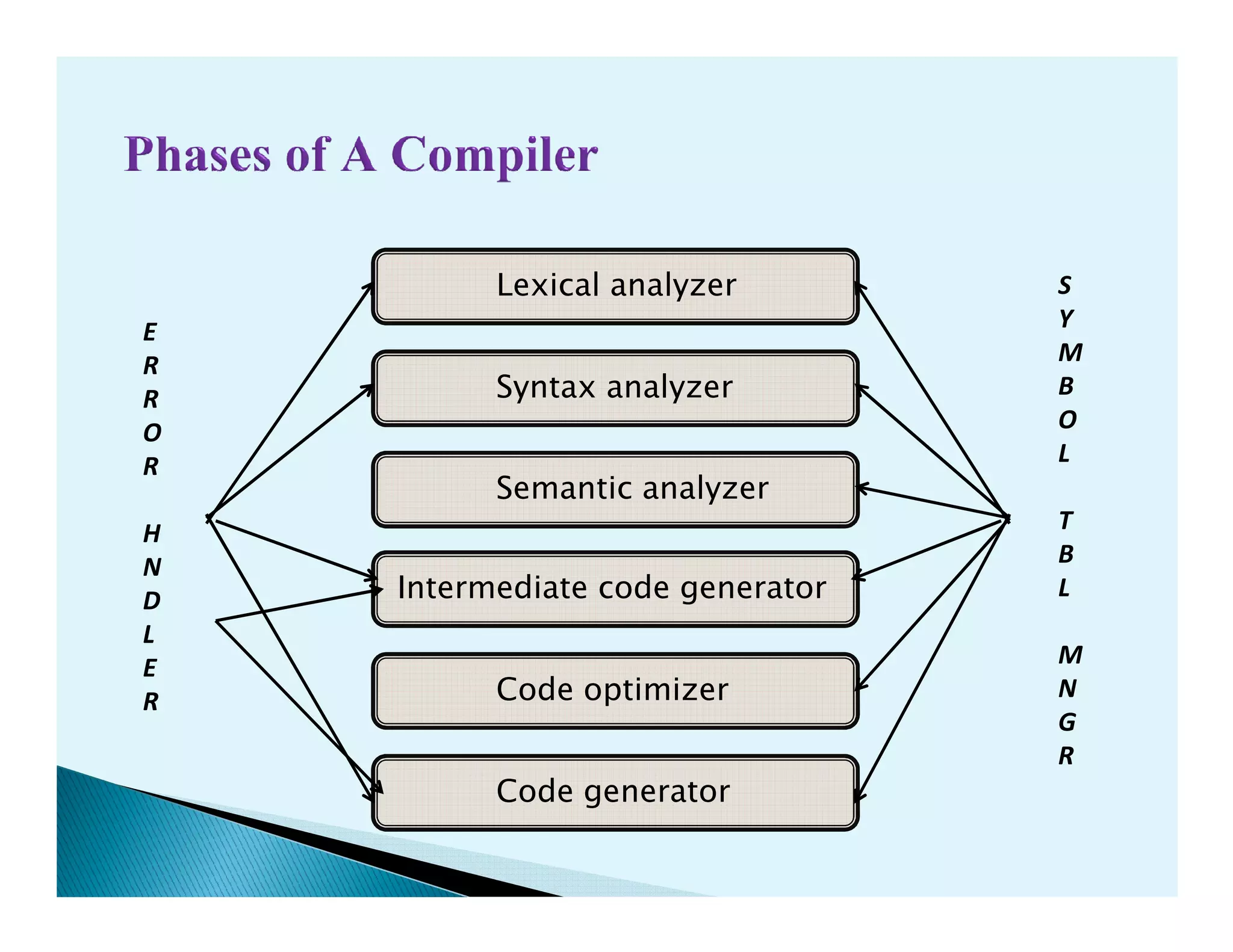
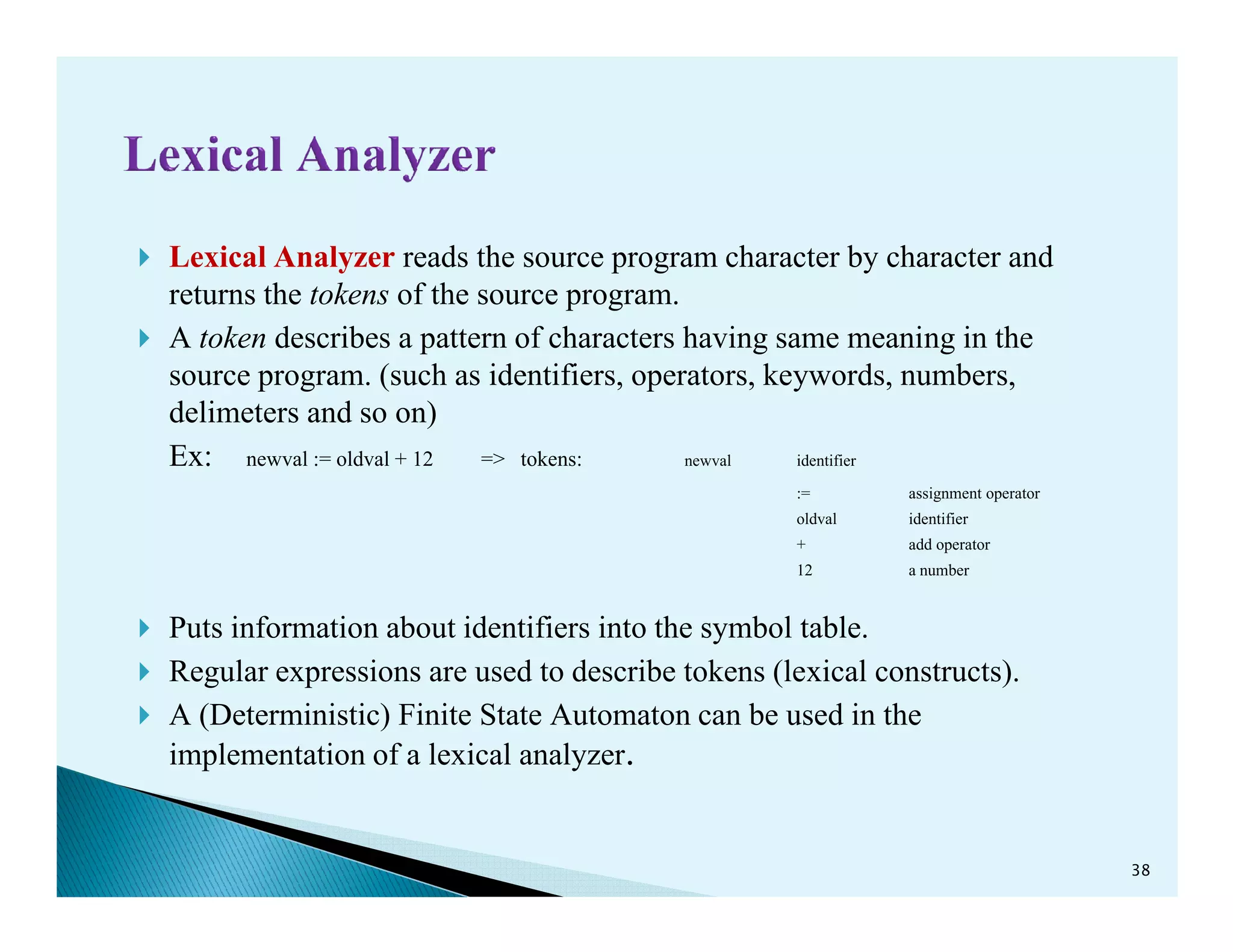
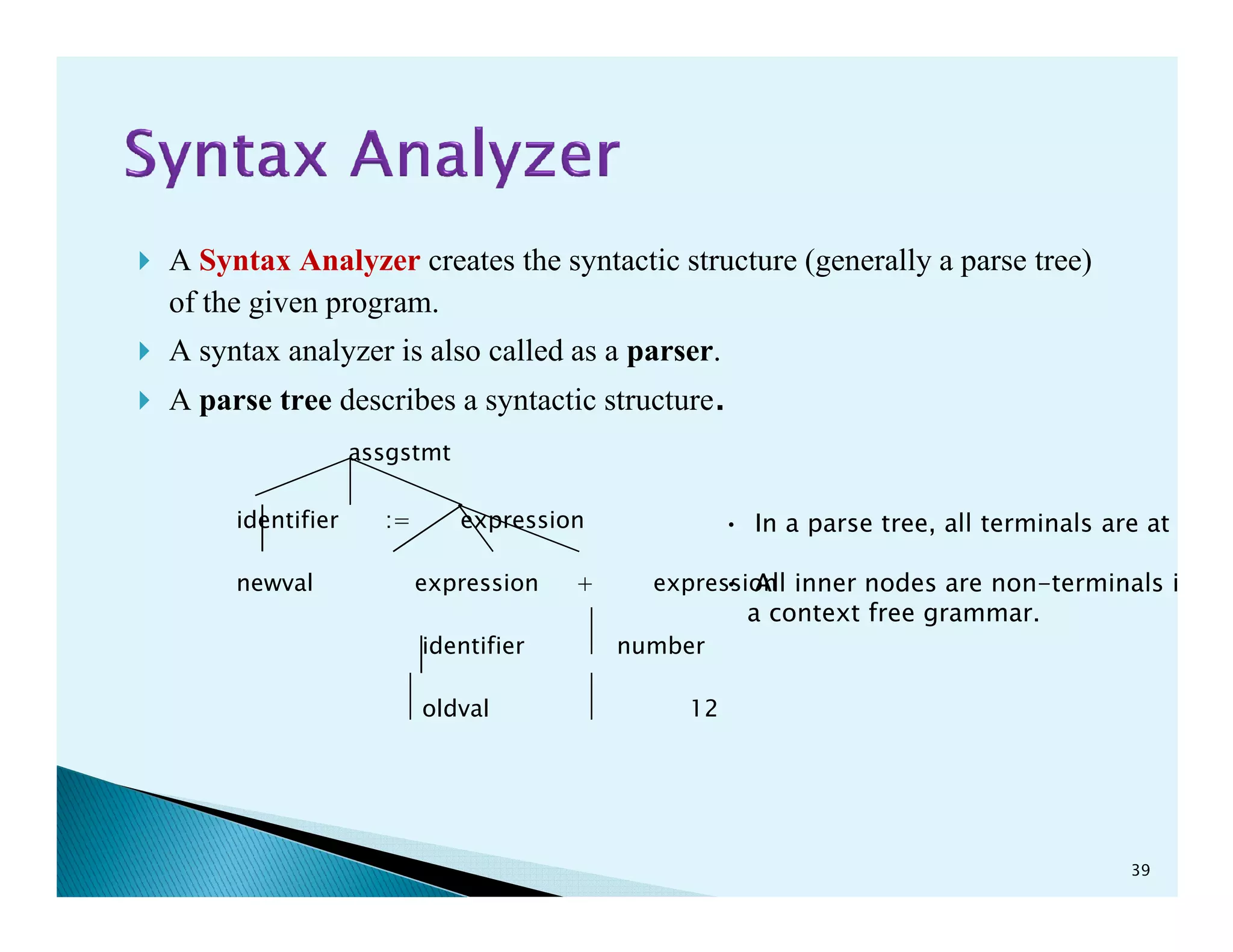
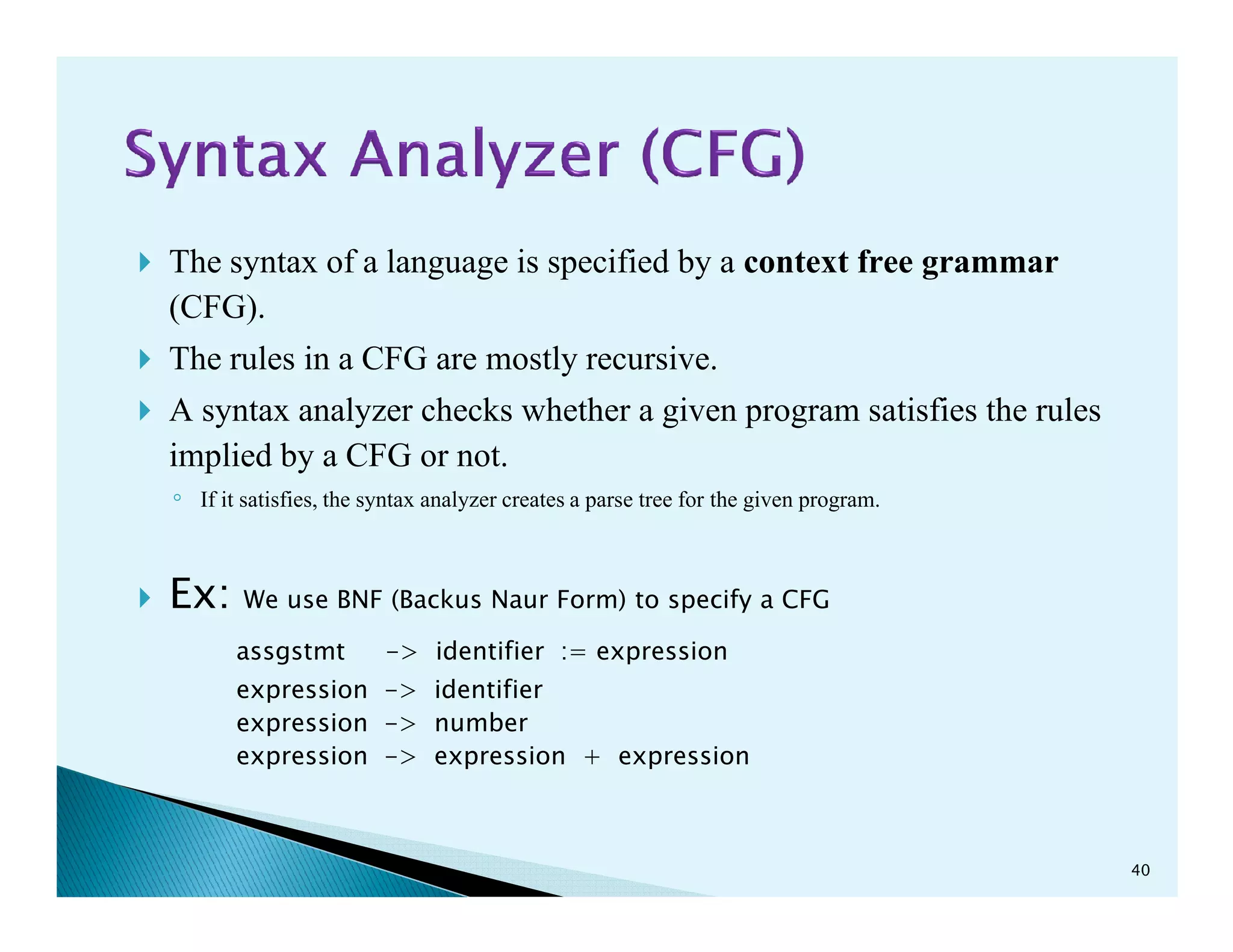
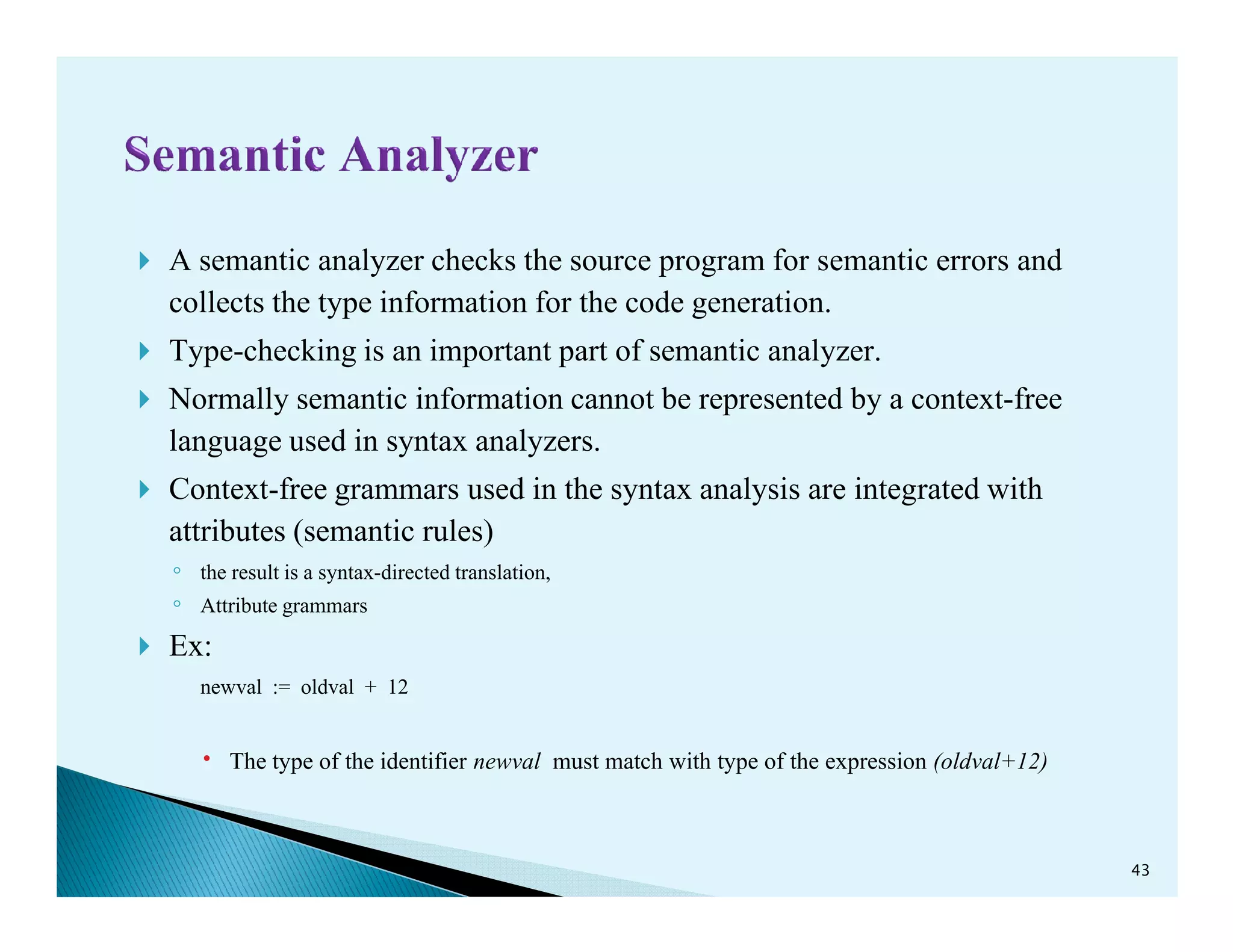
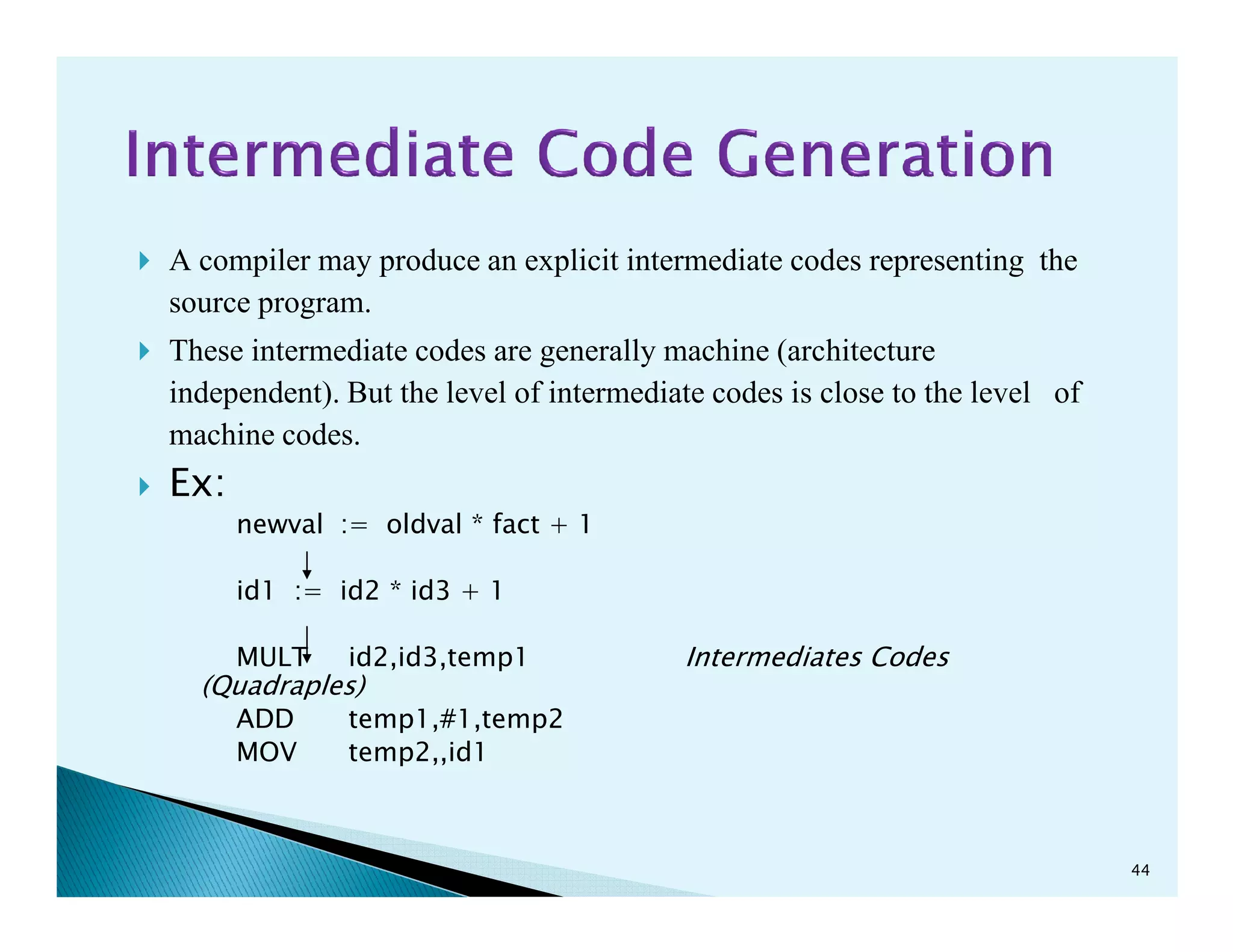
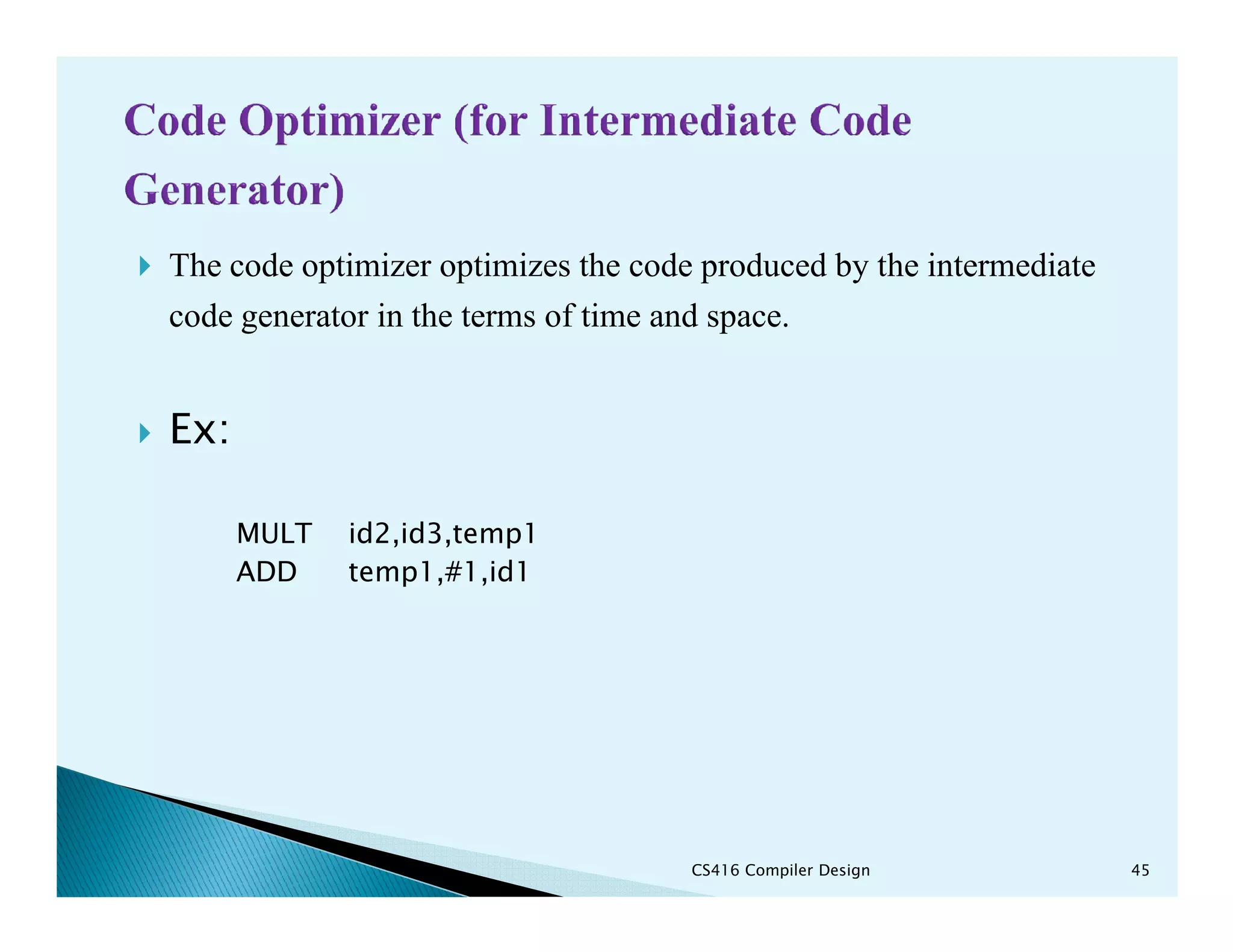
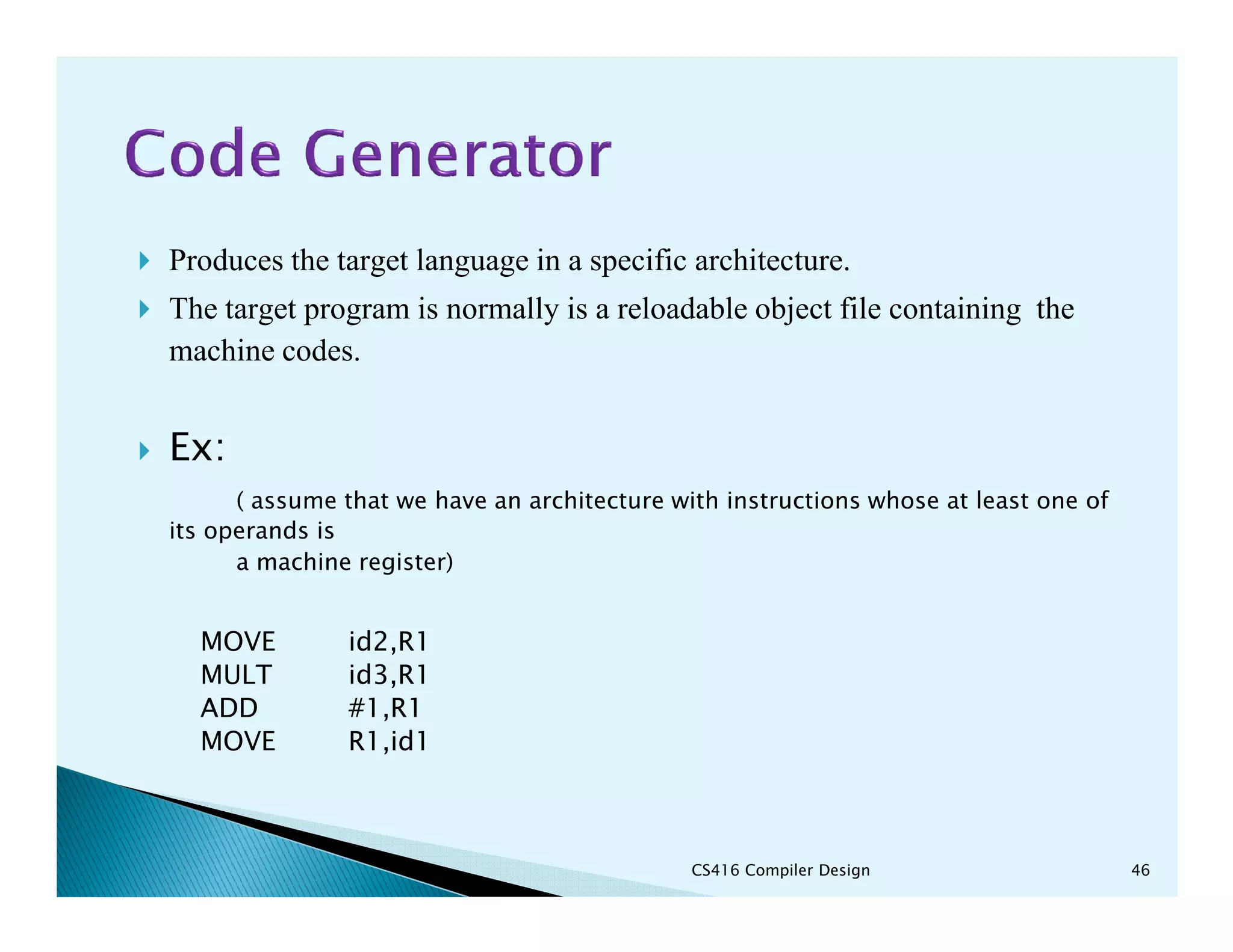
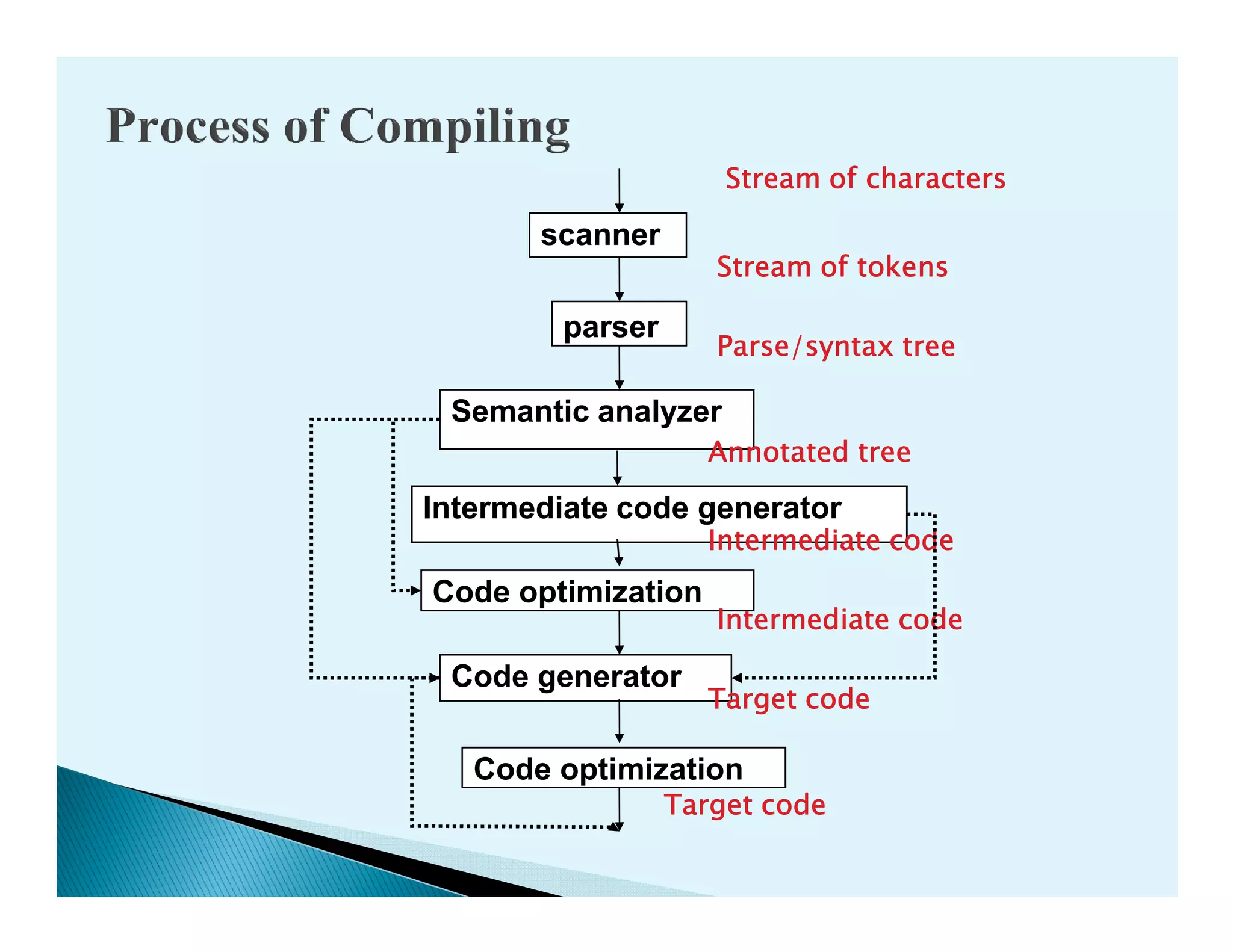
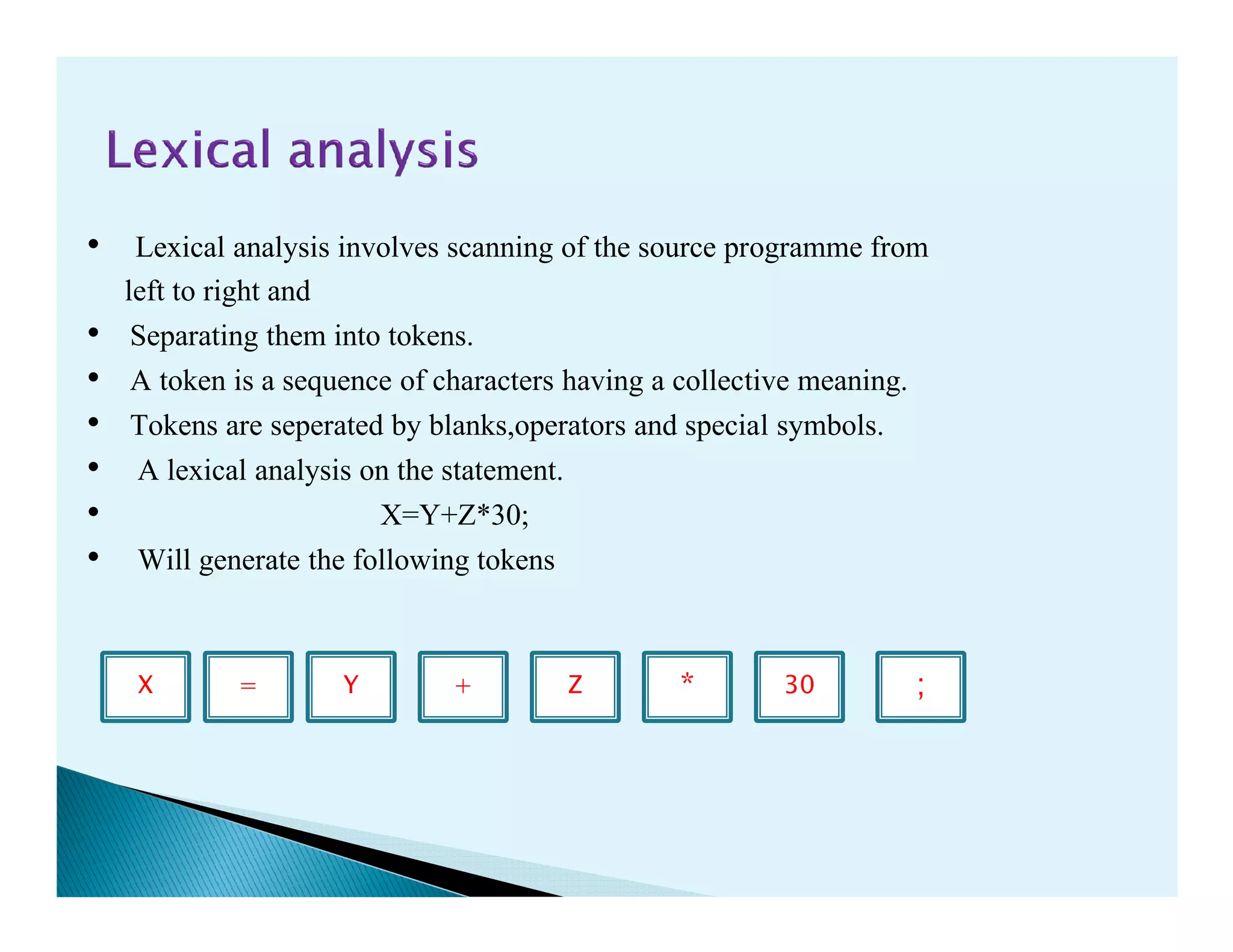
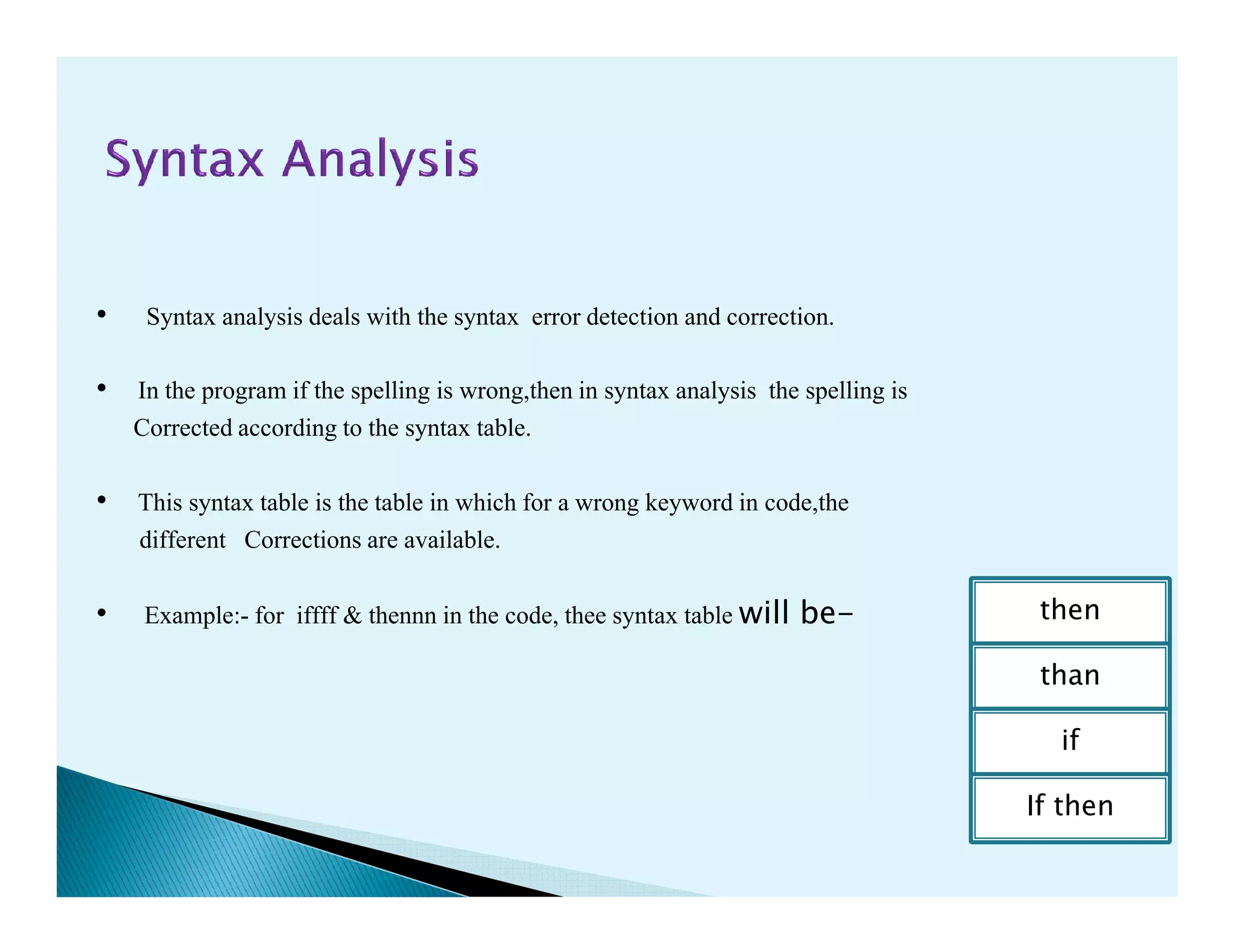
- The phases of a compiler including lexical analysis, syntax analysis, semantic analysis, intermediate code generation, code optimization, and code generation.
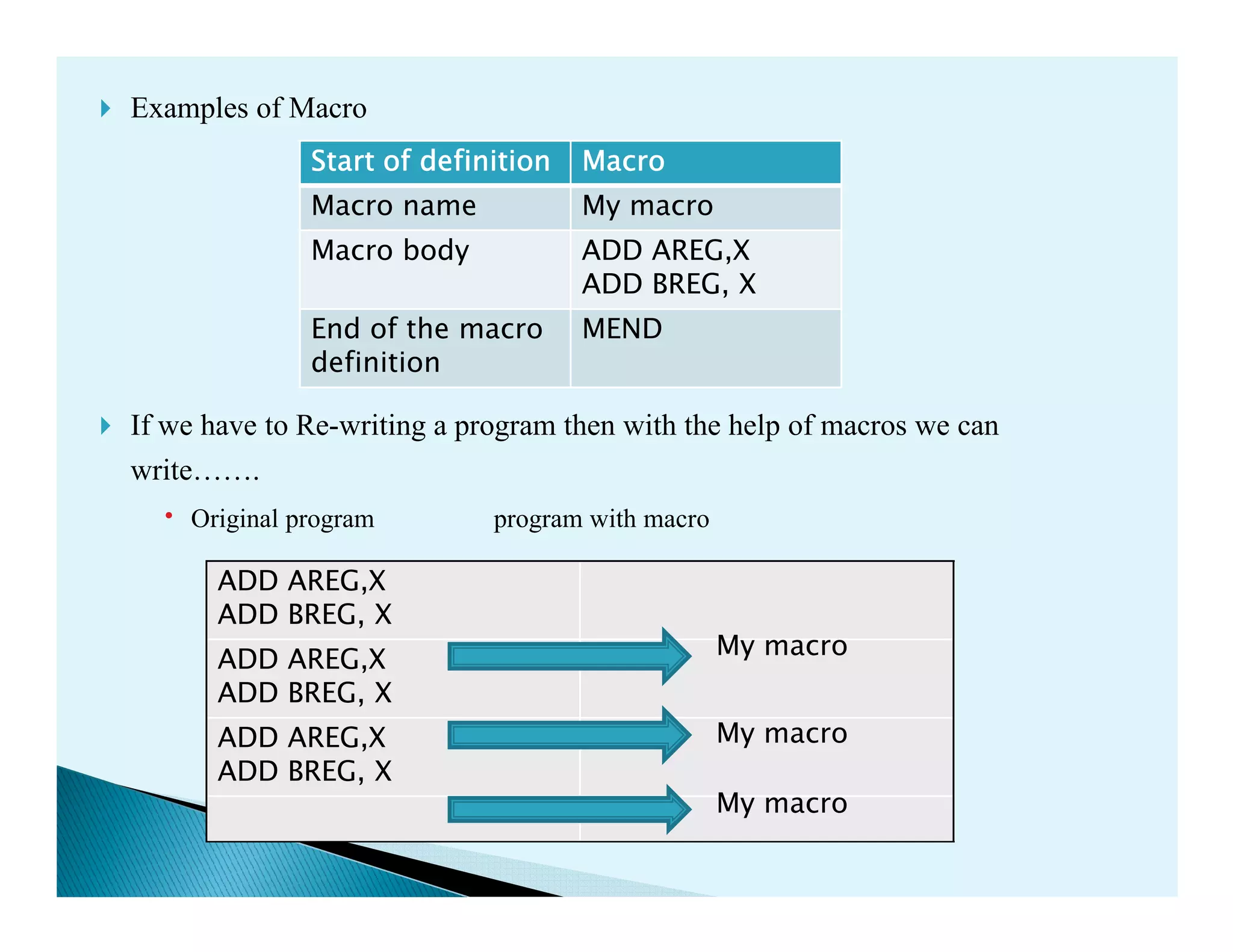
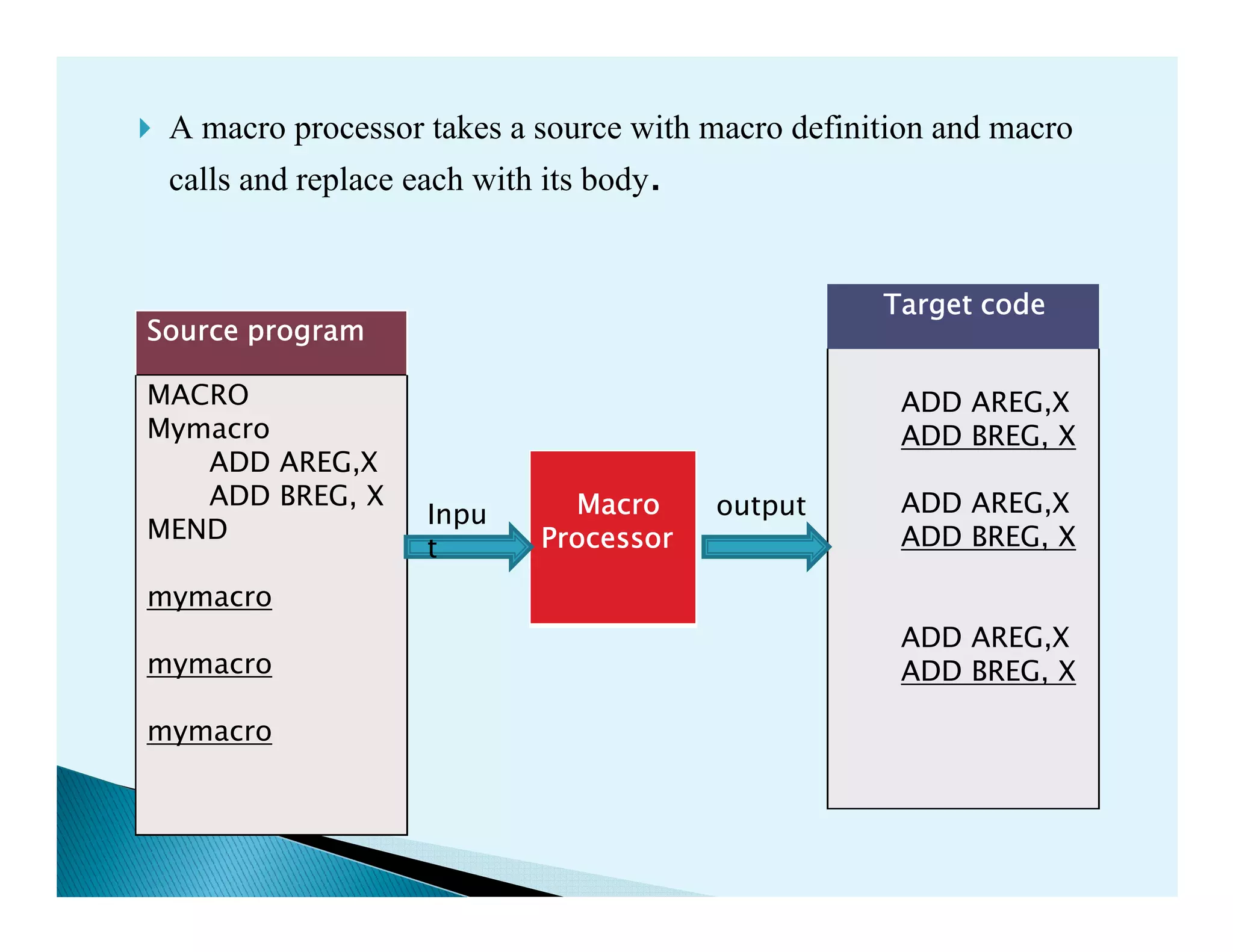
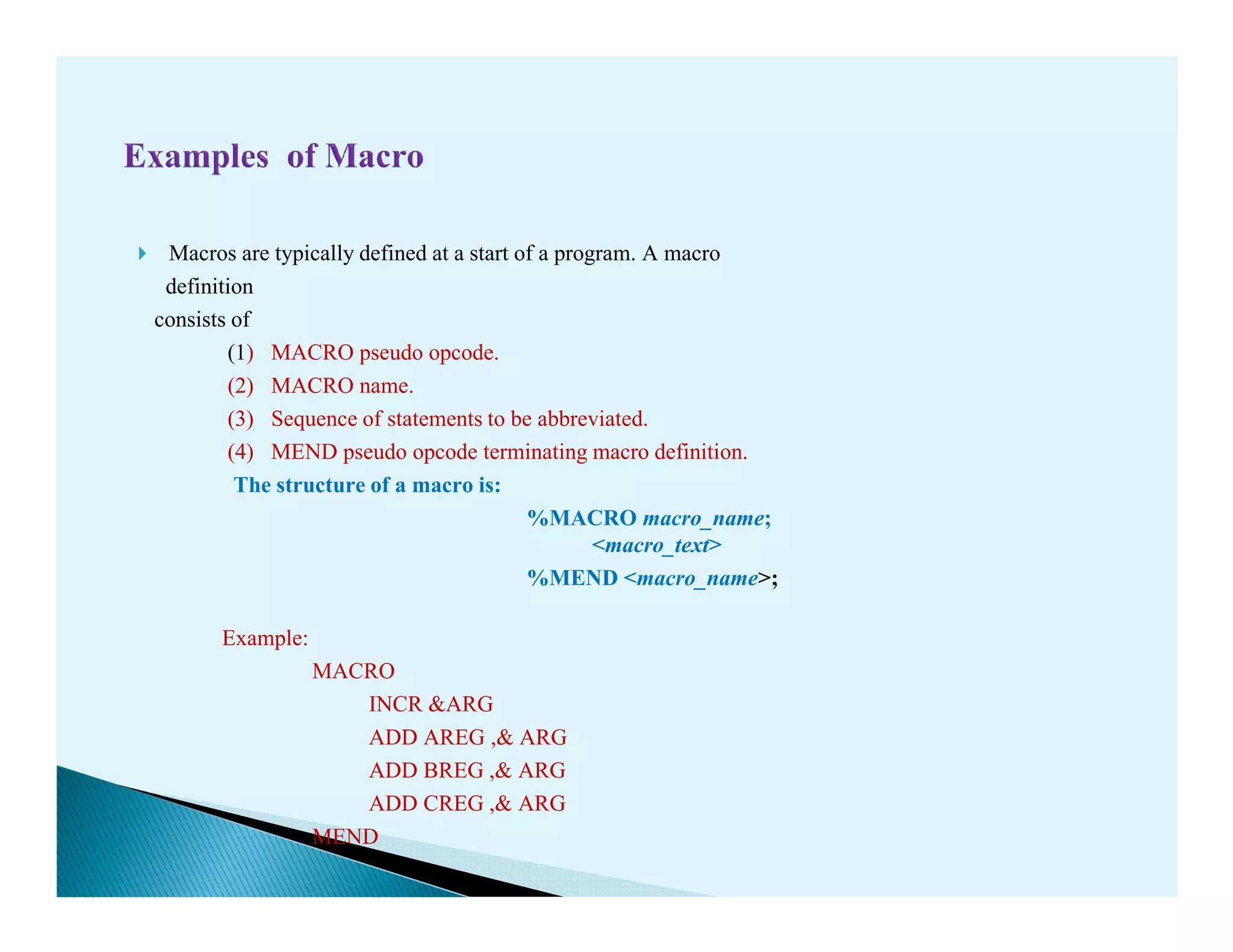
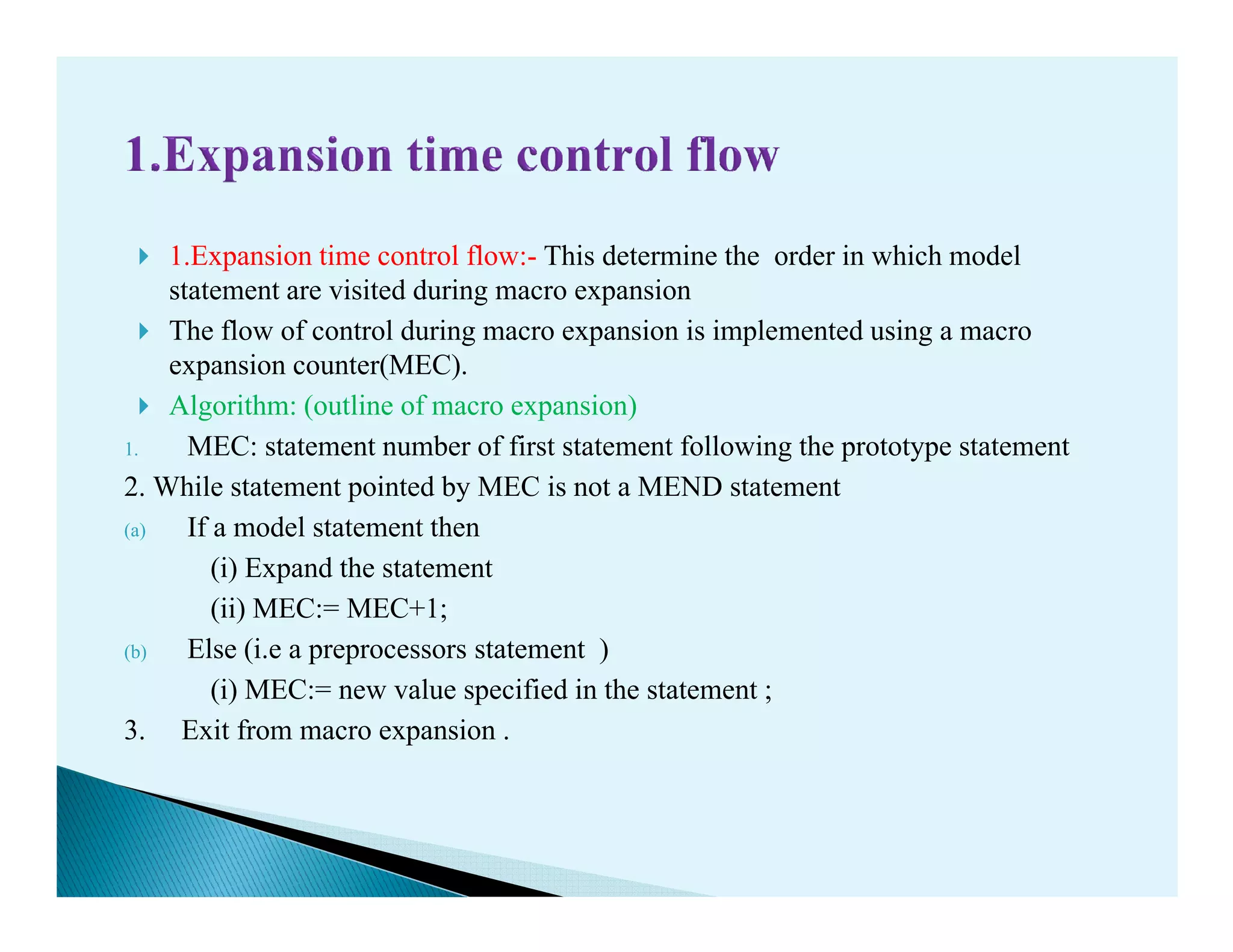
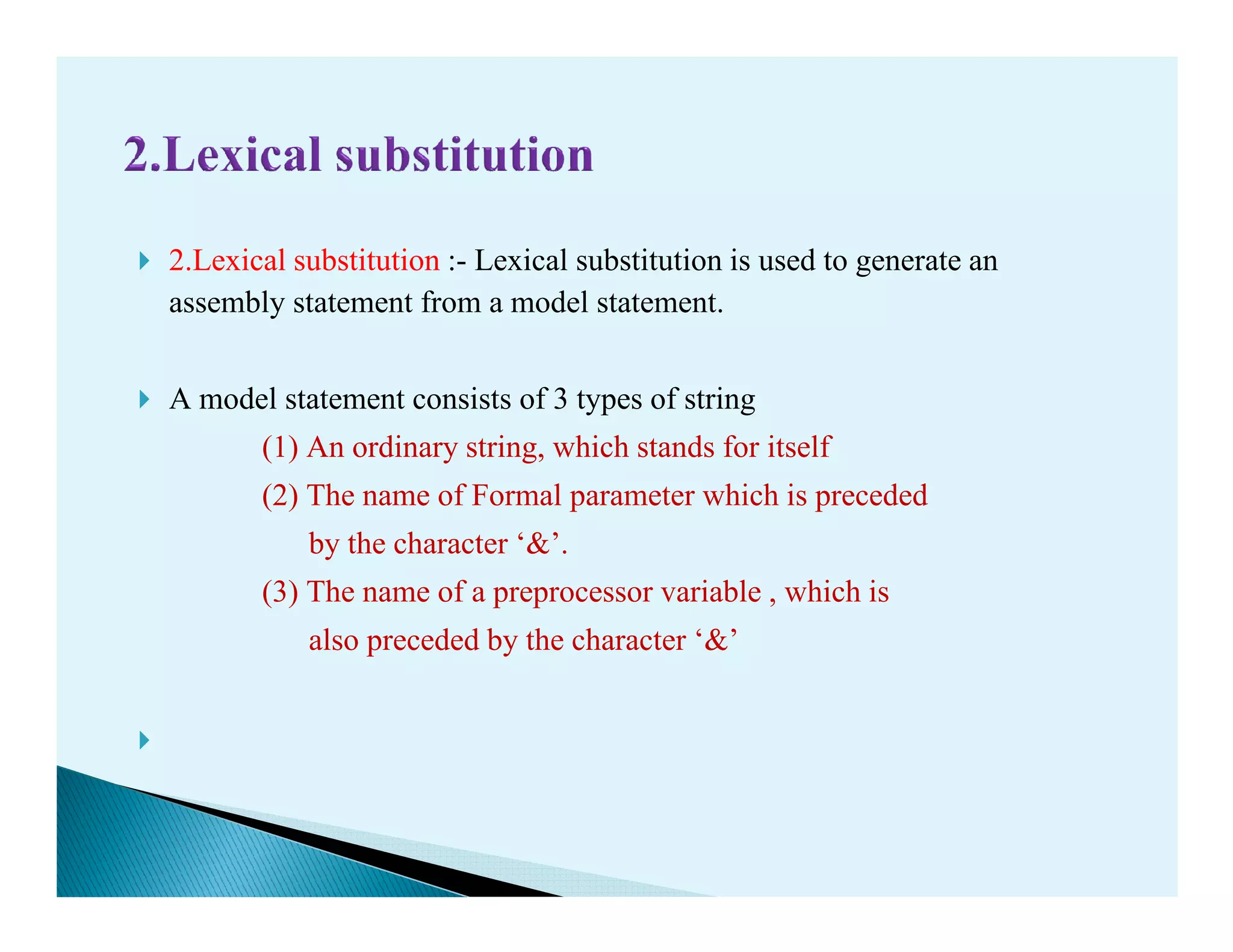
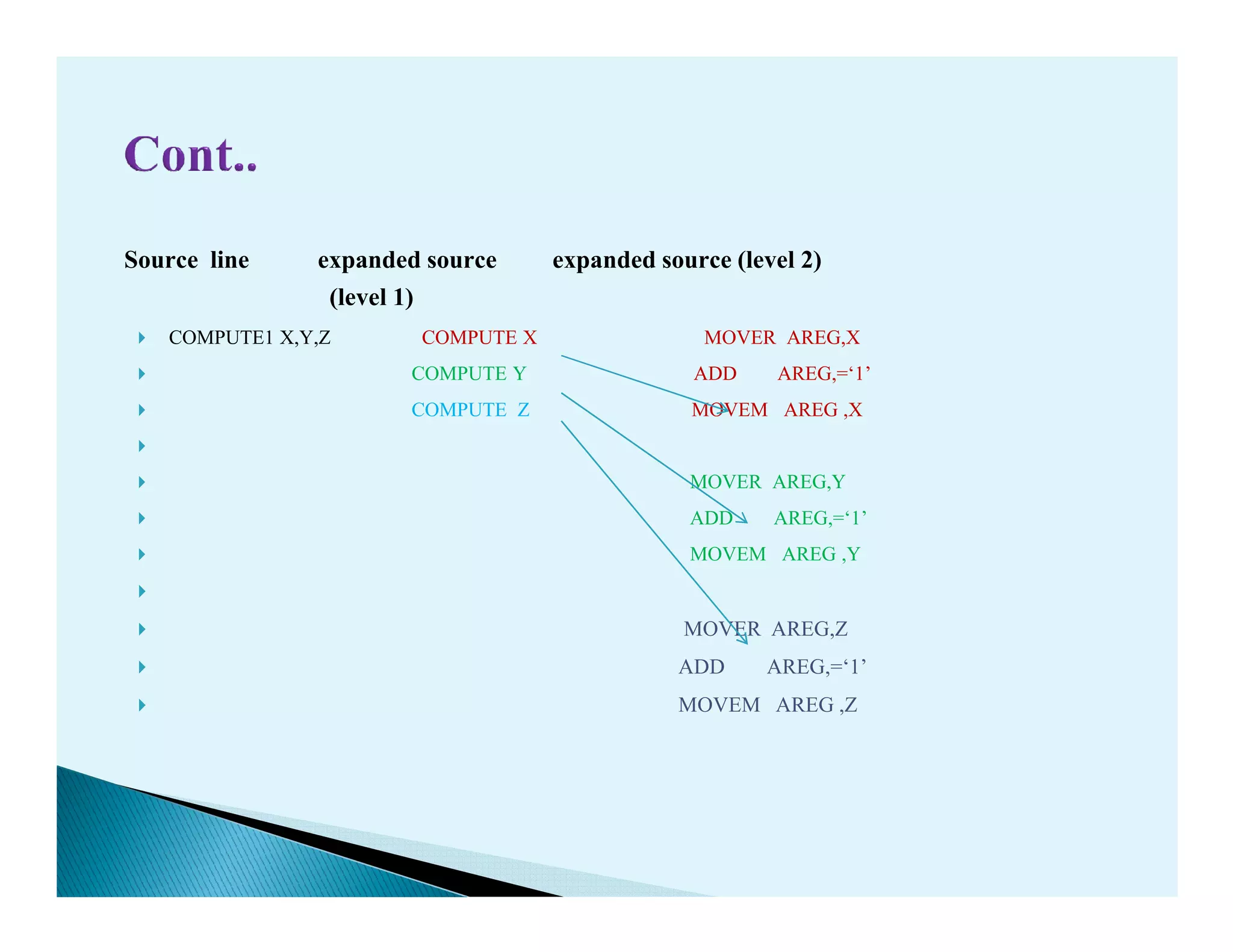
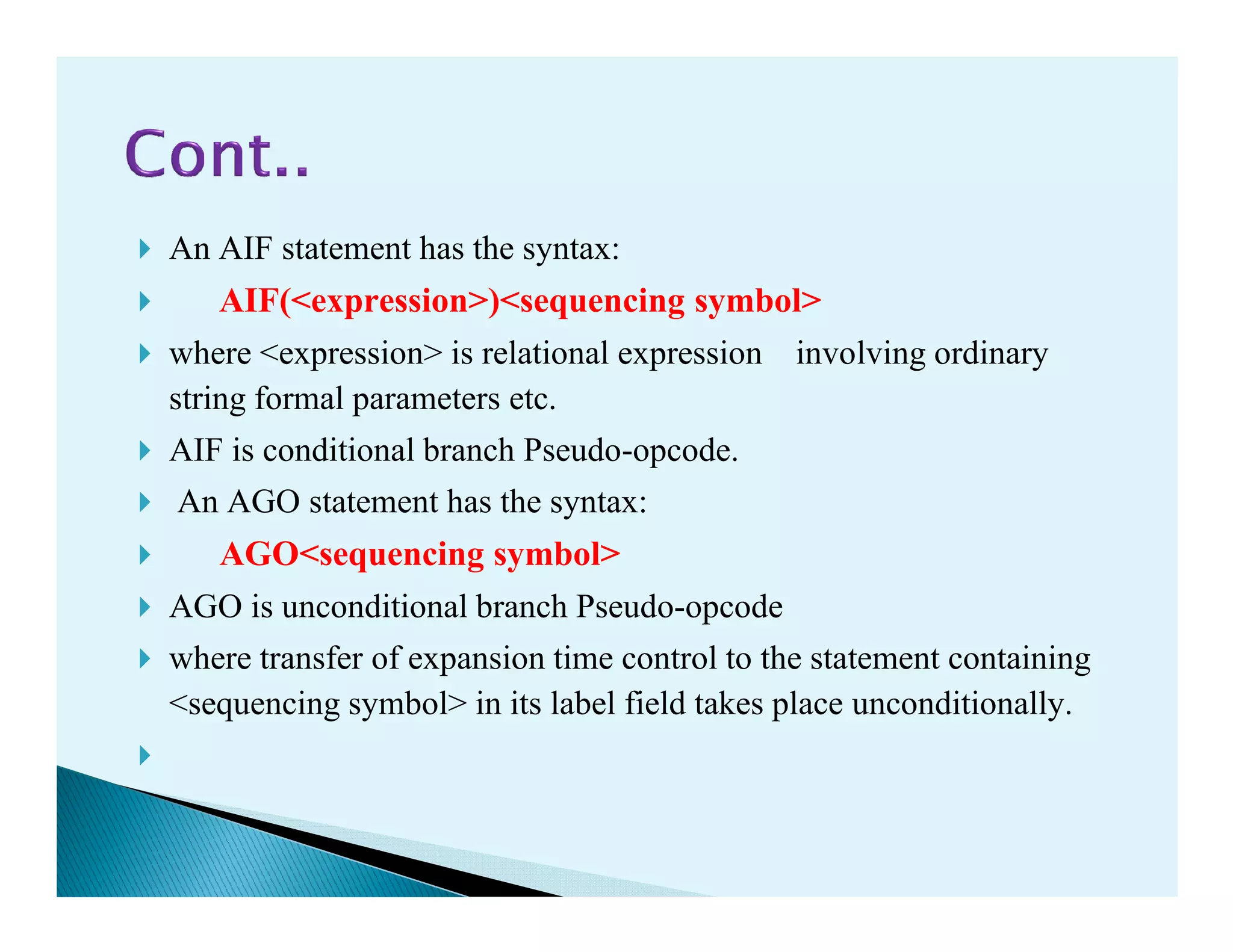
- Macro processors which take source code with macro definitions and calls and replace calls with macro bodies. This includes details on macro expansion, formal/actual parameters, and nested macro calls.
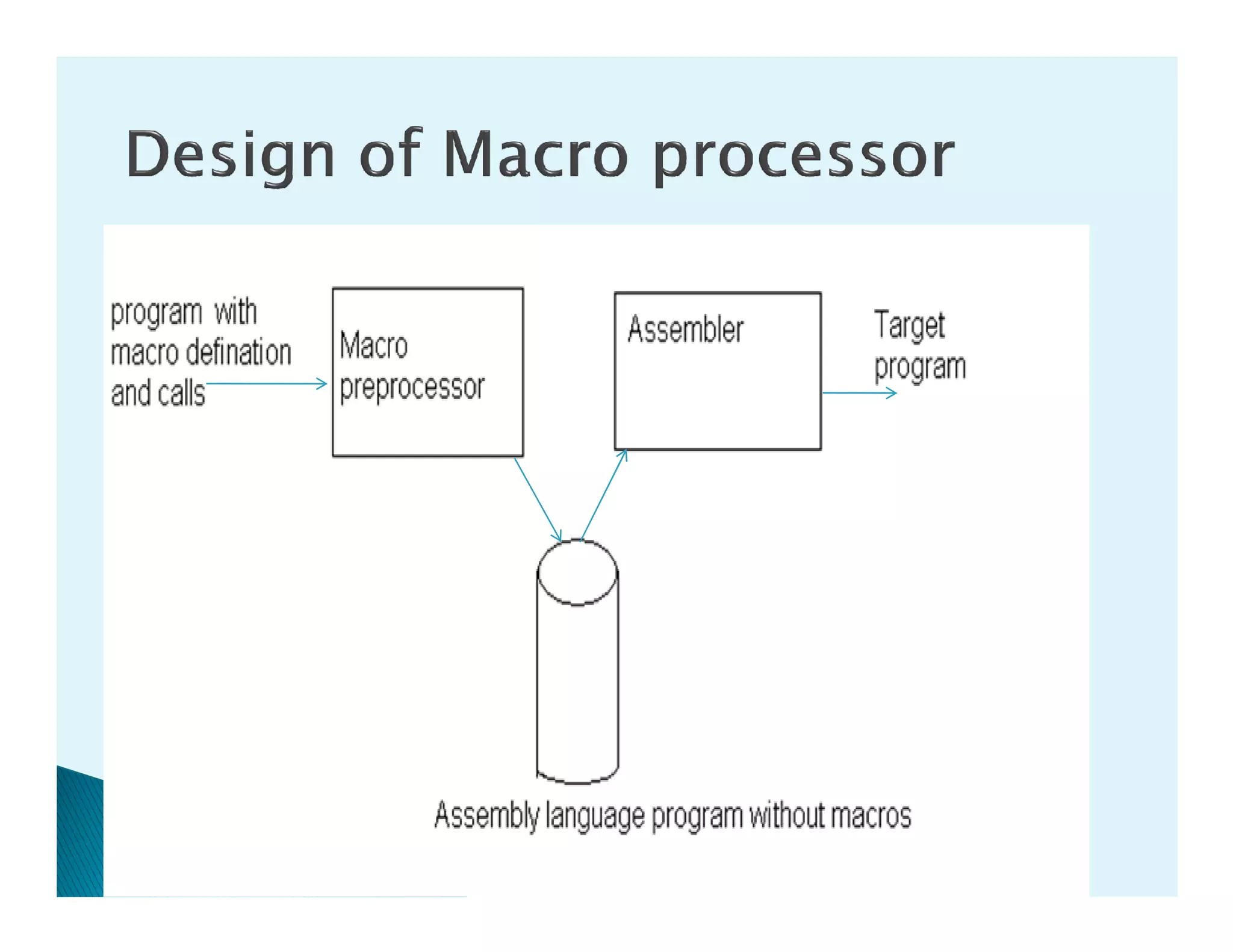
- The design of a macro preprocessor which accepts assembly code with macros and removes macros to generate assembly without macros.
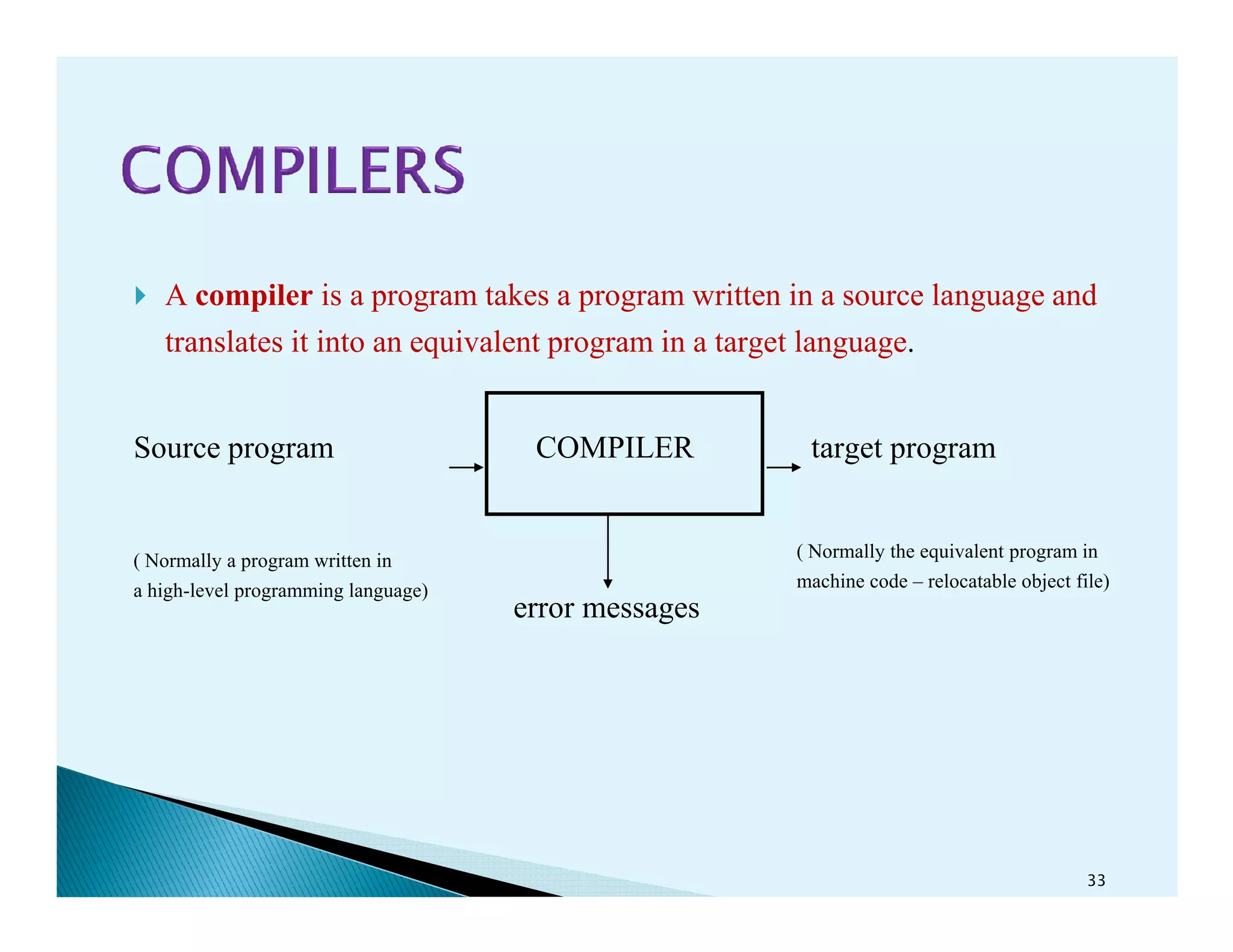
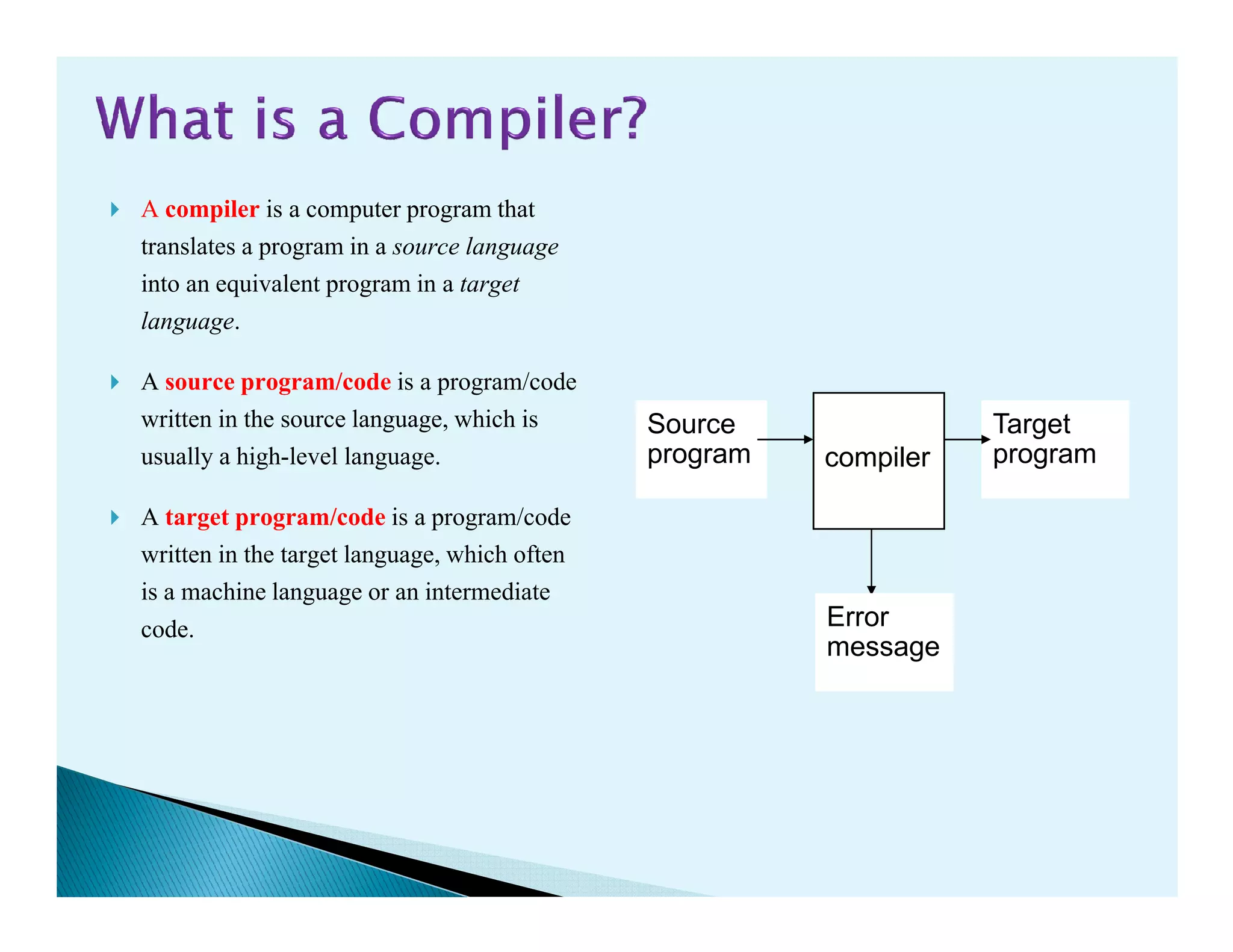
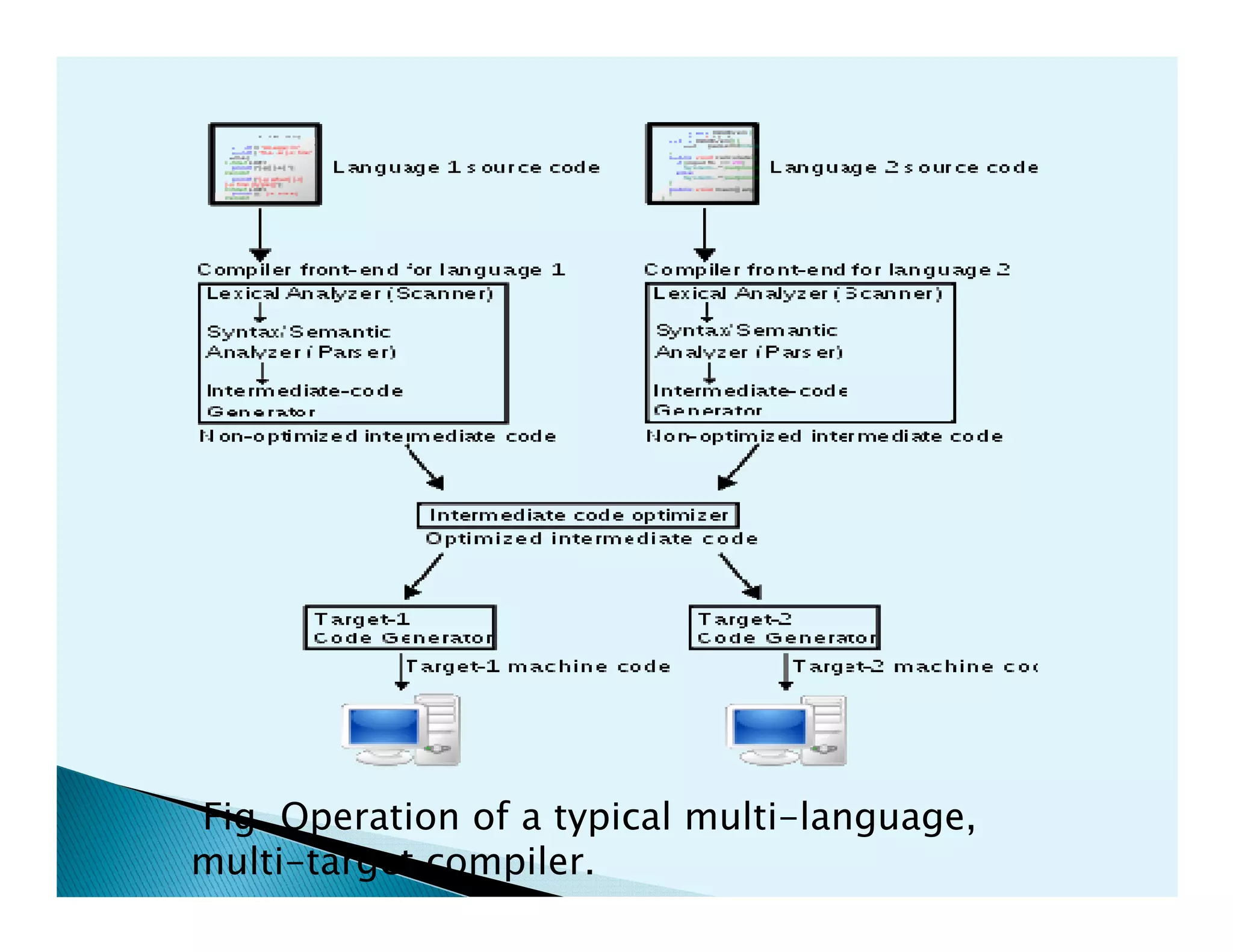
- How compilers translate programs written in a source language into an equivalent program in a target language through various analysis and synthesis phases.






![A macro is called by writing macro name with actual parameters in
an assembly program.
The macro call has following syntax:
< macro name > [ < list of parameters > ]
For example,For example,
INCR X
Will call the macro INCR with the actual parameter X.](https://image.slidesharecdn.com/unit-2-130420010336-phpapp02/75/Unit-2-12-2048.jpg)








![Expansion of time variables(EV) are variables which can only be use
during the expansion of macro calls.
A local EV is created for use only during the a particular macro call .
Its syntax is:-
LCL<&variable name>[,< variable name>¡.]
A global EV exist across all macro calls situated in a program & can beA global EV exist across all macro calls situated in a program & can be
used in any macro which has a declaration for it.
Its syntax is:
GBL<&variable name>[,< variable name>¡.]
Expansion of time variables(EV) can be manipulated through the statement
SET .
Syntax:-
< Expansion time variables>SET< expression>](https://image.slidesharecdn.com/unit-2-130420010336-phpapp02/75/Unit-2-25-2048.jpg)