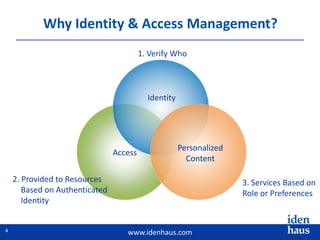
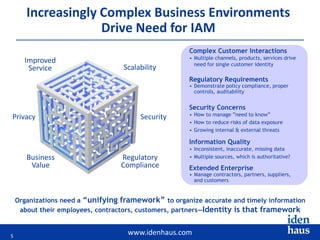
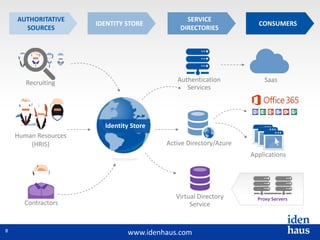
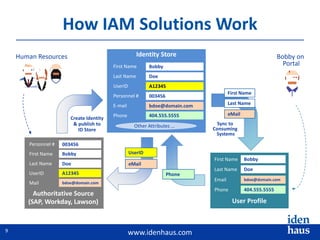
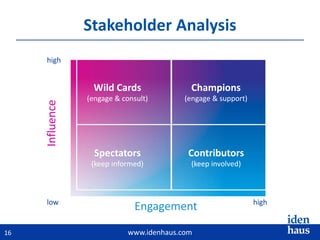
The document discusses the challenges and solutions in identity and access management (IAM), highlighting the need for accurate and timely identity data in complex business environments. Common implementation issues include data quality, process misalignment, and inadequate stakeholder engagement. Successful IAM requires a focus on establishing data accuracy, understanding authoritative sources, and integrating processes across the organization.