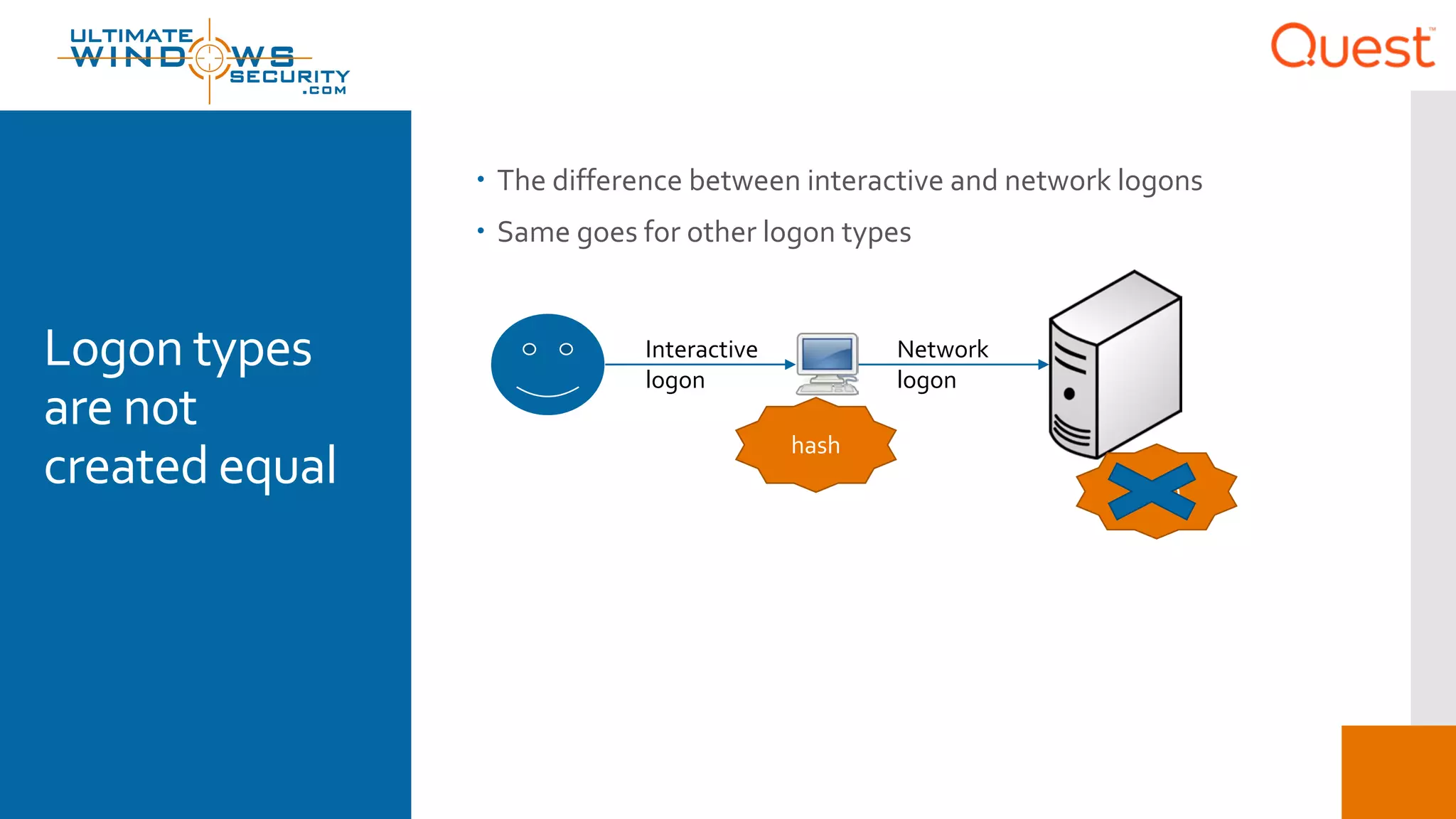
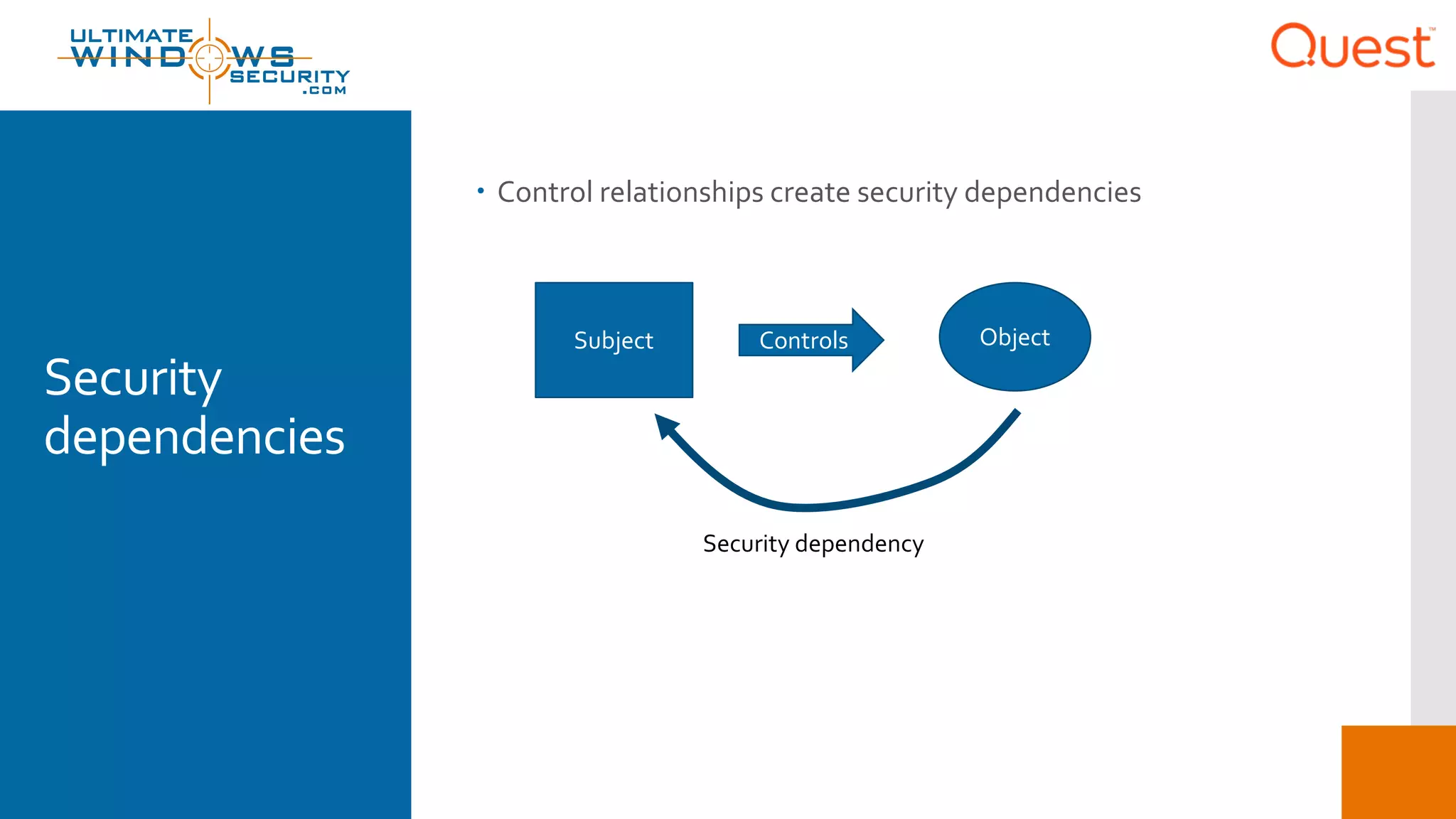
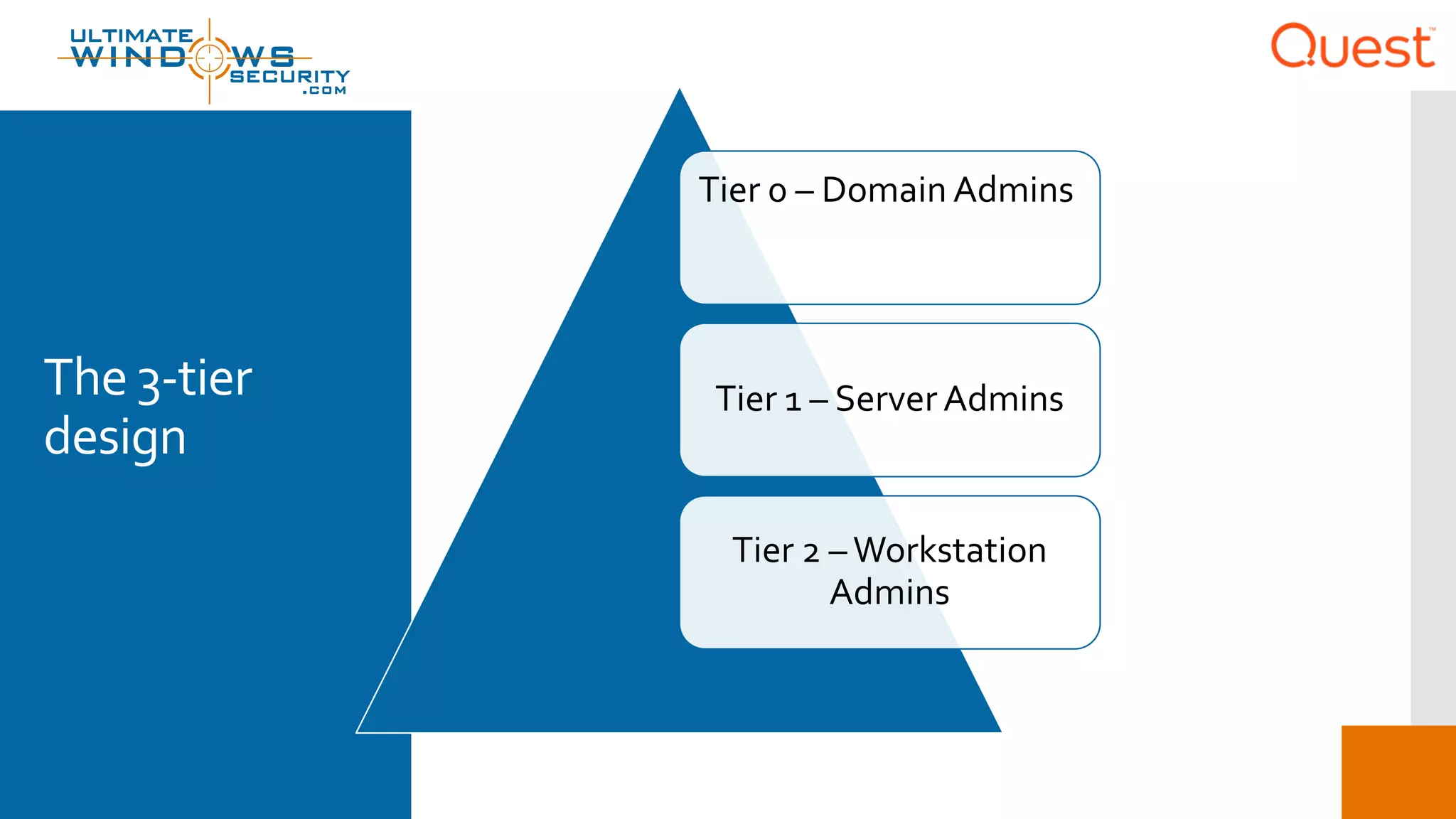
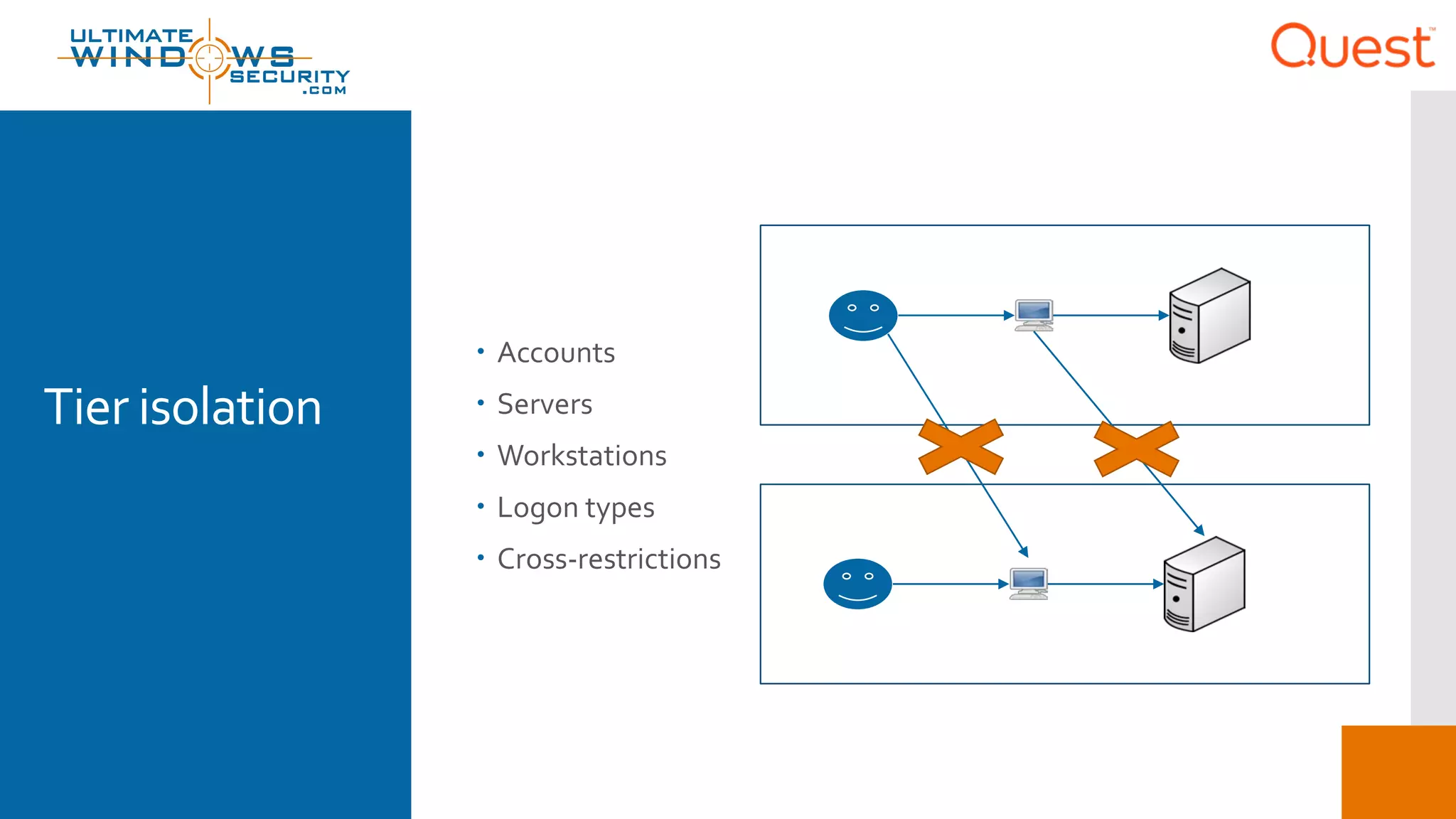
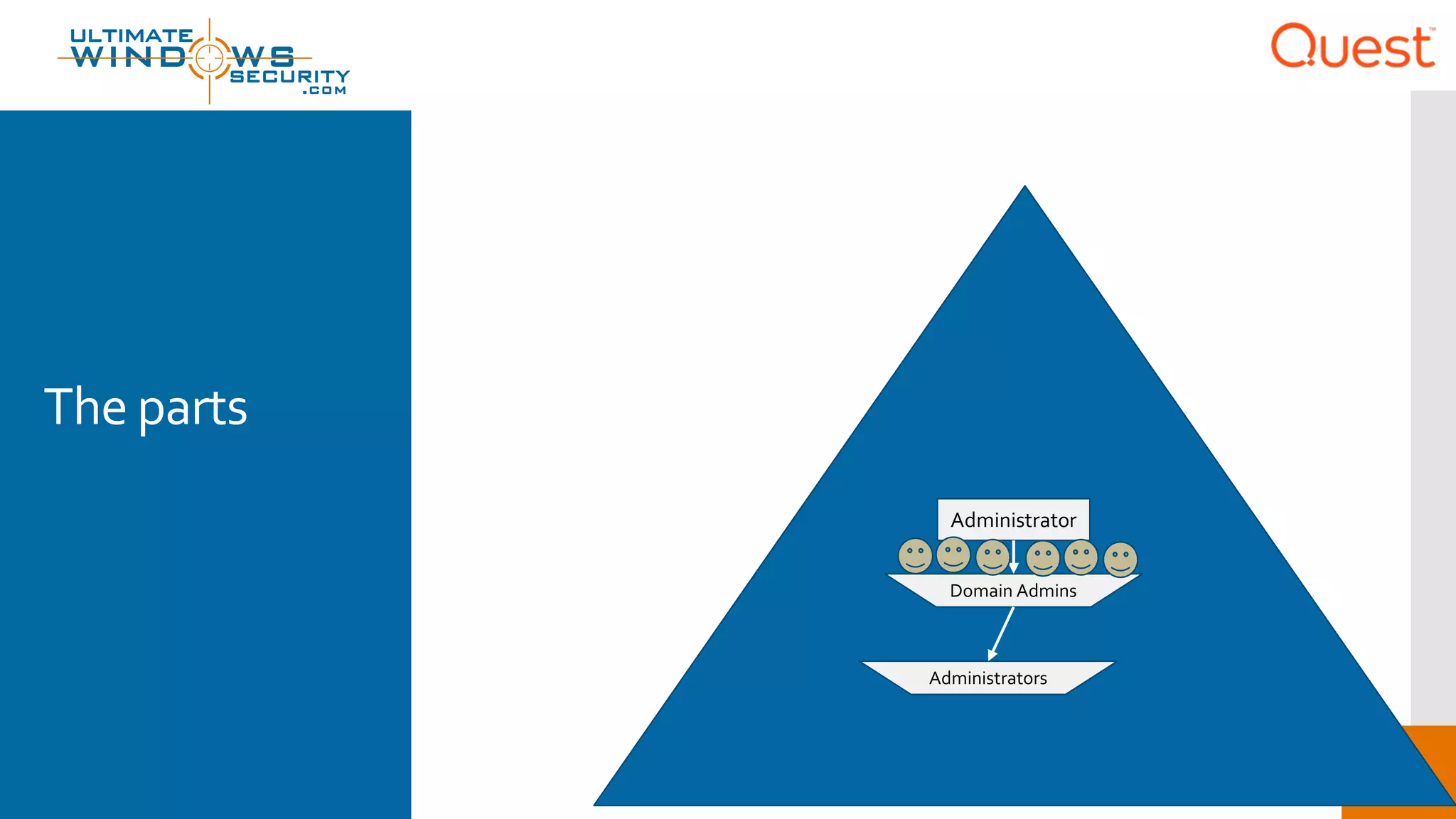
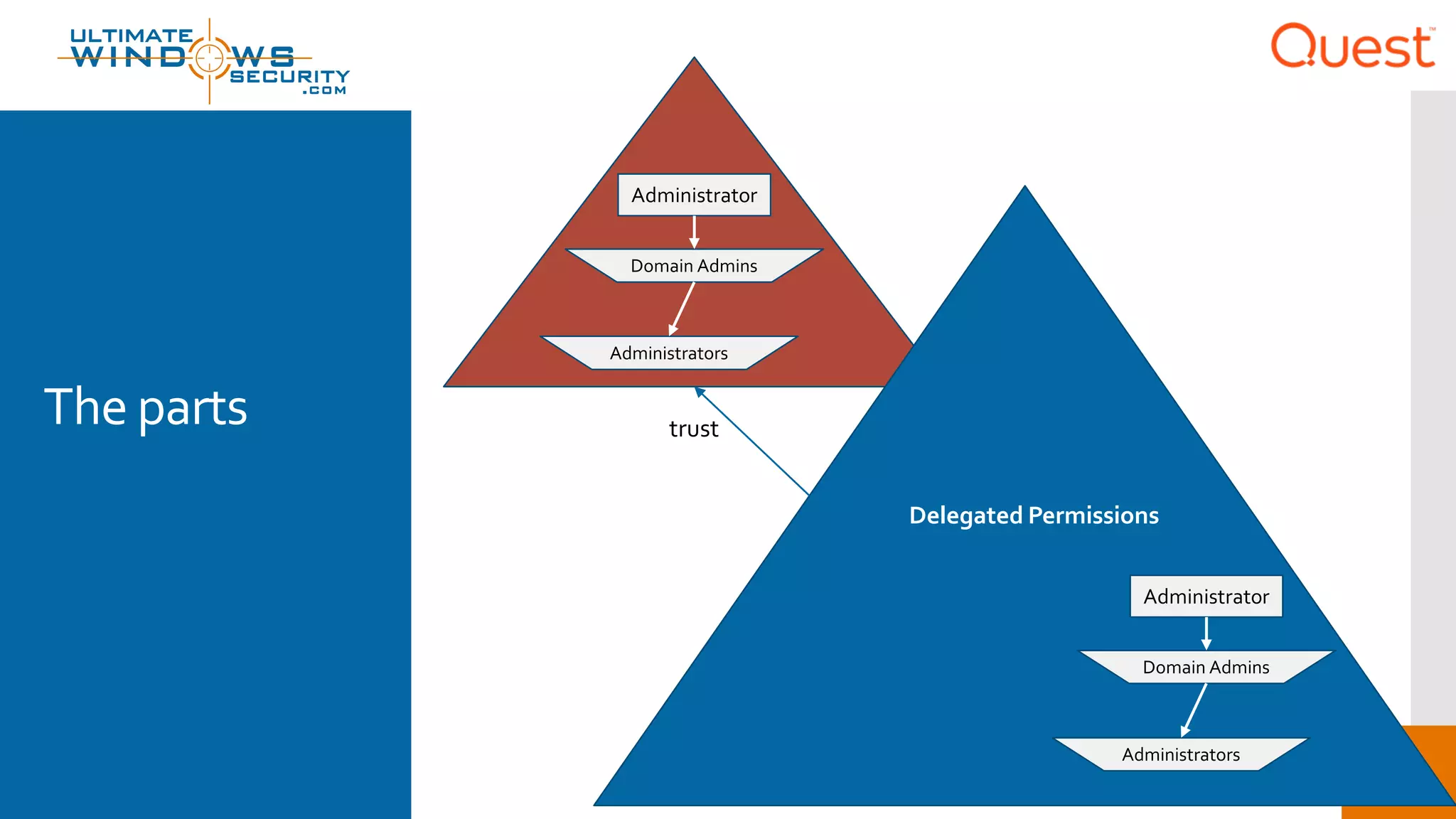
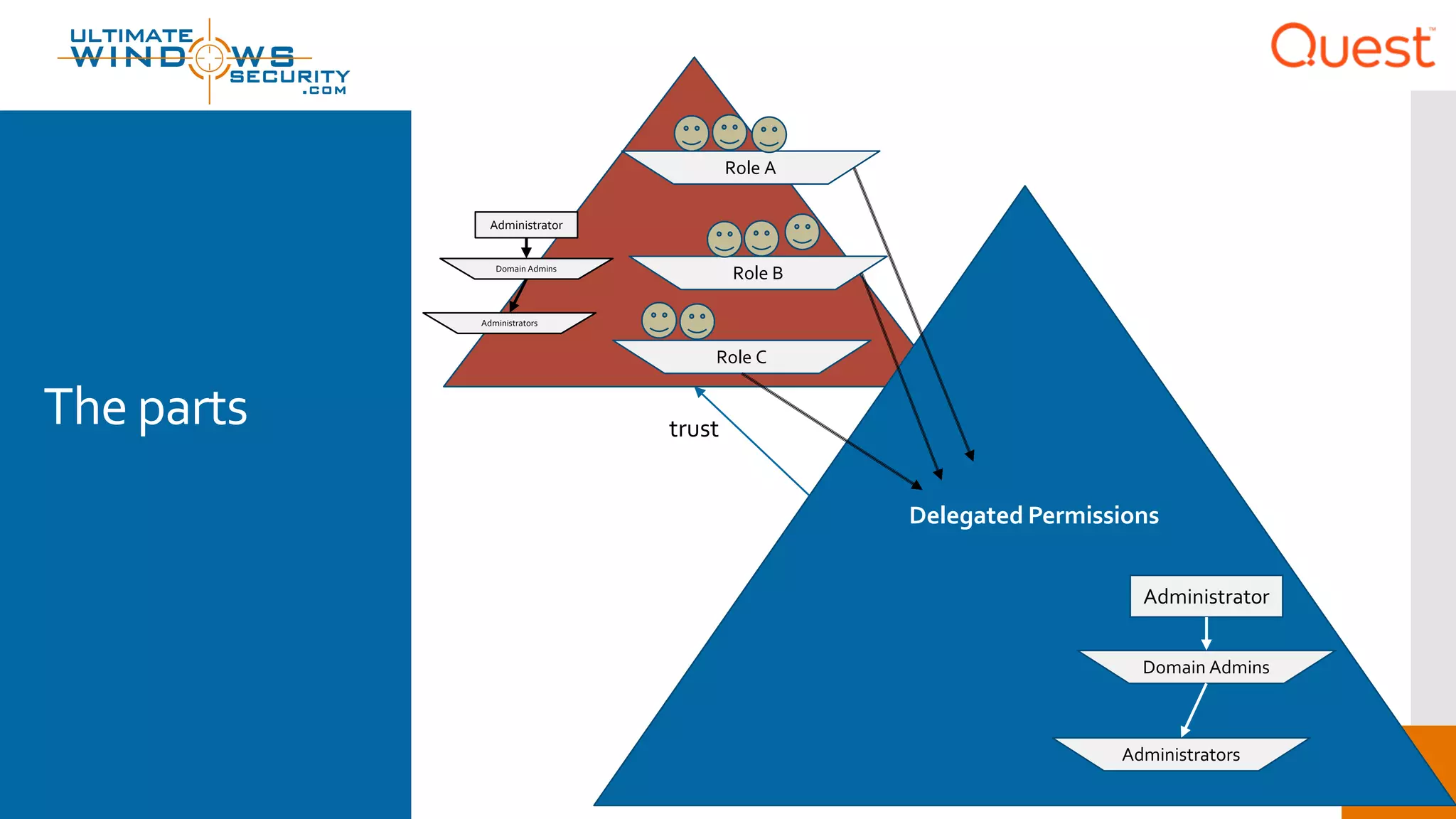
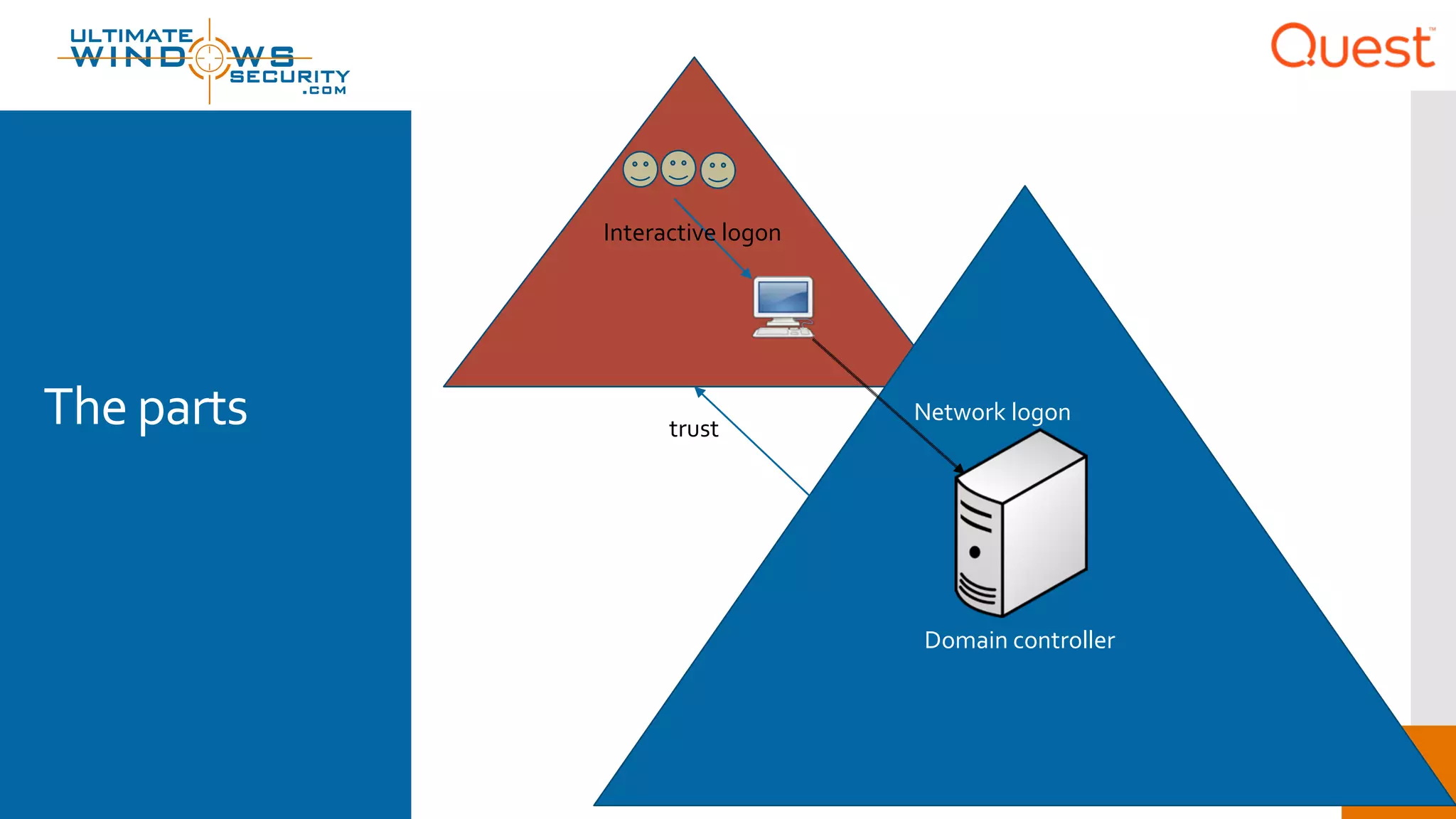
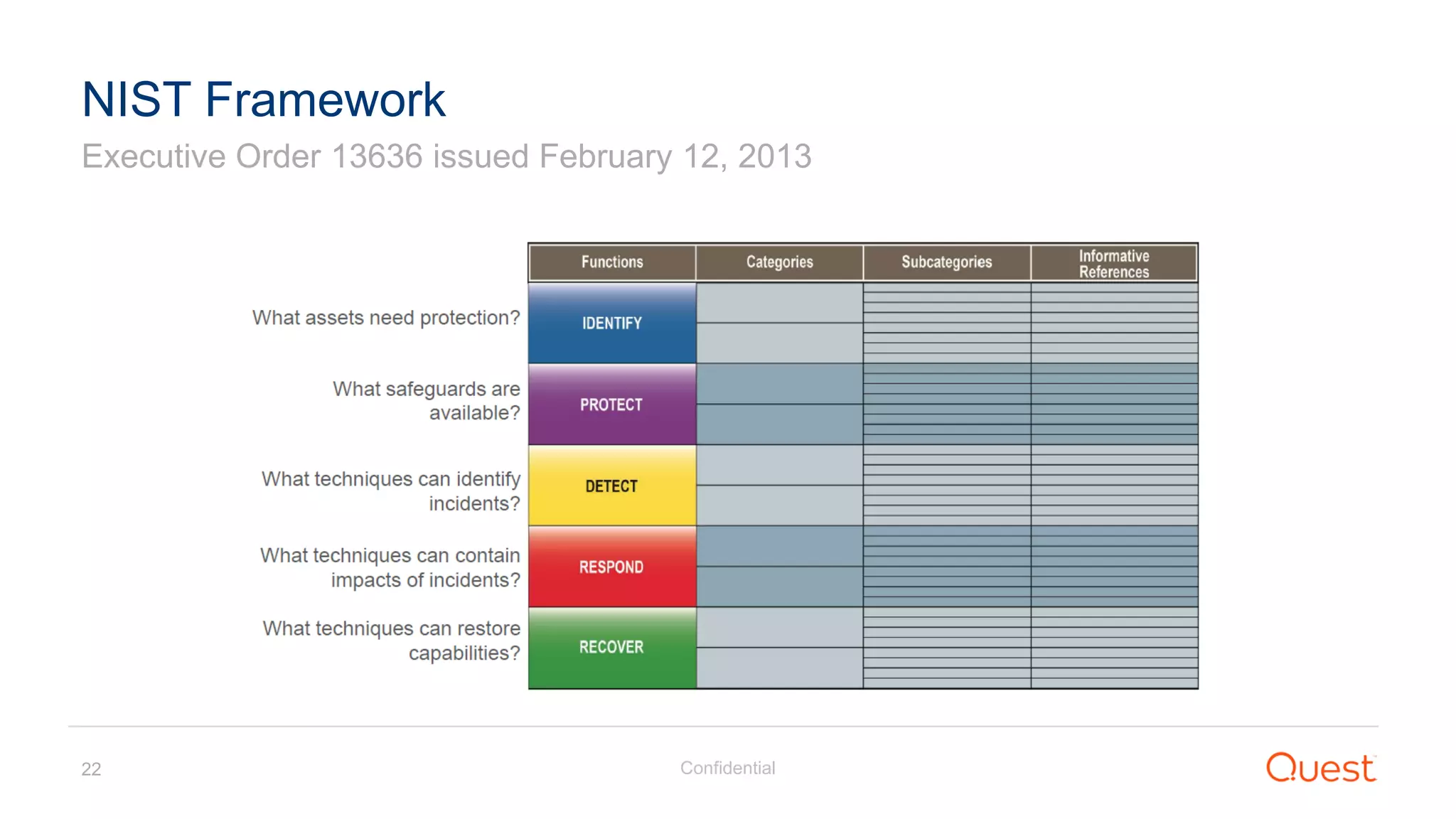
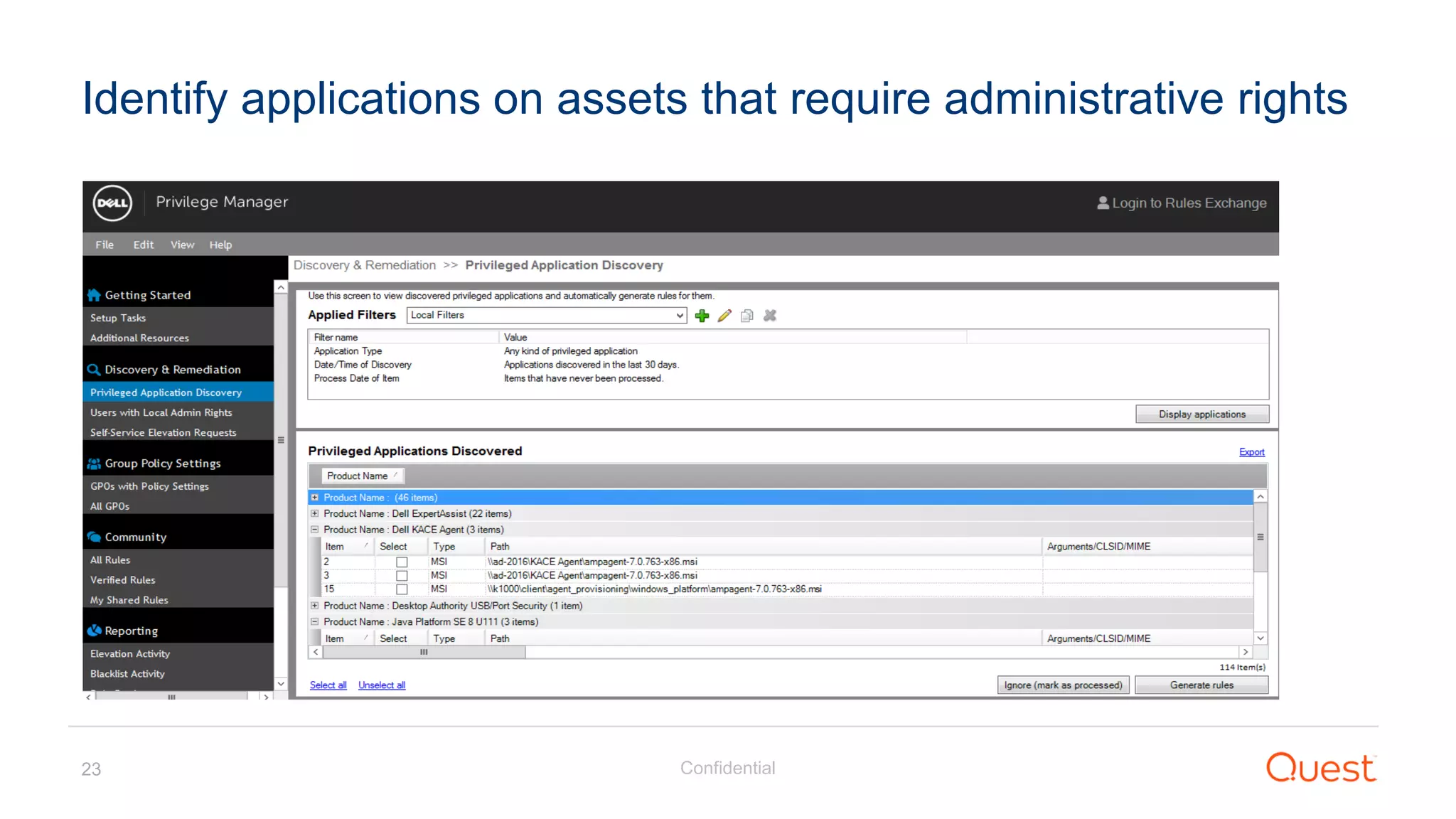
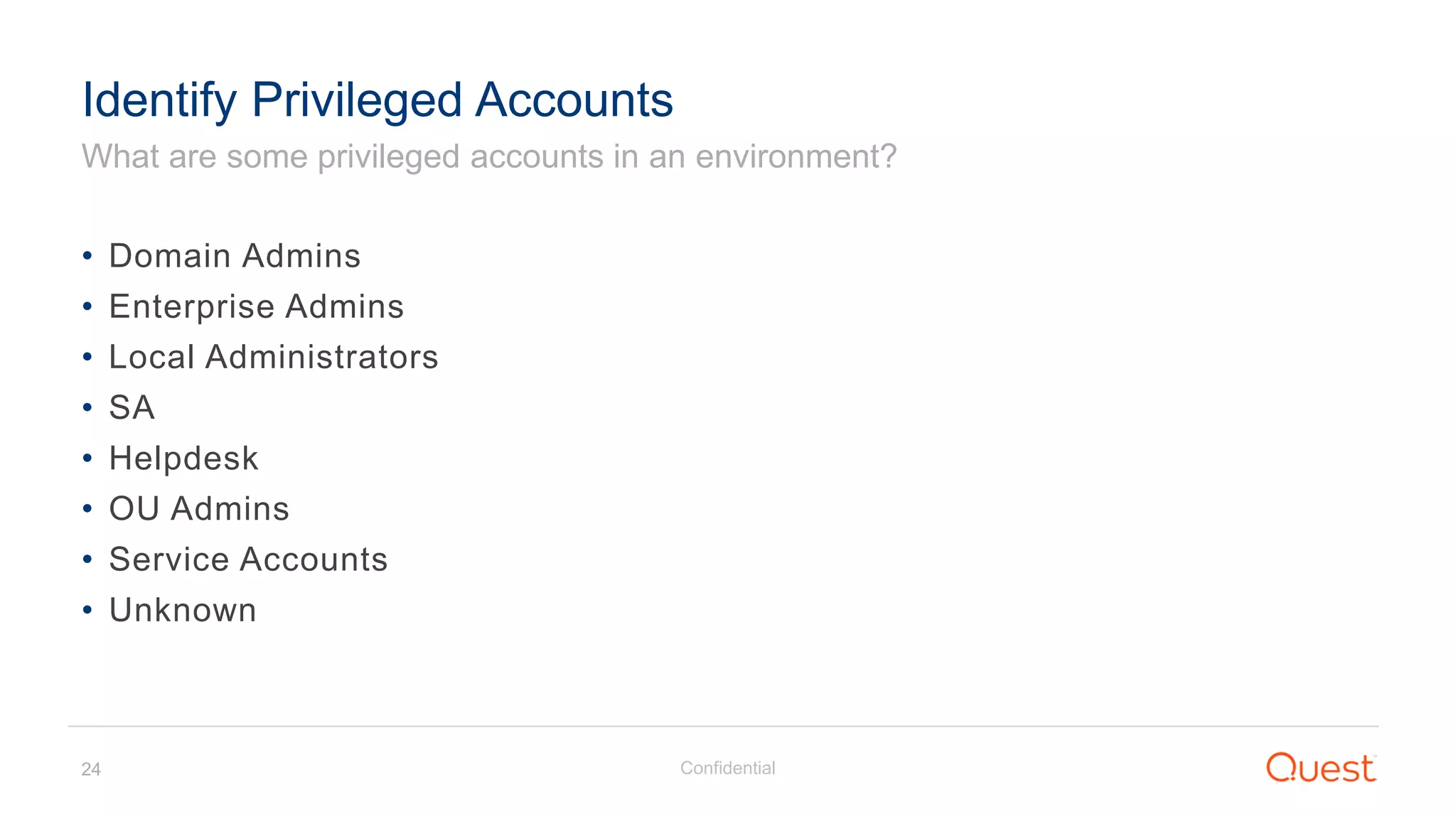
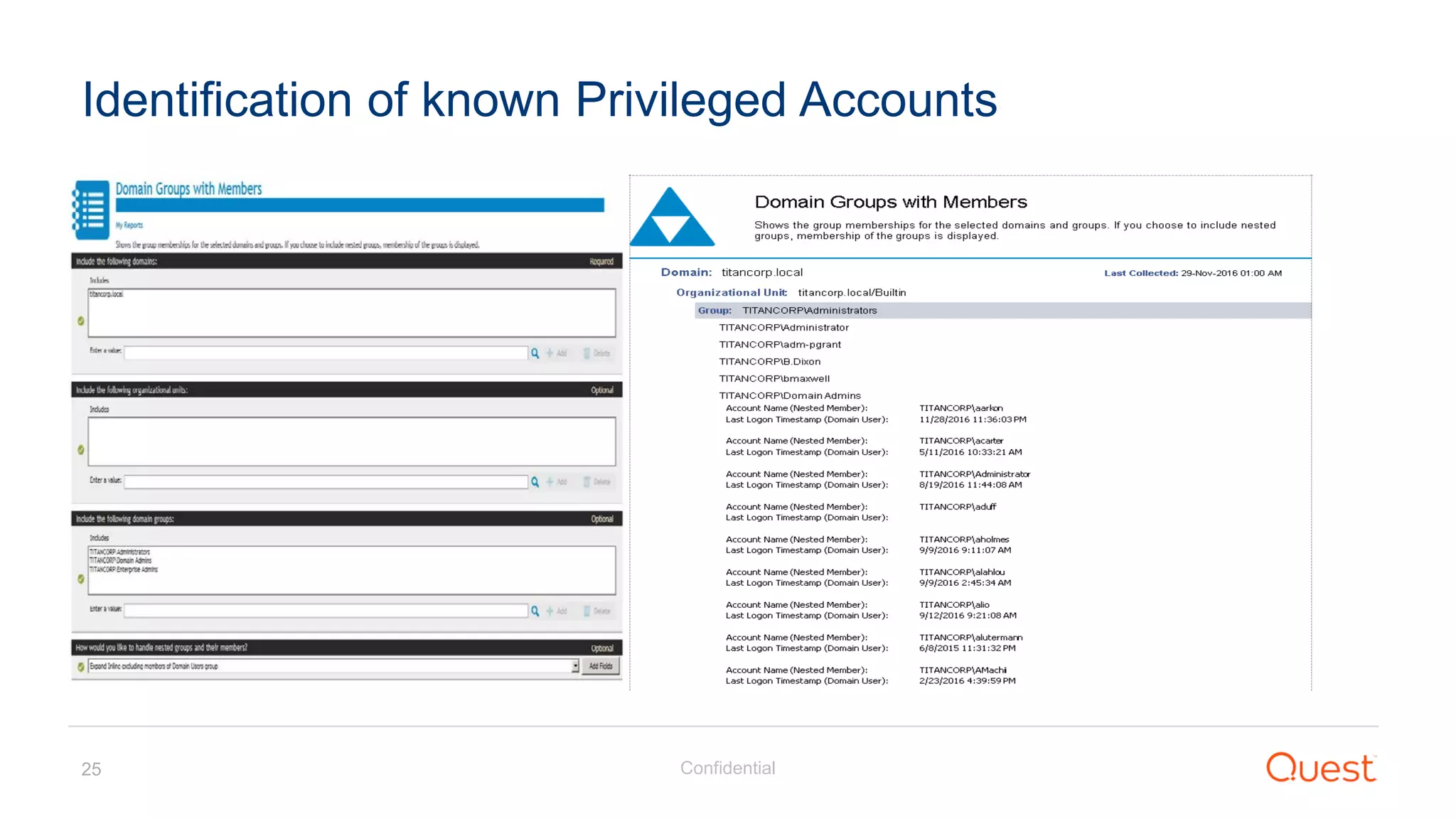
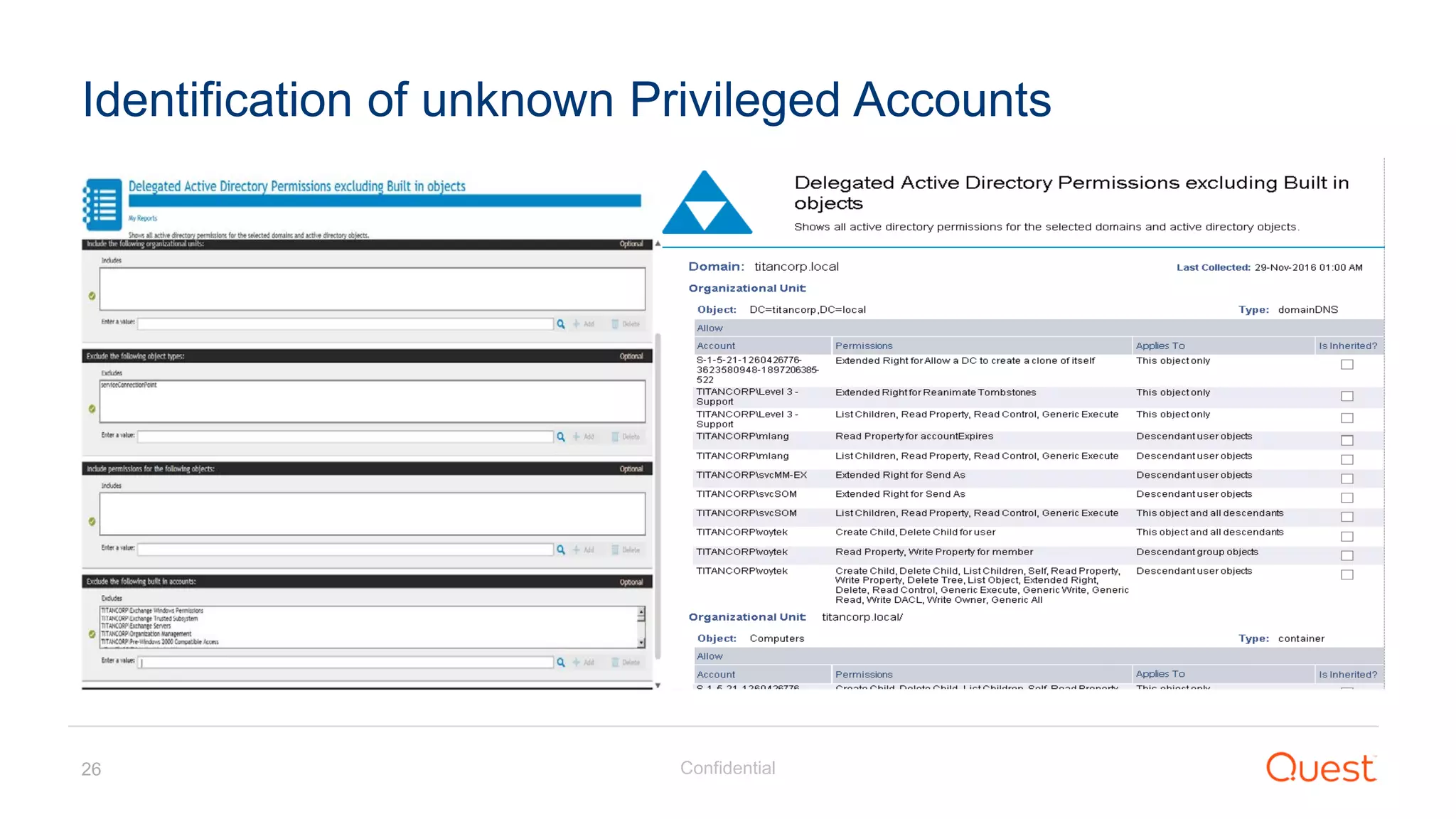
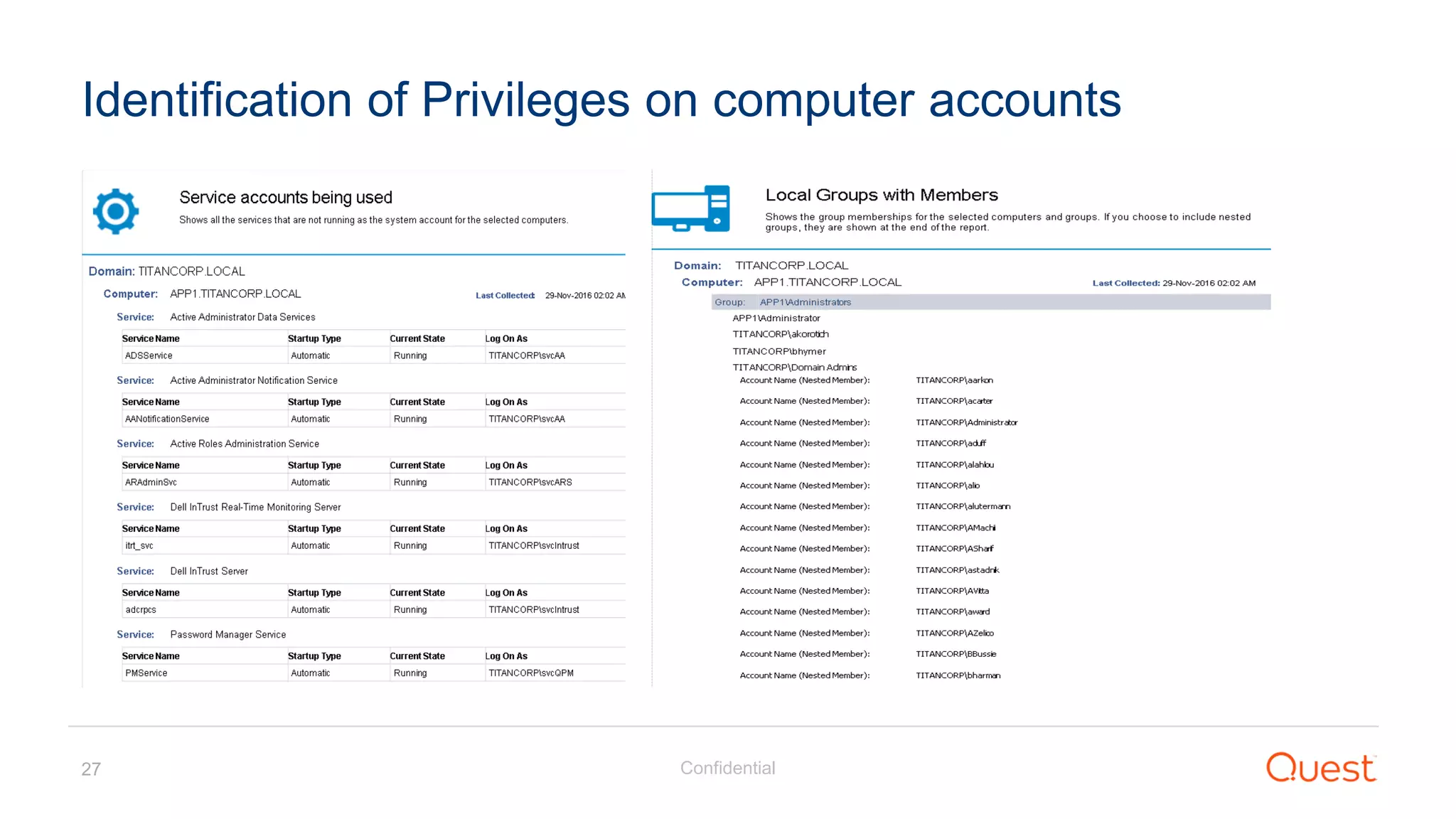
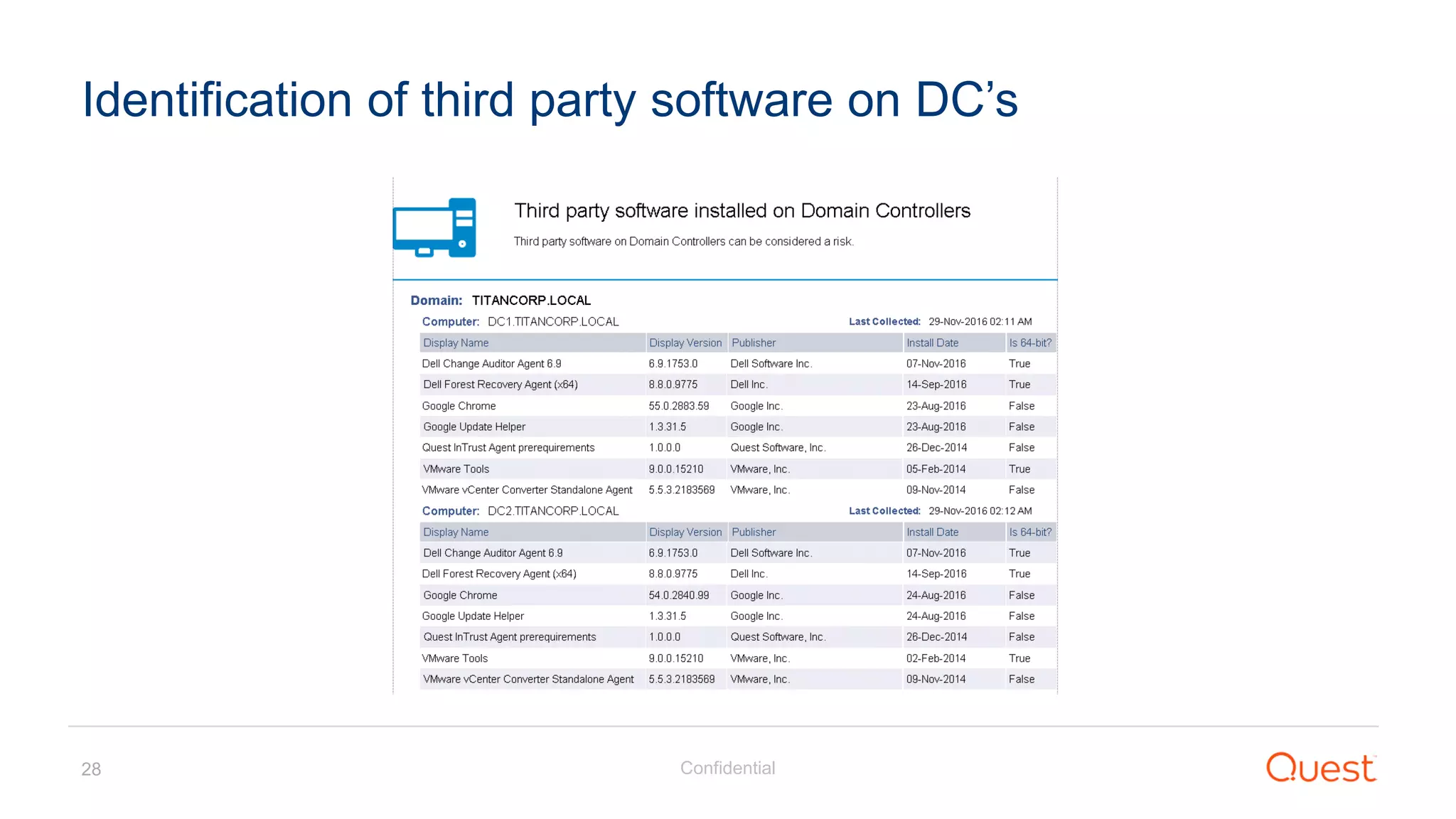
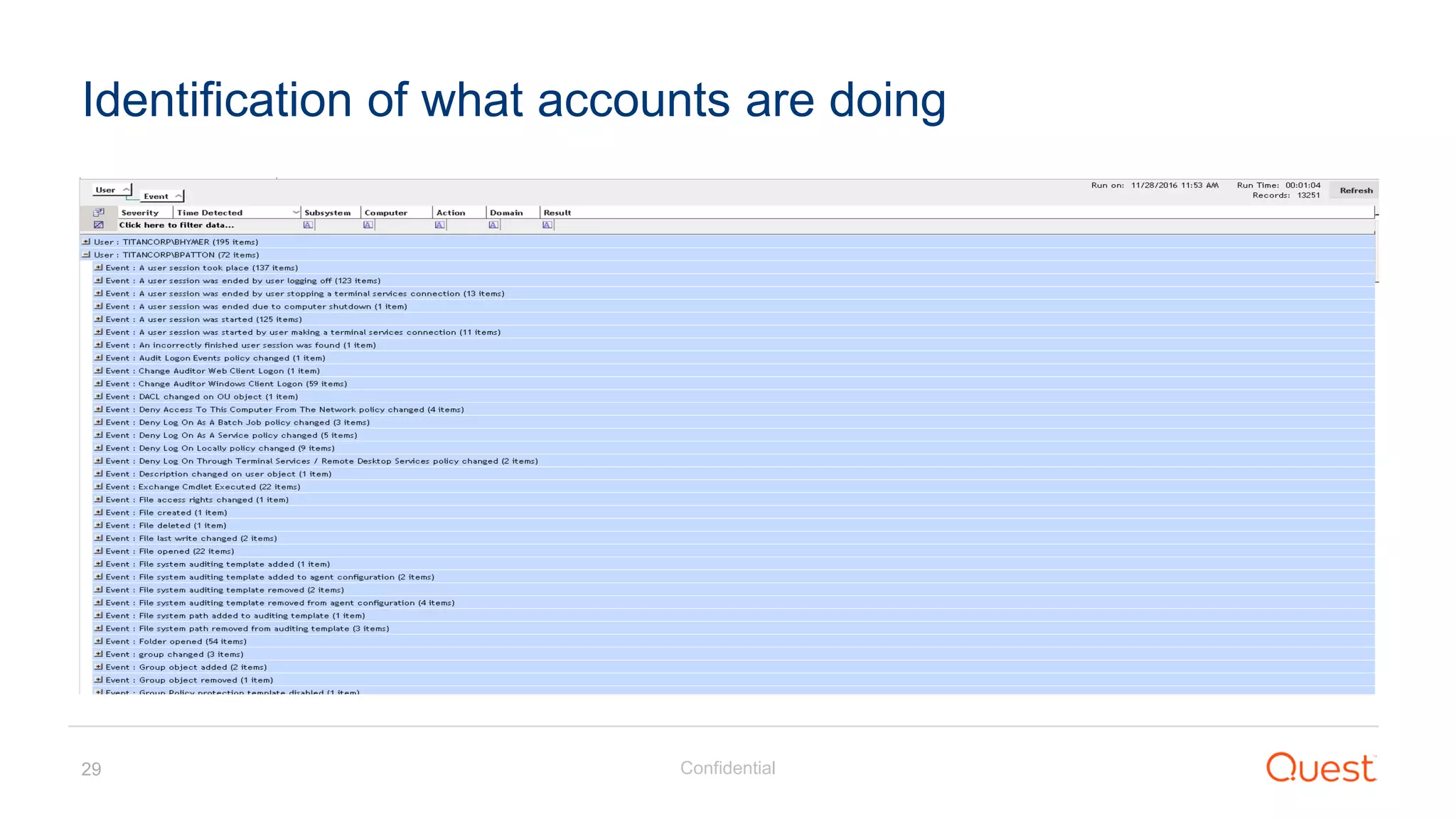
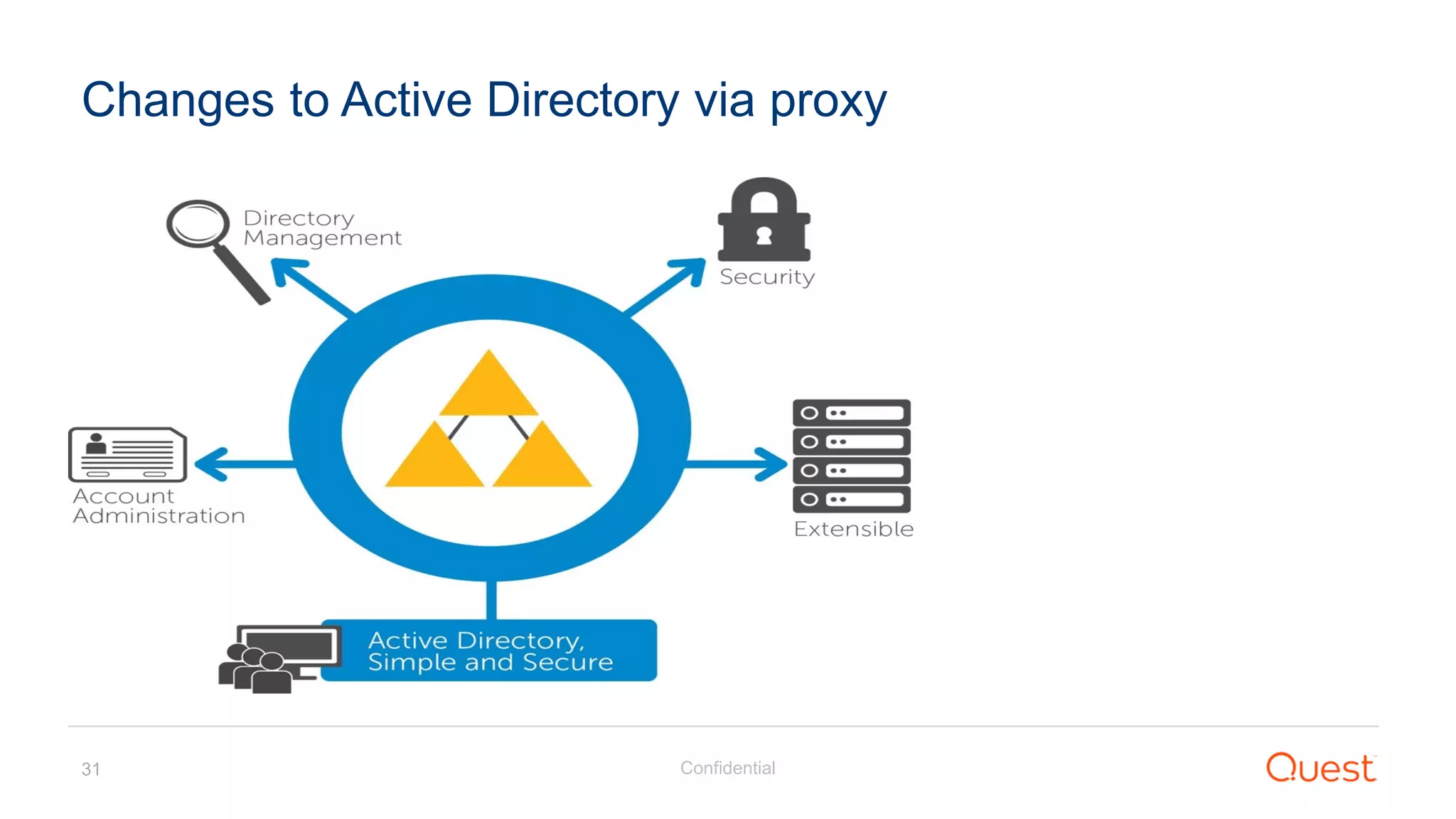
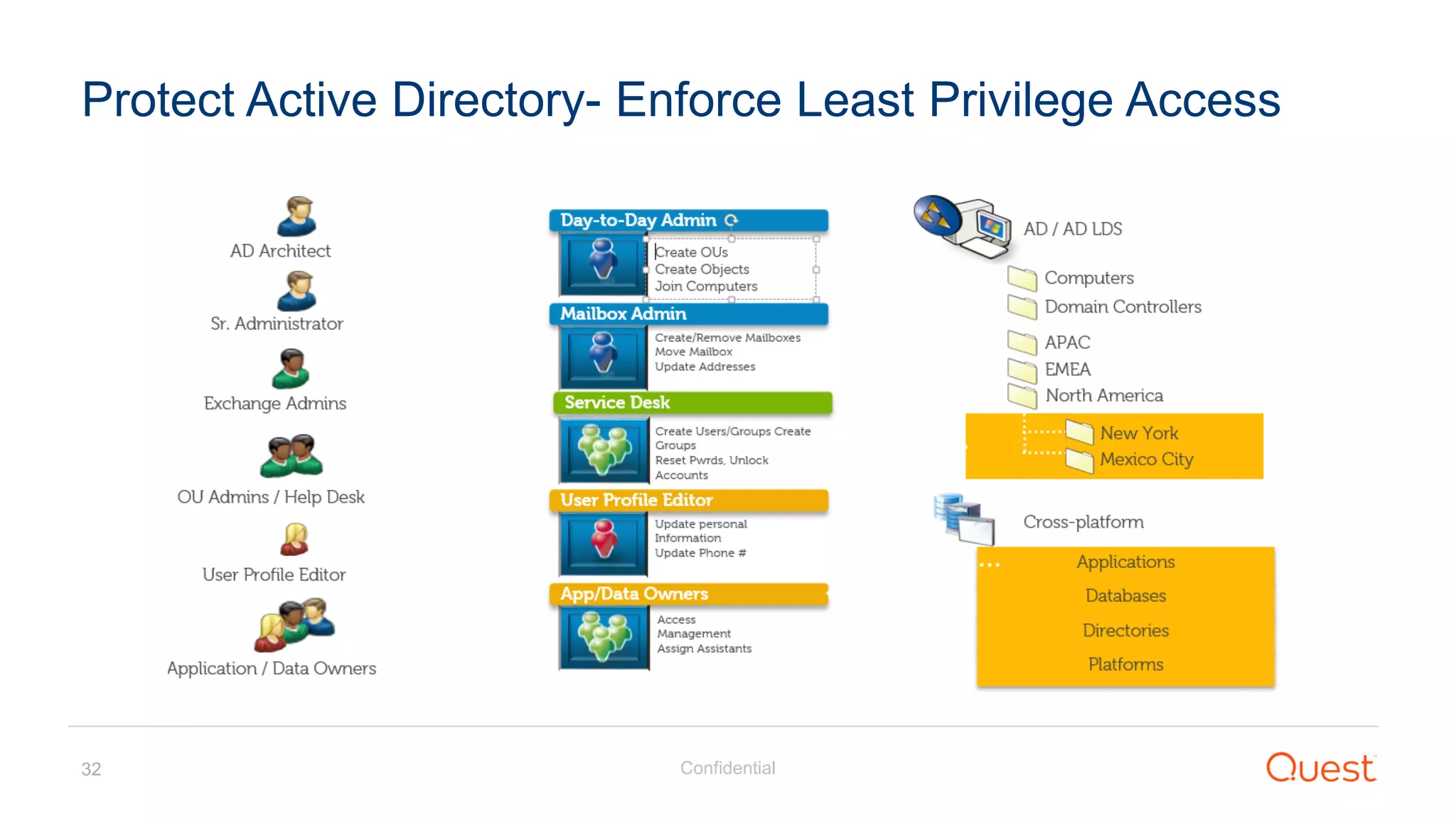
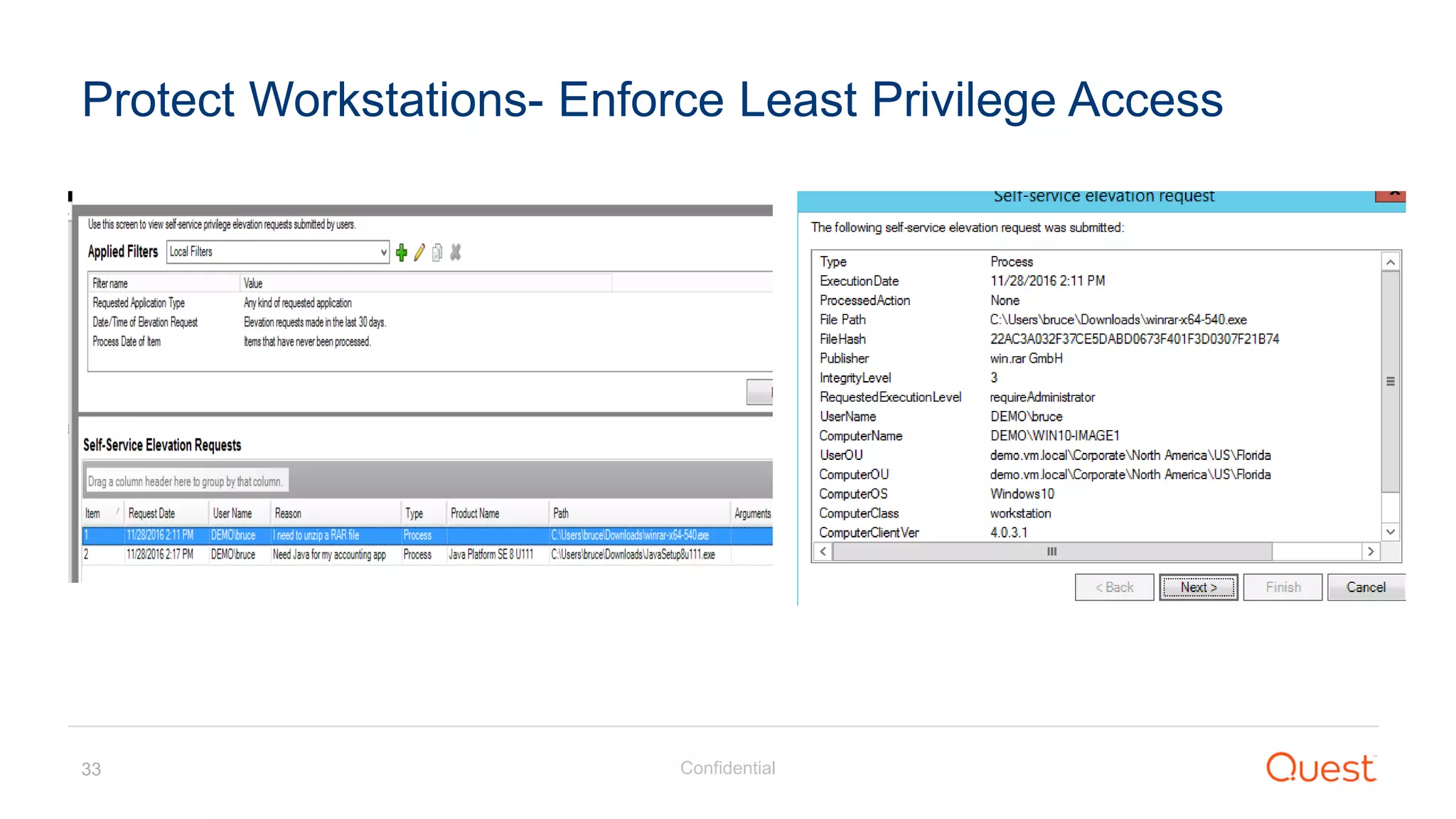
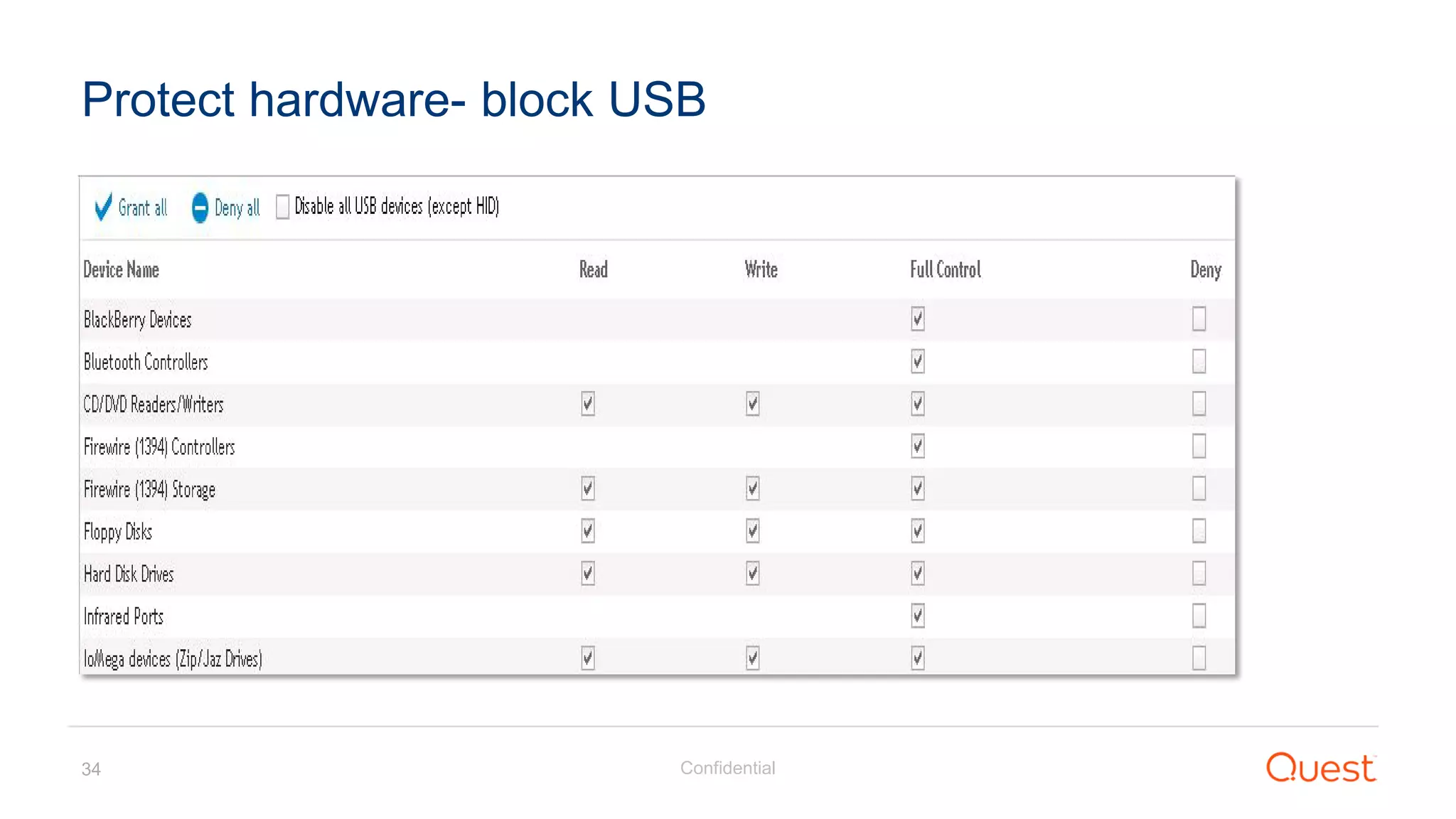
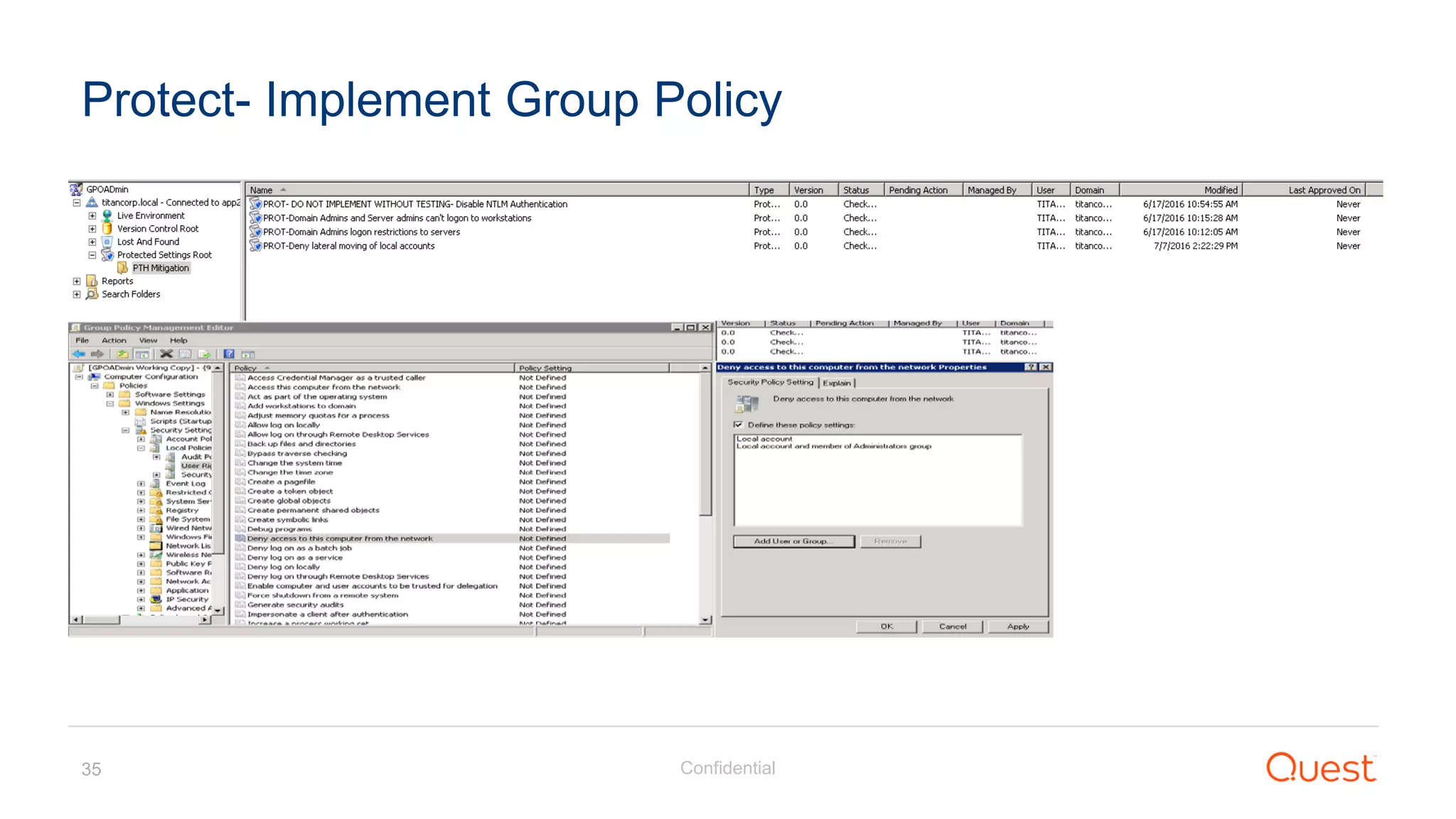
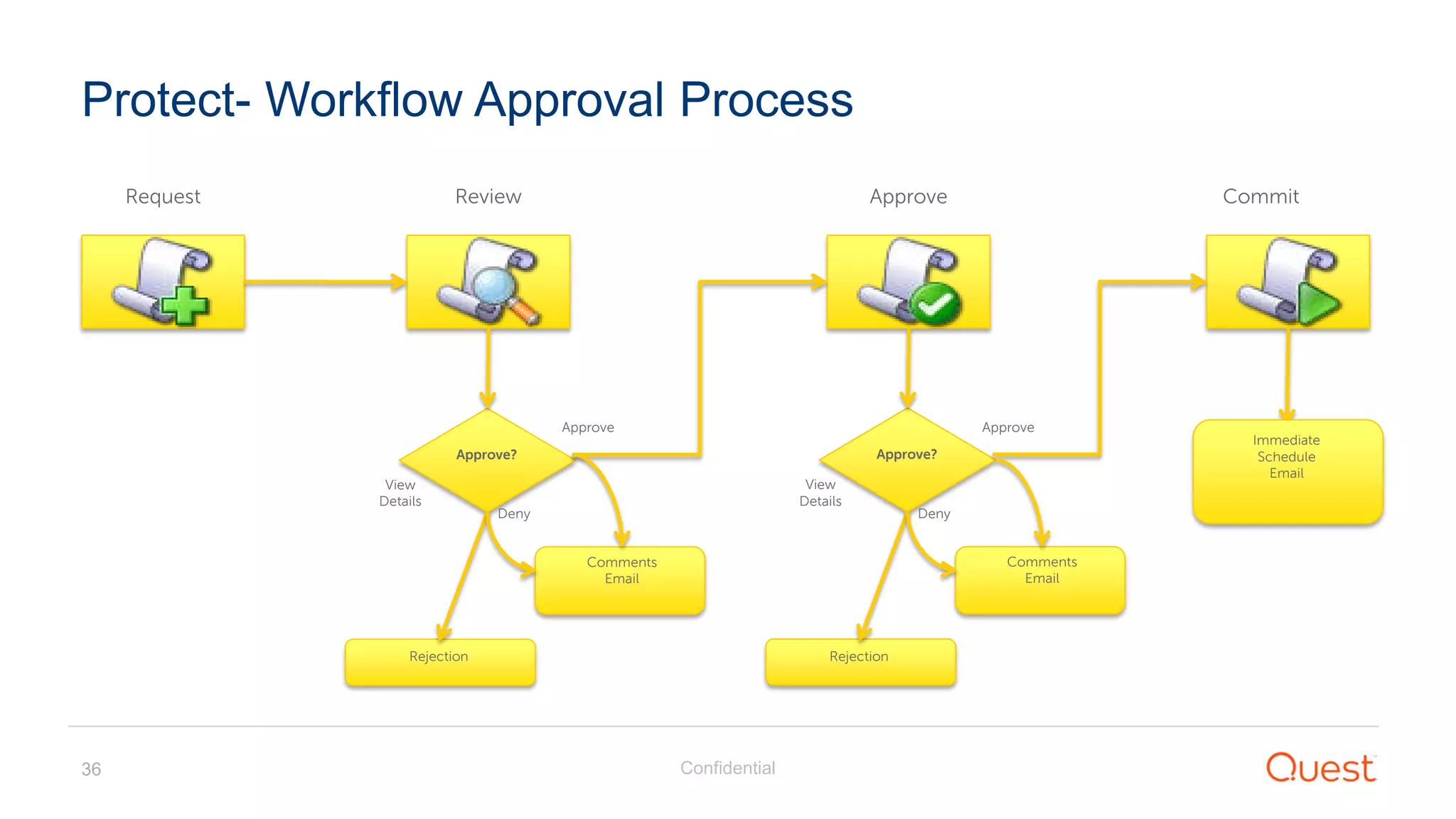
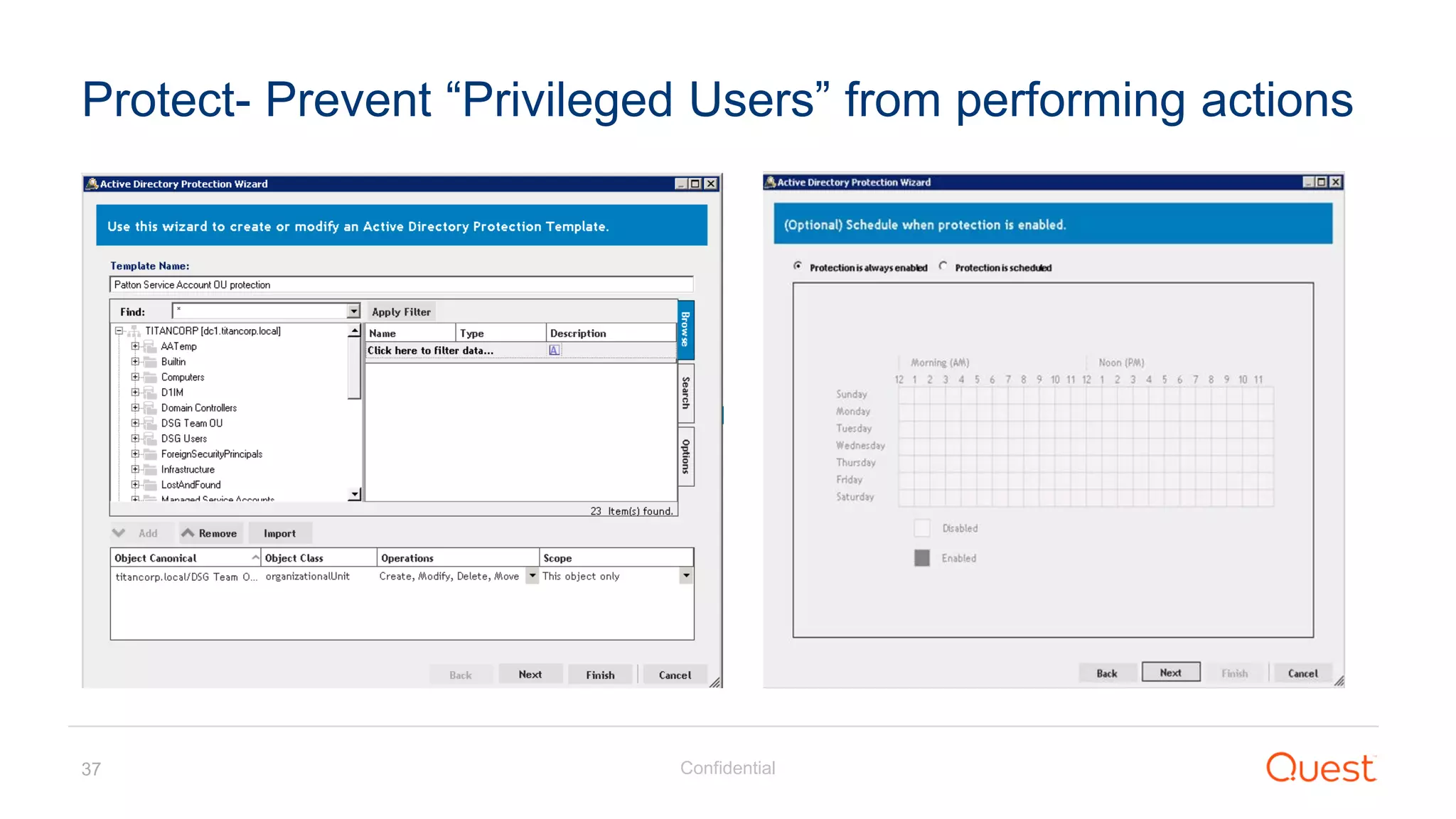
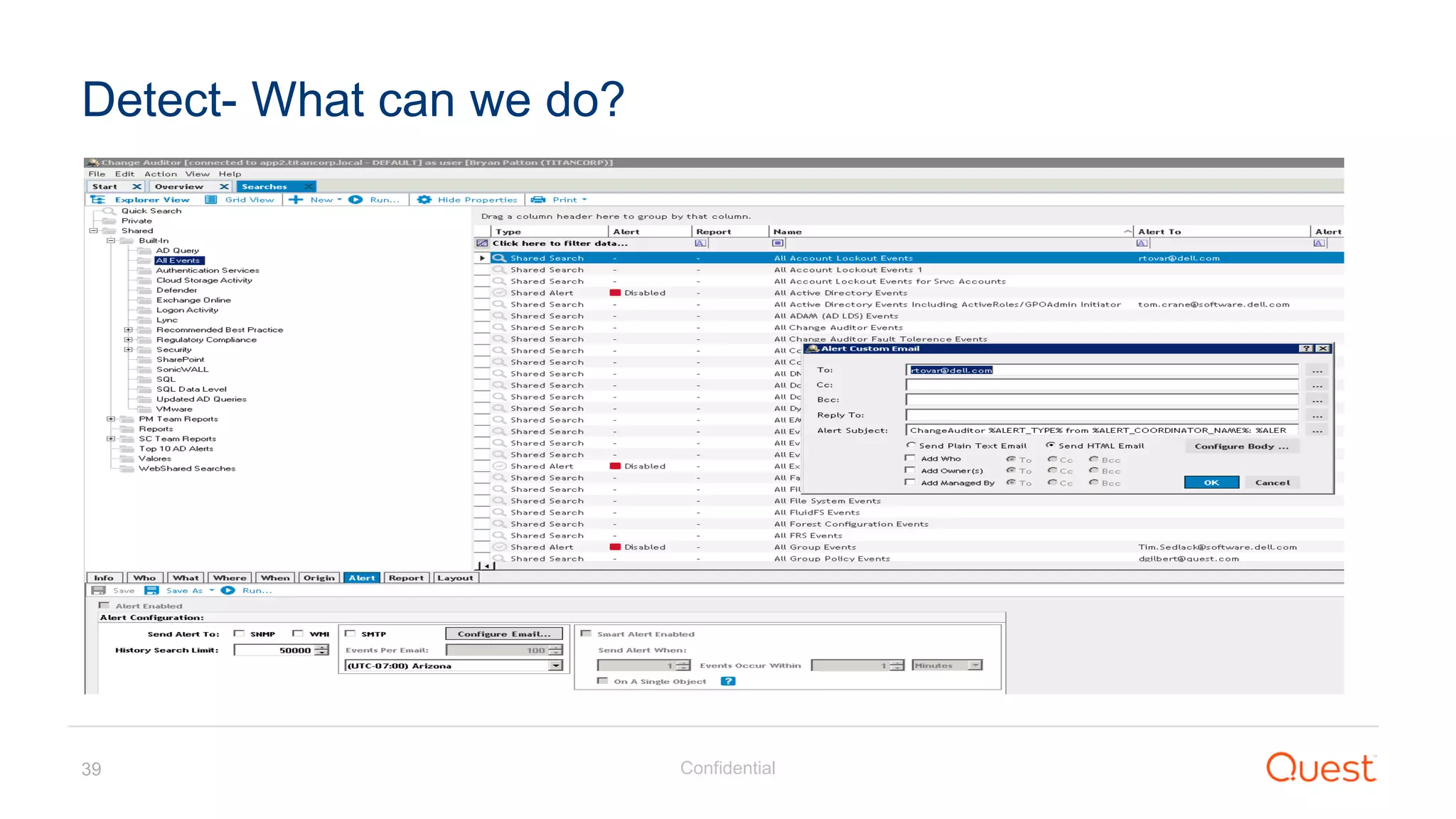
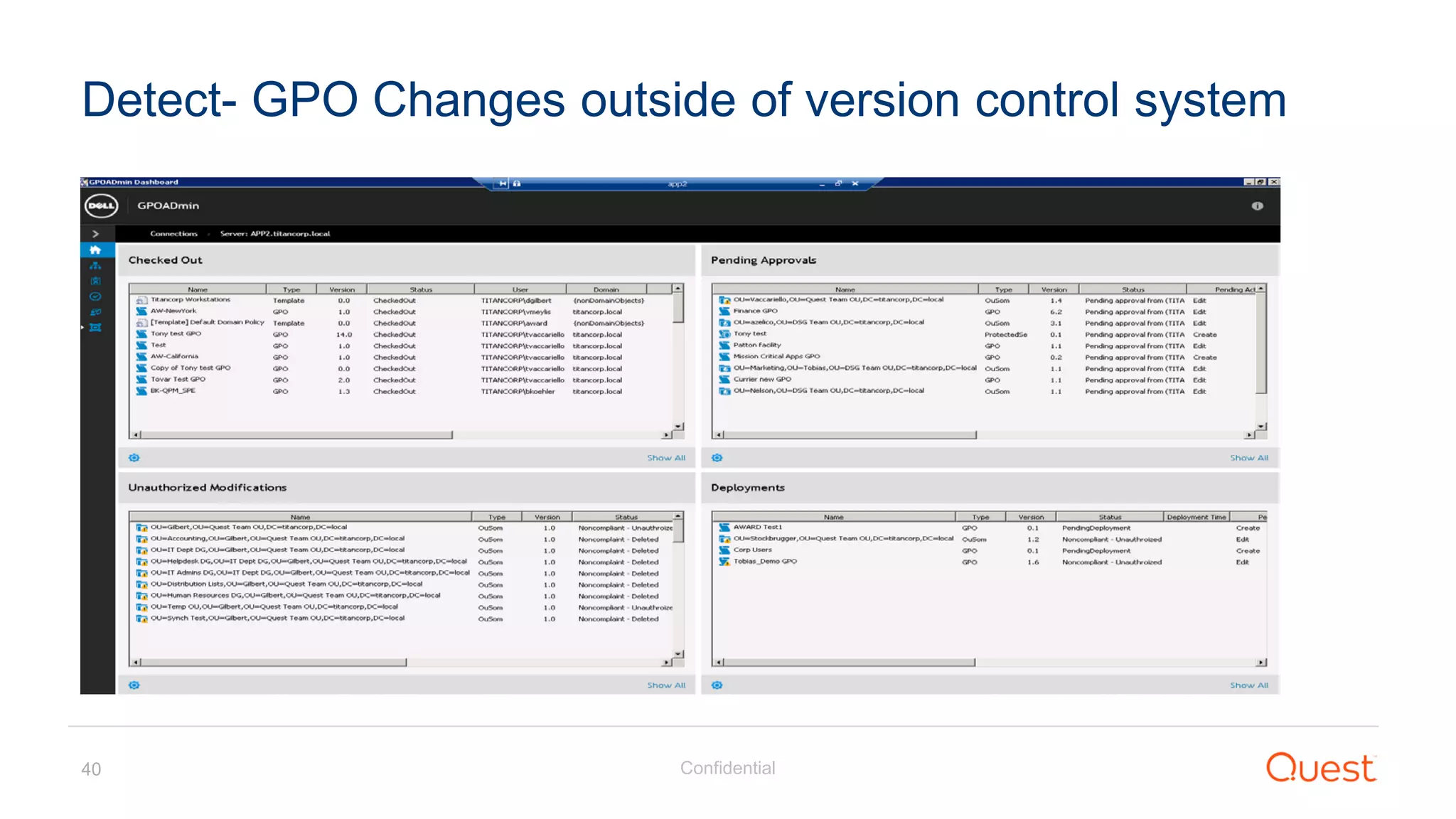
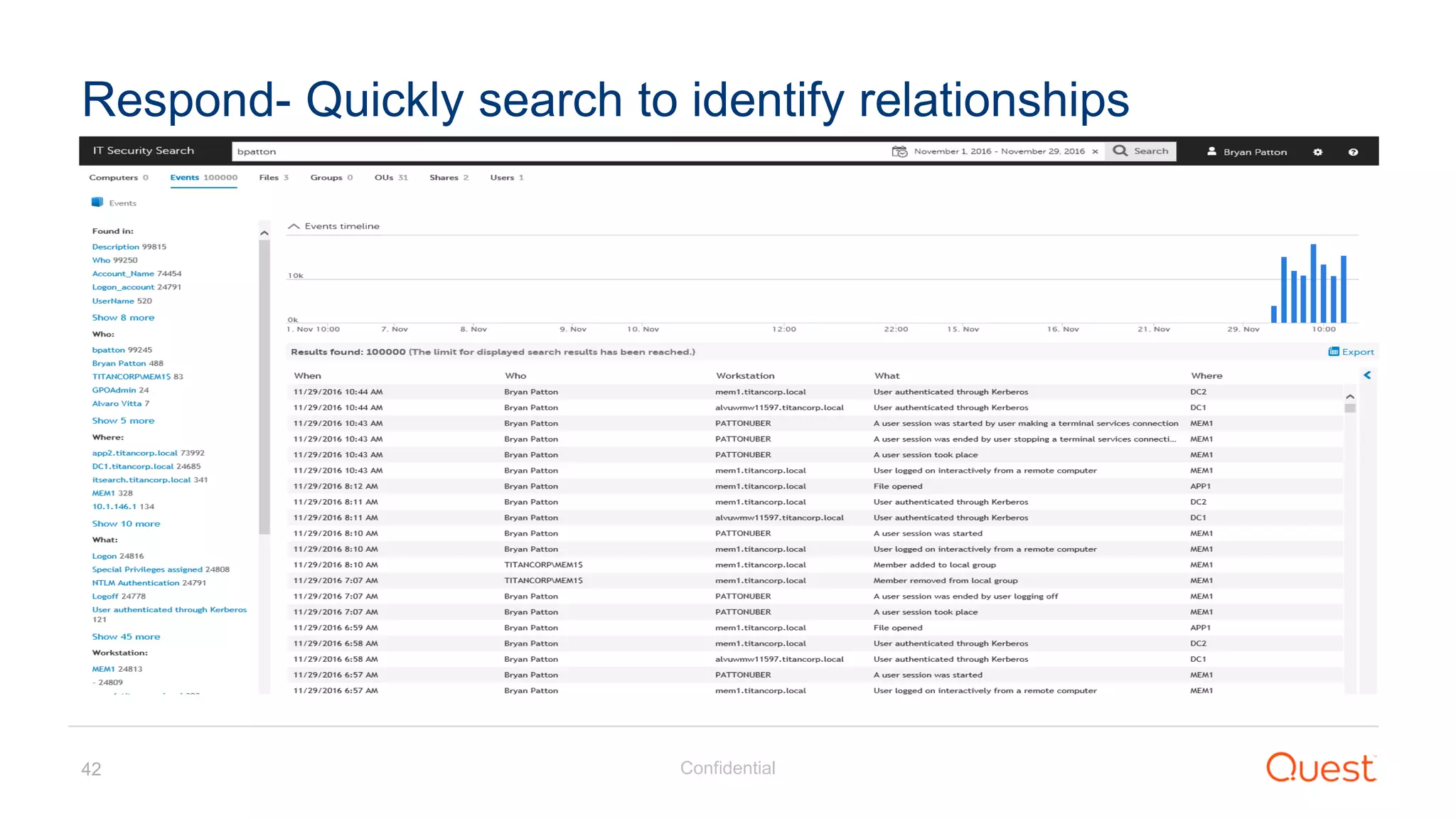
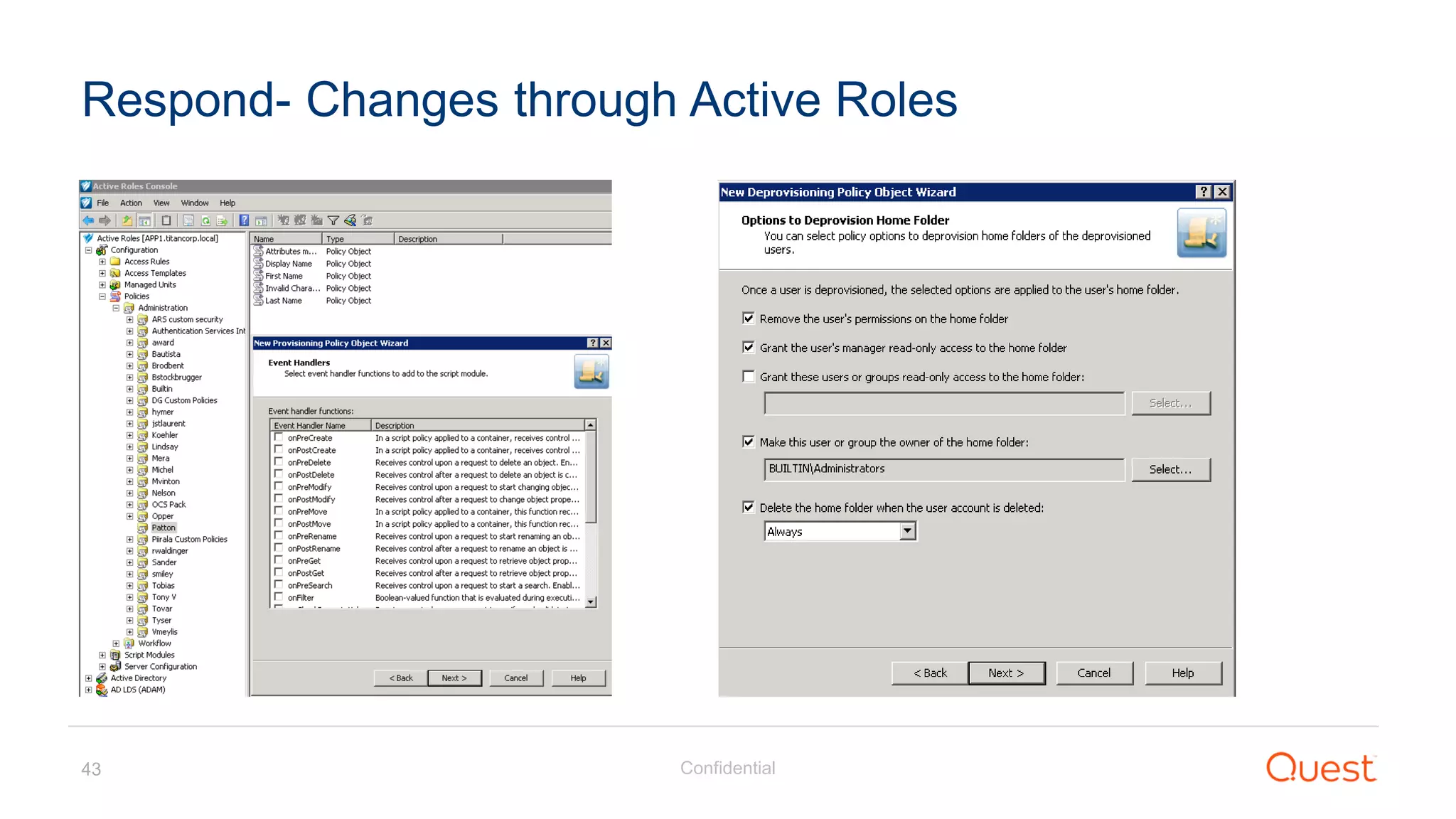
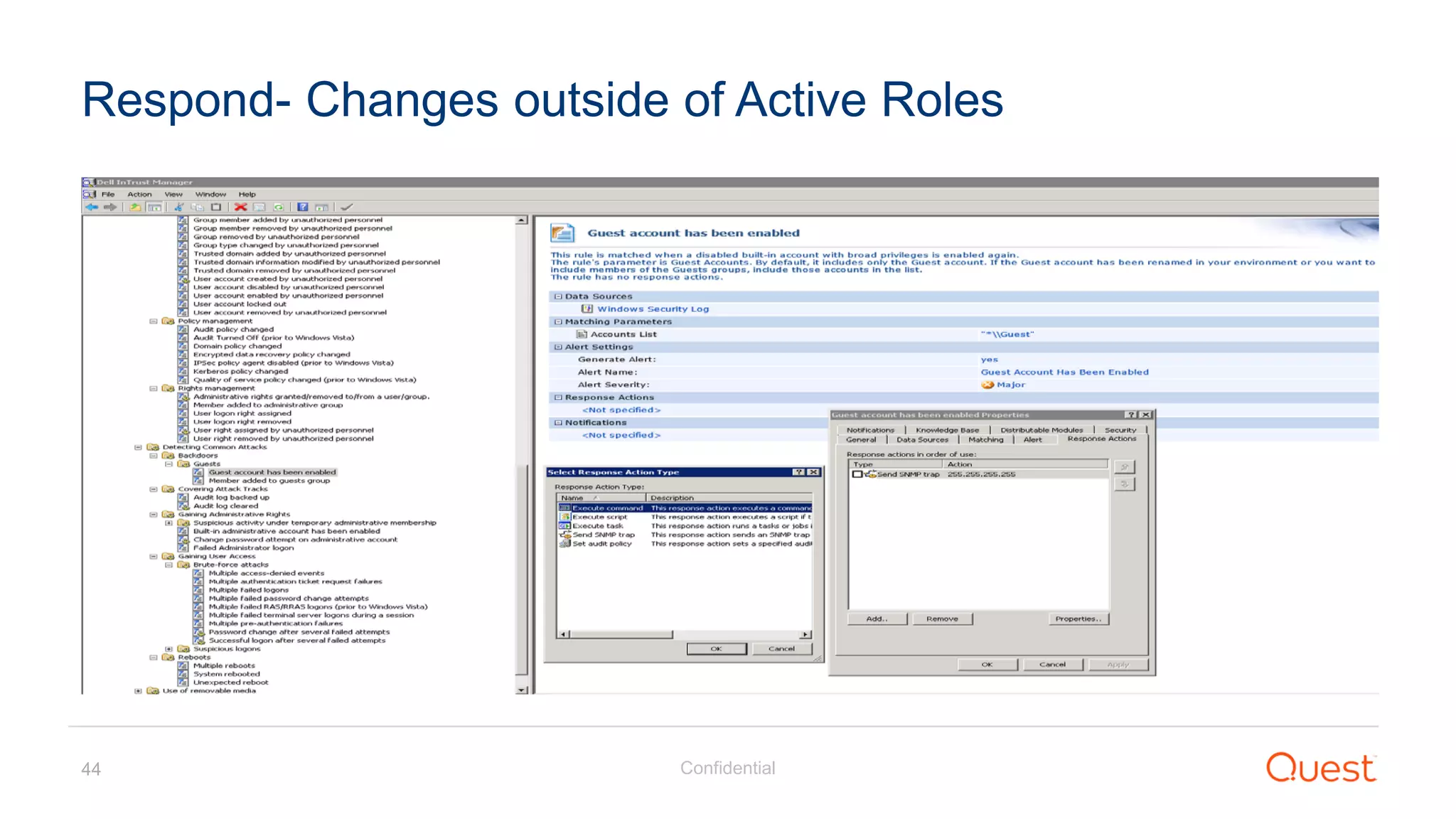
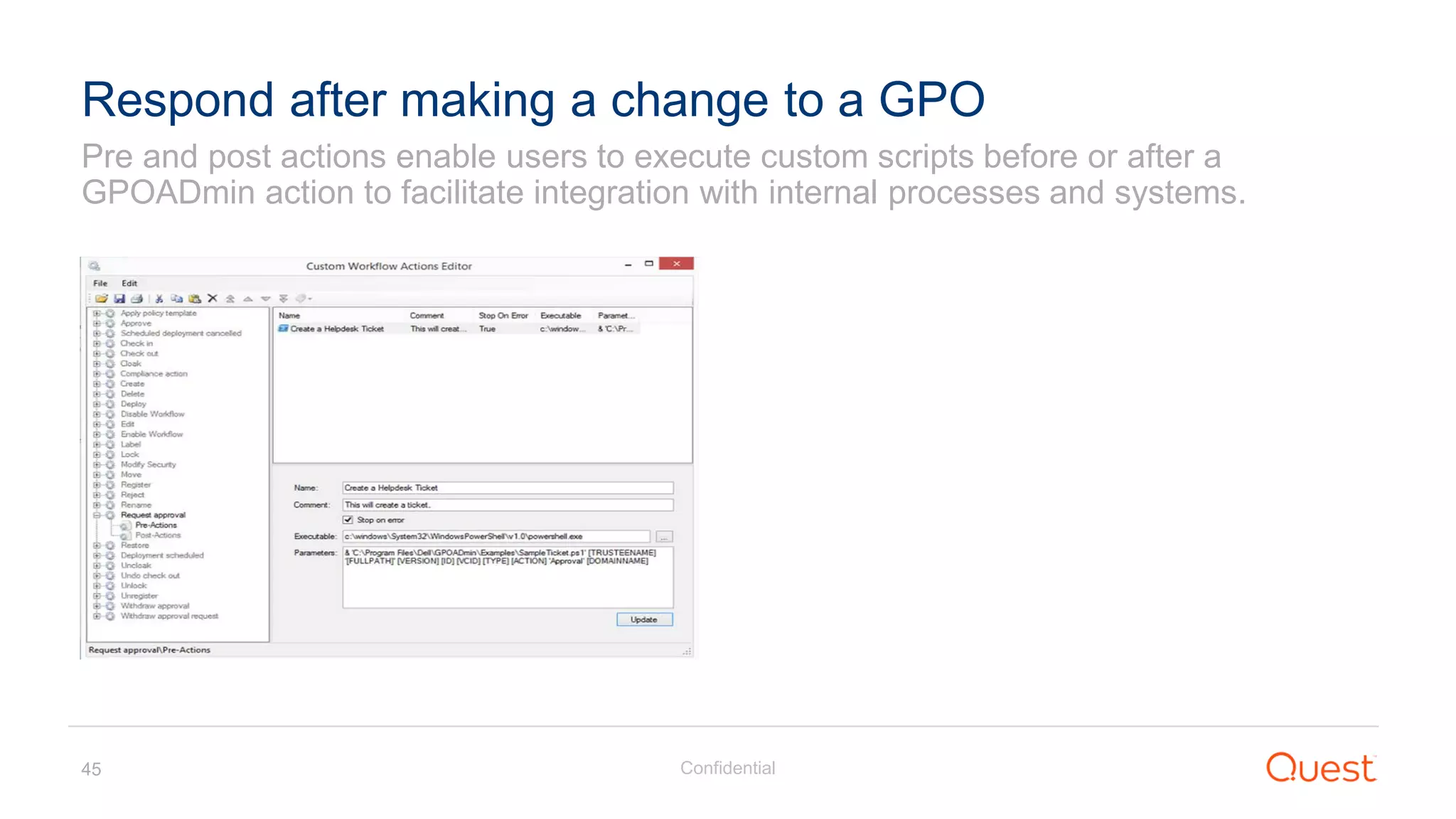
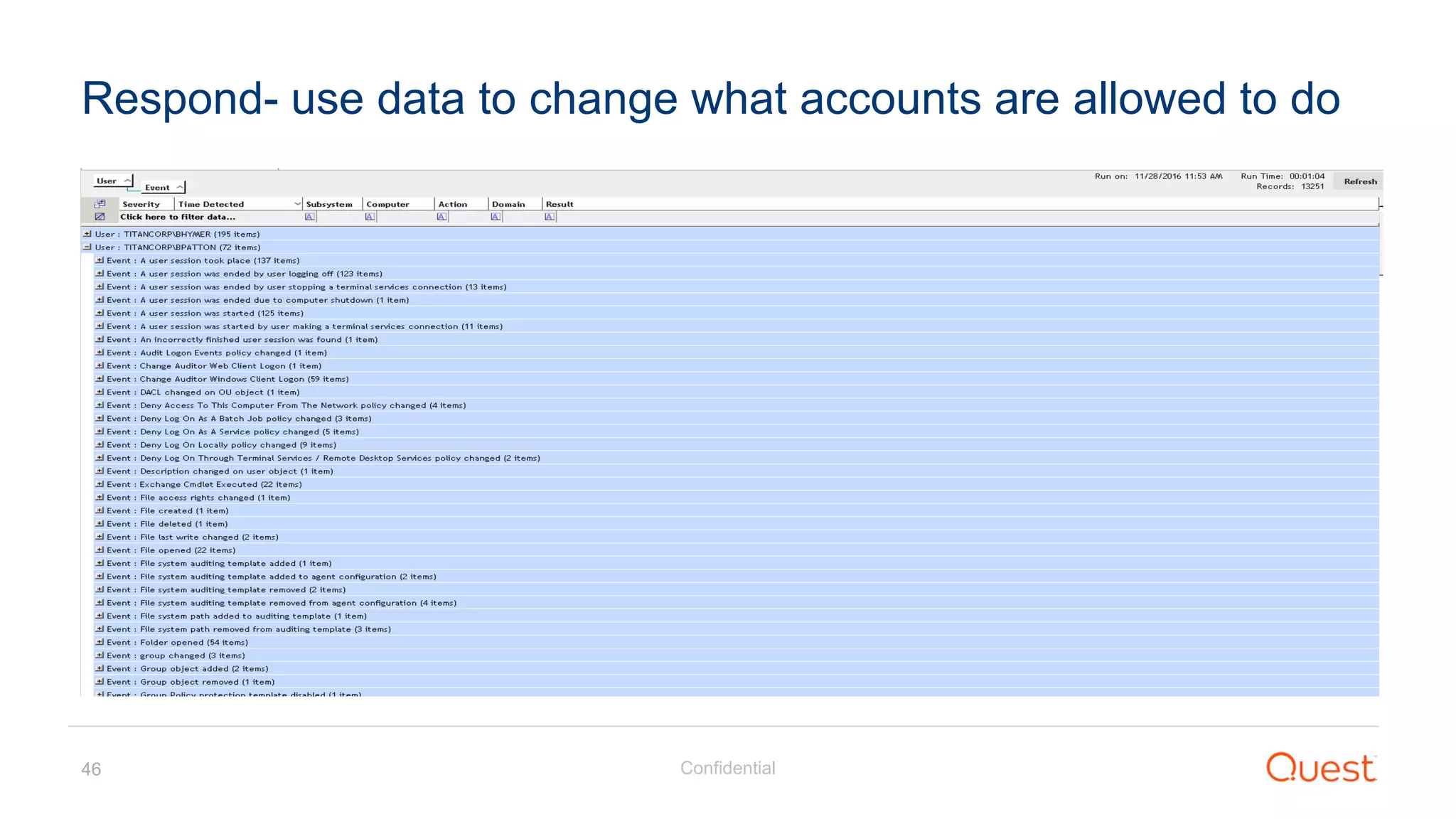
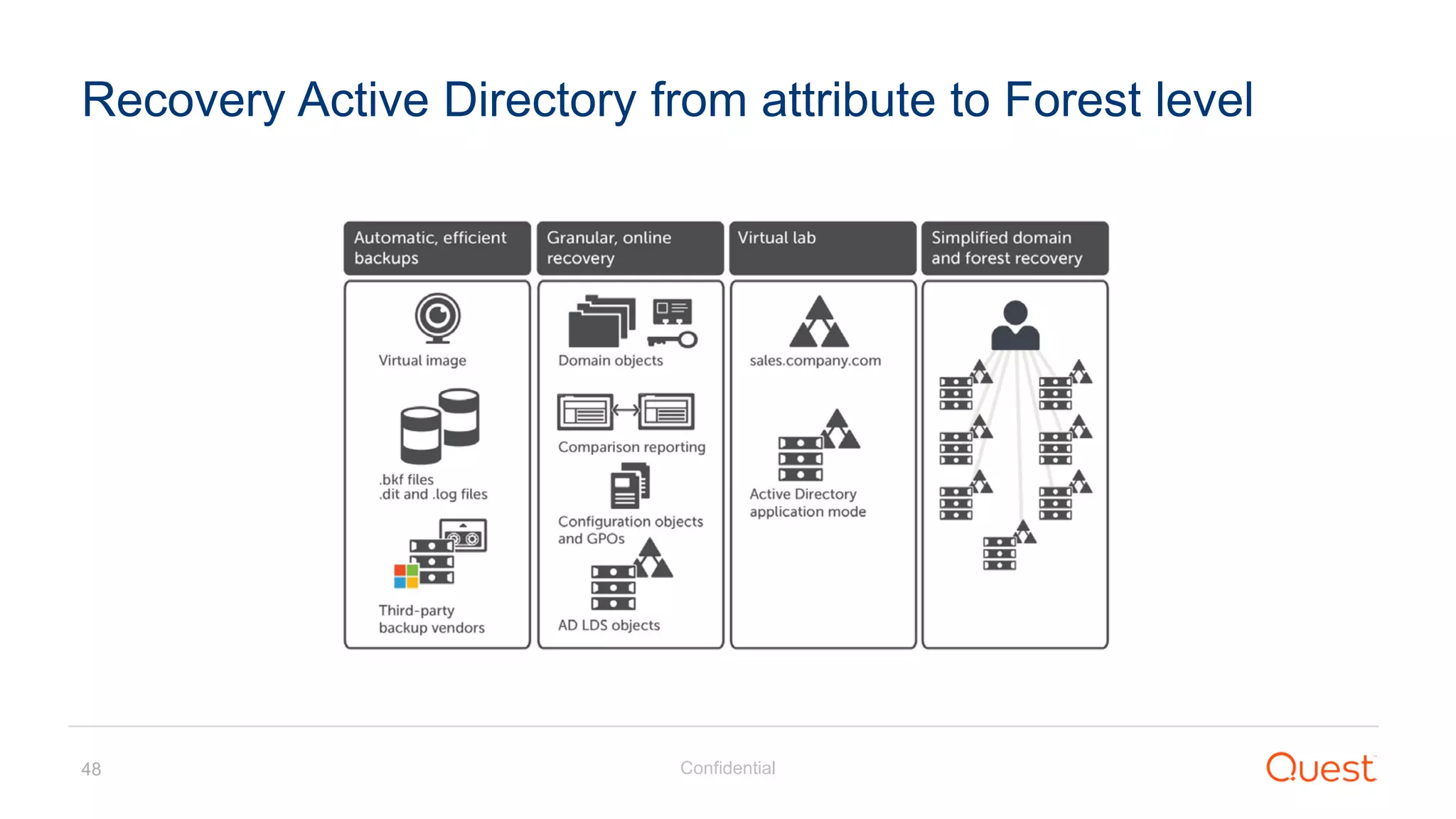
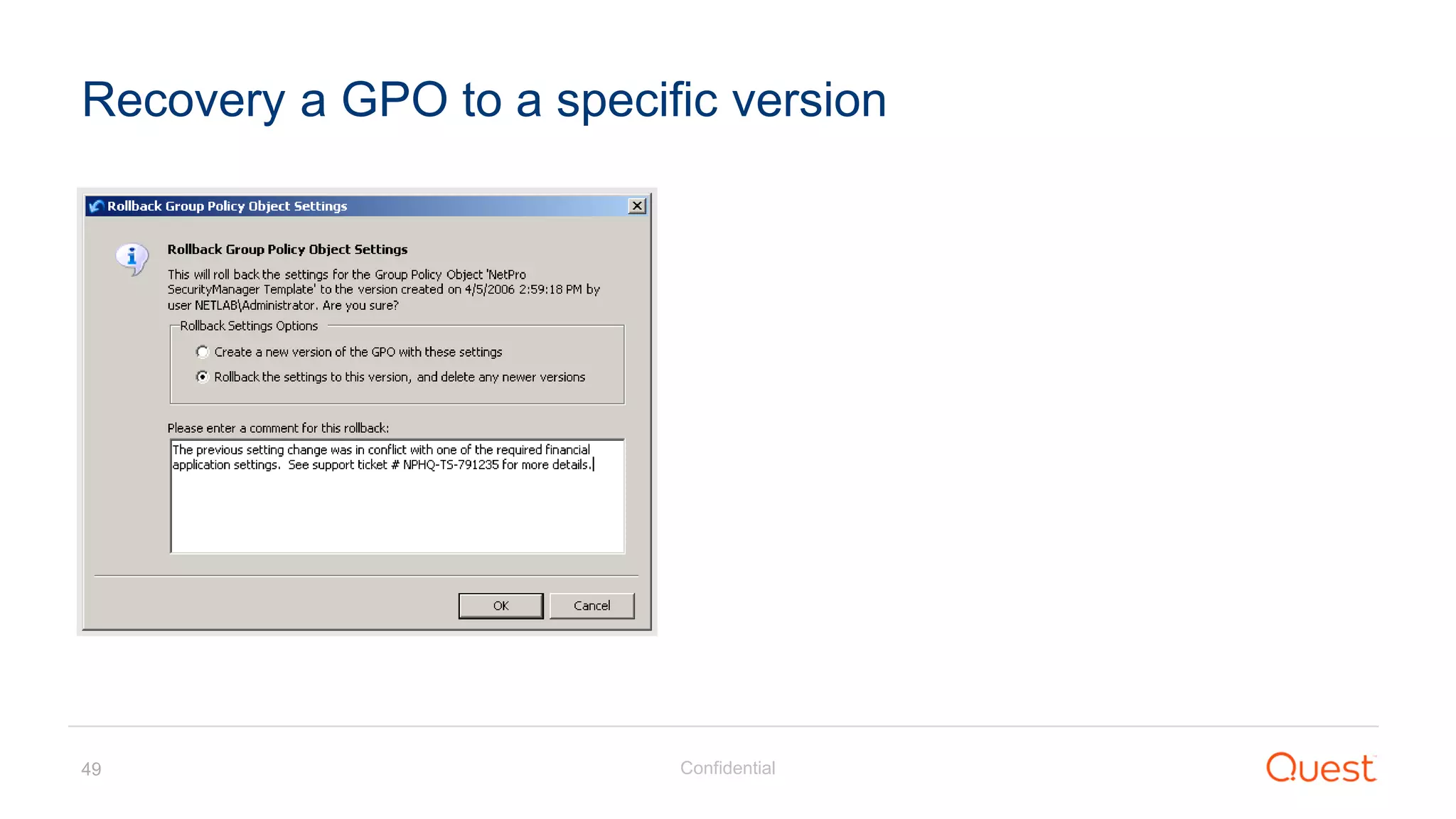
The document discusses the Enhanced Security Administrative Environment (ESAE) and its role in protecting privileged credentials within Active Directory (AD) systems, highlighting key concepts such as logon types, security dependencies, and the challenges posed by Active Directory forests. It outlines a 3-tier security model to isolate administrative roles and discusses alternatives for privilege management, including two-factor authentication and proxy technologies. Additionally, the document emphasizes the importance of understanding security dependencies and implementing good reporting practices to mitigate risks associated with privileged accounts.