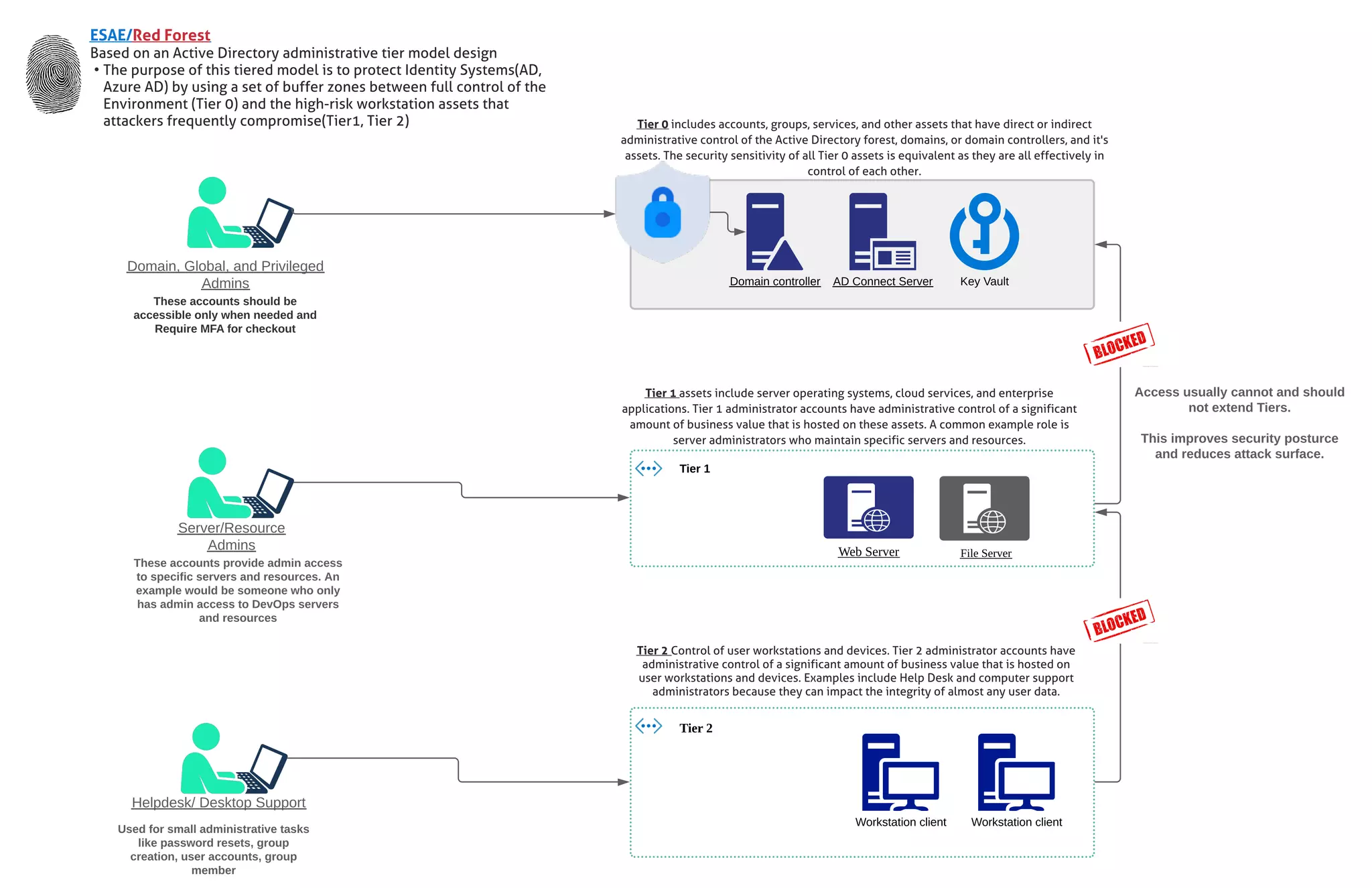
The document outlines a tiered administrative model for managing user and resource access, highlighting the differences between Tier 0 (high-risk control) and Tier 1/Tier 2 (moderate-risk user workstations). It emphasizes the importance of restricting access to enhance security and protect sensitive data, with specific examples of administrator roles and their permissions. Multi-factor authentication (MFA) is recommended for sensitive accounts to minimize security risks.