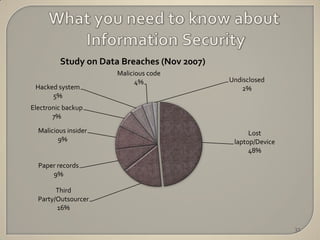
The document discusses the principles of privacy and confidentiality in clinical research, emphasizing the importance of protecting personal health information (PHI) in accordance with HIPAA regulations. It outlines the rights of patients regarding their health information, the responsibilities of healthcare providers, and the consequences of violating privacy laws. Additionally, it details procedures for handling PHI and the significance of maintaining confidentiality to build trust between participants and researchers.