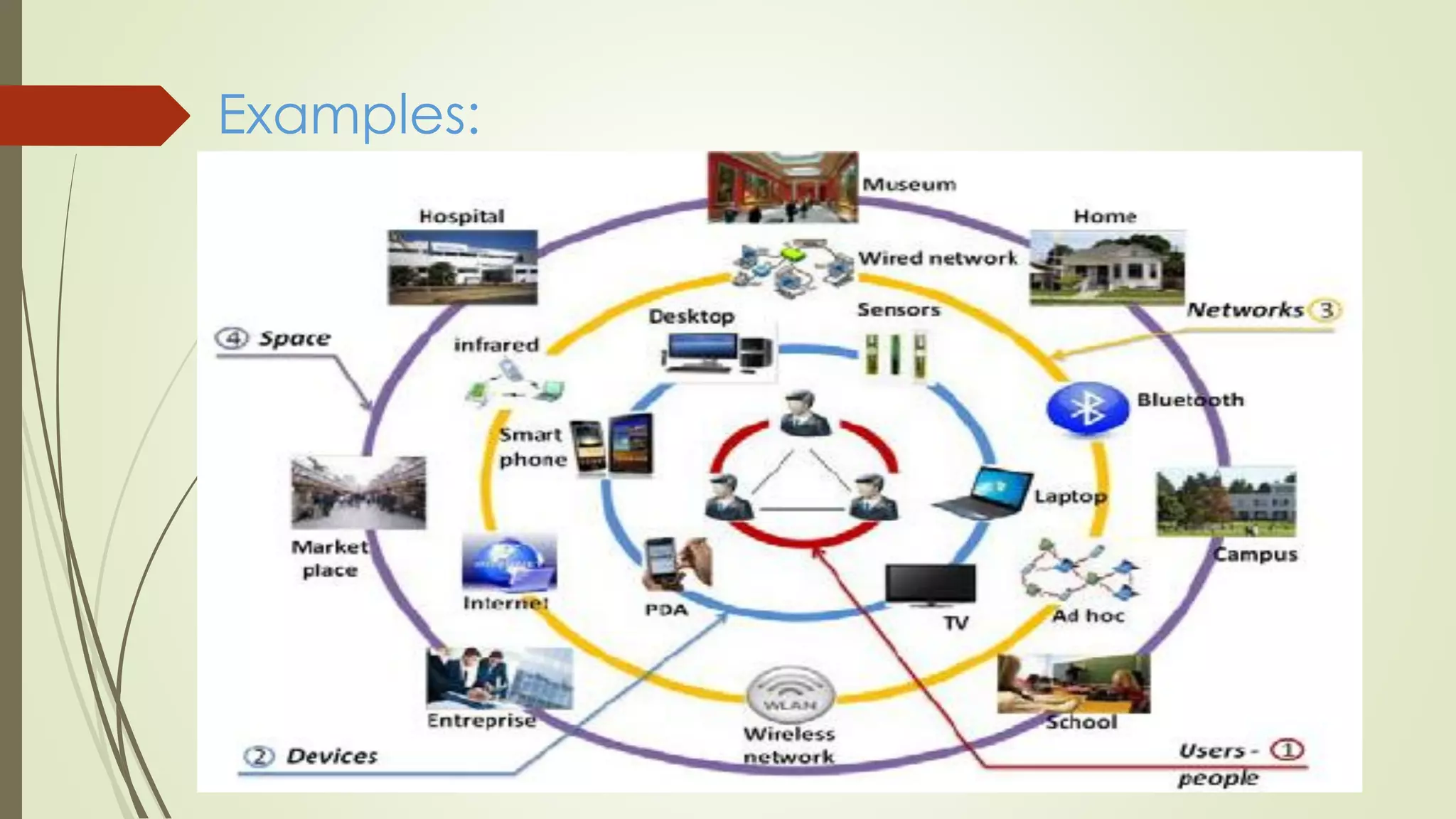
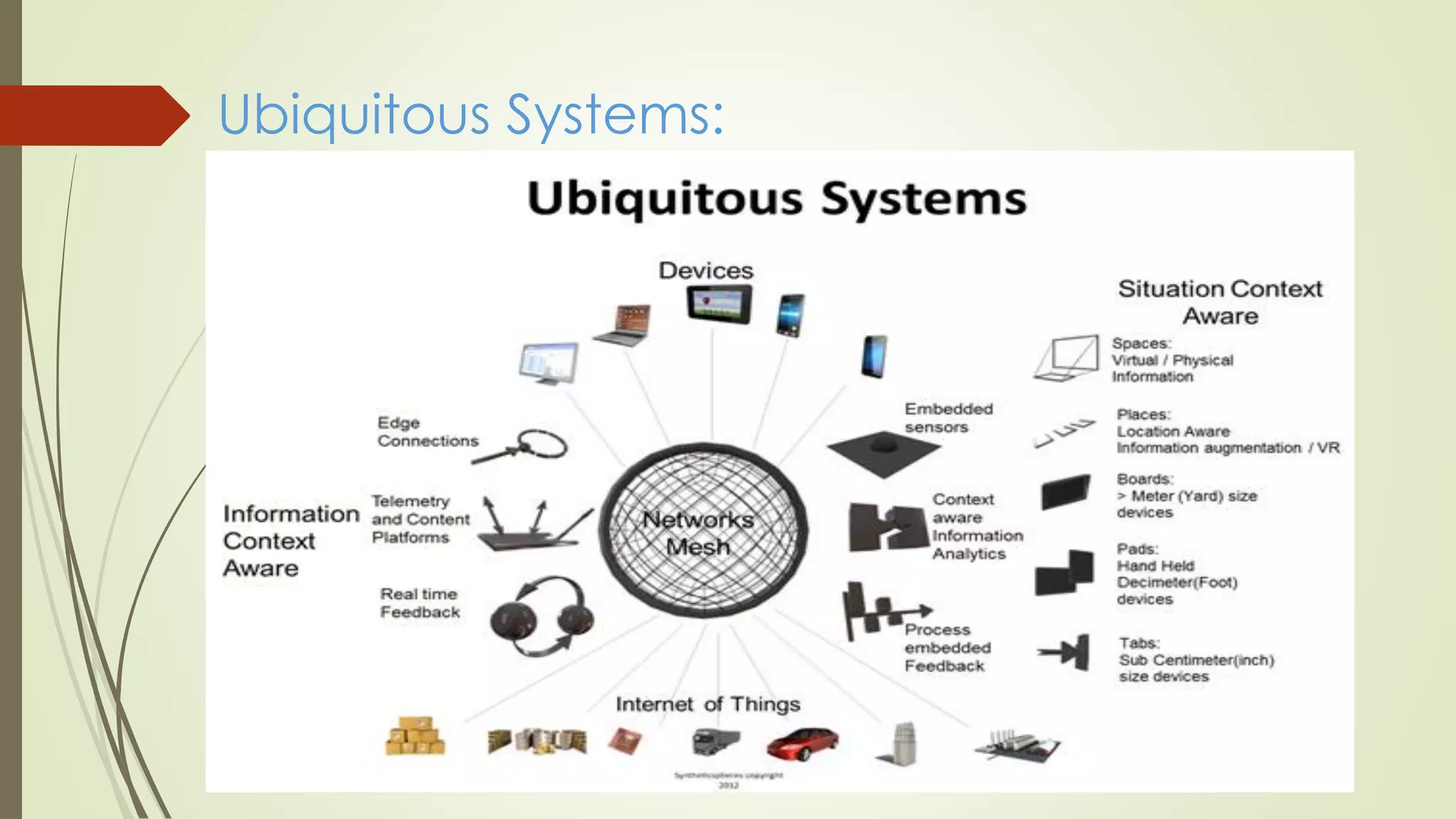
Ubiquitous computing is a post-desktop model where computing is integrated into everyday objects and activities. It allows information access and communication virtually anywhere. Mark Weiser coined the term in 1988 while working at Xerox PARC. Ubiquitous computing aims to make computing mobile and connected through sensors in the environment to enable more effective interaction and analyze user behavior and activities through connected devices like smart TVs and refrigerators. Key challenges include defining appropriate physical interactions and discovering general application features in such a pervasive computing environment.