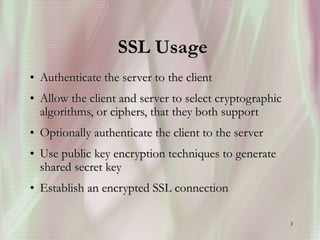
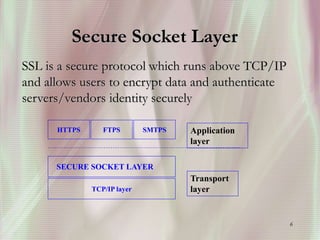
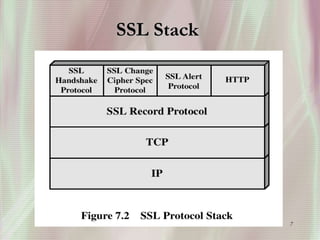
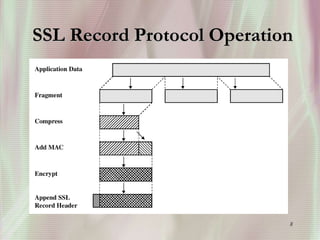
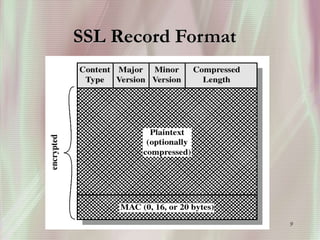
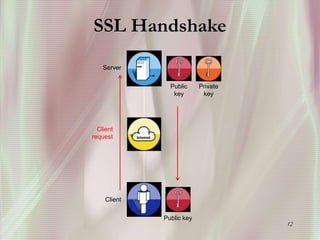
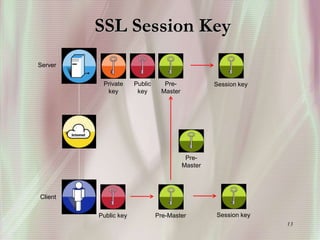
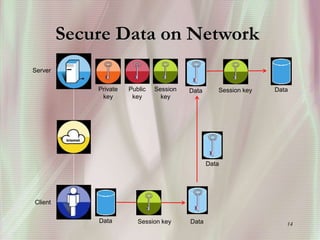
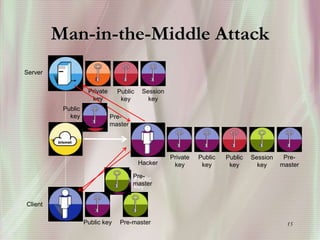
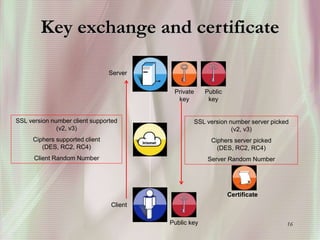
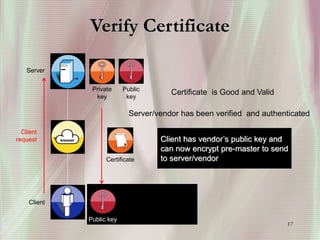
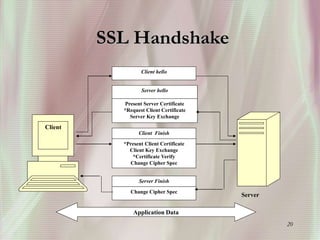
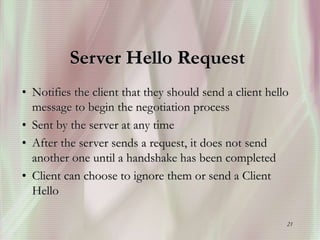
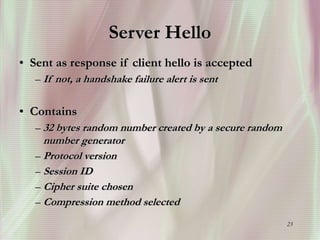
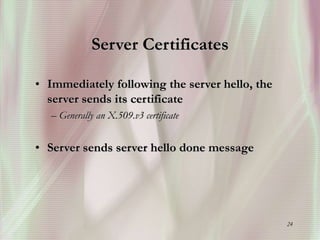
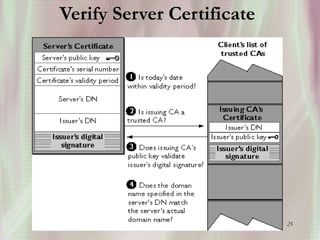
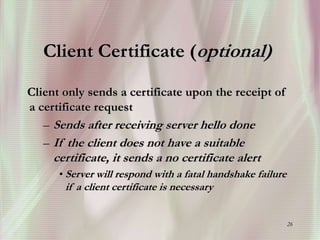
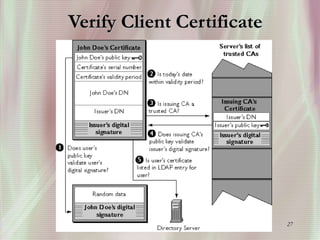
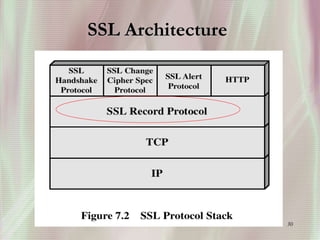
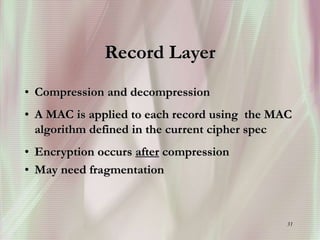
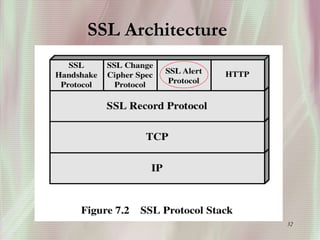
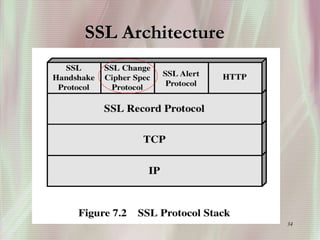
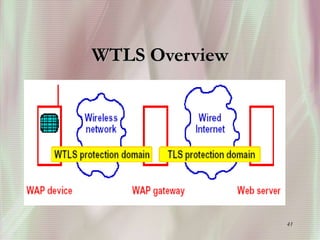
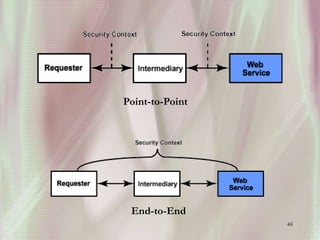
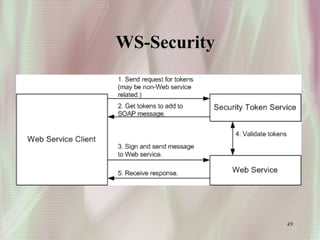
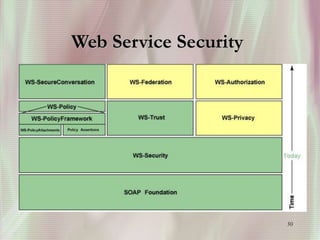
SSL is a secure protocol that runs above TCP/IP and allows users to encrypt data and authenticate servers securely. It was first developed by Netscape in 1994 to provide server authentication, encryption of messages, and message integrity. SSL establishes an encrypted connection between a client and server through a handshake process that verifies servers, negotiates encryption, and generates symmetric keys to encrypt subsequent communication. It has become the standard security technology for web servers and browsers to protect online transactions and sensitive data transmission over the internet.






















![51
Reference
[1] http://www.faqs.org/faqs/computer-security/ssl-talk faq/
[2] http://www.pcwebopedia.com/TERM/S/SSL.htm
[3]http://developer.netscape.com/docs/manuals/security/sslin
/contents.htm
[4] http://www.ece.wpi.edu/~sunar/ee578/SSL.ppt
[5] http://nas.cl.uh.edu/yang/teaching/csci5931webSecurity/
ThesisProWS_Rajiv.doc](https://image.slidesharecdn.com/securesocketlayer-221103055902-37041c42/85/SecureSocketLayer-ppt-51-320.jpg)