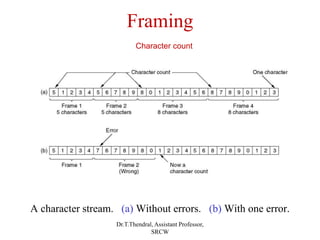
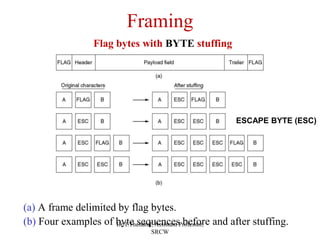
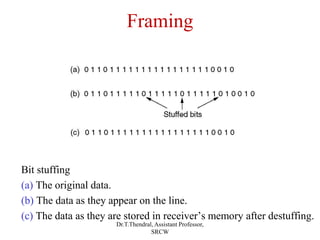
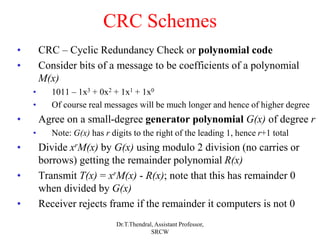
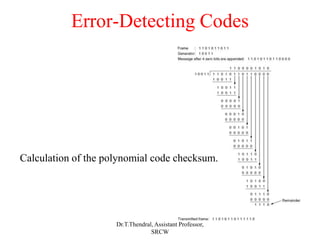
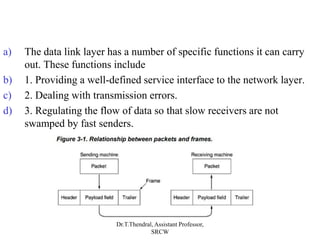
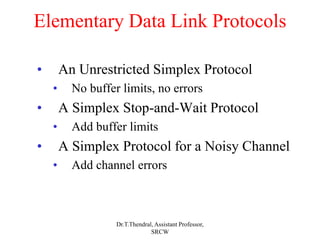
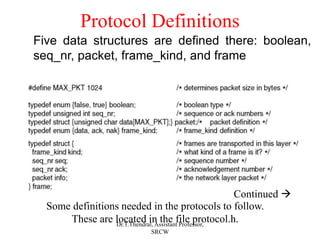
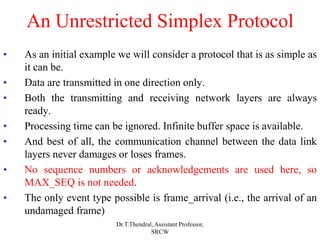
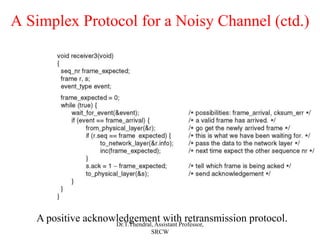
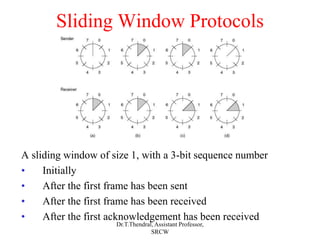
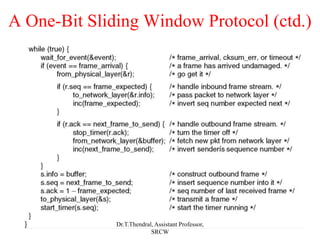
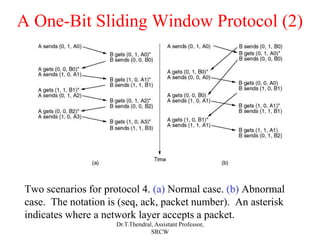
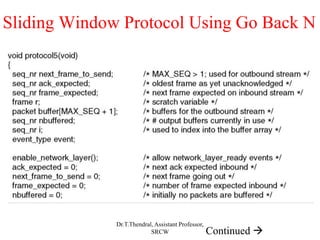
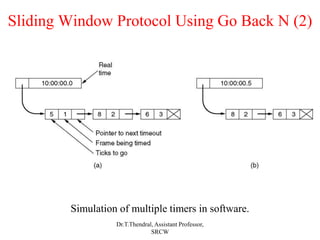
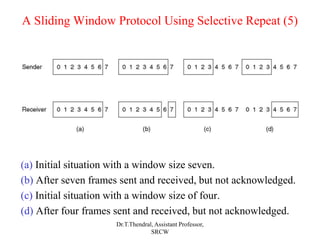
The document outlines the functions and design issues of the data link layer, including error detection and correction, framing techniques, and the various service models like acknowledged and unacknowledged services. It describes elementary data link protocols, including simplex stop-and-wait and sliding window protocols for efficient data transmission, particularly in noisy channels. Key concepts such as parity schemes, cyclic redundancy checks, and Hamming distance for error correction are also explained.