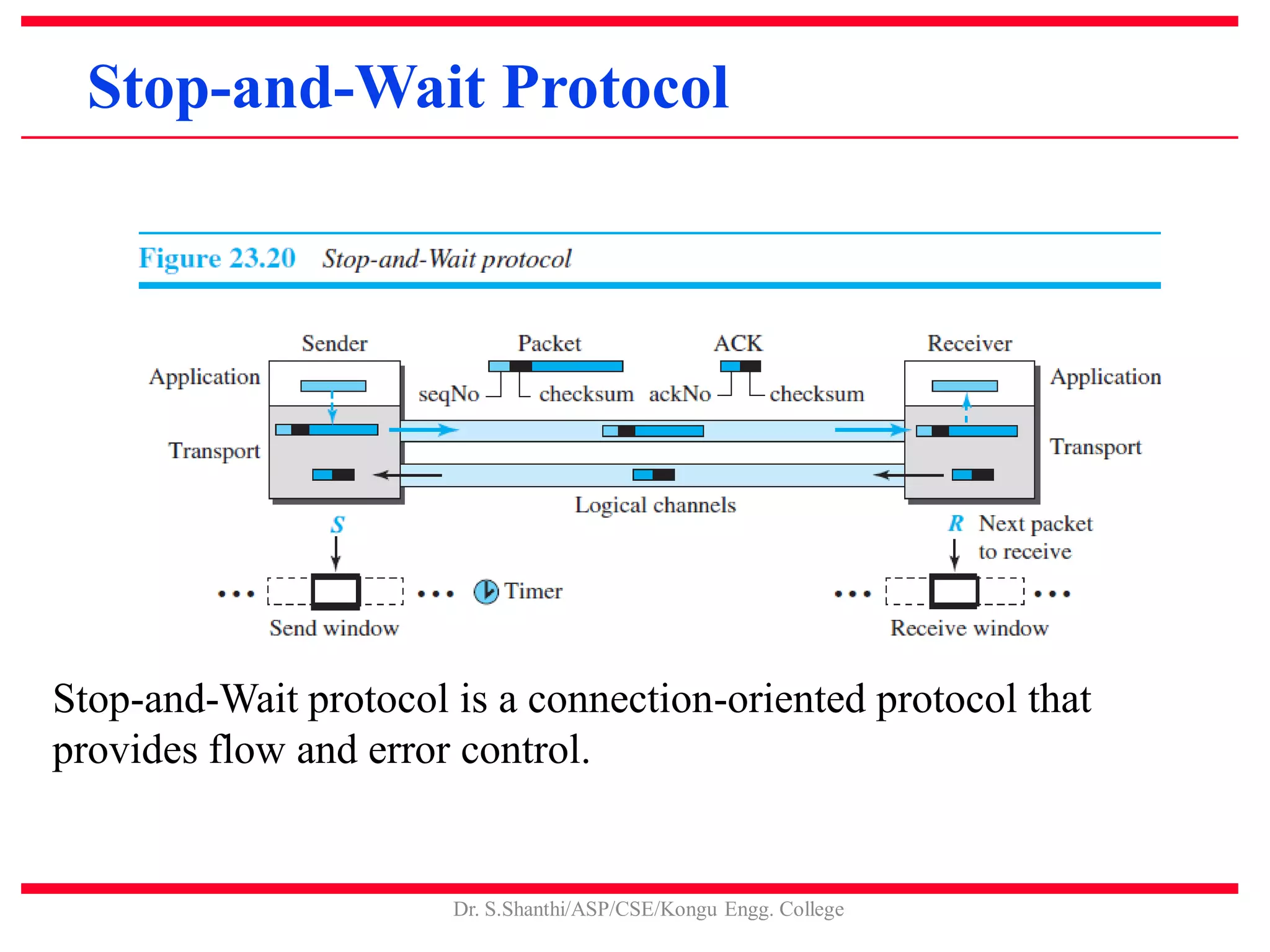
This document discusses the transport layer and TCP/IP protocols. It provides an overview of transport layer services including process-to-process communication, encapsulation and deencapsulation, multiplexing and demultiplexing, flow control, and error control. Connection-oriented and connectionless services are described. TCP and UDP are examined in detail, covering TCP segments, connections, congestion control, and reliable data transfer. Specific transport layer protocols like Go-back-N and Selective Repeat are summarized.