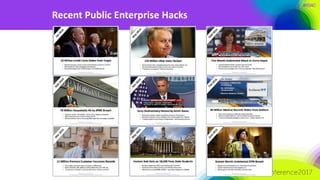
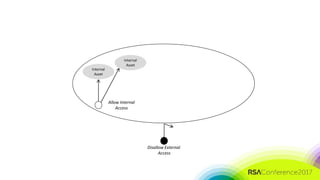
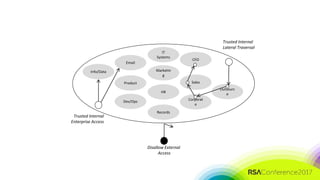
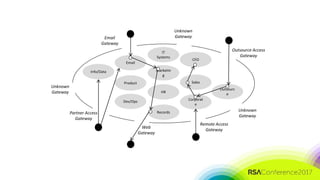
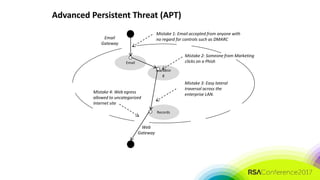
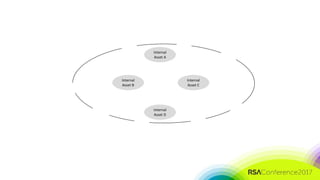
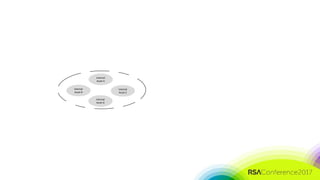
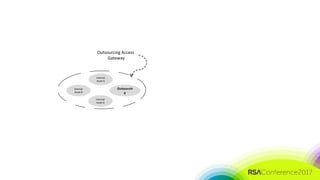
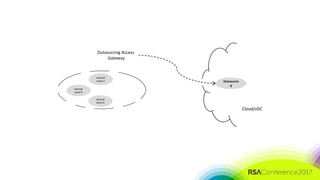
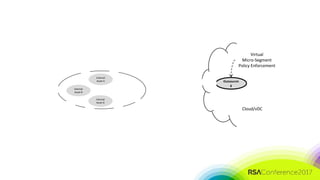
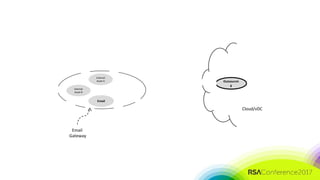
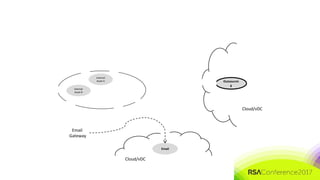
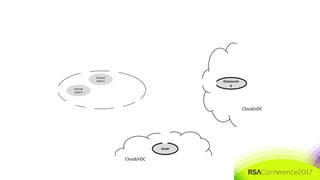
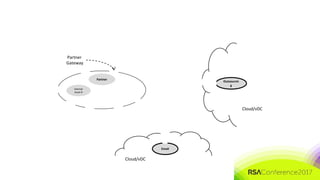
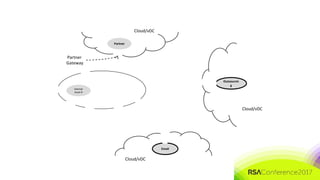
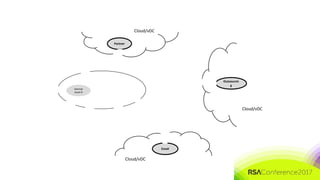
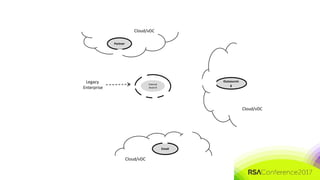
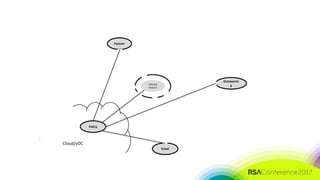
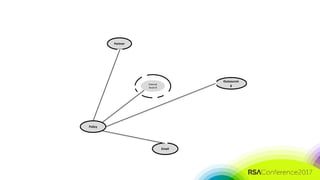
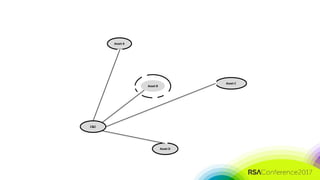
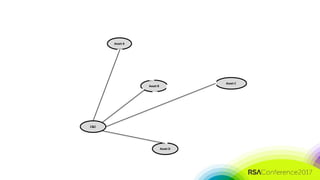
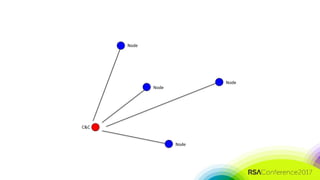
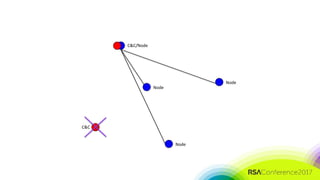
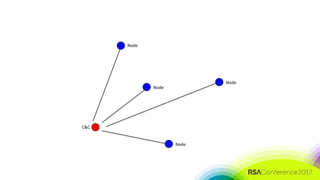
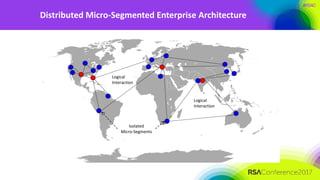
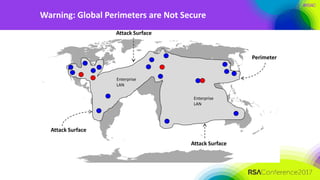
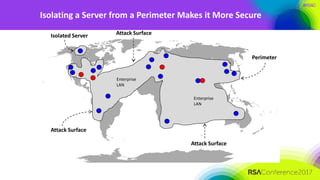
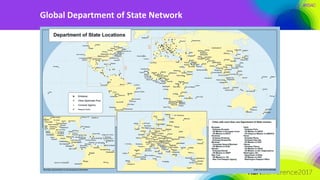
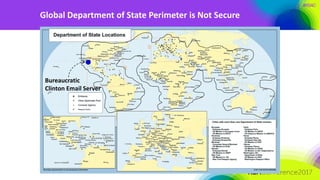
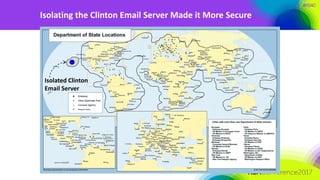
The document discusses the need for distributed and virtualized enterprise security. It covers recent public enterprise hacks and outlines the flaws with traditional enterprise perimeter security models. The presentation advocates for a micro-segmented architecture with isolated security zones and policy-based enforcement to replace the traditional untenable perimeter approach.