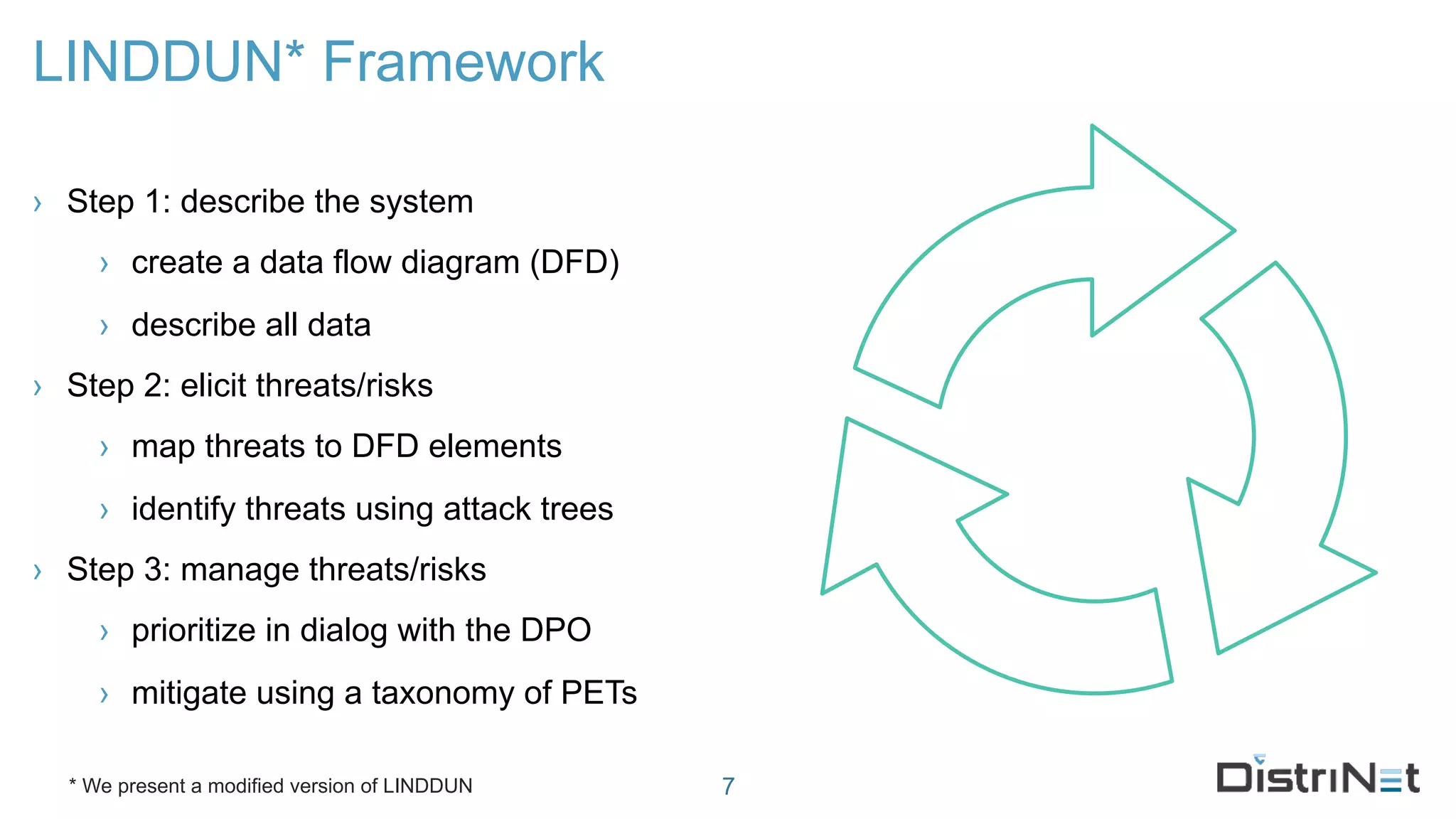
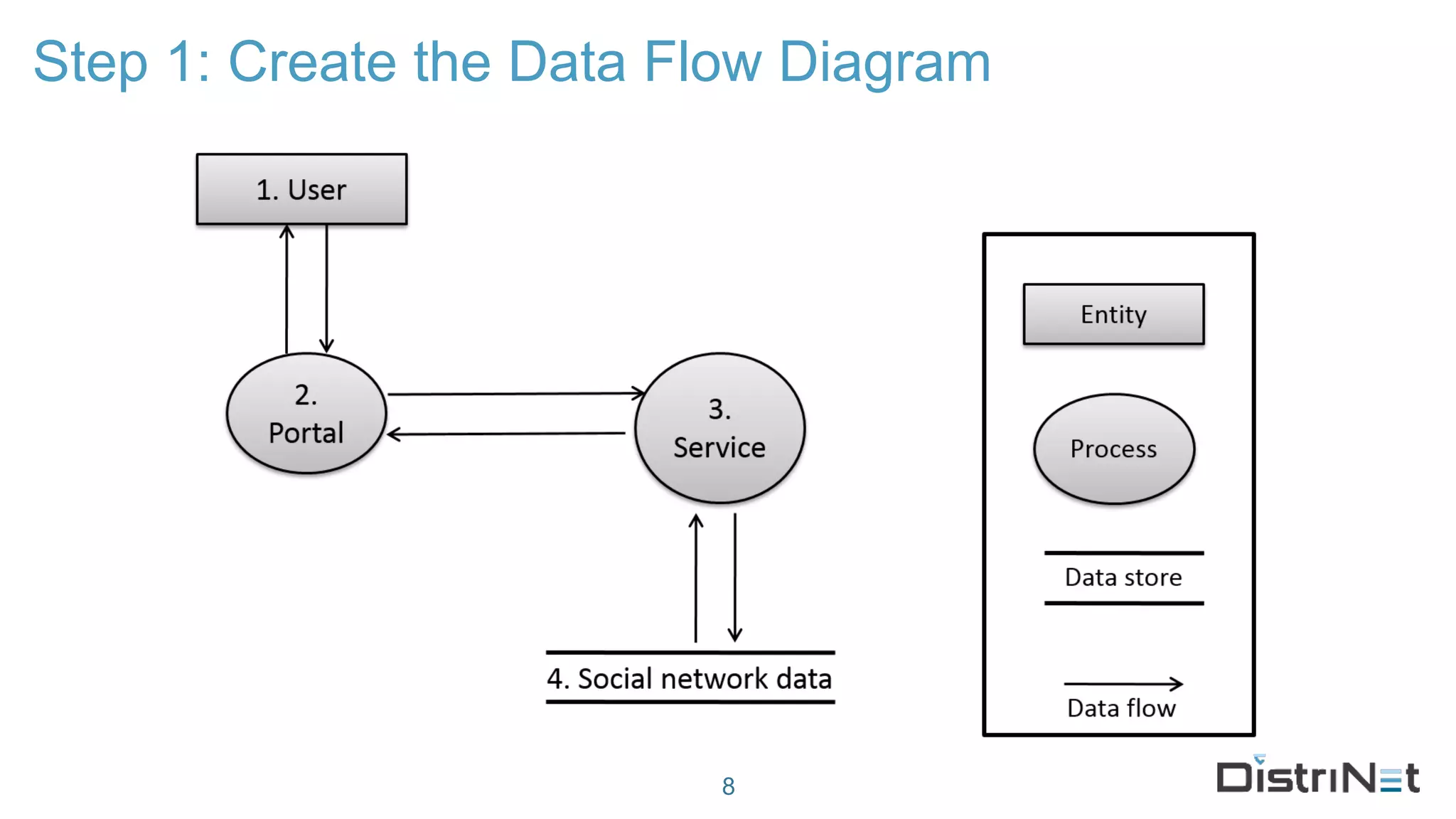
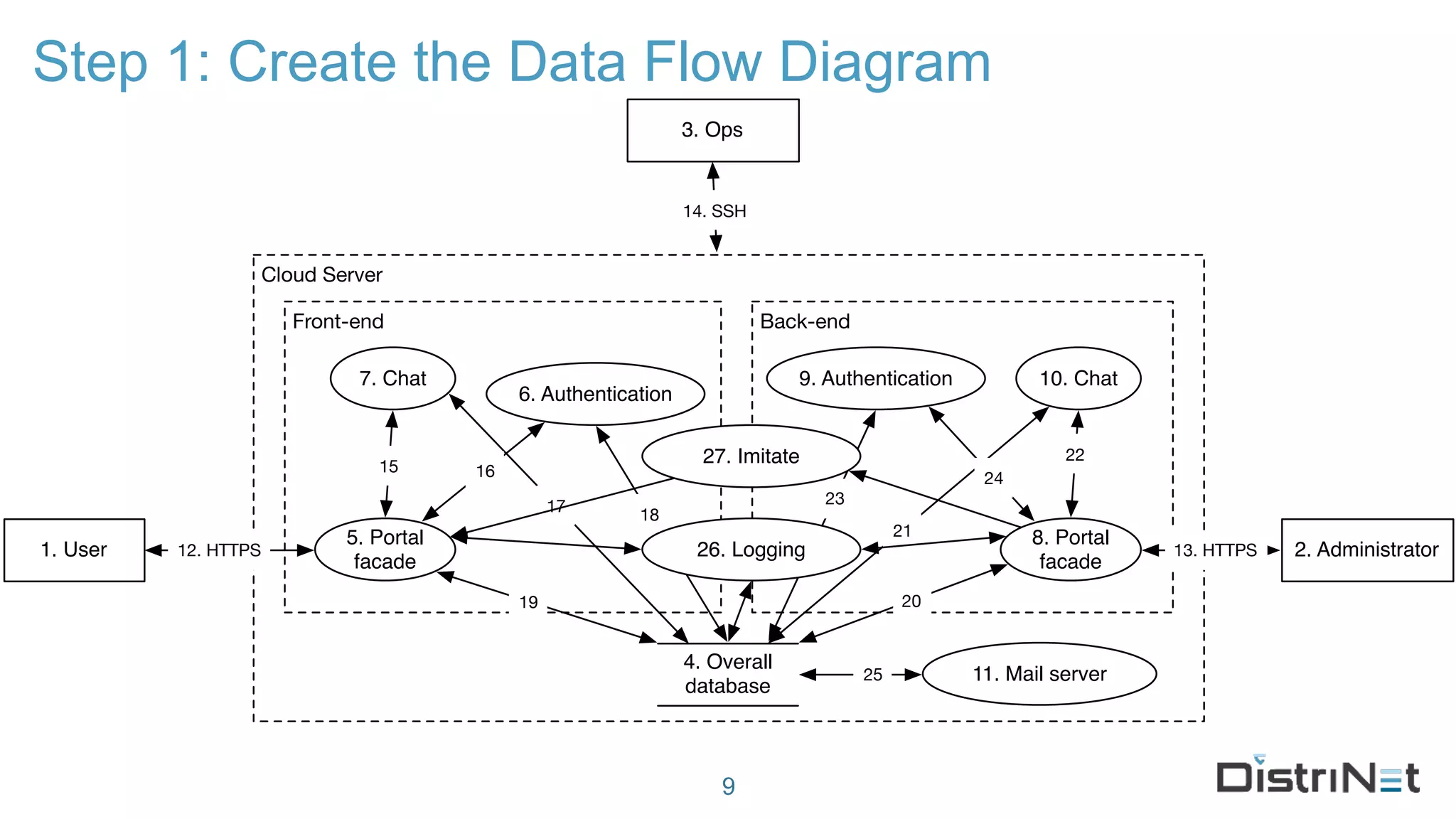
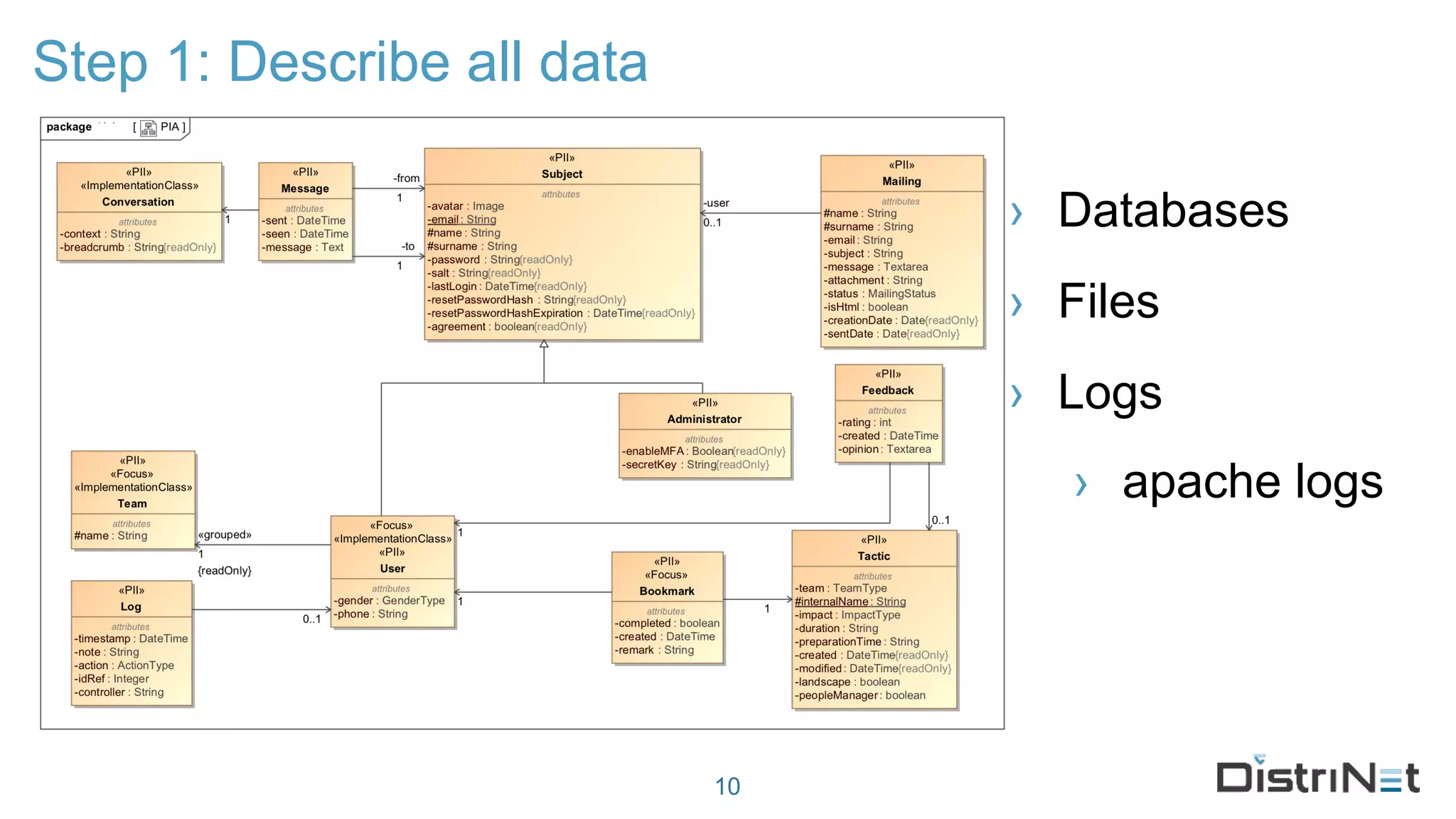
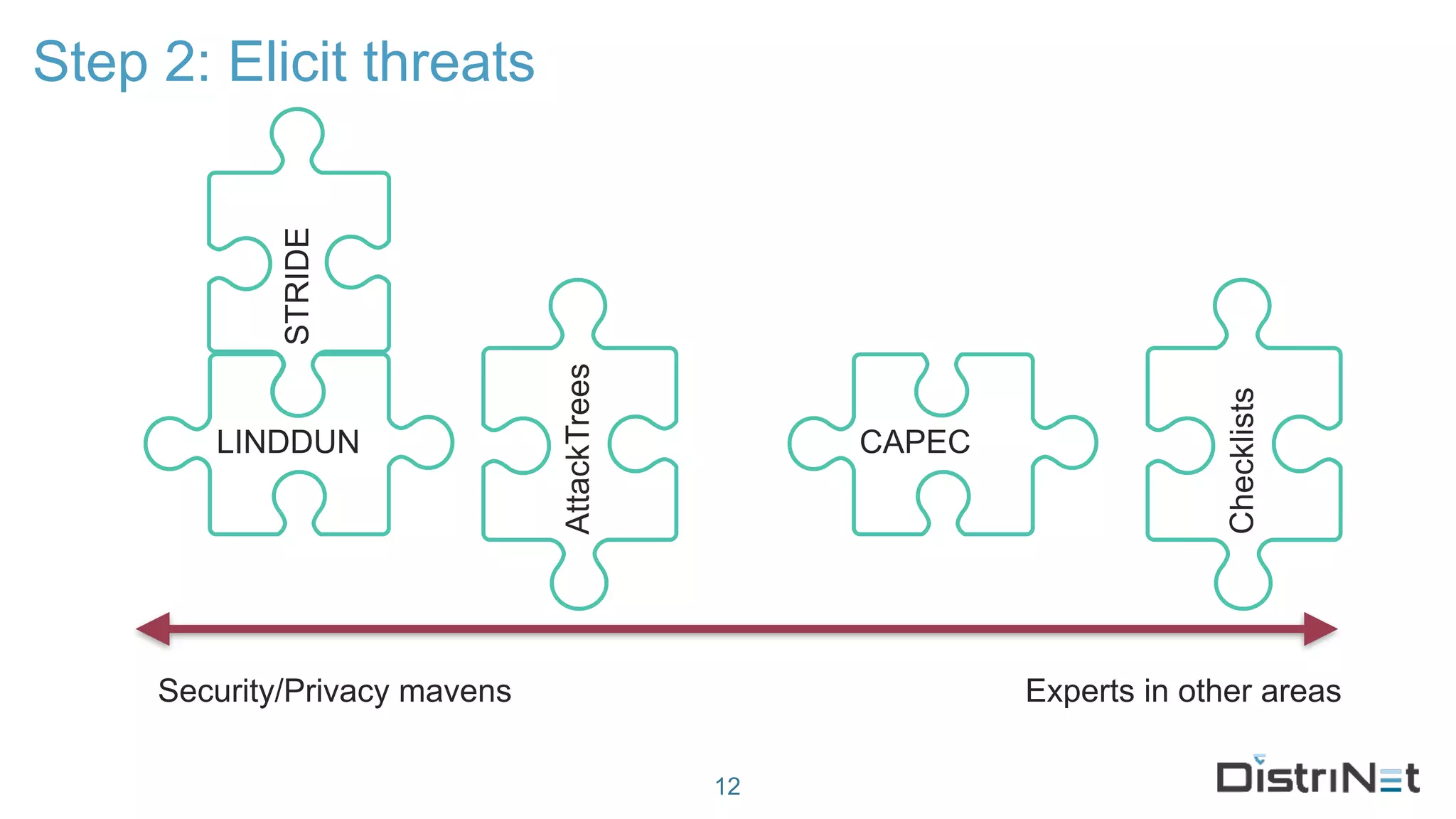
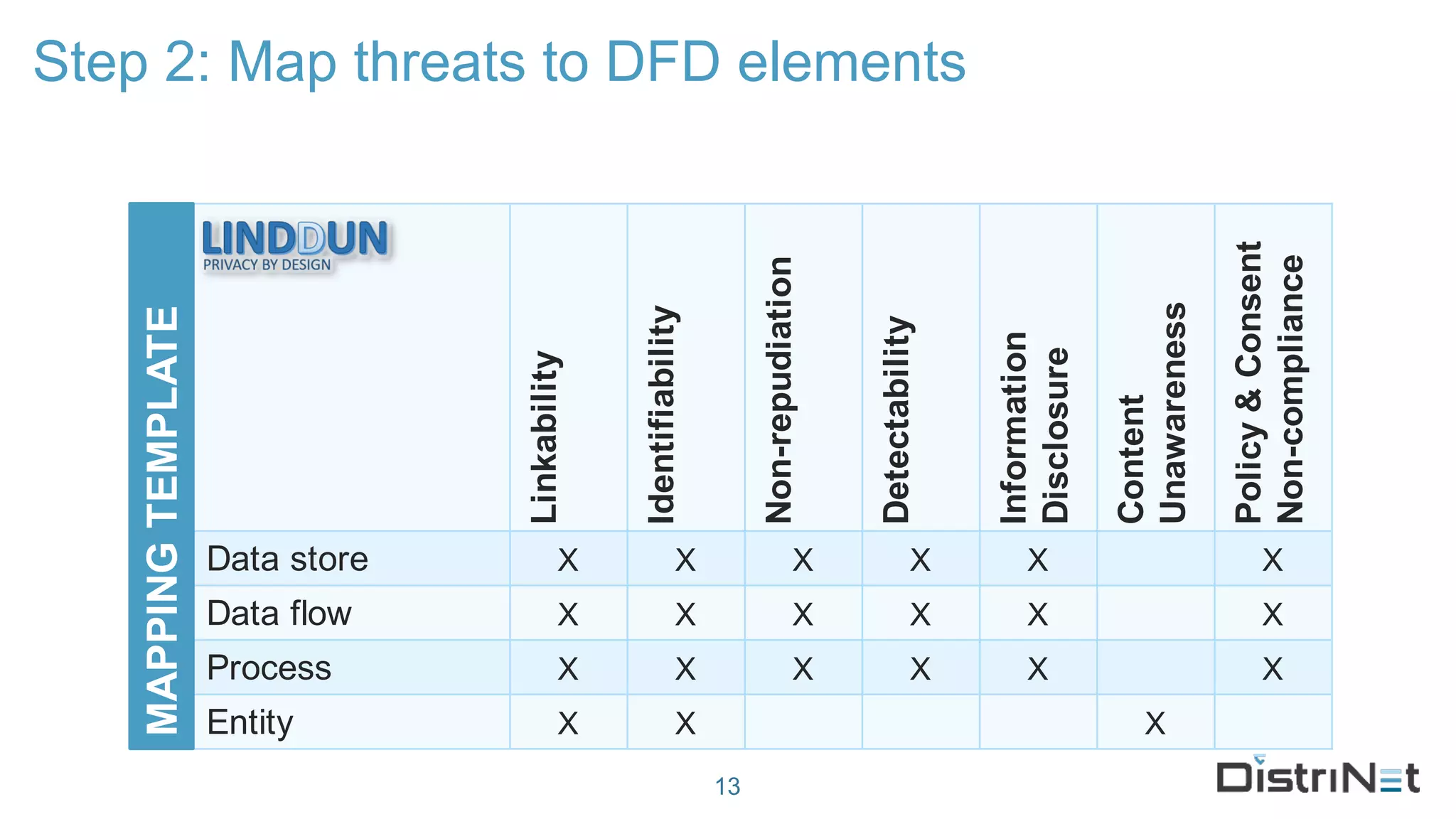
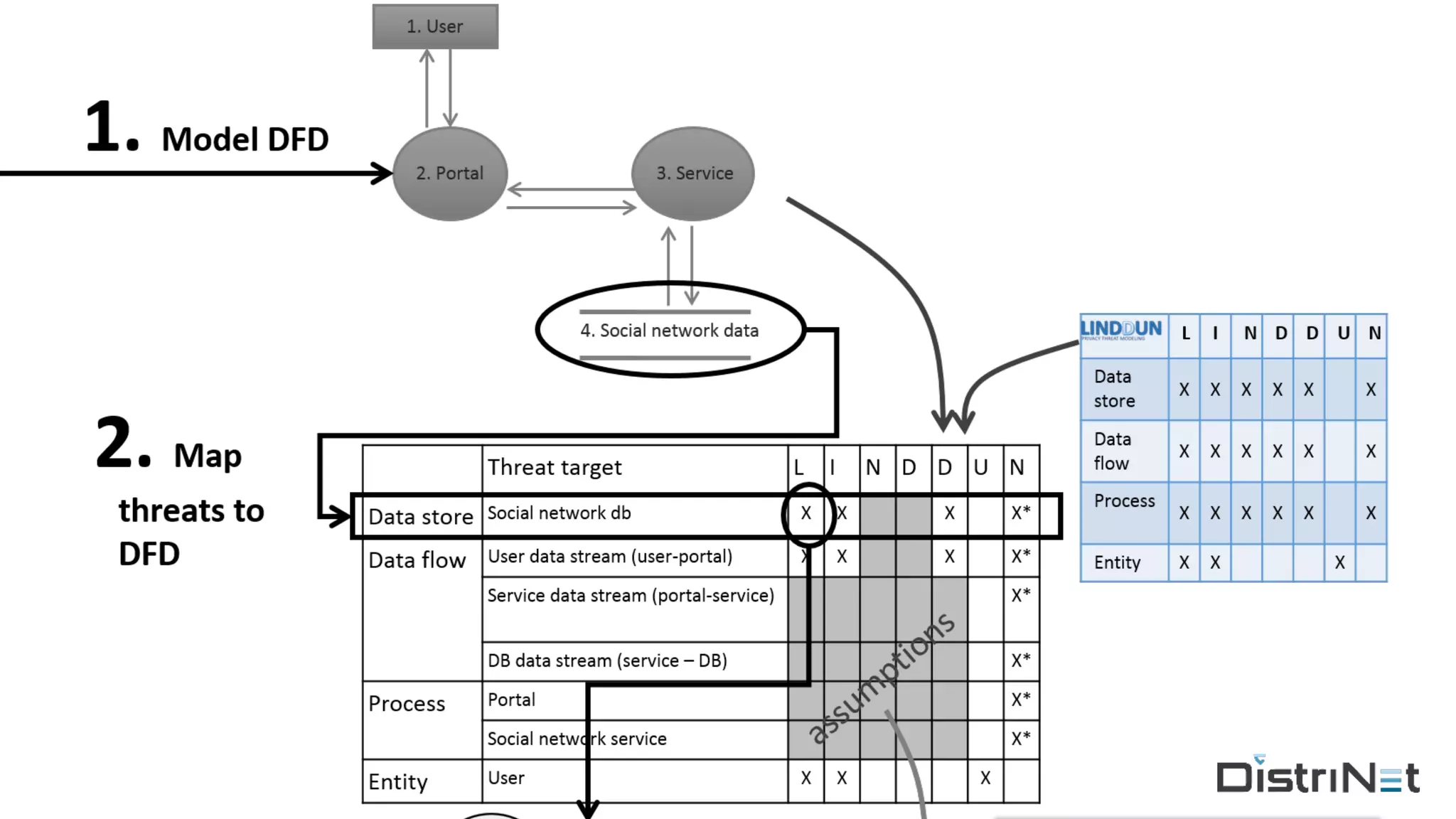
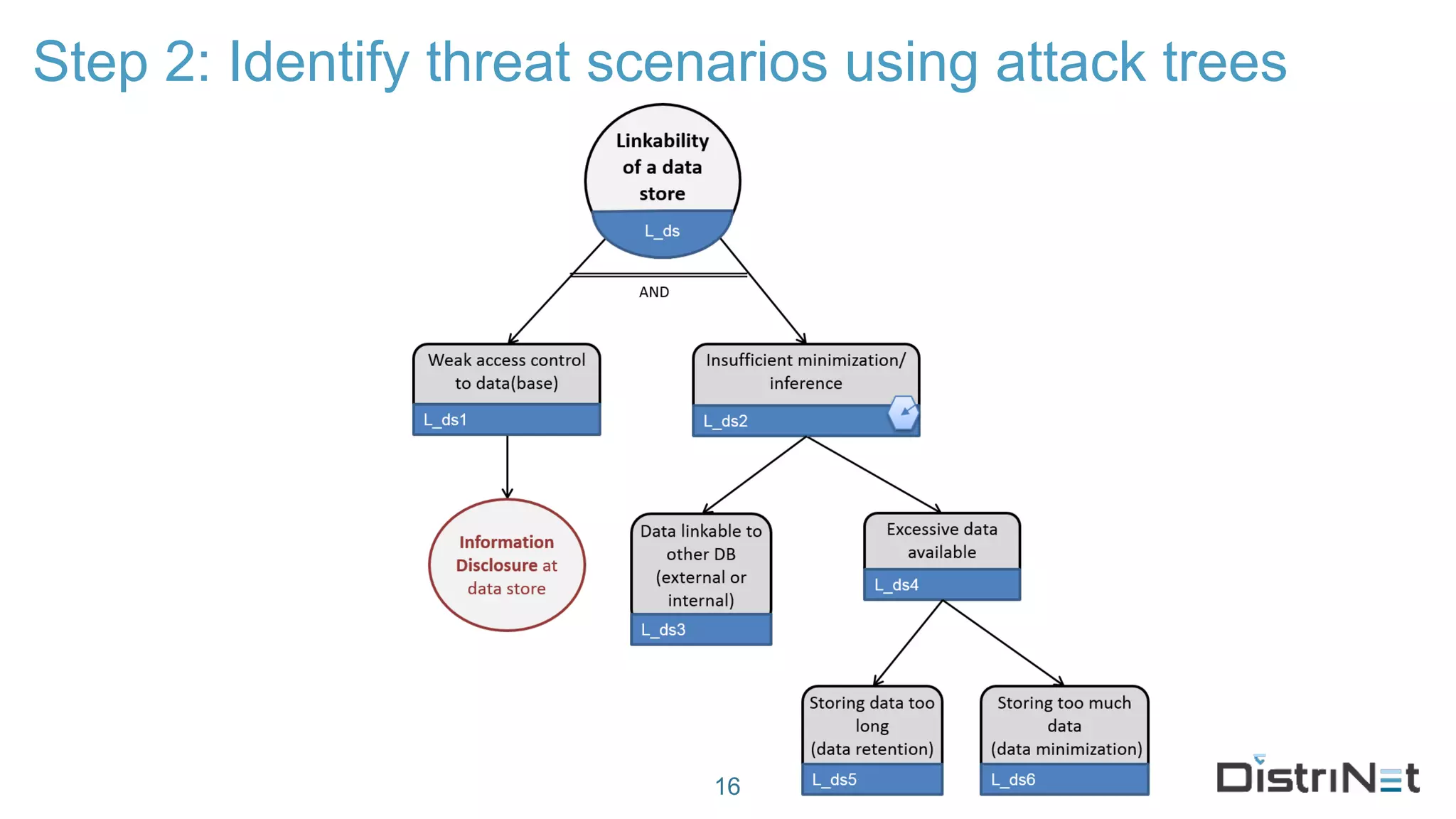
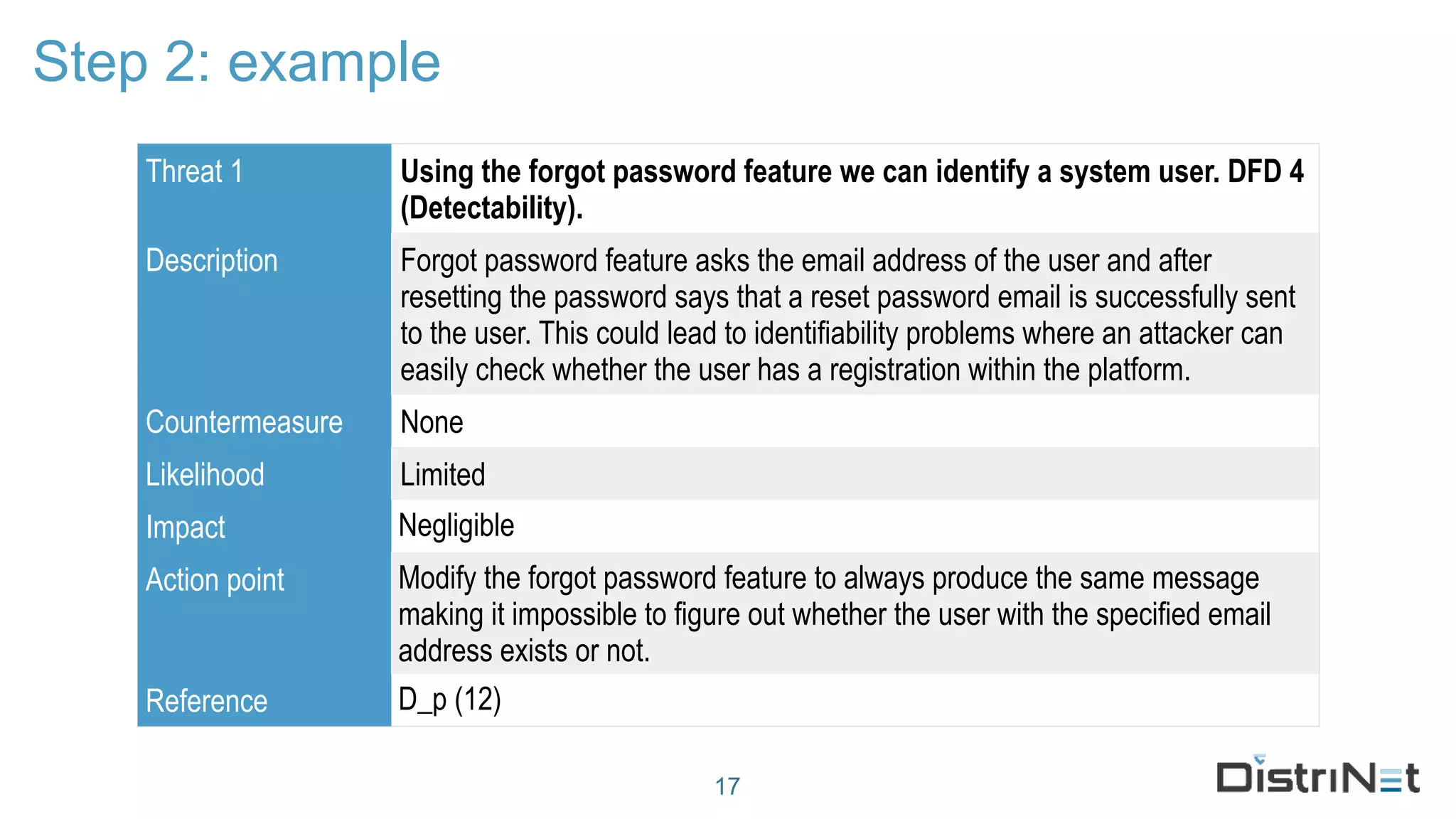
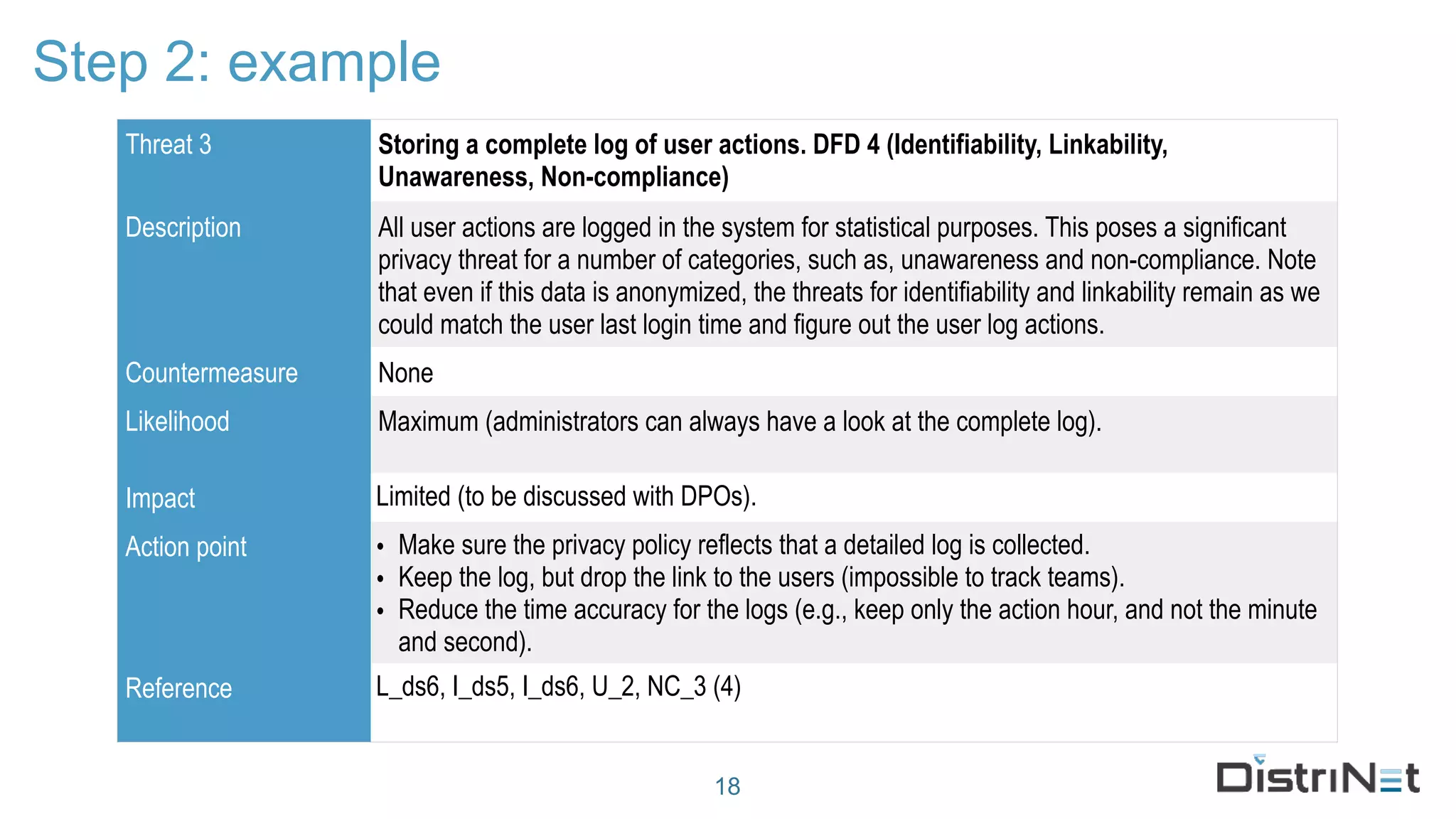
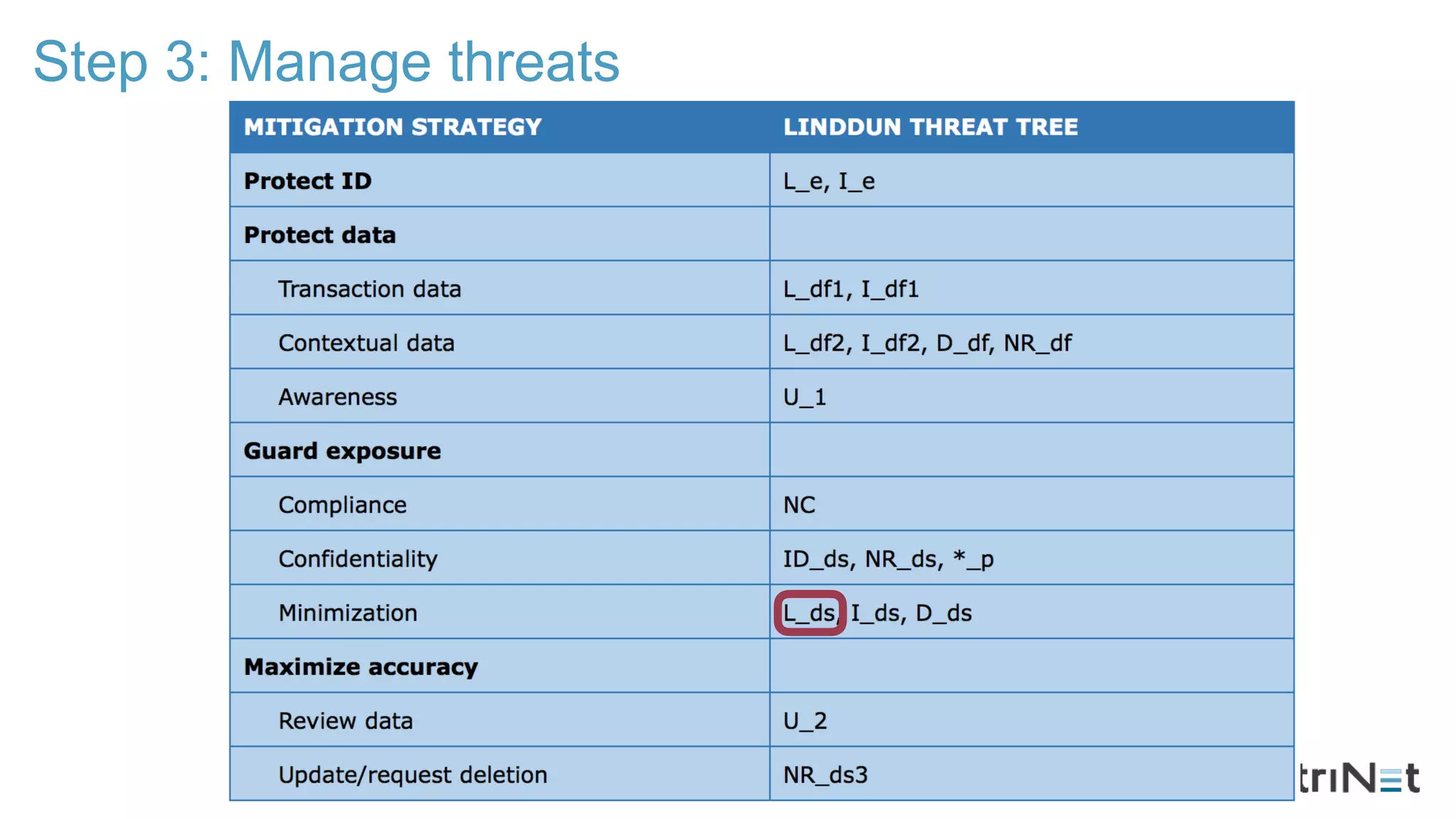
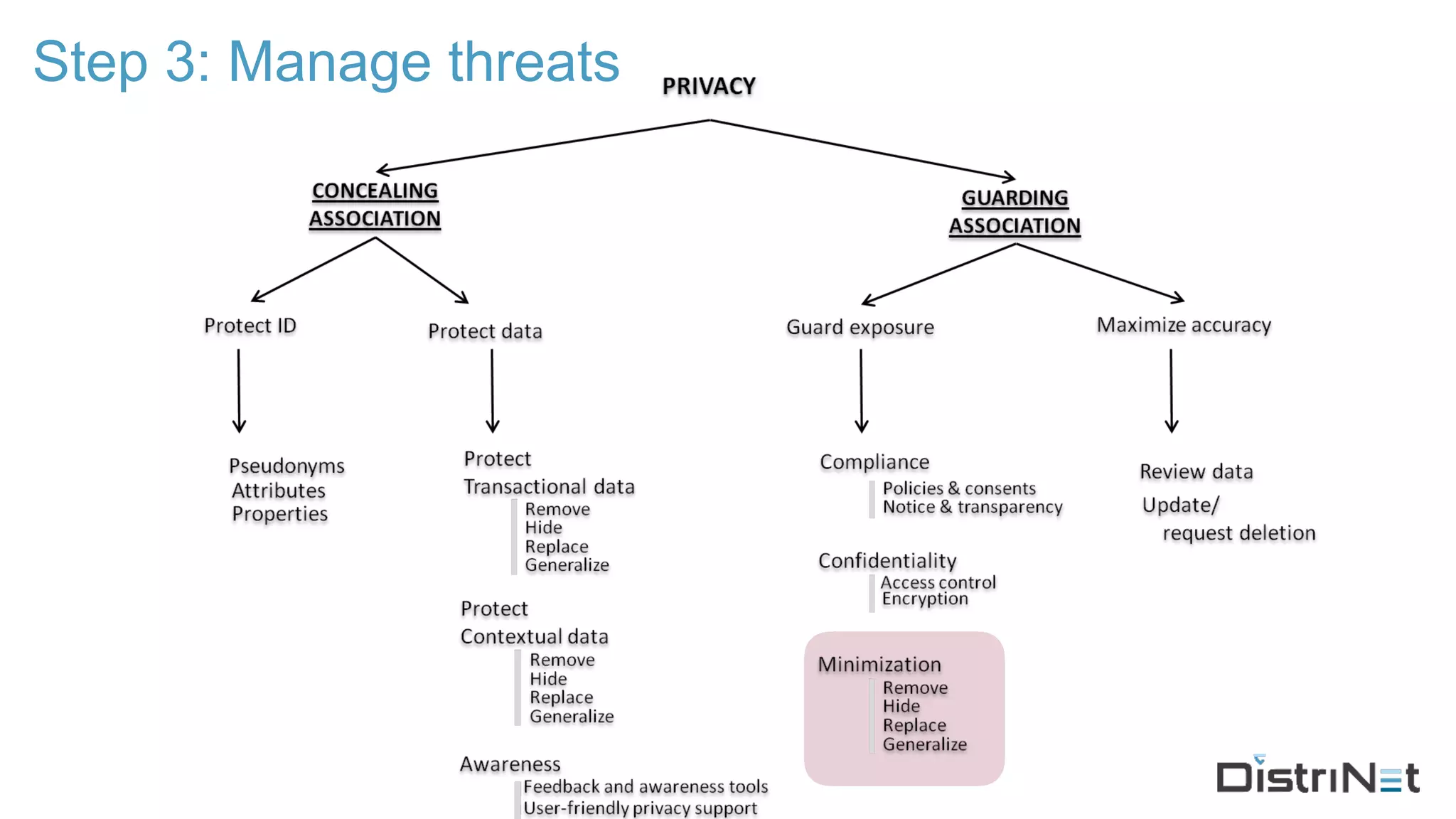
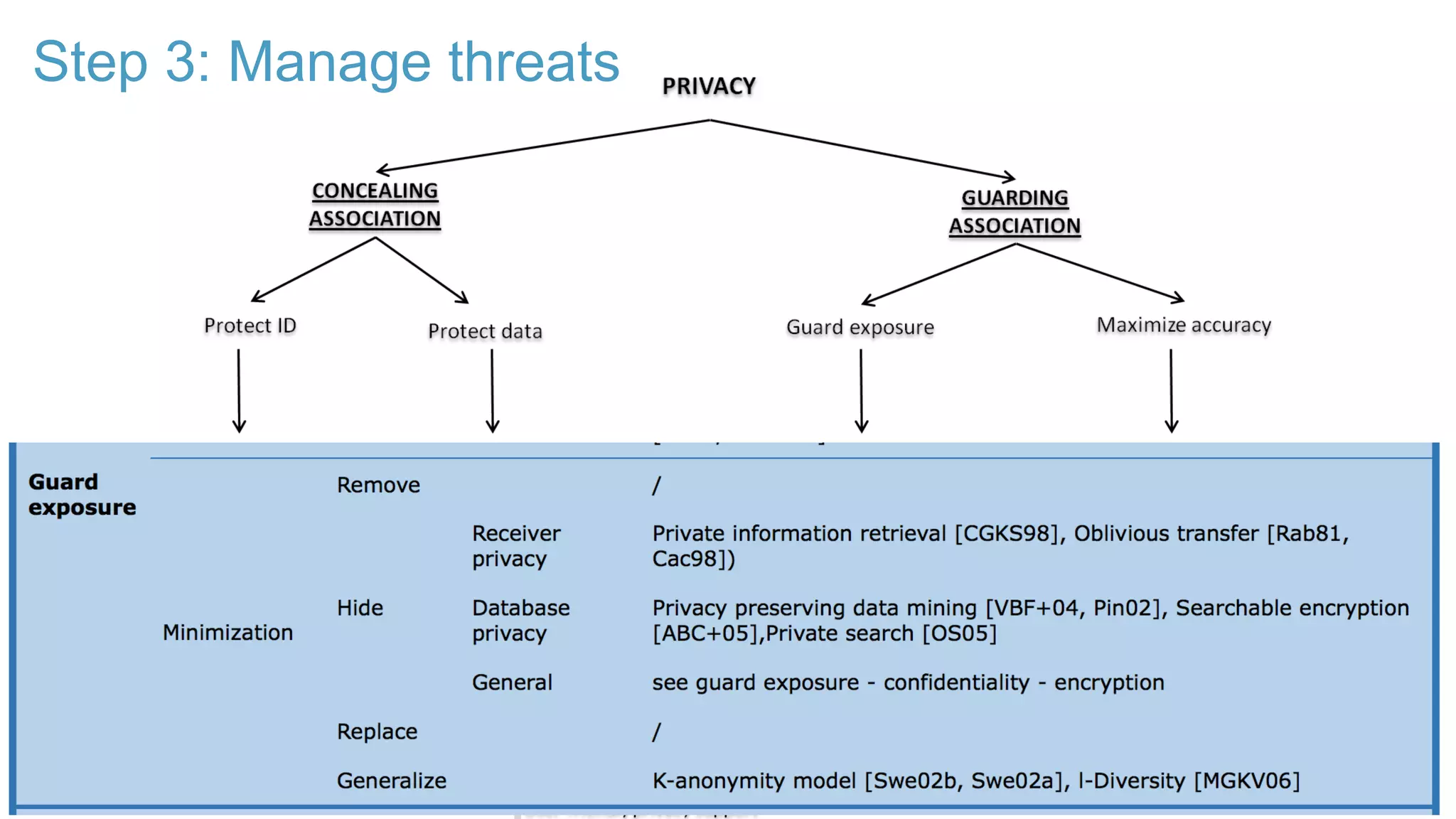
The document discusses the LINDDUN framework, a technical data protection impact assessment methodology designed to help organizations achieve GDPR compliance through systematic threat modeling and risk management. It outlines various steps, including system description, threat elicitation, and management, supported by empirical research and industry acceptance. The framework emphasizes the importance of appropriate technical measures to safeguard privacy rights, such as the right to access and the right to be forgotten.