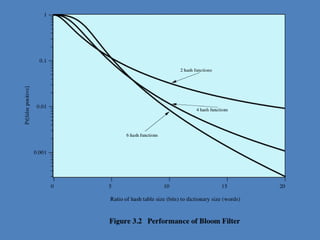
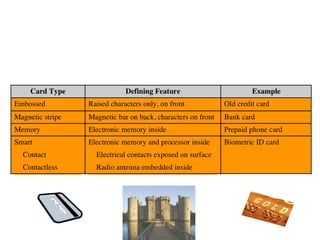
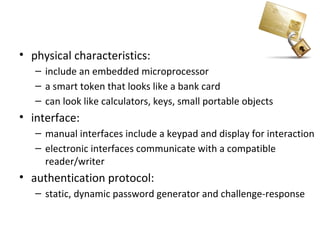
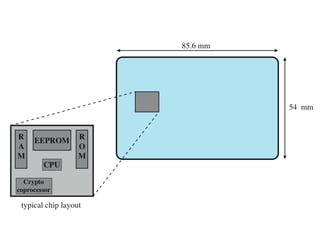
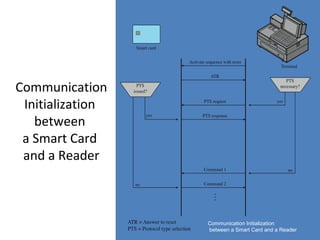
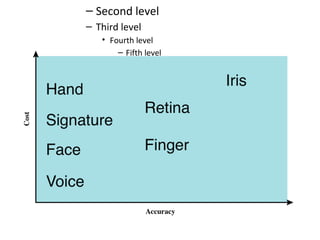
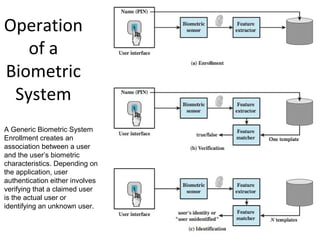
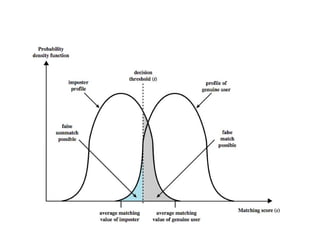
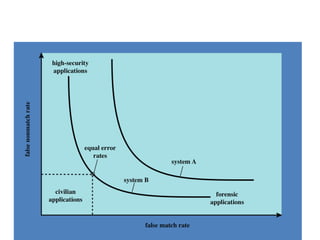
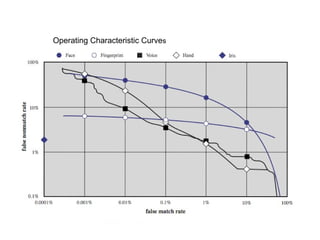
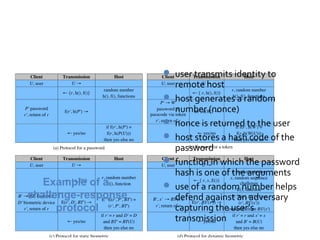
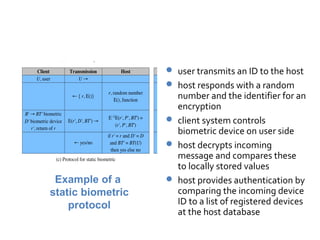
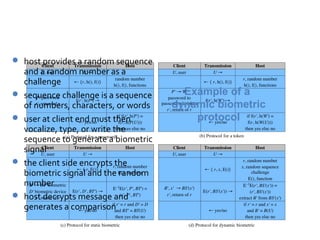
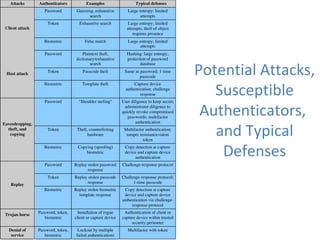
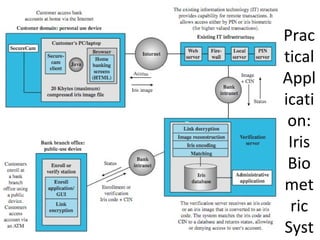
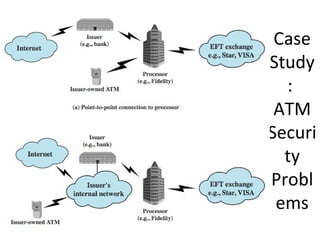
The document discusses various methods for user authentication, including passwords, tokens, and biometrics. It describes strategies for improving password security, such as password selection techniques, password files, and shadow passwords. It also covers token-based authentication using memory cards and smart cards. Biometric authentication using physical characteristics like fingerprints is explored. Finally, it summarizes challenges with remote user authentication and provides examples of password, token, and biometric protocols.