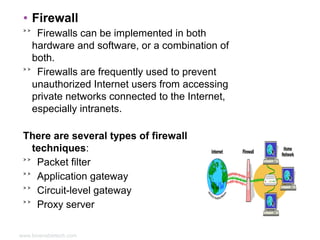
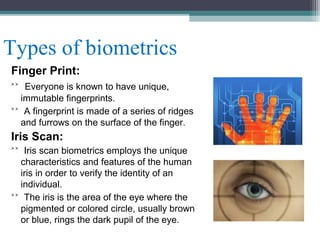
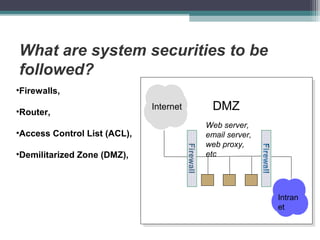
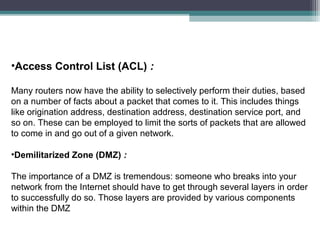
The document discusses various aspects of network security including definitions, threats, prevention techniques, and tools. It describes common network security threats like viruses, trojan horses, and attacks. It also explains prevention techniques such as cryptography, firewalls, digital signatures, and biometrics. Biometrics authentication methods like fingerprints, iris scans, face and voice recognition are outlined. The roles of network security devices, virtual private networks, and the Network Security Toolkit are also summarized.