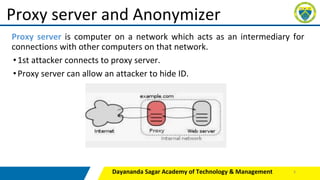
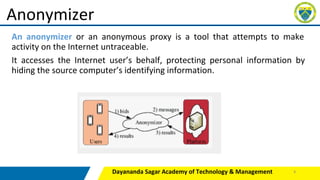
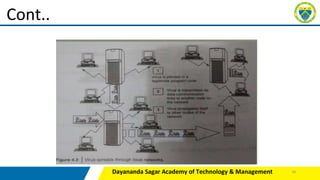
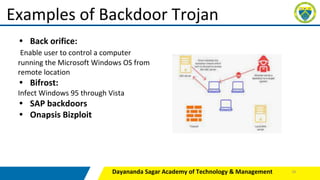
This document provides an overview of various tools and methods used in cybercrime, including proxy servers and anonymizers, phishing, password cracking, keyloggers and spywares, viruses and worms, Trojan horses and backdoors, steganography, denial of service (DoS) and distributed denial of service (DDoS) attacks, and attacks on wireless networks. It describes how these tools work and how attackers use them to compromise networks and systems. The document is intended as part of a course on cybercrime for students.