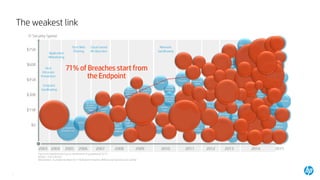
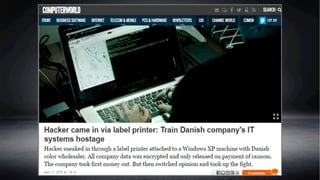
1) Printers are vulnerable endpoints that can be used as an initial entry point for attacks due to weaknesses like default passwords and lack of security configurations. Hackers have successfully used printers to access corporate networks.
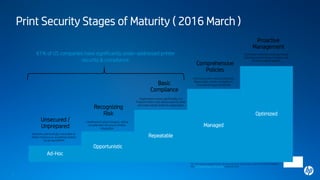
2) Most companies have underaddressed printer security, with 61% at an "ad-hoc" or "opportunistic" stage of security maturity. Proper security requires a comprehensive, layered approach across devices, data, documents, and network access.
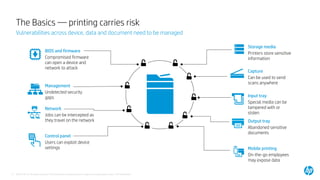
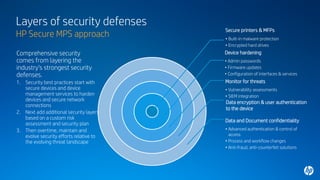
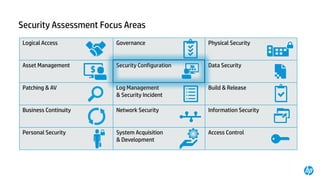
3) A secure managed print service applies layers of defense including secure devices, device hardening, data encryption, monitoring for threats, and controls over data access. Regular security assessments and password management are also recommended actions.