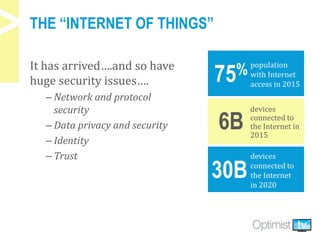
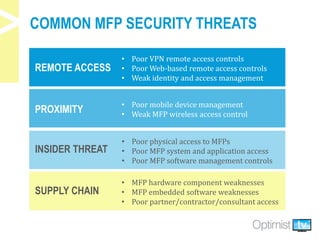
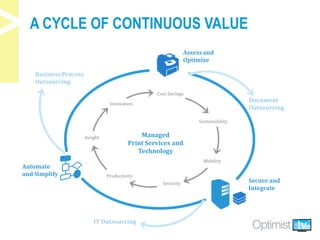
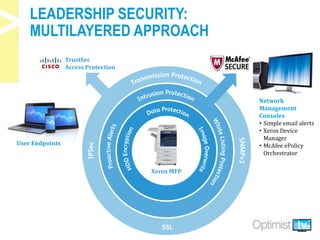
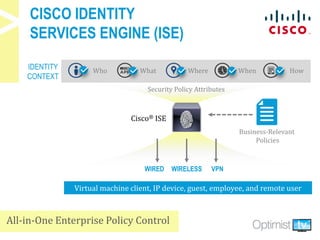
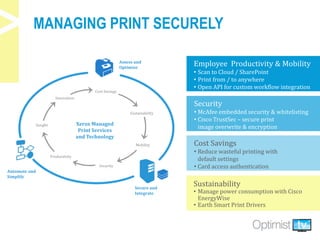
The document discusses security challenges associated with the rise of the Internet of Things, particularly in relation to multi-function printers (MFPs). It provides insights from key experts and highlights common security threats, the need for secure print strategies, and questions organizations should ask regarding their document management and printing processes. Additionally, it emphasizes the importance of integrating security measures and leveraging managed print services to enhance overall document and network security.