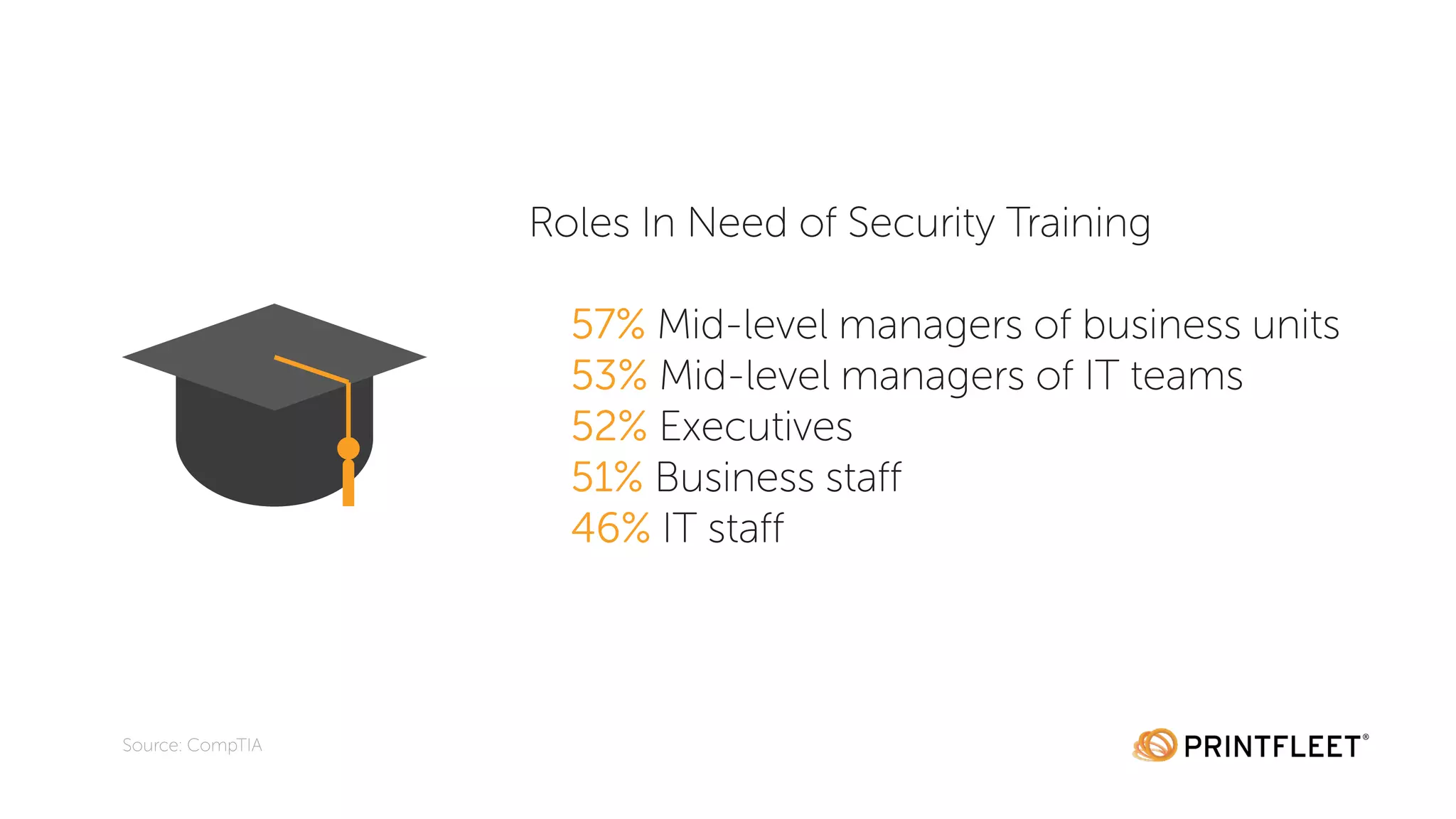
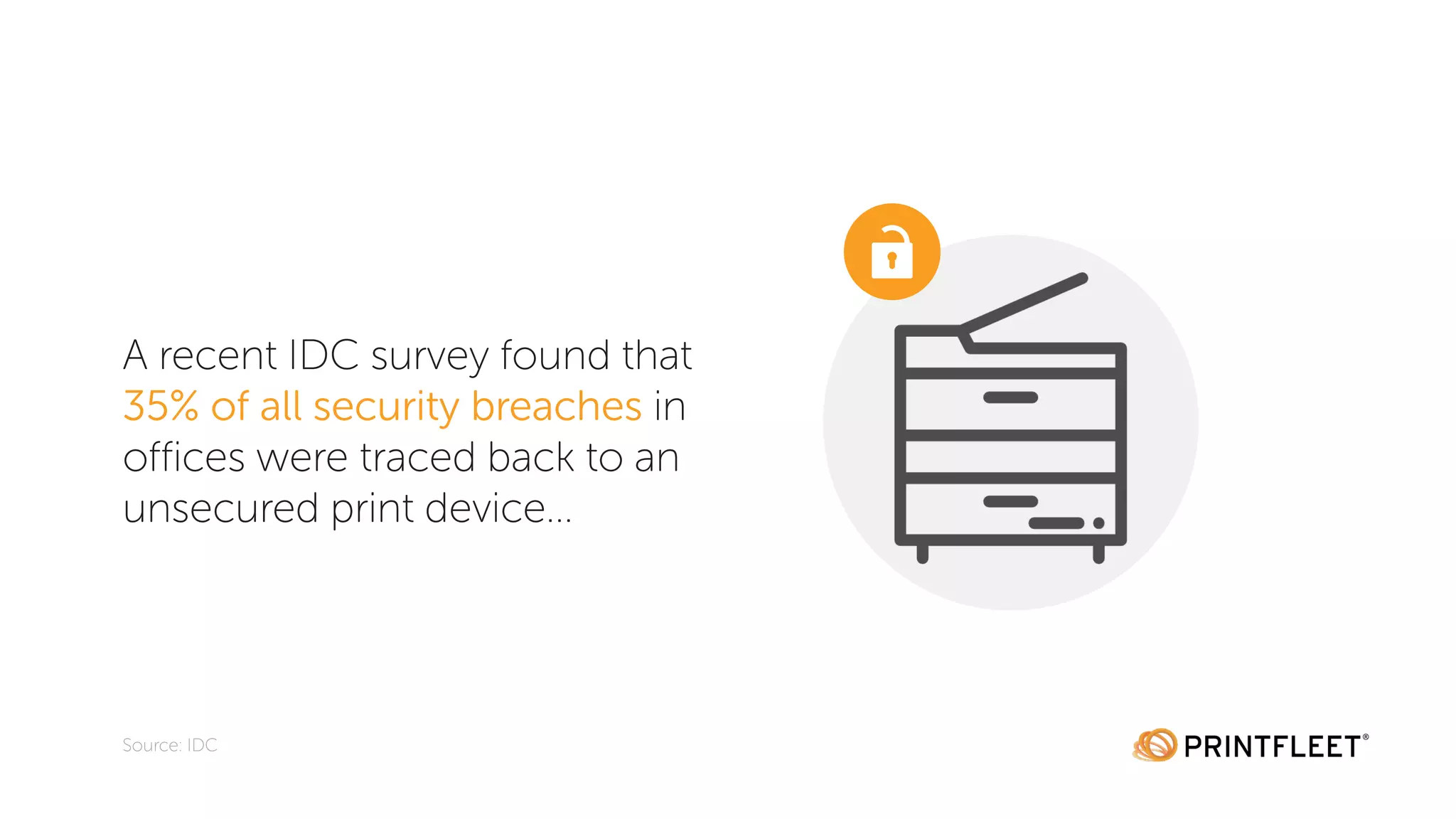
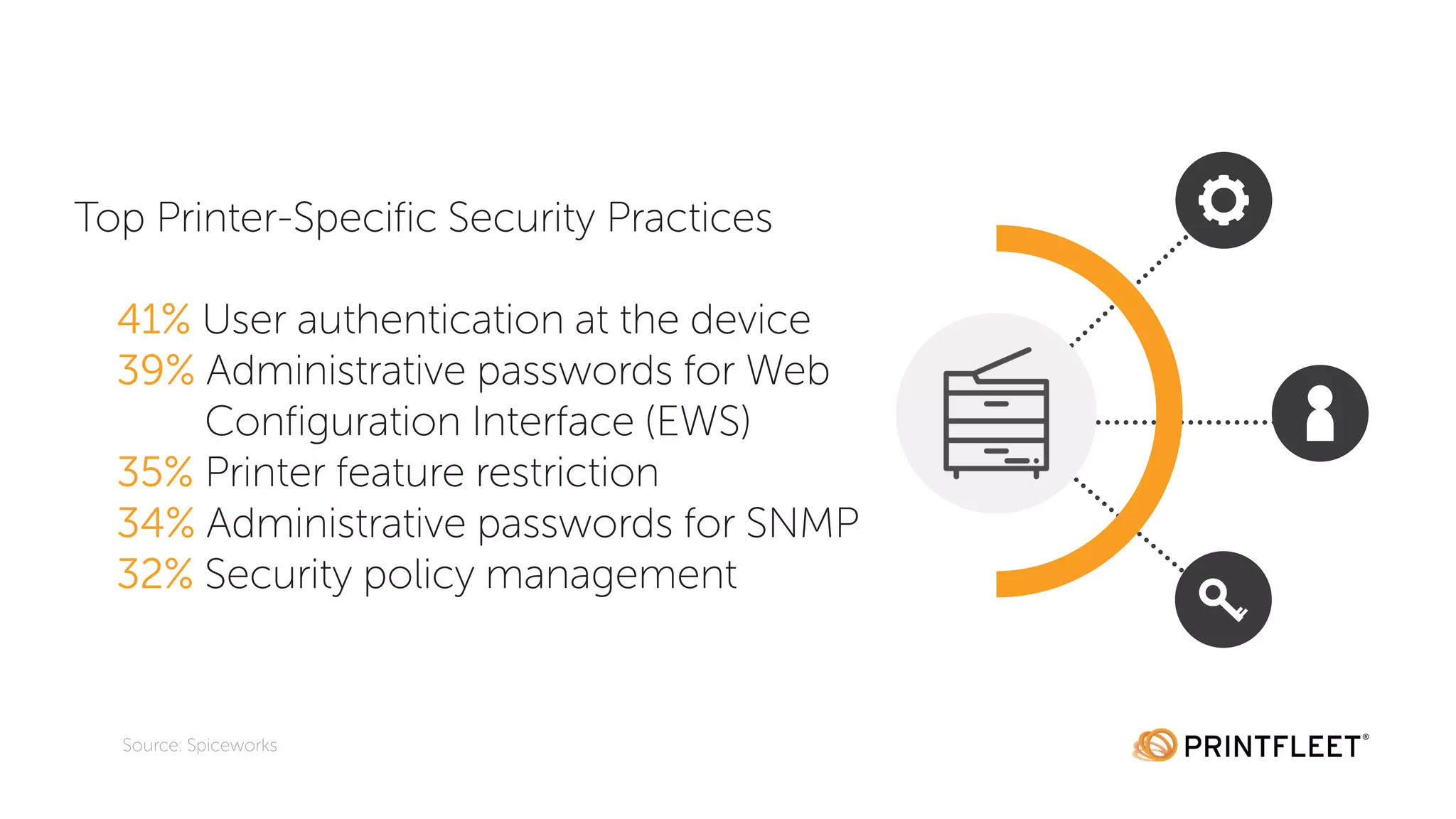
The document discusses the importance of data security in the information age, highlighting the increasing reliance on digital information and the prevalence of cybercrime, with 32% of companies reporting victimization in 2016. It emphasizes the need for security training, particularly in password practices and risk management, and notes that human error is the leading cause of data breaches. Additionally, it addresses the overlooked security risks of office printers and offers best practices for securing these devices.