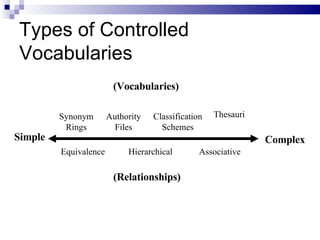
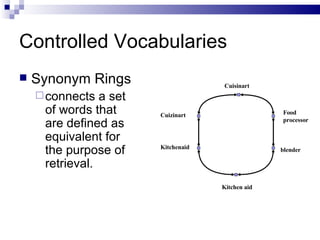
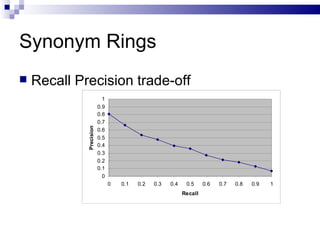
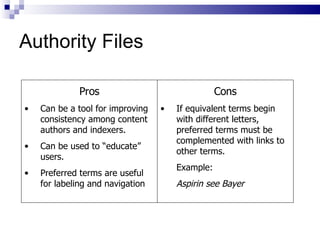
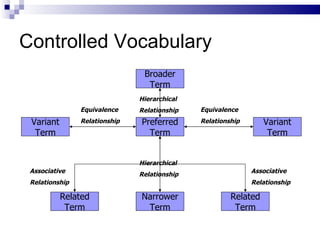
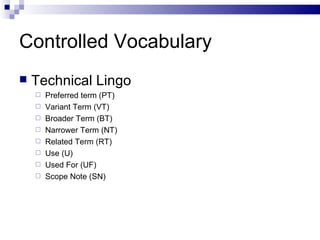
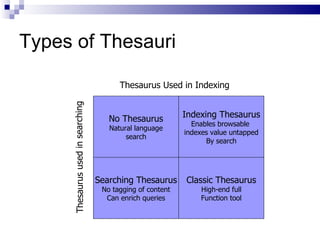
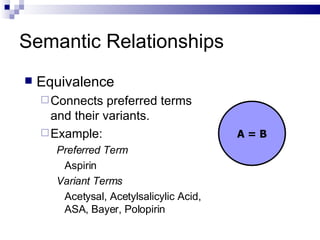
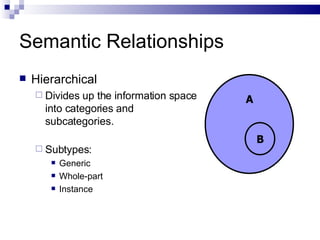
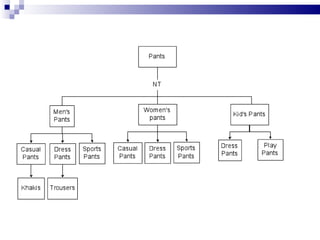
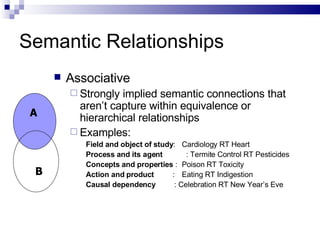
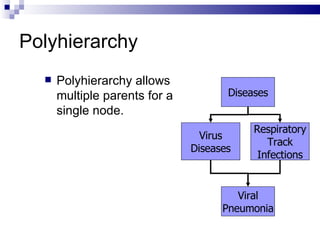
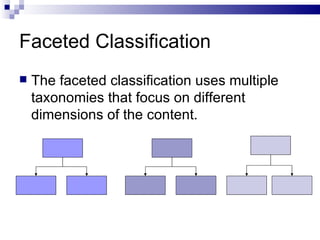
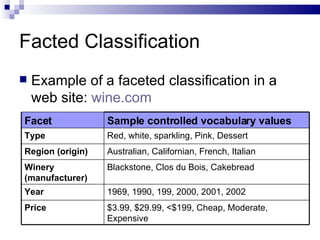
The document discusses various types of controlled vocabularies and metadata that can be used to organize information, including synonym rings, authority files, classification schemes, thesauri, and faceted classification. Controlled vocabularies and metadata help improve search, navigation, and information retrieval by establishing relationships between terms and standardizing language. Faceted classification in particular allows information to be organized from multiple perspectives using different facets or attributes.