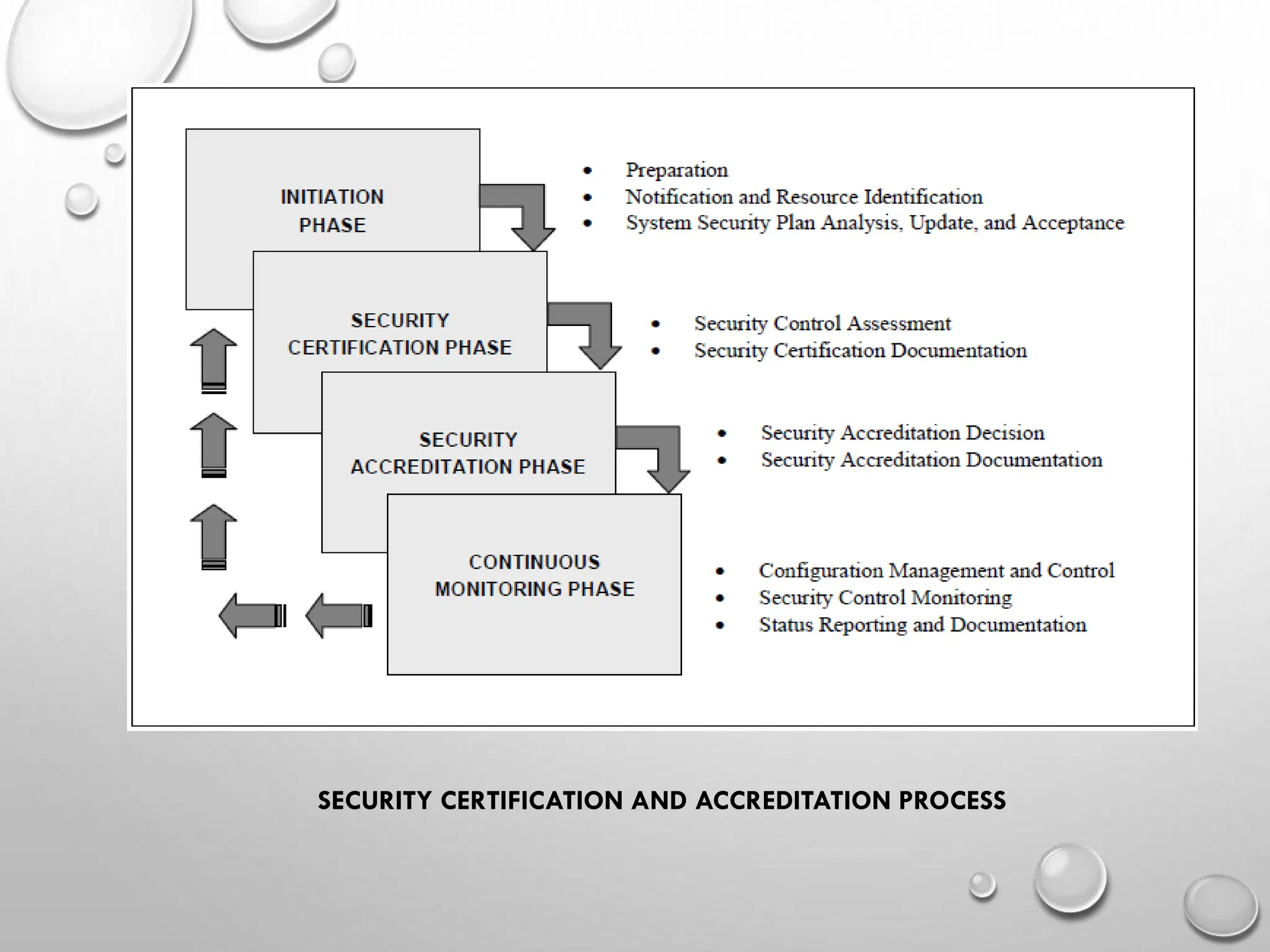
The security certification and accreditation process consists of four phases: initiation, security certification, security accreditation, and continuous monitoring, each with specific tasks and responsible individuals. The purpose of these phases is to ensure alignment with security requirements, assess security controls, determine acceptable risk levels, and maintain ongoing oversight of the information system's security. Each phase involves preparation, documentation, assessment, and reporting to ensure the effectiveness of security measures.