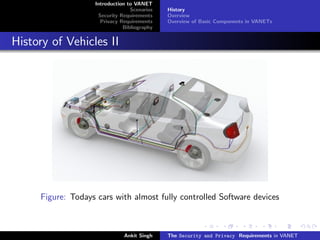
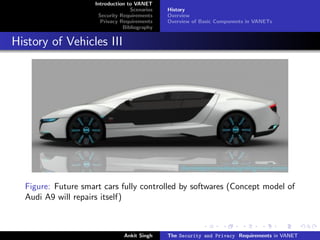
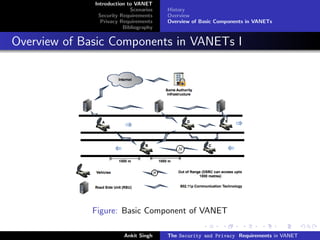
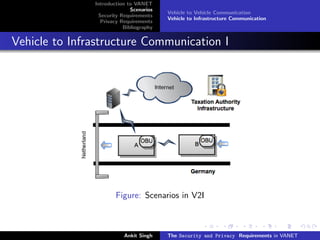
The document discusses security and privacy requirements in vehicular ad hoc networks (VANETs). It begins with an introduction to VANETs, including their history and basic components. It then covers two common VANET communication scenarios: vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I). Some potential threats are outlined for each scenario. The document also discusses security requirements like authentication, accountability, and credential revocation. Privacy requirements for VANETs include anonymity, unlinkability, and restricted credential usage. It concludes with a short bibliography section.