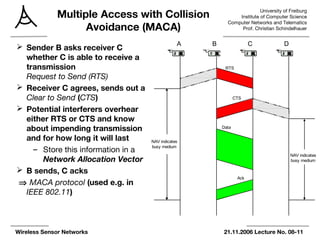
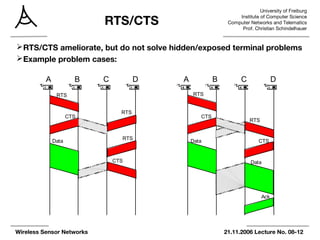
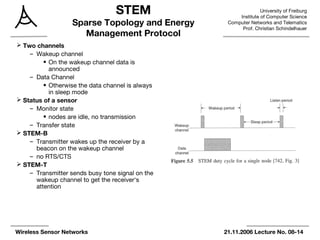
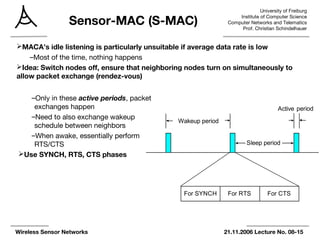
The document summarizes key points from an 8th lecture on wireless sensor networks. It discusses various medium access control (MAC) protocols that control when nodes can access a shared wireless medium. These include contention-based protocols like MACA that use RTS/CTS handshaking and schedule-based protocols with fixed or dynamic scheduling. It also describes energy-efficient MAC protocols for low data rate sensor networks like S-MAC, T-MAC, and preamble sampling that increase sleep time to reduce energy use through synchronized sleep schedules or long preambles.