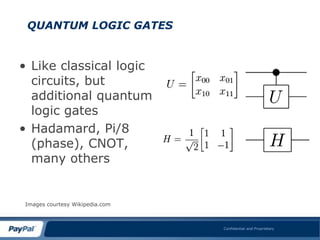
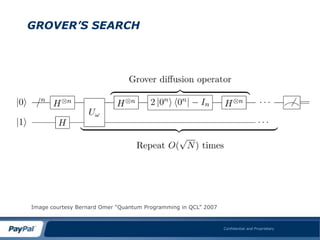
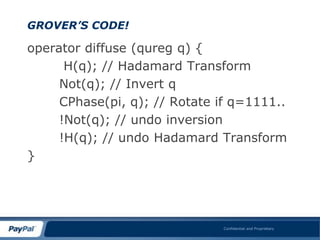
The document discusses Grover's search algorithm, a quantum computing method that offers the fastest possible search capabilities with a complexity of O(n^1/2). It highlights advancements in quantum computing, including the ability to read 16 qubits, achievements in quantum entanglement, and the emergence of the first commercially available quantum computer. The overall message conveys that quantum computing is advancing rapidly and poses unique computational abilities that classical computing cannot match.