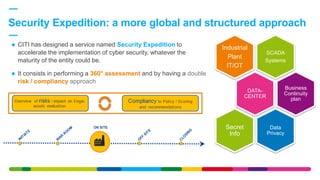
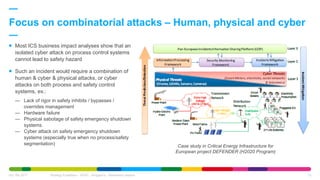
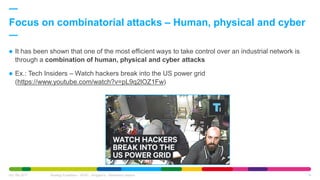
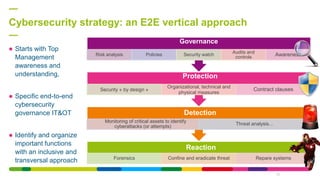
The African Cyber Security Summit held in Oran, Algeria, discussed a holistic approach to industrial cybersecurity, led by Faiz Djellouli from Engie, outlining the integration of governance and operational capabilities. It highlighted the vulnerabilities in industrial control systems and the increasing threats associated with the Internet of Things (IoT), emphasizing the need for robust cybersecurity measures and awareness. The presentation concluded with insights on the financial impacts of cybercrime and the importance of a unified cybersecurity strategy among various stakeholders.






![It is not only a reality, it is a business
10
Cybercrime has become a very
profitable “business”
• $126 billion: global price tag of
consumer cybercrime
• 689 million victims per year
• 10% increase of victims number
since 2015
[source: Norton Cybercrime report 2016]
European passports
1200$
1 million email address
10$ to 150$
AmEx Credit Card
30$
Bank auth. info
1% to 5% of
balance
173$
False int. driver license
300 000 airline points
90$
Underground data market
Cybercriminal services
DDoS attack
5$/hour
Ransomware
< 100$
Remote access
5$ to 10$
Hacking tutorial
20$ to 40$](https://image.slidesharecdn.com/africancybersecuritysummitfaizdjellouli-180417145603/85/Conference-ENGIE-ACSS-2018-10-320.jpg)