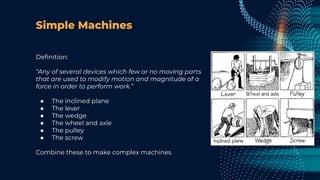
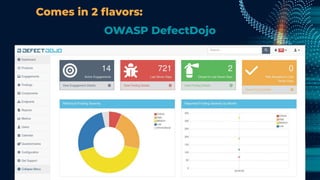
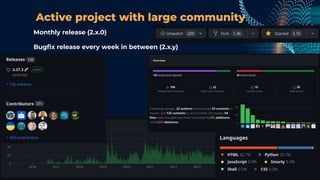
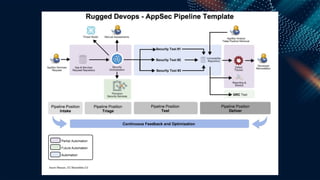
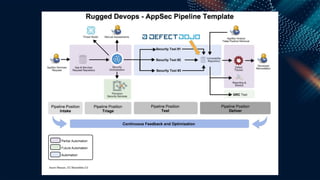
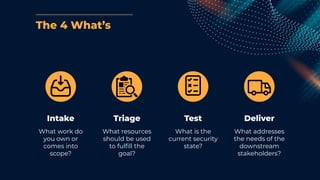
This document outlines a presentation by Matt Tesauro on effectively implementing DevSecOps within appsec teams, focusing on the importance of understanding the initial assessment, establishing a single source of truth, and iterating workflows. It introduces the 'four what’s' framework: intake, triage, testing, and delivery, which are critical for managing security lifecycles and stakeholder needs. The discussion emphasizes the creation of adaptable systems, continual learning, and using tools like DefectDojo to streamline processes in managing application security.