TCP Fairness for Uplink and Downlink Flows in WLANs
•
0 likes•311 views
The document discusses simulation parameters for a wireless network simulation in NS2 including the simulator used, simulation time, packet interval, background data traffic types, packet size, transmission range, routing protocol, and MAC protocol. It also briefly discusses queue management for wireless networks and how it differs from wired networks by not being visible. Client-server computing and networking is defined as well as packet scheduling policies and comparing FIFO to RENO scheduling. Bandwidth sharing approaches are examined for heterogeneous congestion control protocols. Finally, end-to-end throughput is defined and its decrease with more nodes in a chain topology is explained due to relaying overhead at intermediate nodes.
Report
Share
Report
Share
Recommended
DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...

DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...IEEEGLOBALSOFTTECHNOLOGIES
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09849539085, 09966235788 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.org20CS2007 Computer Communication Networks 

Module 6
Transport and Application Protocols Browsing E-commerce website, Remote access to server from workstation, Chat application. Process-to-process delivery, UDP, TCP, Mobile Transport Protocols, Congestion control, DNS, TELNET, HTTP.
Recommended
DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...

DOTNET 2013 IEEE MOBILECOMPUTING PROJECT Delay optimal broadcast for multihop...IEEEGLOBALSOFTTECHNOLOGIES
To Get any Project for CSE, IT ECE, EEE Contact Me @ 09849539085, 09966235788 or mail us - ieeefinalsemprojects@gmail.com-Visit Our Website: www.finalyearprojects.org20CS2007 Computer Communication Networks 

Module 6
Transport and Application Protocols Browsing E-commerce website, Remote access to server from workstation, Chat application. Process-to-process delivery, UDP, TCP, Mobile Transport Protocols, Congestion control, DNS, TELNET, HTTP.
Multi-Channel Multi-Interface Wireless Network Architecture

With the increase of usage of wireless networks for purposes where the nodes are either stationary or minimally mobile, focus is also on increasing the network capacity of wireless networks. One such way is to use non-overlapping multiple channels provided by 802.11 by using multiple interfaces per node. Multiple non overlapped channels exist in the 2.4 GHz and 5 GHz spectrum. Under this scenario, several challenges need to be addressed before all the available channels can be fully utilized.
Cs8591 u4

UNIT IV TRANSPORT LAYER 9
Introduction – Transport Layer Protocols – Services – Port Numbers – User Datagram Protocol – Transmission Control Protocol – SCTP.
Data Link Layer

Data Link Layer
The main goal of this layer is providing reliability to the layers above it.
3.1 DLL Design Issues
What are the services provided by DLL?
3.2 Error Detection and Correction
Adding redundancy in order to find and correct errors.
3.3 DLL Protocols
xxx
3.4 Sliding Window Protocols
xxx
3.5 Protocol Specification and Verification
xxx.
3.6 Examples
Performance Evaluation of Routing Protocols 

This is a research project based on Performance checking of the Routing Protocols. This Presentation shows the basic knowledge of the Protocols use (AODV, DSDV and DSR) and in the end it shows the Result and Conclusion by comparing the graphs which are generated through out the work.
Introduction to data link layer

Data Link Layer
Quick introduction to Data Link Layer.
Its various features and its working.
Data Communication, VTU 4th sem.
8 Packet Switching

A presentation prepared by my friend's friend. I have done no editing at all, I'm just uploading the presentation as it is.
Cs8601 4

UNIT IV MOBILE TRANSPORT AND APPLICATION LAYER
Mobile TCP– WAP – Architecture – WDP – WTLS – WTP –WSP – WAE – WTA Architecture – WML
Network layer - design Issues

Network layer - design Issues ,Store-and-Forward Packet Switching, Services Provided to the Transport Layer, Which service is the best , Implementation of Service , Implementation of Connectionless Service , Implementation of Connection-Oriented Service
On Multihop Distances in Wireless Sensor Networks with Random Node Locations

On Multihop Distances in Wireless Sensor
Networks with Random Node Locations
More Related Content
What's hot
Multi-Channel Multi-Interface Wireless Network Architecture

With the increase of usage of wireless networks for purposes where the nodes are either stationary or minimally mobile, focus is also on increasing the network capacity of wireless networks. One such way is to use non-overlapping multiple channels provided by 802.11 by using multiple interfaces per node. Multiple non overlapped channels exist in the 2.4 GHz and 5 GHz spectrum. Under this scenario, several challenges need to be addressed before all the available channels can be fully utilized.
Cs8591 u4

UNIT IV TRANSPORT LAYER 9
Introduction – Transport Layer Protocols – Services – Port Numbers – User Datagram Protocol – Transmission Control Protocol – SCTP.
Data Link Layer

Data Link Layer
The main goal of this layer is providing reliability to the layers above it.
3.1 DLL Design Issues
What are the services provided by DLL?
3.2 Error Detection and Correction
Adding redundancy in order to find and correct errors.
3.3 DLL Protocols
xxx
3.4 Sliding Window Protocols
xxx
3.5 Protocol Specification and Verification
xxx.
3.6 Examples
Performance Evaluation of Routing Protocols 

This is a research project based on Performance checking of the Routing Protocols. This Presentation shows the basic knowledge of the Protocols use (AODV, DSDV and DSR) and in the end it shows the Result and Conclusion by comparing the graphs which are generated through out the work.
Introduction to data link layer

Data Link Layer
Quick introduction to Data Link Layer.
Its various features and its working.
Data Communication, VTU 4th sem.
8 Packet Switching

A presentation prepared by my friend's friend. I have done no editing at all, I'm just uploading the presentation as it is.
Cs8601 4

UNIT IV MOBILE TRANSPORT AND APPLICATION LAYER
Mobile TCP– WAP – Architecture – WDP – WTLS – WTP –WSP – WAE – WTA Architecture – WML
Network layer - design Issues

Network layer - design Issues ,Store-and-Forward Packet Switching, Services Provided to the Transport Layer, Which service is the best , Implementation of Service , Implementation of Connectionless Service , Implementation of Connection-Oriented Service
What's hot (20)
Multi-Channel Multi-Interface Wireless Network Architecture

Multi-Channel Multi-Interface Wireless Network Architecture
Viewers also liked
On Multihop Distances in Wireless Sensor Networks with Random Node Locations

On Multihop Distances in Wireless Sensor
Networks with Random Node Locations
De snoepreisjes van de Europese Unie

Onder het mom van COREPER worden door de Europese Unie diverse snoepreisjes georganiseerd. OPvallend is dat de leden van COREPER hun partner kunnen meenemen op een dergelijke snoepreis.
An efficient hybrid peer to-peersystemfordistributeddatasharing

An Efficient Hybrid Peer-to-Peer System
for Distributed Data Sharing
Stichting van Jacques van Ypersele kreeg geld van rijke Amerikanen

Op 24 september 2013 richt Jacques van Ypersele de stichting Centres Ste-Thérèse op.
Uit een officieel document van de VS blijkt dat de stichting een geldsom kreeg van rijke Amerikaanse geldschieters.
Het gaat meer bepaald om The Stephen F & Camilla T Brauer Charitable Trust.
Hieruit blijkt dat Van Ypersele nog steeds erg goede relaties onderhoudt met onderdanen uit de Verenigde Staten.
Mahindra Renault Sandero

Mahindra Renault Sandero is about to released in India soon. Read the details about Renault Sandero in this presentation
Vorstelijk Vermogen - interview Thierry Debels - P-Magazine

Interview met auteur Thierry Debels in P-Magazine over zijn boek Vorstelijk vermogen (Pelckmans).
Hoe rijk is eurocommissaris Marianne Thyssen?

Nieuwbakken eurocommissaris Marianne Thyssen moet een verklaring afleggen over haar vermogen. Uit dat document blijkt dat ze een aanzienlijk roerend en onroerend vermogen heeft.
Waarom proces van Delphine wellicht met sisser afloopt

Op 23 september 2014 wordt het proces van Delphine Boël verdergezet. Hierop krijgt de rechtbank een maand de tijd om een uitspraak te doen. Tegen deze uitspraak kan vervolgens door alle partijen hoger beroep aangetekend worden.
De rechtszaak met dossiernummer 2013 / A / 9225 bevat enkele merkwaardige elementen.
Jean-Jacques De Gucht richt bedrijf op

Jean-Jacques De Gucht heeft een passie voor kunst. In interviews heeft hij al eens gezegd dat hij er stiekem van droomt om galeriehouder te worden.
Die droom heeft hij nu waargemaakt. In het voorjaar van 2014 heeft De Gucht met zijn echtgenote de bvba De filatuur opgericht, een kunstgalerie.
Viewers also liked (17)
On Multihop Distances in Wireless Sensor Networks with Random Node Locations

On Multihop Distances in Wireless Sensor Networks with Random Node Locations
Energy efficient cluster-based service discovery in wireless sensor networks

Energy efficient cluster-based service discovery in wireless sensor networks
An efficient hybrid peer to-peersystemfordistributeddatasharing

An efficient hybrid peer to-peersystemfordistributeddatasharing
Admission control and routing in multi hop wireless networks

Admission control and routing in multi hop wireless networks
Stichting van Jacques van Ypersele kreeg geld van rijke Amerikanen

Stichting van Jacques van Ypersele kreeg geld van rijke Amerikanen
A novel pause count backoff algorithm for channel access

A novel pause count backoff algorithm for channel access
Vorstelijk Vermogen - interview Thierry Debels - P-Magazine

Vorstelijk Vermogen - interview Thierry Debels - P-Magazine
Waarom proces van Delphine wellicht met sisser afloopt

Waarom proces van Delphine wellicht met sisser afloopt
Similar to TCP Fairness for Uplink and Downlink Flows in WLANs
Efficient and Fair Bandwidth Allocation AQM Scheme for Wireless Networks

Heterogeneous Wireless Networks are considered nowadays as one of the potential areas in research and development. The traffic management’s schemes that have been used at the fusion points between the different wireless networks are classical and conventional. This paper is focused on developing a novel scheme to overcome the problem of traffic congestion in the fusion point router interconnected the heterogeneous wireless networks. The paper proposed an EF-AQM algorithm which provides an efficient and fair allocation of bandwidth among different established flows. Finally, the proposed scheme developed, tested and validated through a set of experiments to demonstrate the relative merits and capabilities of a proposed scheme
Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network 

Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network
4..[26 36]signal strength based congestion control in manet![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
International Journals Call for paper, http://www.iiste.org
Performance Evaluation of TCP with Adaptive Pacing and LRED in Multihop Wirel...

Transmission Control Protocol (TCP) was designed to provide reliable end-to-end delivery of
data over unreliable networks. In practice, most TCP deployments have been carefully designed in the
context of wired networks. Ignoring the properties of wireless and Ad-hoc Networks can lead to TCP
implementations with poor performance. In a wireless network, however packet losses occur more often
due to unreliable wireless links than due to congestion. When using TCP over wireless links, each packet
loss on the wireless link results in congestion control measures being invoked at the source. This causes
severe performance degradation. If there is any packet loss in wireless networks, then the reason for that
has to be found out. If there is congestion, then only congestion control mechanism has to be applied.
This work shows the performance of TCP with Adaptive Pacing (TCP-AP) and Link Random Early
Discard (LRED) as queuing model in multihop transmission when the source and destination nodes are
in mobile nature. The adaptive pacing technique seeks to improve spatial reuse. The LRED technique
seeks to react earlier to link overload. This paper consists of simulated environment results under
different network scenarios. This work proves that the combination of TCP-AP and LRED give much
better result than as the individual technique. Simulations are done with the use of NS-2.
Data link layer 

This presentation covers the design issues of DLL, Error Correction and detection techniques, Sliding window protocols
www.ijerd.com

hard copy of journal, Call for Papers 2012, publishing of journal, journal of science and technology
Networking issues for distributed systems

> Networking Issues for Distributed Systems
> Basics of Networking
> Internet Protocols
Performance Evaluation of a Layered WSN Using AODV and MCF Protocols in NS-2

In layered networks, reliability is a major concern
as link failures at lower layer will have a
great impact on network reliability. Failure at a l
ower layer may lead to multiple failures at the
upper layers which deteriorate the network performa
nce. In this paper, the scenario of such a
layered wireless sensor network is considered for A
d hoc On-Demand Distance Vector (AODV)
and Multi Commodity Flow (MCF) routing protocols. M
CF is
developed using
polynomial time
approximation algorithms for the failure polynomial
. Both protocols are compared in terms of
different network parameters such as throughput, pa
cket loss and end to end delay. It was
shown that the network reliability is better when M
CF protocol is used. It was also shown that
maximizing the min cut of the layered network maxim
izes reliability in the terms of successful
packet transmission of network. Thetwo routing prot
ocolsare implemented in the scenario of
discrete network event simulator NS-2.
Research Inventy : International Journal of Engineering and Science

Research Inventy : International Journal of Engineering and Science is published by the group of young academic and industrial researchers with 12 Issues per year. It is an online as well as print version open access journal that provides rapid publication (monthly) of articles in all areas of the subject such as: civil, mechanical, chemical, electronic and computer engineering as well as production and information technology. The Journal welcomes the submission of manuscripts that meet the general criteria of significance and scientific excellence. Papers will be published by rapid process within 20 days after acceptance and peer review process takes only 7 days. All articles published in Research Inventy will be peer-reviewed.
Predictable Packet Lossand Proportional Buffer Scaling Mechanism

Packet losses at IP network are common behavior at
the time of congestion. The TCP traffic is explained as in
terms of load and capacity. The load should be measured as
number of sender actively competes for a bottleneck link and
the capacity as the total network buffering available to those
senders. Though there are many congestion mechanism
already in practice like congestion window, slow start,
congestion avoidance, fast transmit but still we see erratic
behavior when there is a large traffic. The TCP protocol that
controls sources send rates degrades rapidly if the network
cannot store at least a few packets per active connection. Thus
the amount of router buffer space required for good
performance scales with the number of active connections
and the bandwidth utilization by each active connections. As
in the current practice, the buffer space does not scale in this
way and router drops the packet without looking at bandwidth
utilization of each connections. The result is global
synchronization and phase effect as well as packet from the
unlucky sender will be frequently dropped. The simultaneous
requirements of low queuing delay and of large buffer
memories for large numbers of connections pose a problem.
Routers should enforce a dropping policy by proportional to
the bandwidth utilization by each active connection. Router
will provision the buffering mechanism when processing slows
down. This study explains the existing problem with drop-tail
and RED routers and proposes the new mechanism to predict
the effective bandwidth utilization of the clients depending
on their history of utilization and drop the packet in different
pattern after analyzing the network bandwidth utilization at
each specific interval of time
Similar to TCP Fairness for Uplink and Downlink Flows in WLANs (20)
Efficient and Fair Bandwidth Allocation AQM Scheme for Wireless Networks

Efficient and Fair Bandwidth Allocation AQM Scheme for Wireless Networks
Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network 

Comparative Analysis of Different TCP Variants in Mobile Ad-Hoc Network
Iaetsd an effective approach to eliminate tcp incast

Iaetsd an effective approach to eliminate tcp incast
4..[26 36]signal strength based congestion control in manet![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![4..[26 36]signal strength based congestion control in manet](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
4..[26 36]signal strength based congestion control in manet
11.signal strength based congestion control in manet

11.signal strength based congestion control in manet
Performance Evaluation of TCP with Adaptive Pacing and LRED in Multihop Wirel...

Performance Evaluation of TCP with Adaptive Pacing and LRED in Multihop Wirel...
Performance Evaluation of a Layered WSN Using AODV and MCF Protocols in NS-2

Performance Evaluation of a Layered WSN Using AODV and MCF Protocols in NS-2
Research Inventy : International Journal of Engineering and Science

Research Inventy : International Journal of Engineering and Science
Predictable Packet Lossand Proportional Buffer Scaling Mechanism

Predictable Packet Lossand Proportional Buffer Scaling Mechanism
More from ambitlick
DCIM: Distributed Cache Invalidation Method for Maintaining Cache Consistency...

DCIM: Distributed Cache Invalidation
Method for Maintaining Cache Consistency
in Wireless Mobile Networks
Partial Doc , For more project contact : Ambitlick@gmail.com , PH : 8940956123
Low cost Java 2013 IEEE projects

Bulk Projects For sale
IEEE 2009-10-11-12-13 PAPERS AVILABLE.
We are providing low cost project for final year student projects.
Solved 2010 -2011 -2012 - 2013 IEEE in all the domain
Mobile : 8940956123
E-Mail : ambitlick@gmail.com,
INNOVATIVE TITLES ARE ALSO WELLCOME TO DO WITH US
For All BE/BTech, ME/MTech, MSC/MCA/MS , and diplamo graduates
PROJECT SUPPORTS & DELIVERABLES
•Project Abstract
•IEEE Paper
•PPT / Review Details
•Project Report
•Working Procedure in Video
•Screen Shots
•Materials & Books in CD
•Project Certification
Efficient spread spectrum communication without pre shared secrets

Efficient spread spectrum communication without pre shared secrets
Comments on “mabs multicast authentication based on batch signature”

Comments on “mabs multicast authentication based on batch signature”
Energy-Efficient Protocol for Deterministic and Probabilistic Coverage In Sen...

Energy-Efficient Protocol for Deterministic and Probabilistic Coverage
In Sensor Networks
Estimating Parameters of Multiple Heterogeneous Target Objects Using Composit...

Estimating Parameters of Multiple
Heterogeneous Target Objects Using Composite
Sensor Nodes
A Privacy-Preserving Location Monitoring System for Wireless Sensor Networks

A Privacy-Preserving Location Monitoring
System for Wireless Sensor Networks
More from ambitlick (20)
DCIM: Distributed Cache Invalidation Method for Maintaining Cache Consistency...

DCIM: Distributed Cache Invalidation Method for Maintaining Cache Consistency...
Moderated group authoring system for campus wide workgroups

Moderated group authoring system for campus wide workgroups
Efficient spread spectrum communication without pre shared secrets

Efficient spread spectrum communication without pre shared secrets
Adaptive weight factor estimation from user review 1

Adaptive weight factor estimation from user review 1
Moderated group authoring system for campus wide workgroups

Moderated group authoring system for campus wide workgroups
Efficient spread spectrum communication without pre shared secrets

Efficient spread spectrum communication without pre shared secrets
Comments on “mabs multicast authentication based on batch signature”

Comments on “mabs multicast authentication based on batch signature”
Energy-Efficient Protocol for Deterministic and Probabilistic Coverage In Sen...

Energy-Efficient Protocol for Deterministic and Probabilistic Coverage In Sen...
Estimating Parameters of Multiple Heterogeneous Target Objects Using Composit...

Estimating Parameters of Multiple Heterogeneous Target Objects Using Composit...
A Privacy-Preserving Location Monitoring System for Wireless Sensor Networks

A Privacy-Preserving Location Monitoring System for Wireless Sensor Networks
Recently uploaded
The geography of Taylor Swift - some ideas

Geographical themes connected with Taylor Swift's ERAS tour - coming to the UK in June 2024
2024.06.01 Introducing a competency framework for languag learning materials ...

http://sandymillin.wordpress.com/iateflwebinar2024
Published classroom materials form the basis of syllabuses, drive teacher professional development, and have a potentially huge influence on learners, teachers and education systems. All teachers also create their own materials, whether a few sentences on a blackboard, a highly-structured fully-realised online course, or anything in between. Despite this, the knowledge and skills needed to create effective language learning materials are rarely part of teacher training, and are mostly learnt by trial and error.
Knowledge and skills frameworks, generally called competency frameworks, for ELT teachers, trainers and managers have existed for a few years now. However, until I created one for my MA dissertation, there wasn’t one drawing together what we need to know and do to be able to effectively produce language learning materials.
This webinar will introduce you to my framework, highlighting the key competencies I identified from my research. It will also show how anybody involved in language teaching (any language, not just English!), teacher training, managing schools or developing language learning materials can benefit from using the framework.
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk from the OECD’s Centre for Educational Research and Innovation presents at the Ask an Expert Webinar: How can education support child empowerment?
Unit 8 - Information and Communication Technology (Paper I).pdf

This slides describes the basic concepts of ICT, basics of Email, Emerging Technology and Digital Initiatives in Education. This presentations aligns with the UGC Paper I syllabus.
Instructions for Submissions thorugh G- Classroom.pptx

This presentation provides a briefing on how to upload submissions and documents in Google Classroom. It was prepared as part of an orientation for new Sainik School in-service teacher trainees. As a training officer, my goal is to ensure that you are comfortable and proficient with this essential tool for managing assignments and fostering student engagement.
Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf

In this webinar you will learn how your organization can access TechSoup's wide variety of product discount and donation programs. From hardware to software, we'll give you a tour of the tools available to help your nonprofit with productivity, collaboration, financial management, donor tracking, security, and more.
Model Attribute Check Company Auto Property

In Odoo, the multi-company feature allows you to manage multiple companies within a single Odoo database instance. Each company can have its own configurations while still sharing common resources such as products, customers, and suppliers.
Digital Tools and AI for Teaching Learning and Research

This Presentation in details discusses on Digital Tools and AI for Teaching Learning and Research
1.4 modern child centered education - mahatma gandhi-2.pptx

Child centred education is an educational approach that priorities the interest, needs and abilities of the child in the learning process.
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH ANSWERS.
"Protectable subject matters, Protection in biotechnology, Protection of othe...

Protectable subject matters, Protection in biotechnology, Protection of other biological materials, Ownership and period of protection
The approach at University of Liverpool.pptx

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
The Roman Empire A Historical Colossus.pdf

The Roman Empire, a vast and enduring power, stands as one of history's most remarkable civilizations, leaving an indelible imprint on the world. It emerged from the Roman Republic, transitioning into an imperial powerhouse under the leadership of Augustus Caesar in 27 BCE. This transformation marked the beginning of an era defined by unprecedented territorial expansion, architectural marvels, and profound cultural influence.
The empire's roots lie in the city of Rome, founded, according to legend, by Romulus in 753 BCE. Over centuries, Rome evolved from a small settlement to a formidable republic, characterized by a complex political system with elected officials and checks on power. However, internal strife, class conflicts, and military ambitions paved the way for the end of the Republic. Julius Caesar’s dictatorship and subsequent assassination in 44 BCE created a power vacuum, leading to a civil war. Octavian, later Augustus, emerged victorious, heralding the Roman Empire’s birth.
Under Augustus, the empire experienced the Pax Romana, a 200-year period of relative peace and stability. Augustus reformed the military, established efficient administrative systems, and initiated grand construction projects. The empire's borders expanded, encompassing territories from Britain to Egypt and from Spain to the Euphrates. Roman legions, renowned for their discipline and engineering prowess, secured and maintained these vast territories, building roads, fortifications, and cities that facilitated control and integration.
The Roman Empire’s society was hierarchical, with a rigid class system. At the top were the patricians, wealthy elites who held significant political power. Below them were the plebeians, free citizens with limited political influence, and the vast numbers of slaves who formed the backbone of the economy. The family unit was central, governed by the paterfamilias, the male head who held absolute authority.
Culturally, the Romans were eclectic, absorbing and adapting elements from the civilizations they encountered, particularly the Greeks. Roman art, literature, and philosophy reflected this synthesis, creating a rich cultural tapestry. Latin, the Roman language, became the lingua franca of the Western world, influencing numerous modern languages.
Roman architecture and engineering achievements were monumental. They perfected the arch, vault, and dome, constructing enduring structures like the Colosseum, Pantheon, and aqueducts. These engineering marvels not only showcased Roman ingenuity but also served practical purposes, from public entertainment to water supply.
special B.ed 2nd year old paper_20240531.pdf

Instagram:-
https://instagram.com/special_education_needs_01?igshid=YmMyMTA2M2Y=
WhatsApp:-
https://chat.whatsapp.com/JVakNIYlSV94x7bwunO3Dc
YouTube:-
https://youtube.com/@special_education_needs
Teligram :- https://t.me/special_education_needs
Slide Shere :-
https://www.slideshare.net/shabnambano20?utm_campaign=profiletracking&utm_medium=sssite&utm_source=ssslideview
Biological Screening of Herbal Drugs in detailed.

Biological screening of herbal drugs: Introduction and Need for
Phyto-Pharmacological Screening, New Strategies for evaluating
Natural Products, In vitro evaluation techniques for Antioxidants, Antimicrobial and Anticancer drugs. In vivo evaluation techniques
for Anti-inflammatory, Antiulcer, Anticancer, Wound healing, Antidiabetic, Hepatoprotective, Cardio protective, Diuretics and
Antifertility, Toxicity studies as per OECD guidelines
The French Revolution Class 9 Study Material pdf free download

The French Revolution, which began in 1789, was a period of radical social and political upheaval in France. It marked the decline of absolute monarchies, the rise of secular and democratic republics, and the eventual rise of Napoleon Bonaparte. This revolutionary period is crucial in understanding the transition from feudalism to modernity in Europe.
For more information, visit-www.vavaclasses.com
Overview on Edible Vaccine: Pros & Cons with Mechanism

This ppt include the description of the edible vaccine i.e. a new concept over the traditional vaccine administered by injection.
Recently uploaded (20)
2024.06.01 Introducing a competency framework for languag learning materials ...

2024.06.01 Introducing a competency framework for languag learning materials ...
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk - How can education support child empowerment.pptx
Unit 8 - Information and Communication Technology (Paper I).pdf

Unit 8 - Information and Communication Technology (Paper I).pdf
Instructions for Submissions thorugh G- Classroom.pptx

Instructions for Submissions thorugh G- Classroom.pptx
Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf

Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf
Digital Tools and AI for Teaching Learning and Research

Digital Tools and AI for Teaching Learning and Research
1.4 modern child centered education - mahatma gandhi-2.pptx

1.4 modern child centered education - mahatma gandhi-2.pptx
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...
"Protectable subject matters, Protection in biotechnology, Protection of othe...

"Protectable subject matters, Protection in biotechnology, Protection of othe...
The French Revolution Class 9 Study Material pdf free download

The French Revolution Class 9 Study Material pdf free download
Overview on Edible Vaccine: Pros & Cons with Mechanism

Overview on Edible Vaccine: Pros & Cons with Mechanism
TCP Fairness for Uplink and Downlink Flows in WLANs
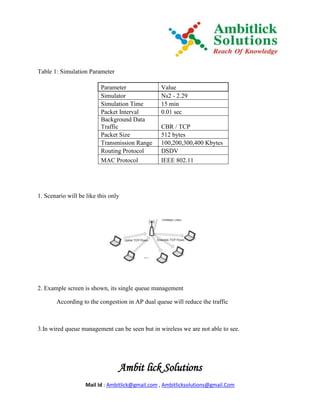
- 1. Table 1: Simulation Parameter Parameter Value Simulator Ns2 - 2.29 Simulation Time 15 min Packet Interval 0.01 sec Background Data Traffic CBR / TCP Packet Size 512 bytes Transmission Range 100,200,300,400 Kbytes Routing Protocol DSDV MAC Protocol IEEE 802.11 1. Scenario will be like this only 2. Example screen is shown, its single queue management According to the congestion in AP dual queue will reduce the traffic 3.In wired queue management can be seen but in wireless we are not able to see. Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 2. NETWORK MODULE Client-server computing or networking is a distributed application architecture that partitions tasks or workloads between service providers (servers) and service requesters, called clients. Often clients and servers operate over a computer network on separate hardware. A server machine is a high- performance host that is running one or more server programs which share its resources with clients. A client also shares any of its resources; Clients therefore initiate communication sessions with servers which await (listen to) incoming requests. PACKET SCHEDULING This packet scheduling policy is simple to implement, and yields good performance in the common case that node schedules are known, and information about node availability is accurate. A potential drawback is that a node crash (or other failure event) can lead to a number of wasted RTSs to the failed node. When added across channels, the number may exceed the limit of 7 retransmission attempts allowed for a single channel in the IEEE 802.11 Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 3. BANDWIDTH SHARING Approach where each node requests and grants as much bandwidth as possible at each turn. Additionally, we compare the RENO algorithm for packet scheduling to a First-In-First-Out (FIFO) scheduler where all the SDUs with the same next-hop are enqueued into the same buffer. For this purpose we simulate a network with an increasing number of nodes, from 2 to 10, arranged in a chain topology. Each node has one traffic flow directed to the chain end-point node, carried with a constant bit-rate stream of 1000 bytes packets emulating infinite bandwidth demands. Congestion control has been extensively studied for networks running a single protocol. However, when sources sharing the same network react to different congestion signals, the existing duality model no longer explains the behavior of bandwidth allocation. The existence and uniqueness properties of equilibrium in heterogeneous protocol case are examined. BURSTY TRAFFIC The end-to-end throughput (or throughput, for short), which is defined as the number of bits received by the destination node per second for a given traffic flow, without any MAC overhead. As it can be seen, the throughput steeply decreases as the number of nodes increases, regardless of the scheme adopted. This is because an increasing fraction of the channel capacity is employed to relay packets at intermediate nodes. For instance, with three nodes the end-to-end Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
- 4. throughput is about 2/3 of the available raw bandwidth: 1/3 is consumed by the traffic flow that is one hop from the destination, and 2/3 is consumed by the other one that has a length of two hops. Ambit lick Solutions Mail Id : Ambitlick@gmail.com , Ambitlicksolutions@gmail.Com
