The authors provide an overview of standardized service discovery and delivery solutions for mobile ad hoc networks (MANETs). They propose a novel architecture that allows selecting a service provider based on metrics like the power supply of the provider and the path to the destination. This architecture is based on a decentralized approach using Service Location Protocol (SLP) extensions. It aims to provide reliable service discovery and delivery in MANETs by considering energy constraints affecting the network topology and connectivity.

![KATSIGIANNIS LAYOUT 10/9/06 1:11 PM Page 91
case the requested telephone number does not
exist in our phone book, we can alternatively
(XML) is used in control messages that describe
device features and capabilities. The XML
The Jini
search for it in the white pages, search in a relat- description allows complex, powerful descrip- communication
ed site on the Internet, call the telephone direc- tions of device capabilities — and, most impor-
tory service, or even ask friends or family. This is tantly — in a standardized manner. SOAP over mechanism is based
the case when the same service can be provided HTTP can be used for the transportation of the
by several actors (i.e., several service locations). XML control messages, which is also a on the Java Remote
Telecommunication applications, however, gen- lightweight and standard communication mecha-
erally do not have the luxury of the richness and nism. Method Invocation,
stability of human communications available to
them [1]. Harking back to the previous example,
The Jini architecture is an extension of the
Java programming language, where each device
which allows the
even in our everyday life, we would be happy if is assumed to run a Java virtual machine (JVM). code movement
we could a priori know that the desired tele- Devices and applications are registered with a
phone number does not exist in our phone book, Jini network using processes like Discovery and around the network.
while, for example, searching in the white pages Join. To join a Jini network, devices or applica-
will be much more efficient and faster than ask- tions register themselves in a Lookup Table, a Thus, the benefit of
ing our friends for it. The above paradigm is database placed on a lookup server, which keeps
depicted in the case of telecommunication ser- track of all services in the network. This kind of code mobility
vices, when multiple mappings of the same ser-
vice are offered by different servers (i.e., service
registration follows the concept of leasing. In
other words, the device is registering itself and
replaces the
locations). The client has to choose a specific exposes its services only for a certain time period necessity of
server providing the desired service, based on — called a lease — which is very useful, espe-
multiple criteria. Those factors can be network cially for dynamic ad hoc networks. Inside the preinstalling drivers
layer parameters, the hop-count number, or even Lookup Table, apart from the pointers associat-
the actual distance between client and server. ing a service provider with a requested service, on the client.
The last parameter could be very useful in the Java code for these services can also be
mobile environments, since routing is based not stored, while device drivers, interfaces, and other
only on the number of hops a message will roam auxiliary programs helping the clients access a
from the source to the destination, but also on service can be uploaded to the Lookup Table
the distance or the traffic load between the too. When a client wants to utilize a service, the
nodes. object code is downloaded to the client’s JVM.
Moreover, the selection of the service descrip- The Jini communication mechanism is based on
tion language is very proprietary in service dis- the Java Remote Method Invocation (RMI),
covery. A client requiring a service and a server which allows the code movement around the
offering this service must use a common descrip- network. Thus, the benefit of code mobility
tion language in order to efficiently map the ser- replaces the necessity of preinstalling drivers on
vice description with the location. In a the client.
service-discovery mechanism, services advertise SLP is an IETF standard for service discovery
themselves, thus providing information and [3]. There are three types of agents that operate
details about their capabilities and access (e.g. on behalf of network-based software:
IP address). • The user sgent (UA), which performs service
Several protocols and technologies support discovery on behalf of the client software
service-discovery and delivery mechanisms. The • The service agent (SA), which advertises the
most commonly known and used ones are briefly location and attributes on behalf of the ser-
described below and are mentioned in [2]. vices
Universal plug and play (UPnP), an extension • The directory agent (DA), which aggregates
of Microsoft’s plug and play technology, is appli- service information registered or advertised by
cable in the case where devices, either wireless the SAs
or wired, are reachable via TCP/IP. It is pro- SLP can operate in both centralized and
posed for small office or home networks to decentralized modes. In the centralized mode
enable peer-to-peer mechanisms for auto-config- one or more DAs are present in the network
uration of devices, service discovery, and control registering information about a service.
of services. In UPnP architecture there are two Through either the service agent’s advertise-
main classifications of devices: controlled devices ment (SAAdvert) messages or the service regis-
and control points. Controlled devices are the ter (SrvReg) messages, sent by an SA, the DA
devices that form the network and respond to registers in its cache information about the
requests coming from the control points. When location (URL of the node) and the type
a new device joins the network, it can dynamical- (attributes) of a service. When a UA requests a
ly obtain an IP address. If this node functions as service, it sends a service request (SrvRqst)
a controlled device, it has to convey its services message to the DA. Then the DA replies with a
and capabilities to the control points upon service reply (SrvRply) message. With this mes-
request. This action is accomplished by using the sage, the DA informs the client about the loca-
Simple Service Discovery Protocol (SSDP). In tion of the service. Then the UA requests
the case of a newcomer control point, the device directly the service from the SA, by establishing
has to exchange discovery messages with the a direct TCP connection.
other nodes of the network, in order to gather The decentralized approach is associated with
information about the available services and the absence of DAs in the network. In that case,
devices of the network. UPnP architecture is UAs repeatedly multicast requests (SrvRqst) to
applied over standard TCP/IP and web-based the SAs. The SA that can offer the requested
networks, while eXtensible Markup Language service unicasts a reply message.
IEEE Wireless Communications • October 2006 91
Authorized licensed use limited to: Annamalai University. Downloaded on August 8, 2009 at 02:30 from IEEE Xplore. Restrictions apply.](https://image.slidesharecdn.com/architectureforreliableservicediscovery-120715132652-phpapp01/85/Architecture-for-reliable-service-discovery-2-320.jpg)
![KATSIGIANNIS LAYOUT 10/9/06 1:11 PM Page 92
If a node is off need to register services to a registry server. The
description of services is made through the
because of low Node 0 DARPA Agent Markup Language
(DAML+OIL).
power or processing Node 1 In-advance cross-layer architectures have
been proposed in order to reduce the number of
resources, the whole message exchanges in a mobile ad hoc network.
However, the cross-layer approach simplifies the
path from the source procedure of service request and reply, since all
to the destination these messages are included in the network layer
and the application layer is lightweight. A cross-
Node 3
Node 2
will probably change, layer architecture is proposed in [7], where the
service-discovery and delivery messages are
thus causing included in the Dynamic Source Routing (DSR)
I Figure 1. A simple mobile ad hoc network. protocol and the Destination Sequenced Dis-
difficulties in the tance Vector (DSDV) algorithm, representatives
of reactive (on-demand) routing and proactive
discovery of services SERVICE DISCOVERY IN MANET (table-driven) routing, respectively.
as well as in the Architectures for service discovery like SLP and
Another cross-layer architecture is proposed
in [3] with the On-Demand Multicast Routing
establishment of a Jini do not offer efficiency in a mobile ad hoc Protocol (ODMRP), where the service advertise-
network, due to energy and mobility constraints. ment and discovery messages are included in the
connection between Specifically, the centralized mechanisms of these network layer.
protocols act as a contrary wind against
the service provider MANET, since the DA’s presence and the
Lookup Server impose difficulties, and both can POWER CONSTRAINTS AND
and the client r be often assumed as a bottleneck for the net- SERVICE DISCOVERY IN MANETS
equiring the work. Sending periodically updated SrvReg mes-
sages to the DA or the Lookup Table and the The most intense problem in mobile networks,
specific service. concomitant SrvRqst and SrvRply messages can especially in mobile ad hoc networks, is network
cause extra traffic to the network. connectivity, which can change due to power
Moreover, all those extra messages sent to consumption as analyzed in [8]. If a node is off
the DA or to the Lookup Server will lead to because of low power or processing resources,
additional energy consumption from the nodes’ the whole path from the source to the destina-
point of view, causing rapid “death” of nodes. A tion will probably change, thus causing difficul-
better solution in the implementation of the SLP ties in the discovery of services as well as in the
in a MANET could be a decentralized approach establishment of a connection between the ser-
without the presence of the DA. Both central- vice provider and the client requiring the specific
ized and decentralized SLP approaches have service.
already been developed in CSLP and DSLP An example depicting the abovementioned
architectures for service discovery in MANETs difficulties in a mobile ad hoc network is shown
[4]. in Fig. 1.
Because of the infrastructureless nature of The mobile ad hoc network is comprised by
this kind of networks and their dynamic topolo- four nodes and we assume that node 0 is request-
gy, service discovery is becoming a crucial issue. ing a service that only node 3 can provide to
Bandwidth and energy constraints reduce the him. If the requested service is energy and time
efficiency of the well-known application-layer demanding, such as, for example, a video, music,
service-discovery protocols. Previous attempts or other multimedia service, power management
made to implement an application-layer service- is very important in order to increase network’s
discovery technique are briefly described below. lifetime. Therefore node 0, which requests the
Konark is a service-discovery and delivery service from node 3, has to know the remaining
protocol implemented for mobile ad hoc net- power not only of the service provider, but also
works. Concerning discovery, Konark proposes a of the intermediate nodes in order to select the
completely distributed, peer-to-peer mechanism proper route to the destination for both the
giving each device the ability to advertise and request and reply messages.
discover services in the network. The service
description is based on XML messages, and the
services are described in a way that is under- THE PROPOSED ARCHITECTURE FOR POWER
standable by humans and machines alike. Each MANAGEMENT BASED ON SLP EXTENSIONS
participating node can cache its services in a
local registry and deliver them to the requested The basic challenge of mobile ad hoc networks is
client using a micro-HTTP server. The service to develop algorithms that take into account the
delivery mechanism is based on the exchange of resources’ constraints. All devices participating
SOAP-based messages [5]. in a MANET have restricted power resources
Group-based Service Discovery (GSD) is a such as batteries. It is probable that a mobile
novel distributed service-discovery architecture node may fail because of lack of resources,
based on the concept of peer-to-peer caching of destroying (in this case) a link or a route and
service advertisement and group-based intelli- changing the network’s topology. This dynamic
gent forwarding of service requests [5]. Contrary configuration of network topology causes serious
to the abovementioned techniques, there is no problems in service discovery and delivery. This
92 IEEE Wireless Communications • October 2006
Authorized licensed use limited to: Annamalai University. Downloaded on August 8, 2009 at 02:30 from IEEE Xplore. Restrictions apply.](https://image.slidesharecdn.com/architectureforreliableservicediscovery-120715132652-phpapp01/85/Architecture-for-reliable-service-discovery-3-320.jpg)
![KATSIGIANNIS LAYOUT 10/9/06 1:11 PM Page 93
A better solution in
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
Version Function-ID Length the implementation
Length cont. O F D
Next extension offset cont.
Reserved
XID
Next extension offset
of the SLP in a
Language tag length Language tag MANET could be a
Protocol data
decentralized
Protocol data approach without the
Extension ID (0x8001) Next extension offset
Next extension Extension data presence of the DA.
offset cont. Request/reply Byte 1 Byte 2
Both centralized and
I Figure 2. SLP message structure. decentralized SLP
approaches of have
problem can be overcome by introducing a new
service-discovery and delivery architecture, in
remaining power resources. It is an implementa-
tion requirement that every node engaging in
already been
which critical information, such as the remaining the proposed power-management scheme will be developed in CSLP
energy resources of the service provider and the able to report their lifetime in minutes, from
remaining power of the intermediate nodes, is their available power resources. Routing based and DSLP
known to the client. on this metric, called Minimum Battery Cost
Our proposed scheme is based on a decen- Routing (MBCR), has been suggested in [10], architectures for
tralized extended approach of the Service Loca- where it was compared with regard to perfor-
tion Protocol version 2 (SLPv2). SLPv2 is mance to other power-based routing schemes service discovery
documented in [9], where the protocol life cycle,
message structuring, and scope are described.
such as Minimum Total Transmission Power
Routing (MTTPR) and Min–Max Battery Cost
in MANETs
SLPv2 is flexible enough to provide an extension Routing (MMBCR).
mechanism through which the protocol adapts to The Next Extension Offset field has two pos-
specific service-discovery requirements. Guide- sible values
lines for extending the protocol are also docu- • Zero, when this is the last extension section in
mented in RFC 3224. the message
The extension mechanism in SLPv2 is provid- • The value of the “Extension Offset” field in
ed by dedicated sections located at the end of the message header plus eight for the 8 bytes
SLP messages. The exact position of the first of the proposed extension section, when there
extension in an SLP message is defined by a are subsequent extension sections in the SLP
dedicated field in the SLP message header, as an message.
offset in bytes from the message beginning. This Accordingly, the Rqst/Rply field has a value
is the “Next Extension Offset” field, which takes of
2 bytes and contains an integer number in net- • 0 × 00 when the extension section resides in an
work byte order. Each extension section at the SLP SrvRqst message
end of the message defines the exact position of • 0 × F0 when the extension section resides in
the following extension section as an offset (in an SLP SrvRply message.
number of bytes) from the message beginning. The proposed incorporation of the concepts
Again, the field’s name is “Next Extension Off- of MBCR in SLP-based discovery is described in
set,” its length is two bytes, and it contains an the algorithm below. For the sake of clarity, the
integer number in network byte order. If no fur- algorithm’s functionality concerning the pro-
ther extension section is present, the immediate posed extended-SLP architecture is described
preceding “Next Extension Offset” field should using an example and is depicted in Fig. 3. The
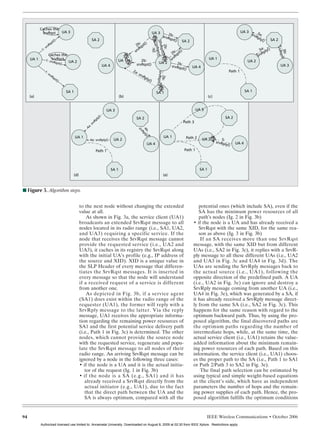
have the value zero. Figure 2 describes this assumptions regarding the following description
arrangement. It shows the general structure of are that UA1 enters into the MANET and
an SLP message and the location and length of requests a service that both SA1 and SA2 can
the different fields. The SLP message header provide, while UA2, UA3, and UA4 cannot offer
takes up the first four lines of the matrix, fol- the requested service. The latter can act only as
lowed by the SLP message protocol data and the intermediate routing nodes during the service
extension field which takes up the last two lines. provision phase. We also assume that each SA
The proposed power-management extension that receives a SrvRqst message replies with the
for SLP is assigned the Extension ID 0x8001, as corresponding SrvRply one by extending it and
described in RFC 3224 for experimental exten- adding in the above-described field its remaining
sions. The “Extension Data” field of the pro- power resource value. Furthermore, we assume
posed extension section has a length of three that each node manipulates the received extend-
bytes and it contains a one byte field defining ed SrvRply call-back SLP message, as described
whether this is a power state request or response, below: it first checks this new field in the SrvR-
and two bytes containing an integer number in ply message regarding the remaining power
network byte order, representing the minutes that resources of the previous node and, if its own
the corresponding route to a service provider will resources are lower than the previous one, it
be available, expressed as the remaining lifetime of substitutes this field with the lower value (its
the intermediate hop in the route with the least own value); otherwise, it dispatches the message
IEEE Wireless Communications • October 2006 93
Authorized licensed use limited to: Annamalai University. Downloaded on August 8, 2009 at 02:30 from IEEE Xplore. Restrictions apply.](https://image.slidesharecdn.com/architectureforreliableservicediscovery-120715132652-phpapp01/85/Architecture-for-reliable-service-discovery-4-320.jpg)
![KATSIGIANNIS LAYOUT 10/9/06 1:11 PM Page 95
[9] E. Guttman et al., “Service Location Protocol (SLP) Ver-
regarding service provision, while in parallel it
has the intention to conserve the MANET’s cur- sion 2,” IETF RFC 2608, June 1999. Further cross-layer
[10] C.-K. Toh, “Maximum Battery Life Routing to Support
rent configuration and network topology. Ubiquitous Mobile Computing in Wireless Ad Hoc Net- implementation,
works,” IEEE Commun. Mag., June 2001, pp. 138–47.
CONCLUSIONS AND FUTURE WORK incorporating the
BIOGRAPHIES
In this article a new architecture concerning ser- CHRISTOS I. KATSIGIANNIS (chkatsig@telecom.ntua.gr) received useful power and
a Dipl-Ing. degree from the Computer Engineering and
vice-discovery procedures in a mobile ad hoc
network (MANET) has been proposed. This
Informatics Department of Patras (CEID) in 2004. Since
then he has been a research associate and a Ph.D. candi-
hop-number metrics
architecture is implemented in the application
layer, without taking into account procedures in
date in the Intelligent Communications and Broadband
Networks Laboratory of National Technical University of
with the
the network layer. The main concept of the pro- Athens (NTUA). His current research interests are in the
fields of mobile networks, and mobile ad hoc and sensor corresponding
posed architecture is based on SLP extensions in networks. He is a member of the Technical Chamber of
conjunction with an algorithm, taking into Greece. distance and load
account the remaining energy supplies and the
minimum number of hops in each potential ser- DIMITRIOS A. KATEROS (dkateros@telecom.ntua.gr) received a
Dipl-Ing.degree from the School of Electrical and Computer
ones, arising from
vice-provisioning path within a MANET. The
new metrics are passed through an “application-
Engineering of NTUA in 2004. Since then he has been a
research associate and a Ph.D. candidate in the Intelligent
the network layer,
layer signaling” procedure. The slight load over-
head caused by adding this kind of “signaling”
Communications and Broadband Networks Laboratory of
NTUA. His primary research interests are mobile computing can be applied for
and software development in the area of mobile Internet.
can be easily condoned, if its vital advantages — He is a member of the Technical Chamber of Greece. advanced routing
the ad hoc environment’s lifetime maintenance
and all nodes’ connectivity retention — are real- N IKOLAOS D. T SELIKAS (ntsel@telecom.ntua.gr) received
Dipl.-Ing. and Ph.D. degrees from the School of Electrical
algorithms in
ized.
Further cross-layer implementation, incorpo-
and Computer Engineering of NTUA in 1999 and 2004,
respectively. He is currently working in NTUA as a research
MANETs.
rating the useful power and hop-number metrics associate. He is interested in broadband intelligent net-
with the corresponding distance and load ones, works, network convergence, service control, distributed
and middleware architectures, and telecommunications ser-
arising from the network layer, can be applied vice engineering. He has participated in several European
for advanced routing algorithms in MANETs. A Union and national research projects. He is a member of
possible comparison of the proposed architec- the Technical Chamber of Greece.
ture in this article with a cross-layer one could
E LEFTHERIOS A. K OUTSOLOUKAS (lefterisk@telecom.ntua.gr)
offer very useful results for considering the best received a Dipl-Ing. degree from the School of Electrical
solution in the development of a service-discov- and Computer Engineering of NTUA in 2002. Since then he
ery and delivery framework. has been a research associate and a Ph.D. candidate in the
Intelligent Communications and Broadband Networks Lab-
oratory of NTUA. His primary research interests are mobile
REFERENCES computing, and software development in the area of
[1] S. Vinoski, “Service Discovery 101,” IEEE Internet mobile Internet, middleware applications, and distributed
Comp., vol. 7, no. 1, Jan. 2003, pp. 69–71. technologies. He has participated in European Union and
[2] C. Bettstetter and C. Renner, “A Comparison of Service national research projects and he is a member of the Tech-
Discovery Protocols and Implementation of the Service nical Chamber of Greece.
Location Protocol,” Proc. 6th EUNICE Open Euro. Sum-
mer School: Innovative Internet Apps., Twente, The I AKOVOS S. V ENIERIS [M] (venieris@cs.ntua.gr) received a
Netherlands, Sept. 2000, pp. 13–15. Dipl.-Ing. degree from the University of Patras, Patras,
[3] W. Ma et al., “Implementation of a Lightweight Service Greece in 1988, and a Ph.D. degree from NTUA in 1990, all
Advertisement and Discovery Protocol for Mobile Ad in electrical and computer engineering. In 1994 he became
Hoc Networks,” IEEE GLOBECOM ’03, vol. 2, nos. 1–5, an Assistant Professor in the School of Electrical and Com-
Dec. 2003, pp. 1023–27. puter Engineering of NTUA, where he is now a full profes-
[4] H. Seo et al., “Performance of Service Location Proto- sor. His research interests are in the fields of broadband
cols in MANET Based on Reactive Routing Protocols” communications, Internet, mobile networks, intelligent net-
ICN 2005, 2005. works, internetworking, signaling, service creation and con-
[5] S. Helal et al., “Konark:A Service Discovery and Delivery trol, distributed processing, agents technology, and
Protocol for Ad Hoc Networks,” Proc. WCNC 2003, performance evaluation. He has more than 150 publica-
2003. tions in the above areas. He leads NTUA participation in
[6] D. Chakraborty, A. Joshi, and T. Finin, “GSD: A Novel several European Union and national projects. He is a
Group-Based Service Discovery Protocol for MANETS,” reviewer for several IEEE, ACM, Elsevier, and Wiley journals;
Proc. IEEE MWCN, 2002. Associate Editor for IEEE Communications Letters; a mem-
[7] A. Varshavsky, B. Reid, and E. de Lara, “The Need for ber of the editorial staff of Computer Communications
Cross-Layer Service Discovery in MANETs,” Tech. Rep. (Elsevier); and has been a guest editor for IEEE Communi-
CSRG-492, UofT Comp. Sci., 2004 cations Magazine. He is a co-editor of the books Intelligent
[8] A.Ephremides, “Energy Concerns in Wireless Networks.” Broadband Networks (Wiley, 1998) and Object Oriented
IEEE Wireless Commun., vol. 9, no. 4, Aug. 2002, pp. Software Technologies in Telecommunications (Wiley,
48–59. 2000). He is a member of the Technical Chamber of Greece.
IEEE Wireless Communications • October 2006 95
Authorized licensed use limited to: Annamalai University. Downloaded on August 8, 2009 at 02:30 from IEEE Xplore. Restrictions apply.](https://image.slidesharecdn.com/architectureforreliableservicediscovery-120715132652-phpapp01/85/Architecture-for-reliable-service-discovery-6-320.jpg)