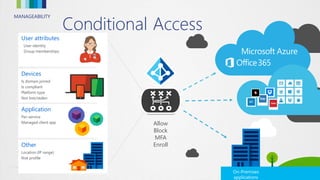
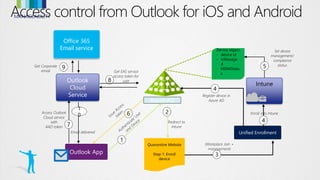
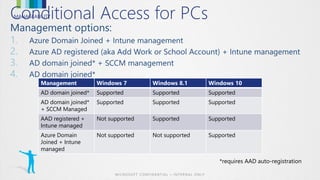
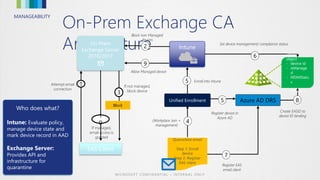
This document discusses conditional access for managing access to resources. It provides an overview of conditional access for devices and mobile apps accessing Office 365. It also covers conditional access for on-premises Exchange and SharePoint. Upcoming features are previewed. Functionality and deployment of conditional access are discussed for mobile devices, domain joined PCs, mobile apps without MDM, and advanced scenarios using ADFS. FAQs about conditional access are also addressed.