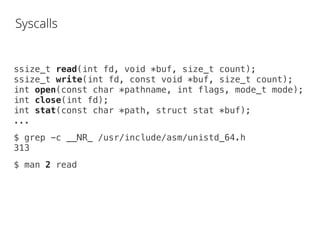
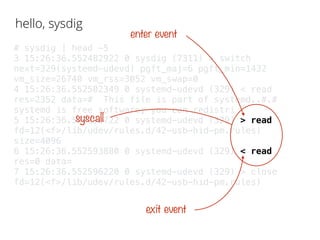
The document discusses various system calls and performance monitoring techniques using tools like strace and sysdig. It highlights the overhead of tracing methods and provides benchmarks comparing different performance metrics. Additionally, it presents examples of using sysdig to filter and analyze syscall events for optimization and troubleshooting purposes.



![strace
# strace cat /etc/hostname
execve("/bin/cat", ["cat", "/etc/hostname"], ...
brk(0) = 0x1675000
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT
mmap(NULL, 8192, PROT_READ|PROT_WRITE, ...
access("/etc/ld.so.preload", R_OK) = -1 ENOENT
open("/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=48577, ...}) = 0
mmap(NULL, 48577, PROT_READ, MAP_PRIVATE, 3, 0) = ...
close(3) = 0
access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT
(...)](https://image.slidesharecdn.com/sysdig-141109101238-conversion-gate02/85/Sysdig-5-320.jpg)













![filters
fd.name FD full name. If the fd is a file, this
field contains the full path. If the FD
is a socket, this field contain the
connection tuple.
!
proc.apid the pid of one of the process
ancestors.
!
evt.latency delta between an exit event and the
correspondent enter event.
!
(...)
!
# sysdig -l | grep -Ec '^[a-z0-9_.]+'
88](https://image.slidesharecdn.com/sysdig-141109101238-conversion-gate02/85/Sysdig-21-320.jpg)

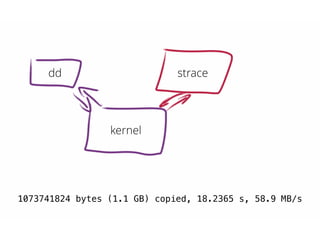
![back to that dd again…
# sysdig proc.name=not_dd > /dev/null & dd if=/dev/
zero of=/dev/null bs=1k count=1M ; killall sysdig
[1] 24070
1048576+0 records in
1048576+0 records out
1073741824 bytes (1.1 GB) copied, 0.981408 s, 1.1 GB/s](https://image.slidesharecdn.com/sysdig-141109101238-conversion-gate02/85/Sysdig-23-320.jpg)




![chisels: higher level of awesome
Lua
sysdig -cl
sysdig -i chisel_name
sysdig -c chisel_name [args…]](https://image.slidesharecdn.com/sysdig-141109101238-conversion-gate02/85/Sysdig-28-320.jpg)
![chisel all the things!
# sysdig -cl | grep -c ^[a-z]
37
# find /usr/share/sysdig/chisels/ -name '*.lua' | wc -l
42
the extra ones a re utilities to use in ch isels
(json, A NSI term ina l, etc.)](https://image.slidesharecdn.com/sysdig-141109101238-conversion-gate02/85/Sysdig-29-320.jpg)





