Embed presentation
Download as PDF, PPTX

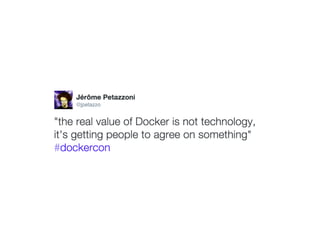

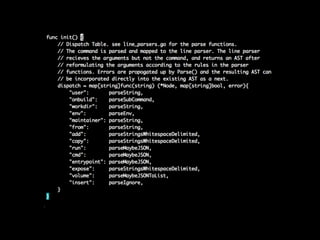
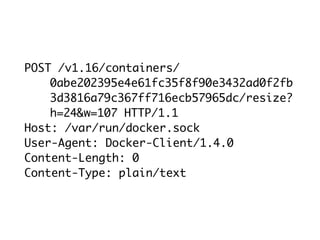
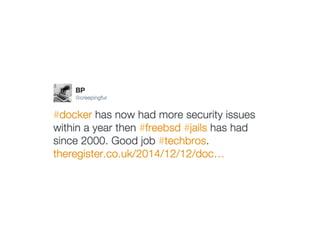








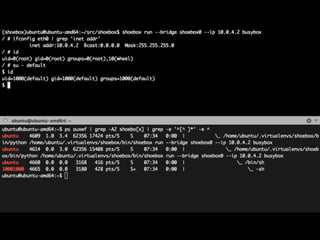

This document contains a Docker API request to resize a container's dimensions to a height of 24 and width of 107. It also includes commentary on making Docker containers more secure by running them unprivileged without needing root access, using user namespaces, and removing remaining setuid bits and capabilities.
















