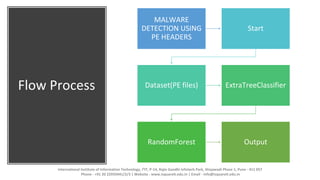
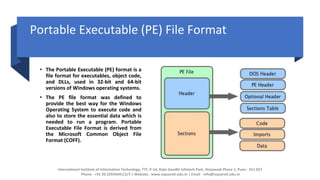
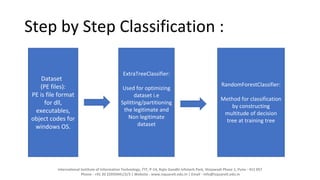
The document discusses using supervised machine learning for malware detection. It aims to classify files as malicious or not malicious by analyzing their PE headers with algorithms like ExtraTreeClassifier and RandomForestClassifier. The process involves extracting features from a dataset of PE files, using the classifiers to optimize and partition the data, then training the random forest model to classify files. Machine learning can effectively analyze malware and help build better antivirus solutions to detect threats in real-time.