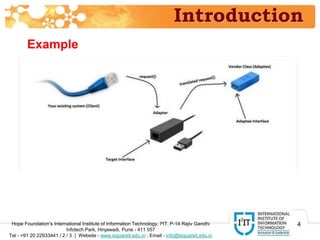
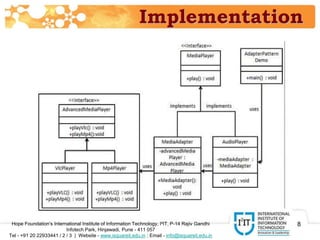
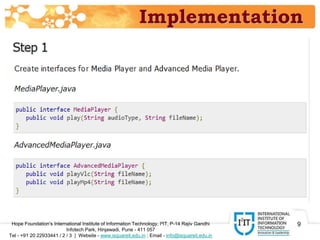
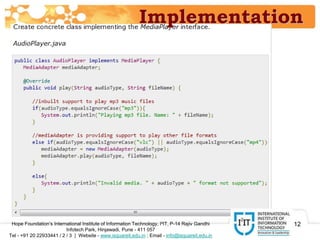
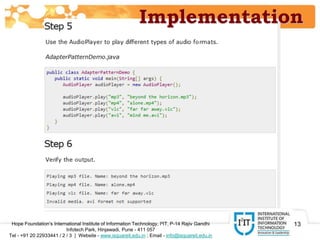
The document discusses the adapter pattern in software design, which provides a solution for bridging incompatible interfaces. It illustrates how this pattern can be implemented using an audio player that connects to advanced audio capabilities through an adapter class. A real-world analogy of this concept is likened to devices like USB to Ethernet adapters or card readers that enable compatibility between different interfaces.