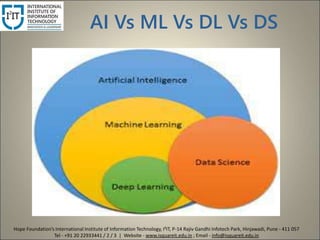
The document provides an overview of the differences between artificial intelligence (AI), machine learning (ML), deep learning (DL), and data science (DS), detailing their definitions and applications. It highlights specific examples of each technology, such as self-driving cars for AI and image recognition for ML. Additionally, it mentions career opportunities in related fields such as machine learning engineering and data science.