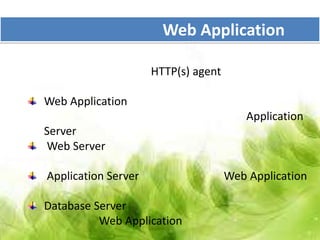
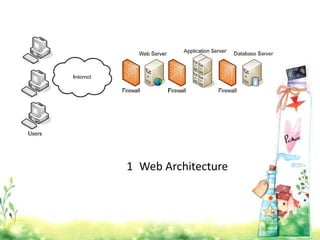
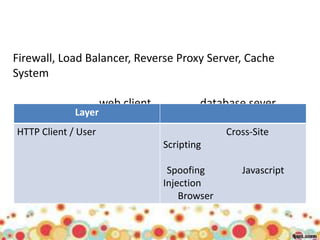
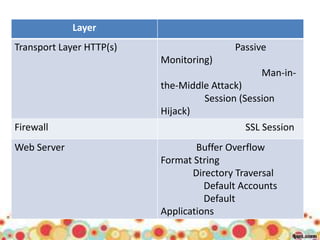
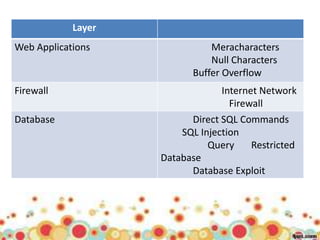
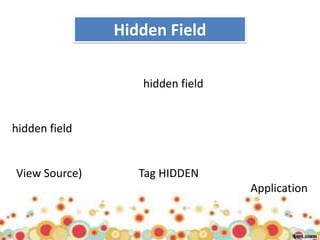
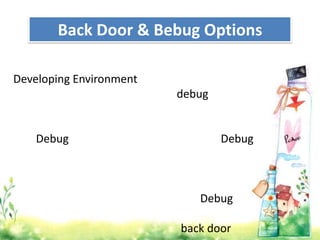
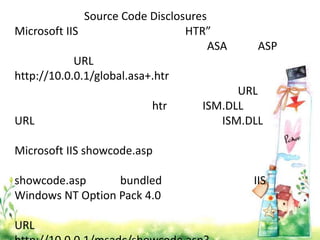
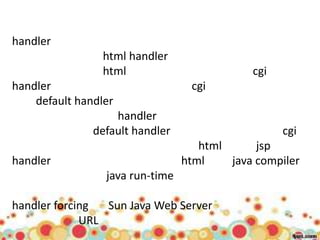
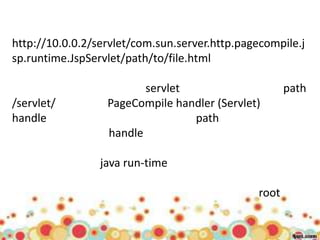
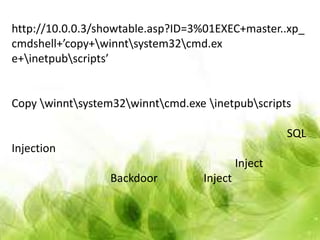
This document provides an overview of web application architecture and security. It describes the typical layers of a web application including the browser, web server, application server, and database server. It then discusses various types of attacks against web applications like SQL injection, cross-site scripting, and hidden field manipulation. Finally, it outlines best practices for secure coding and system scanning to prevent vulnerabilities.