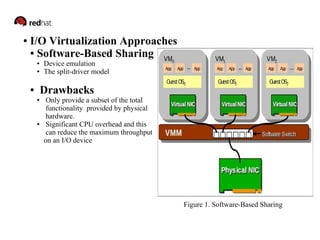
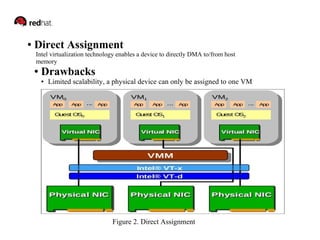
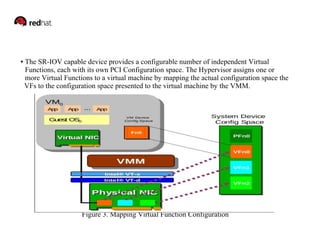
This document discusses SR-IOV (Single Root I/O Virtualization), which allows a PCIe device to appear as multiple separate devices. It describes how SR-IOV works by introducing physical functions and virtual functions. It then outlines the steps to enable SR-IOV on a Xen hypervisor, including configuring the network device, enabling virtual functions, binding VFs to the pciback driver, and assigning VFs to guest VMs. Reference links are also provided for additional information on SR-IOV and its implementation in Xen.





![How it works with Xen ● Setup
● Enabled VT-d(for Intel machine) or AMD-V(for AMD machine) in BIOS
● SR-IOV supported hardware. (for example: Intel 82576 and Intel 82599 NIC)
● Check PF
[host]#lspci | grep Etherne
86:00.0 Ethernet controller: Intel Corporation 82576 Gigabit Network Connection
(rev 01)
86:00.1 Ethernet controller: Intel Corporation 82576 Gigabit Network Connection
(rev 01)
● Enable VF in grub.conf
Add "iommu=no-intremap" in kernel line
Add "pci_pt_e820_access=on" in module line
Reboot the host.
After reboot, please check if these lines exist in `xm dmesg` output(mainly the first
line):
(XEN) [VT-D]iommu.c:1720: Interrupt Remapping hardware not found
(XEN) [VT-D]iommu.c:1722: Device assignment will be disabled for security reasons
(CVE-2011-1898).
(XEN) [VT-D]iommu.c:1724: Use iommu=no-intremap to override.](https://image.slidesharecdn.com/sr-iov-lkong-141109193324-conversion-gate01/85/SR-IOV-Introduce-9-320.jpg)
![If exist, change `iommu=1` to `iommu=no-intremap` and reboot again.
Enable VF in driver
[host]#echo 'options igb max_vfs=7' >> /etc/modprobe.conf
Then, restart system. VFs will be enabled automatically when host start.
Another way to enable VF(after reboot):
[host]# modprobe -r igb
[host]# modprobe igb max_vfs=7](https://image.slidesharecdn.com/sr-iov-lkong-141109193324-conversion-gate01/85/SR-IOV-Introduce-10-320.jpg)
![● Check VF
[root@unused ~]# lspci|grep Ethernet
04:00.0 Ethernet controller: Broadcom Corporation NetXtreme II BCM5709 Gigabit
Ethernet (rev 20)
04:00.1 Ethernet controller: Broadcom Corporation NetXtreme II BCM5709 Gigabit
Ethernet (rev 20)
86:00.0 Ethernet controller: Intel Corporation 82576 Gigabit Network Connection (rev 01)
86:00.1 Ethernet controller: Intel Corporation 82576 Gigabit Network Connection (rev 01)
86:10.0 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.1 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.2 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.3 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.4 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.5 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.6 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:10.7 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.0 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.1 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.2 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.3 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.4 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
86:11.5 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)](https://image.slidesharecdn.com/sr-iov-lkong-141109193324-conversion-gate01/85/SR-IOV-Introduce-11-320.jpg)
![● Load pciback driver
[host]#modprobe pciback
[host]#lsmod |grep pciback
pciback 65617 0
● Get device ID of Vfs
[host]# lspci -D | grep "82576 Virtual Function"
0000:86:10.0 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
0000:86:10.1 Ethernet controller: Intel Corporation 82576 Virtual Function (rev 01)
….
● Unbind device from host kernel driver
[host]#echo 0000:86:10.0 > /sys/bus/pci/drivers/igbvf/unbind
● Bind PCI device to pciback driver
[host]#echo 0000:86:10.0 > /sys/bus/pci/drivers/pciback/new_slot
[host]#echo 0000:86:10.0 > /sys/bus/pci/drivers/pciback/bind
Make sure the vifs get ip addresss?](https://image.slidesharecdn.com/sr-iov-lkong-141109193324-conversion-gate01/85/SR-IOV-Introduce-12-320.jpg)
![● Make sure the VFs has been hidden from Dom0 already
[host]#xm pci-list-assignable-devices
0000:86:10.0
● Create the guest with VF devices' ID as parameter
xm create pv-6.4-64.cfg pci='0000:86:10.0'](https://image.slidesharecdn.com/sr-iov-lkong-141109193324-conversion-gate01/85/SR-IOV-Introduce-13-320.jpg)


