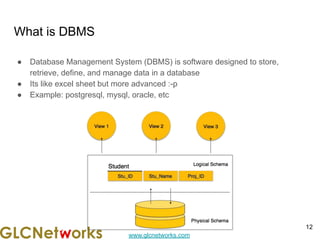
This document outlines the agenda for a webinar hosted by GLC Networks on SQL for data science. The webinar will include introductions to data science, database management systems (DBMS), how SQL is used for data science, a live practice session, and a question and answer period. It also provides background on GLC Networks and the trainer, Achmad Mardiansyah. Attendees are invited to introduce themselves and share their networking, Mikrotik, and expectations for the course.