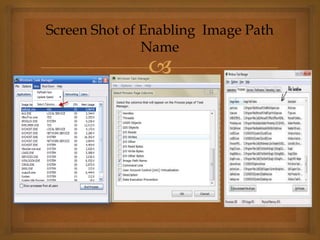
Keyloggers are tools that secretly monitor keyboard input to steal sensitive information like passwords or credit card numbers. There are software and hardware keyloggers. Software keyloggers can operate invisibly as kernel drivers or by intercepting API calls, while hardware keyloggers may include keyboard overlays or wireless sniffers. Keyloggers aim to protect the stolen data and avoid detection through techniques like hiding processes and filenames or requiring a password to access stored logs. Users can help prevent keylogging through measures such as enabling detailed task manager views, scanning for suspicious programs, and using alternative input methods when necessary.







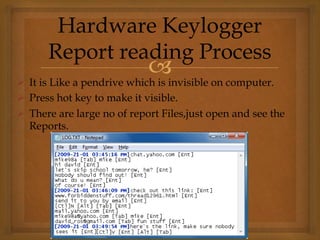


![
Use Speech to Text Services.
Use Hand writing recognition Tools.
Type Password randomly
if Your password is a1b2c3d4
then first type 1234 & then click at first position enter a
similar click on other proper position and enter
corresponding
letter ,then Key logger logs seems to be
[click]a[click]b[click]c[click]d
Detection And Prevention](https://image.slidesharecdn.com/keylogger-130921102132-phpapp01/85/Key-logger-Why-and-How-to-prevent-Them-14-320.jpg)