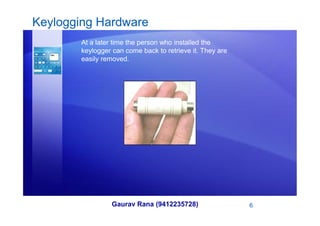
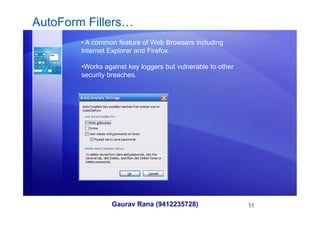
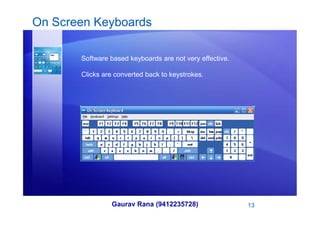
Key loggers can be used to record keyboard input either through hardware installed on a computer or software secretly installed. They are sometimes used legitimately to monitor employees but can also be used illegally to steal sensitive information like passwords, usernames, credit card numbers, and personal details. Prevention methods include keeping security software like antivirus and firewalls up to date, using auto-form fillers cautiously, and considering alternative keyboard layouts or on-screen keyboards.