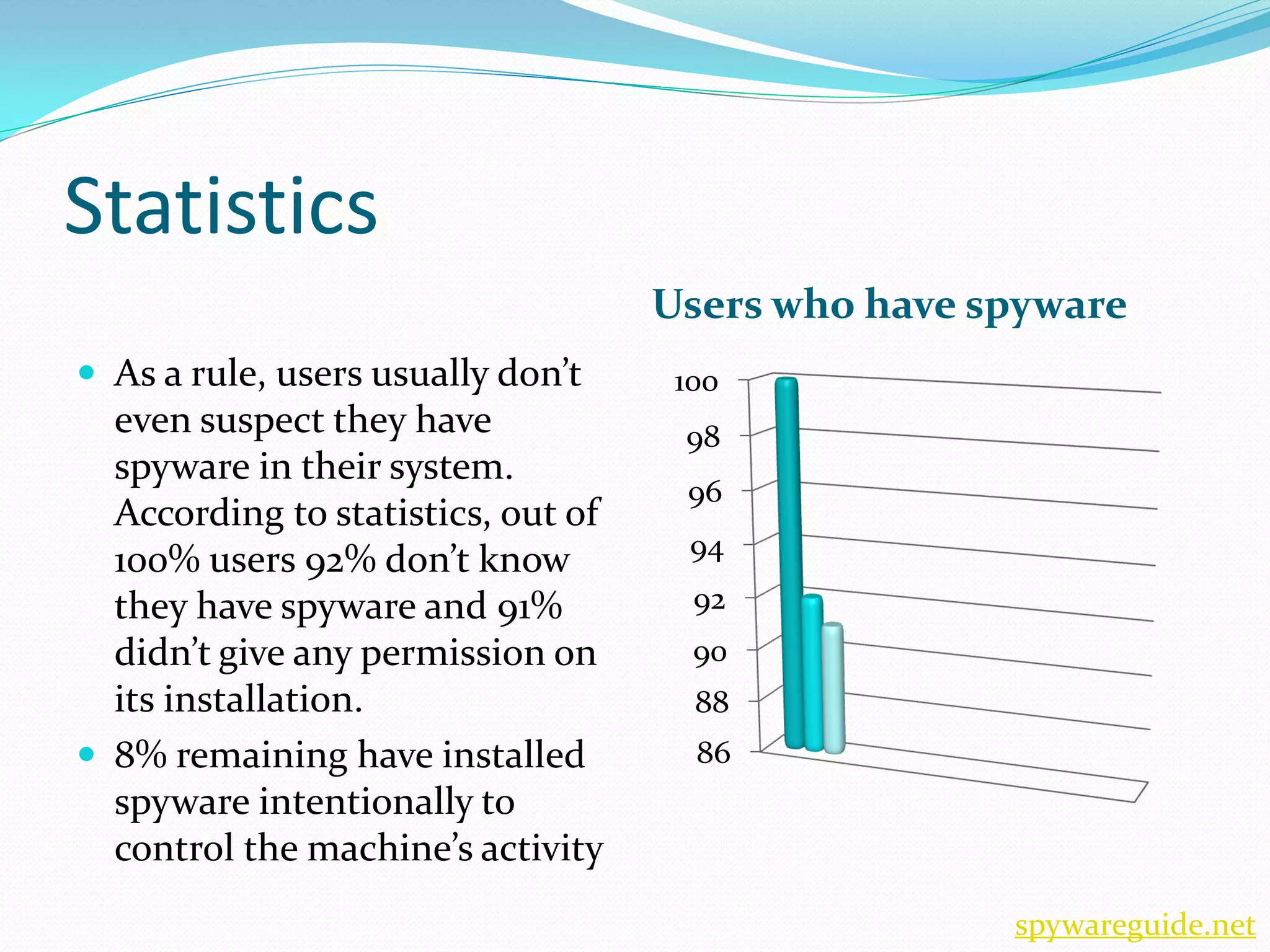
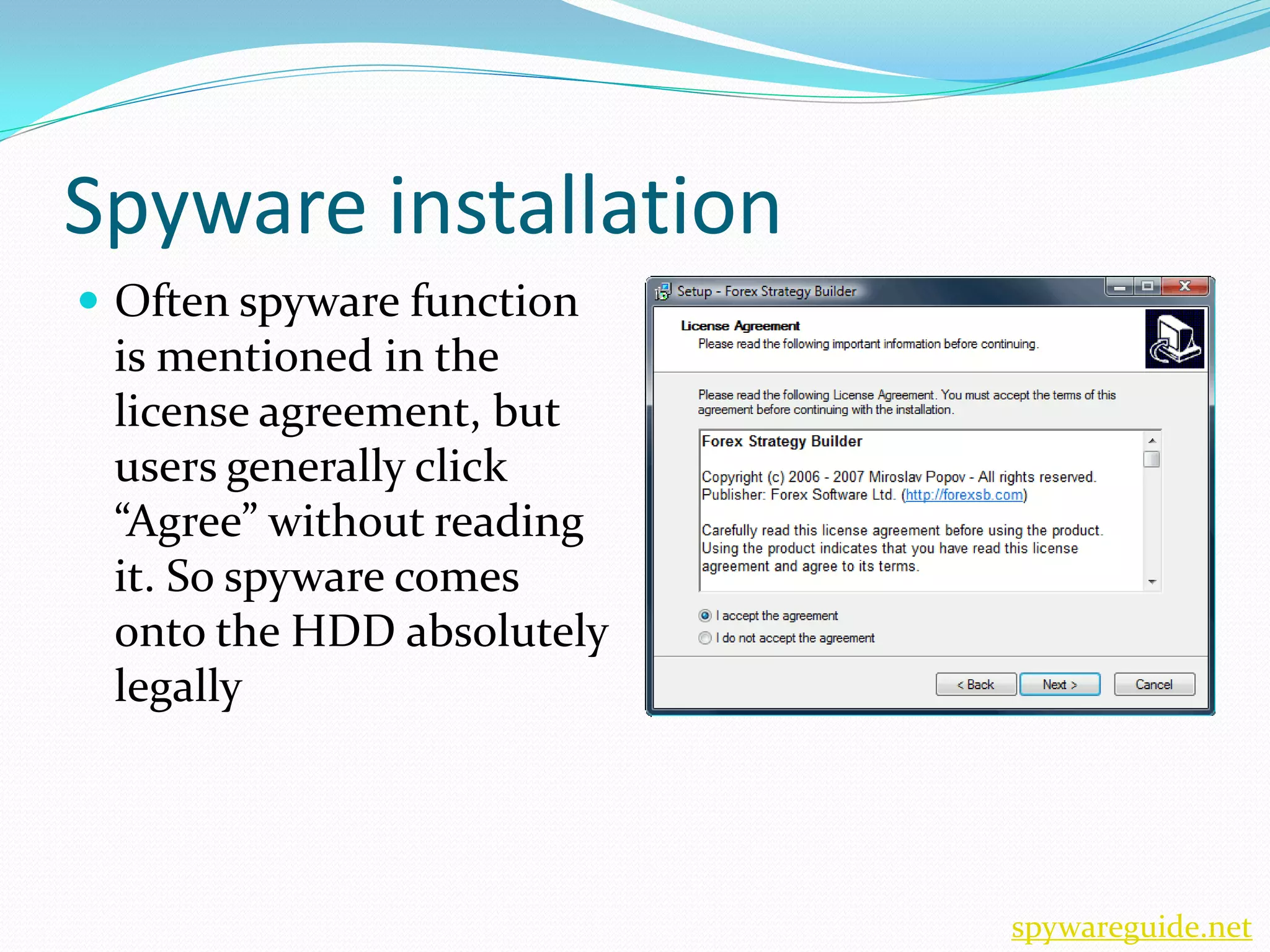
Getting spyware infects computers through other programs and exploits vulnerabilities. Spyware monitors users' activities and slows down computers by using system resources. Signs of spyware include reduced performance, changed browser settings, and unusual hard drive activity. Users can protect themselves by using anti-spyware software, avoiding suspicious sites, and keeping programs updated.