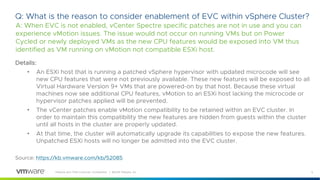
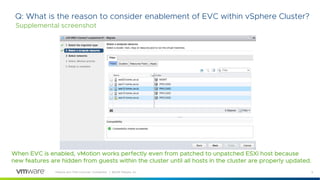
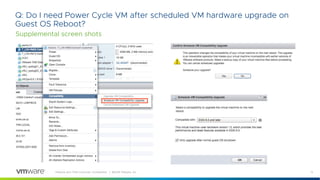
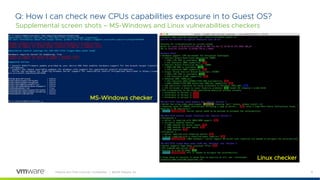
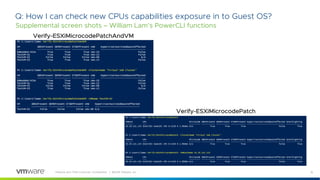
This document provides answers to frequently asked questions about Spectre and Meltdown security vulnerabilities for VMware ESXi administrators. It discusses available patches for ESXi, the need to apply microcode and guest operating system updates, and how to check that new CPU capabilities are properly exposed in virtual machines. Applying patches requires updating vCenter, ESXi hosts, and coordinating reboots of guest VMs, which can be a significant effort for large environments. Enabling Extended CPU Features in vCenter helps maintain VM compatibility during the update process.