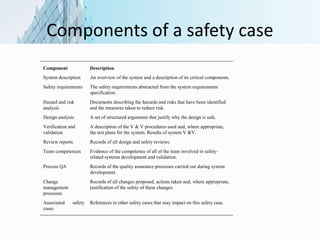
The document discusses validation processes for critical systems, including reliability validation, safety assurance, security assessment, and developing safety and dependability cases. Validation of critical systems involves additional processes compared to non-critical systems, such as formal validation to demonstrate that requirements are met to regulators' satisfaction. Reliability validation assesses whether a system meets required reliability levels through representative testing, while safety assurance establishes confidence in a system's safety through processes, validation techniques, and reviews. Security assessment and safety assurance both aim to demonstrate that systems cannot enter unsafe or insecure states. Safety and dependability cases make detailed arguments through evidence that systems achieve required safety levels.